The new bill on the protection of large user data (BPDn)

Previously, only large-scale organizations could afford a serious infrastructure for storing and analyzing Big Data. Today, big data is becoming increasingly diverse in various fields. At the same time, the development of Big Data not only opens up opportunities, but also carries with it many difficulties. Modern organizations are increasingly using machine learning and cognitive technologies, which often allow for more efficient use of big data. Also, in this area there are also their own, inherent in relatively new technologies, the threat to information security.
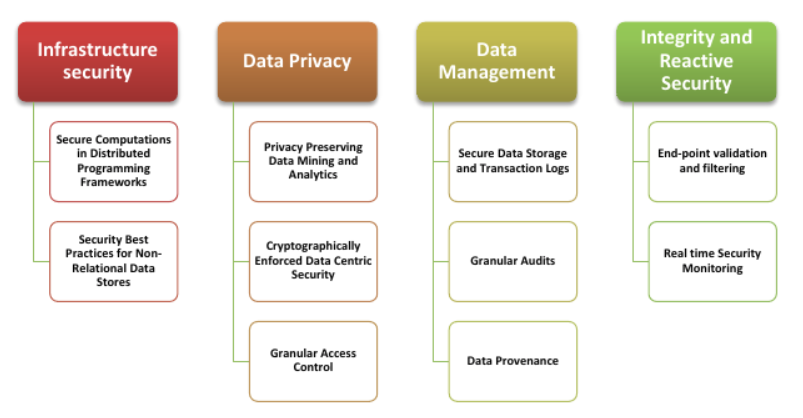
Around 2013, the Cloud Security Alliance (CSA) organization conducted an analysis of the major security problems of Big Data technology. CSA is a non-profit organization created to promote the use of best practices in ensuring the security of cloud computing, as well as to raise awareness of all stakeholders on this topic. Based on the analysis, they identified 10 main ones:
- Secure computing in distributed programming structures
- Security recommendations for non-relational data warehouses
- Secure data storage and transaction logs
- Check / filter endpoint input
- Real-time security monitoring
- Scalable and Comprehensive Data Mining and Analytics
- Cryptographically enhanced data security
- Granular Access Control
- Granular audit
- Data prediction
Later added 3 more new questions:
- Modeling: formalizing a threat model that covers most cyber-attack or data breach scenarios
- Analysis: search for acceptable solutions based on the threat model
- Implementation: implementation of the solution into existing infrastructures
If anyone is interested, the full version of the report can be obtained by reference .
In 2016, CSA publishes under the heading “Big Data Security and Privacy Guide: 100 Best Practices” (Big Data Security and Privacy Handbook). The material is available in the workgroup catalog for large data by reference .
It states that information security vulnerabilities are determined by the diversity of big data sources and formats, the streaming nature of data collection, and the need to transfer data between distributed cloud infrastructures. In addition, large amounts of such data contribute to an increase in the attack surface.
Two years have passed and on October 17, 2018 on the MegaFon company's official website there is news that the “Association of Big Data Market Participants” has been created in Russia. MegaFon, Mail.Ru Group, oneFactor, Tinkoff Bank, Yandex and Sberbank establish the Big Data Market Participants Association. Anna Serebryanikova, MegaFon's Operations Director, was elected President of the organization.
Quote from MegaFon press release:
“The members of the Association will be engaged in creating unified principles and standards for processing, storing, transmitting and using big data. Joint development will form the basis of the big data treatment policy of each company-participant of the Association. The priority tasks of the organization are to develop a business-oriented strategy for the development of the big data market, increase the technical and operational efficiency of interaction between industry participants, and form a code of ethics to protect the interests of users. ”The plot of the famous video “Seven Red Lines” surfaced in my head:
“Our company has developed a new strategic initiative to expand market penetration, maximize brand loyalty and increase intangible assets. To achieve these goals ... we started a new project. ”
At about the same time, 10/23/2018, a draft of the new Federal Law appears on the website of the Legislative System. Under this link you can familiarize yourself with the entire package of documents submitted for this project.
We will go briefly on the accompanying documents and the Federal Law itself. To begin with, I will quote an explanatory note to it:
“Every day, as a result of using various social networks, services, devices, and other information technologies, users leave a vast array of impersonal information about themselves on the Internet, which is commonly called“ large user data ”. This information as a result of automated processing allows you to determine individual user characteristics that are later used by operators of large user data for their own purposes or transferred by them to other interested parties for free or for a fee. However, such data is not personal data.From the same place:
The legal vacuum in the regulation of large user data in the Russian Federation deprives individuals (users) of adequate legal protection and support. ”
“By the Decree of the President of the Russian Federation of May 7, 2018 No. 204“ On the national goals and strategic objectives of the development of the Russian Federation for the period up to 2024 ”, the Government of the Russian Federation, together with the state authorities of the constituent entities of the Russian Federation, is charged with ensuring by 2024 the creation of sustainable and secure information and telecommunications infrastructure for high-speed transmission, processing and storage of large amounts of data, accessible to all organizations and households; the creation of a global competitive infrastructure for the transfer, processing and storage of data mainly based on domestic developments; information security based on domestic developments in the transmission, processing and storage of data, guaranteeing the protection of the interests of the individual, business and state. "The bill itself proposes to define the following concepts in the Federal Law of July 27, 2006 No. 149-ФЗ “On Information, Information Technologies and Protection of Information”:
- "Large user data",
- "Operator of large user data",
- "Processing large user data".
It is also proposed to establish the features of state regulation of processing large user data (the order of collection, transfer and other processing of large user data). And also, the duties of the operator of large user data.
A group of State Duma deputies headed by Mikhail Romanov proposed to understand by a large user data a set of information about natural persons and their behavior, which does not contain personal data, but at the same time allows a specific person to be identified without using additional information and processing. It is clarified that we are talking about information collected from various sources, including the Internet, the number of which exceeds a thousand network addresses.
It is supposed to establish a rule according to which users will be obliged to inform about such processing by placing a large user data on the operator’s website of the corresponding information message, and if it is not available, in another available way. By law, a provision may be introduced prohibiting the processing of large user data aimed at identifying a particular individual. However, it is planned that it will not be applied to the processing of such data at the request of federal executive bodies carrying out operational investigative activities.
Requirements for the information message and its form, as well as the maintenance of the register of operators of big data “by tradition” were hung on Roskomnadzor. Immediately, an obvious analogy can be traced: “operator”, “user data”, “notify” ...
We have little protection of personal data, now we are starting to protect Large User Data (BPN) by law. It is possible that a suddenly forgotten project GOST “Information Security When Using Cloud Technologies” will soon be pulled out from under the cloth . General provisions. ”The
study of personal data processing in Russia in accordance with the regulatory legal acts will help to study in more detail:
