Study: Almost all popular firewalls skip XSS attacks

Security researcher Mazin Ahmed (Mazin Ahmed) published the results of an analysis of how to bypass XSS protection in the popular application-level firewalls (Web application firewalls, WAF).
Ahmed used several virtual machines running the popular browsers Google Chrome, Opera, Mozilla Firefox, and Internet Explorer.
The researcher studied commercial and open products: F5 Big IP, Imperva Incapsula, AQTRONIX WebKnight, PHP-IDS, Mod-Security, Sucuri, QuickDefence, Barracuda WAF. At least one XSS vector was presented for each product, which allowed to bypass the protection.
Incorrect handling of JS events
A number of well-known firewalls were missed by the onwheel and onshow JS events - they allow you to execute a malicious script when scrolling with the mouse and when displaying a menu item, respectively. In particular, F5 Big IP, Barracuda WAF were found to be affected by this error.
Quick Defense was also unable to detect malicious code injection using the “onsearch” and “ontoggle” JS events.
Double URL encoding and JS-F ** K
Using double URL coding, as well as a technique called JS-F ** K (allows you to represent any JS code using a set of 6 characters), the researcher bypassed XSS filters of several WAFs at once. This round was affected by Imperva Incapsula, F5 Big IP (this WAF has four different rounds at once), Mod-Security, PHP-IDS.
Other vulnerabilities
In addition, the PHP-IDS rules contained an error that allowed an attacker to bypass the filters using the svg tag. And Sucuri WAF did not take into account the possibility of a seven-bit data representation in the us-ascii encoding, which is perceived by Internet Explorer 6 and 7 browsers: A
¼script¾alert(¢xss¢)¼/script¾detailed description of all the workarounds is presented in the study .
The researcher passed information about the detected security errors to the developers of all the firewalls involved in the study. Most of them have already released patches or will fix bugs in the next version of the product, there was no answer only from the PHP-IDS development team.
And what do we have
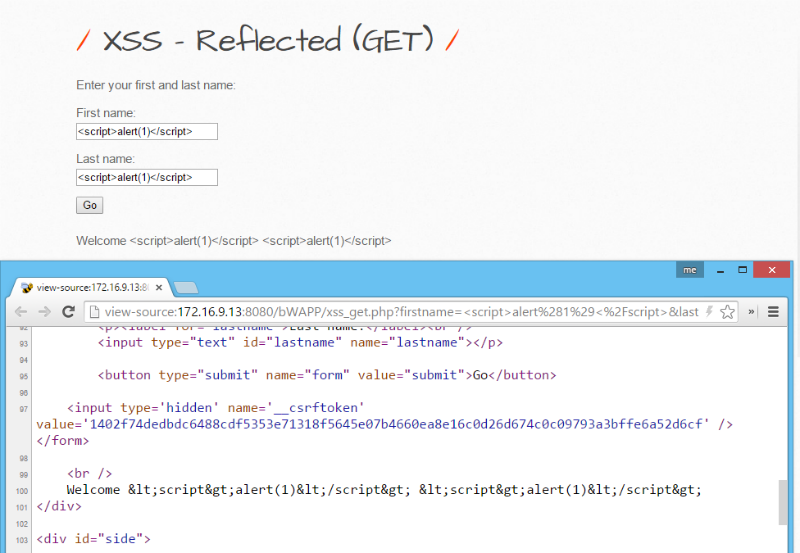
We tested the self-learning PT Application Firewall (PT AF) for exposure to the workarounds described by Ahmed. We will consider three possible scenarios of the operation of our defense.
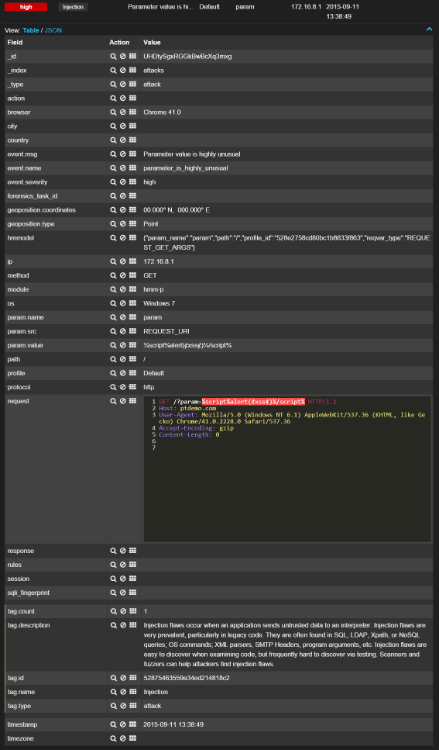
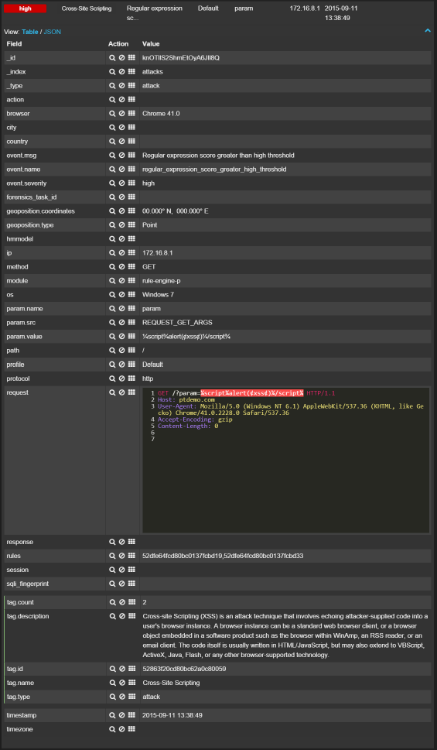
(1) The trained system blocks such attacks, considering them as anomalous requests to the application: (2) Attacks similar to the examples given in the PDF document are blocked by regular expressions: (3) If the user input somehow bypassed all the protective PT AF mechanisms were found in the server’s response, they will be escaped in the context of the HTML page: PS If you are close to the WAF theme, join the PT Application Firewall development team - habrahabr.ru/company/pt/blog/266415