Another way to disable telemetry collection in Windows 10 OC
Microsoft, using solitaire and a kerchief, taught users
how to use a mouse; now, using windows 10, it teaches to read a license agreement.
After the release of windows 10, messages immediately appeared about the collection of information about user actions and a lot of discussion about what to do. Quickly enough, users made a list of the main servers collecting information and tried to block them through the hosts file. But skeptics immediately made the sound assumption that MS could provide for this method and write some addresses in the code. Moreover, MS can always update server addresses through windows update.
The first users of windows 10 began to appear in our company, and we decided to try blocking the transmission of telemetry through the built-in windows firewall.
So, assembled a simple test bench:
Two laptops, put Windows 10 on one of them and connect it to the Internet through a second laptop using internet sharing. On the second laptop, which works as a NAT router, put Wireshark and determine the outgoing traffic to the MS servers from the first laptop.
What happened:
- Yes, Windows 10 sends data;
- The list of servers almost completely coincided with that indicated in the article habrahabr.ru/company/pt/blog/264763 and forums.untangle.com/web-filter/35894-blocking-windows-10-spying-telemetry.html
- The built-in Windows Firewall completely blocks the transfer of data to these nodes.
Rules for Firewall
After we received the IP list and made sure that they were effectively blocked, you can use Powershell script to add them to the settings.
To add a rule to the Firewall, you must run the following command (as an example, take the server "watson.telemetry.microsoft.com"):
netsh advfirewall firewall add rule name="telemetry_watson.telemetry.microsoft.com" dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes
Where:
name - the name of the rule and, by compatibility, the name of the Microsoft server;
dir = out - parameter indicating that the rule matches only outgoing network traffic;
action = block - network packets specified in this rule will be dropped by the firewall;
remoteip - the IP address of the recipient of the outgoing network packet area;
enable = yes - Indicates that the rule is currently enabled.
Similarly, other rules will be spelled out. As a result, the script will look something like this:
Firewall rules
Set-NetFirewallProfile -all
netsh advfirewall firewall add rule name=«telemetry_vortex.data.microsoft.com» dir=out action=block remoteip=191.232.139.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telecommand.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.92 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sqm.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.93 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.telemetry.microsoft.com» dir=out action=block remoteip=65.55.252.43,65.52.108.29 enable=yes
netsh advfirewall firewall add rule name=«telemetry_redir.metaservices.microsoft.com» dir=out action=block remoteip=194.44.4.200,194.44.4.208 enable=yes
netsh advfirewall firewall add rule name=«telemetry_choice.microsoft.com» dir=out action=block remoteip=157.56.91.77 enable=yes
netsh advfirewall firewall add rule name=«telemetry_df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.7 enable=yes
netsh advfirewall firewall add rule name=«telemetry_reports.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.91 enable=yes
netsh advfirewall firewall add rule name=«telemetry_wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.93 enable=yes
netsh advfirewall firewall add rule name=«telemetry_services.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.92 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sqm.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.94 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.9 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.ppe.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.11 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.appex.bing.net» dir=out action=block remoteip=168.63.108.233 enable=yes
netsh advfirewall firewall add rule name=«telemetry_telemetry.urs.microsoft.com» dir=out action=block remoteip=157.56.74.250 enable=yes
netsh advfirewall firewall add rule name=«telemetry_settings-sandbox.data.microsoft.com» dir=out action=block remoteip=111.221.29.177 enable=yes
netsh advfirewall firewall add rule name=«telemetry_vortex-sandbox.data.microsoft.com» dir=out action=block remoteip=64.4.54.32 enable=yes
netsh advfirewall firewall add rule name=«telemetry_survey.watson.microsoft.com» dir=out action=block remoteip=207.68.166.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.live.com» dir=out action=block remoteip=207.46.223.94 enable=yes
netsh advfirewall firewall add rule name=«telemetry_watson.microsoft.com» dir=out action=block remoteip=65.55.252.71 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe2.ws.microsoft.com» dir=out action=block remoteip=64.4.54.22 enable=yes
netsh advfirewall firewall add rule name=«telemetry_corpext.msitadfs.glbdns2.microsoft.com» dir=out action=block remoteip=131.107.113.238 enable=yes
netsh advfirewall firewall add rule name=«telemetry_compatexchange.cloudapp.net» dir=out action=block remoteip=23.99.10.11 enable=yes
netsh advfirewall firewall add rule name=«telemetry_cs1.wpc.v0cdn.net» dir=out action=block remoteip=68.232.34.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a-0001.a-msedge.net» dir=out action=block remoteip=204.79.197.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe2.update.microsoft.com.akadns.net» dir=out action=block remoteip=64.4.54.22 enable=yes
netsh advfirewall firewall add rule name=«telemetry_sls.update.microsoft.com.akadns.net» dir=out action=block remoteip=157.56.77.139 enable=yes
netsh advfirewall firewall add rule name=«telemetry_fe2.update.microsoft.com.akadns.net» dir=out action=block remoteip=134.170.58.121,134.170.58.123,134.170.53.29,66.119.144.190,134.170.58.189,134.170.58.118,134.170.53.30,134.170.51.190 enable=yes
netsh advfirewall firewall add rule name=«telemetry_diagnostics.support.microsoft.com» dir=out action=block remoteip=157.56.121.89 enable=yes
netsh advfirewall firewall add rule name=«telemetry_corp.sts.microsoft.com» dir=out action=block remoteip=131.107.113.238 enable=yes
netsh advfirewall firewall add rule name=«telemetry_statsfe1.ws.microsoft.com» dir=out action=block remoteip=134.170.115.60 enable=yes
netsh advfirewall firewall add rule name=«telemetry_pre.footprintpredict.com» dir=out action=block remoteip=204.79.197.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_i1.services.social.microsoft.com» dir=out action=block remoteip=104.82.22.249 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.windows.com» dir=out action=block remoteip=134.170.185.70 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.microsoft-hohm.com» dir=out action=block remoteip=64.4.6.100,65.55.39.10 enable=yes
netsh advfirewall firewall add rule name=«telemetry_feedback.search.microsoft.com» dir=out action=block remoteip=157.55.129.21 enable=yes
netsh advfirewall firewall add rule name=«telemetry_rad.msn.com» dir=out action=block remoteip=207.46.194.25 enable=yes
netsh advfirewall firewall add rule name=«telemetry_preview.msn.com» dir=out action=block remoteip=23.102.21.4 enable=yes
netsh advfirewall firewall add rule name=«telemetry_dart.l.doubleclick.net» dir=out action=block remoteip=173.194.113.220,173.194.113.219,216.58.209.166 enable=yes
netsh advfirewall firewall add rule name=«telemetry_ads.msn.com» dir=out action=block remoteip=157.56.91.82,157.56.23.91,104.82.14.146,207.123.56.252,185.13.160.61,8.254.209.254 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a.ads1.msn.com» dir=out action=block remoteip=198.78.208.254,185.13.160.61 enable=yes
netsh advfirewall firewall add rule name=«telemetry_global.msads.net.c.footprint.net» dir=out action=block remoteip=185.13.160.61,8.254.209.254,207.123.56.252 enable=yes
netsh advfirewall firewall add rule name=«telemetry_az361816.vo.msecnd.net» dir=out action=block remoteip=68.232.34.200 enable=yes
netsh advfirewall firewall add rule name=«telemetry_oca.telemetry.microsoft.com.nsatc.net» dir=out action=block remoteip=65.55.252.63 enable=yes
netsh advfirewall firewall add rule name=«telemetry_reports.wes.df.telemetry.microsoft.com» dir=out action=block remoteip=65.52.100.91 enable=yes
netsh advfirewall firewall add rule name=«telemetry_ssw.live.com» dir=out action=block remoteip=207.46.101.29 enable=yes
netsh advfirewall firewall add rule name=«telemetry_msnbot-65-55-108-23.search.msn.com» dir=out action=block remoteip=65.55.108.23 enable=yes
netsh advfirewall firewall add rule name=«telemetry_a23-218-212-69.deploy.static.akamaitechnologies.com» dir=out action=block remoteip=23.218.212.69 enable=yes
Execution of the created script
In order not to go a long way to launch this power shell script with administrator privileges, it is easier to create a .bat file and run it. UAC will itself request confirmation of rights.
@echo off
cls
echo Telemetry
echo Rules of Firewall
echo.
echo press any key to continue...
pause > NUL
echo Rules of Firewall
echo.
PowerShell -NoProfile -ExecutionPolicy Bypass -Command "& {Start-Process PowerShell -ArgumentList '-NoProfile -ExecutionPolicy Bypass -File ""%~dp0.\ms_new.ps1""' -Verb RunAs}"
echo Rules included in Firewall...
echo.
pause
Where ms_new.ps1 is the name of the created file with power shell commands.
After that, the added rules will be displayed in the Windows Firewall, as in the screenshot below:
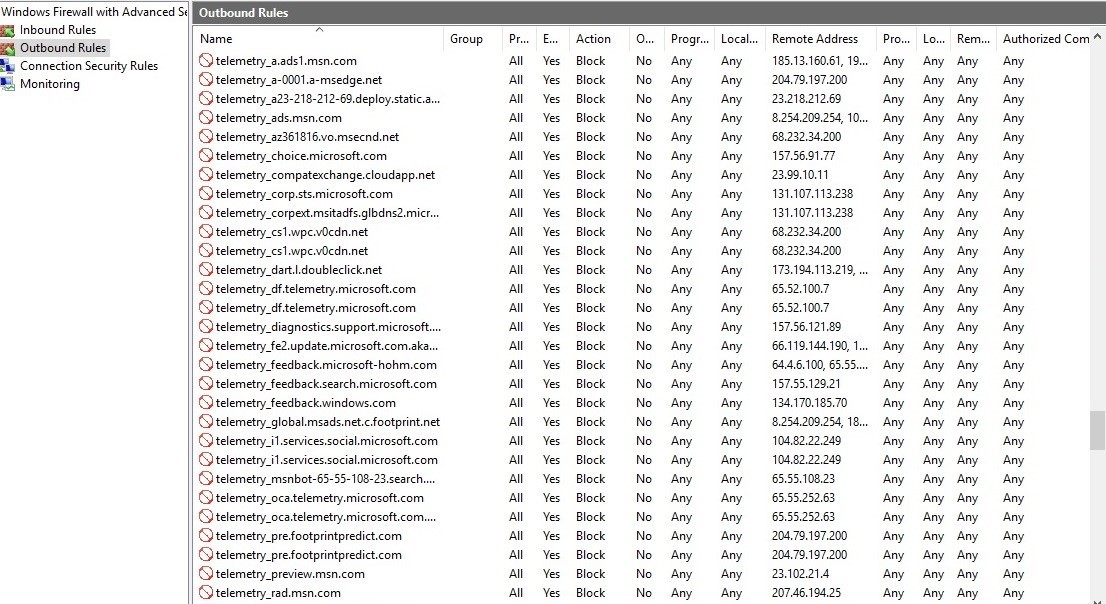
And, in addition, information not related to the firewall, but related to the collection of telemetry
Windows 7/8 / 8.1
It is also worth noting that users of Windows 7/8 / 8.1 have received updates that expand the system's capabilities for collecting and sending telemetric data. Accordingly, you can also apply the recommendations presented in this article to these users, or delete the updates habrahabr.ru/post/265283 .Key logger
It is necessary to disable “DiagTrack” (data collection in Windows components) and “dmwappushservice” (WAP push message routing service). To do this, run the command line as administrator and disable the services:sc stop DiagTrack
sc stop dmwappushservicesc delete DiagTrack
sc delete dmwappushservice
Telemetry Scheduler
In the Taskschd.msc console, you must disable the tasks:Spoiler heading
REM *** Task that collects data for SmartScreen in Windows ***
schtasks /Change /TN "Microsoft\Windows\AppID\SmartScreenSpecific" /Disable
REM *** Collects program telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\ProgramDataUpdater" /Disable
REM *** Collects program telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser" /Disable
REM *** Aggregates and uploads Application Telemetry information if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\AitAgent" /Disable
REM *** This task collects and uploads autochk SQM data if opted-in to the Microsoft Customer Experience Improvement Program ***
schtasks /Change /TN "Microsoft\Windows\Autochk\Proxy" /Disable
REM *** If the user has consented to participate in the Windows Customer Experience Improvement Program, this job collects and sends usage data to Microsoft ***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\Consolidator" /Disable
REM *** The Kernel CEIP (Customer Experience Improvement Program) task collects additional information about the system and sends this data to Microsoft. ***
REM *** If the user has not consented to participate in Windows CEIP, this task does nothing ***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\KernelCeipTask" /Disable
REM *** The Bluetooth CEIP (Customer Experience Improvement Program) task collects Bluetooth related statistics and information about your machine and sends it to Microsoft ***
REM *** The information received is used to help improve the reliability, stability, and overall functionality of Bluetooth in Windows ***
REM *** If the user has not consented to participate in Windows CEIP, this task does not do anything.***
schtasks /Change /TN "Microsoft\Windows\Customer Experience Improvement Program\BthSQM" /Disable
REM *** Create Object Task ***
schtasks /Change /TN "Microsoft\Windows\CloudExperienceHost\CreateObjectTask" /Disable
REM *** The Windows Disk Diagnostic reports general disk and system information to Microsoft for users participating in the Customer Experience Program ***
schtasks /Change /TN "Microsoft\Windows\DiskDiagnostic\Microsoft-Windows-DiskDiagnosticDataCollector" /Disable
REM *** Measures a system's performance and capabilities ***
schtasks /Change /TN "Microsoft\Windows\Maintenance\WinSAT" /Disable
REM *** Network information collector ***
schtasks /Change /TN "Microsoft\Windows\NetTrace\GatherNetworkInfo" /Disable
REM *** Initializes Family Safety monitoring and enforcement ***
schtasks /Change /TN "Microsoft\Windows\Shell\FamilySafetyMonitor" /Disable
REM *** Synchronizes the latest settings with the Family Safety website ***
schtasks /Change /TN "Microsoft\Windows\Shell\FamilySafetyRefresh" /Disable
REM *** SQM (Software Quality Management) ***
schtasks /Change /TN "Microsoft\Windows\IME\SQM data sender" /Disable
REM *** This task initiates the background task for Office Telemetry Agent, which scans and uploads usage and error information for Office solutions ***
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentFallBack" /Disable
REM *** This task initiates Office Telemetry Agent, which scans and uploads usage and error information for Office solutions when a user logs on to the computer ***
schtasks /Change /TN "Microsoft\Office\OfficeTelemetryAgentLogOn" /Disable
also suspicious tasks in the scheduler, I recommend to disable:
Spoiler heading
REM *** Scans startup entries and raises notification to the user if there are too many startup entries ***
schtasks /Change /TN "Microsoft\Windows\Application Experience\StartupAppTask" /Disable
REM *** Protects user files from accidental loss by copying them to a backup location when the system is unattended ***
schtasks /Change /TN "Microsoft\Windows\FileHistory\File History (maintenance mode)" /Disable
REM *** This task gathers information about the Trusted Platform Module (TPM), Secure Boot, and Measured Boot ***
schtasks /Change /TN "Microsoft\Windows\PI\Sqm-Tasks" /Disable
REM *** This task analyzes the system looking for conditions that may cause high energy use ***
schtasks /Change /TN "Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem" /Disable
All of the above is not a 100% panacea, but one of the compromise solutions.
In this article we will update the list of servers and PS script for them.
update 1: Updated the list of task scheduler.
How to protect yourself from the firewall with malware, you can read in my article:
A simple but reliable way to protect your computer from viruses and trojans.
Sincerely, the team of the company Servilon.ru Servilon.com
