Security Week 37: Bug-bugzilla, Karbanak backing, C & C fishing
 In a new episode of the series, based on news in the field of information security:
In a new episode of the series, based on news in the field of information security: - Hacking Bugzilla once again reminds that passwords must be not only complex, but also unique.
- The Carbanak campaign, responsible for the theft of hundreds of millions of dollars from financial institutions, has been seen in Europe and the USA.
- The Lab’s study on how to transfer the command server of an espionage campaign from the “very difficult to find” level to the “look for winds in the field” level
as well as unclosed telnet in Seagate WiFi drives, patches, fishing and music viruses from the past. I remind you of the rules: every week the editorial board of the Threatpost news site selects the three most significant news, to which I add an extended and merciless comment. All episodes of the series can be foundhere .
To summarize the survey from the last issue: Most often, the router is updated every couple of years or even less often (31% chose this option). 28% never updated the router. The survey involved 210 people. Thanks to all!
Hacking Bugzilla bug tracker
News . FAQ on the attack.
In the issue for the 34th week, I raised the topic of responsible disclosure of information about vulnerabilities, showing by examples when it is possible and when it is not advisable to disclose information about bugs found. The story about hacking the Mozilla bug tracker shows well when to disclose vulnerability information is not worth it. Well it’s clear: they haven’t repaired it yet. Firefox Browser Released in Augustpatch to close vulnerability in the built-in PDF viewer. It was discovered thanks to a user who became a victim of an exploit and reported an incident: the source of the attack was a “prepared” advertising banner, and the result was stolen personal data.
I suspect that already in the process of releasing the patch, it became clear to the developers that the bug was not new. The Bugzilla system already had information about him, albeit in a part that was closed to the public. There were suspicions of unauthorized access, which were confirmed last week. At the same time, there was no “hacking" as such: they simply identified the privileged user, found the password from the hacked database of another resource, which coincided with the password for Bugzilla.

As a result, attackers had access to “secret bugs” from September 2014, and possibly from September 13th, that is, a couple of years. During this time, according to a very detailed FAQ released following the investigation, crackers had access to information about 185 bugs, including 53 serious vulnerabilities. 43 vulnerabilities from this list were already closed by the time of gaining unauthorized access. Of the remaining ten, two vulnerabilities “leaked out” less than a week before the patch; five theoretically could be exploited from a week to a month before closing. The remaining three vulnerabilities could be exploited 131, 157 and 335 days before the release of the patch. This is the worst news about this hack, although Mozilla developers "have no evidence that these vulnerabilities have been exploited" in practice.
In general, the moral of this story is understandable, and here I certainly want to get into an armored car and proclaim instructively: “Comrades! Ladies and Gentlemen! Friends! Use unique passwords for each resource! ” But not everything is so simple: such a work scheme makes it almost mandatory to use a password manager. And even if you have one, you need to carefully and patiently change the passwords on all the resources that you use actively. And ideally - generally at all. Meanwhile, according to our data, only 7% of users constantly work with password managers. It is interesting to compare with the audience of Habr, therefore, at the end of the post, another poll.
New versions of Carbanak attack US and Europe
News . February study of the "Laboratory". New CSIS study .
I will quote the February announcement of our study on the “great robbery”:
“Attackers could transfer funds to their own accounts, manipulate the balance so that numerous security systems did not notice this. Without full control over domestic banking systems, it was impossible to crank up such an operation. Therefore, after the penetration, various methods were used to collect information on how the infrastructure of the bank was arranged, including video recording. ”
Thanks to cooperation with law enforcement agencies, the damage from Carbanak, a complex, multi-stage attack on financial institutions, was estimated at a billion dollars, with more than a hundred victims - large companies. But this was in February, and at the end of August, researchers at the Danish company CSIS discovered a new modification to Carbanak. The differences between the new and old versions are small, in particular, a permanent IP address is used instead of a domain name to connect to the management server. But the plugins used to steal data are similar to those mentioned in the February study of the "Laboratory".
According to CSIS, the goal of the new Carbanak option is for large companies in Europe and the United States.
Turla APT: hiding C&C via satellite Internet
News . Previousnews. Research .
The Turla cyber-espionage campaign has long been investigated by several security companies, including Kaspersky Lab. Last year we published a detailed studydevoted to methods of penetrating victims' computers, collecting information and sending data to control servers. At each stage of this relatively complex campaign, many tools are used - spear phishing with infected documents that exploit zero-day vulnerabilities, infected websites, various data collection modules used depending on the task and importance of information, a complex network of proxies and Command & Control servers. Outcome (as of August last year): several hundred victims in 45 countries, mainly in Europe and the Middle East.
Lab expert Stefan Tanase published this weekthe results of a more detailed study of the final stage of the attack - when the data is transferred to the management server. To collect information Turla, like other attacks of the APT-class, uses many methods, for example, bulletproof hosting. But when a specific server on a specific hosting becomes the end point of the information, the probability of its confiscation by law enforcement agencies (and simply disconnection by the provider) is noticeably different from zero, how many proxy chains do not build.
This is where satellite Internet comes to the rescue. Pros: the server can be installed anywhere in the satellite’s coverage area (and it’s also easy to move to another location). Cons: renting a bilateral channel of a minimum decent width costs a lotexpensive, and, again, easily tracked by paper trail. So, the data delivery methodology discovered by our expert does not require a channel rental at all.
There is such a thing as " satellite fishing ": when slightly modified software on the satellite terminal does not discard data packets that are not intended for a particular subscriber, but collects them. As a result, the "fisherman" receives files and web pages that are not intended for him, and indeed any data. This works under one condition: if the data stream is not encrypted. The Turla attack uses approximately the same method, with one clarification: when listening to traffic, you need to determine the IP of the victim - the legal and unsuspecting owner of the satellite Internet terminal, and force the infected machines to send data to this IP.
In this case, special ports are used for communication, which are closed on ordinary systems, and data packets arriving at these ports are simply discarded by the victim’s network equipment. But those who listen to traffic can intercept this data without revealing their location.
I remember that old radiotelephones did not encrypt voice communication at all, with the expectation that devices for receiving at these frequencies simply could not be bought. At first, that was how it was, but pretty quickly all-wave radios began to be sold on every corner and cost a penny. The analogy is rather strained, because you still have to spend a couple of thousand dollars on a kit for receiving and processing data using the “Turla method”. But the bottom line is that in satellite Internet systems there is an “inherent” vulnerability that cybercriminals use. What to do with this is not very clear.
And the result is that the approximate location of the Turla command server coincides with the coverage area of the satellite operator:
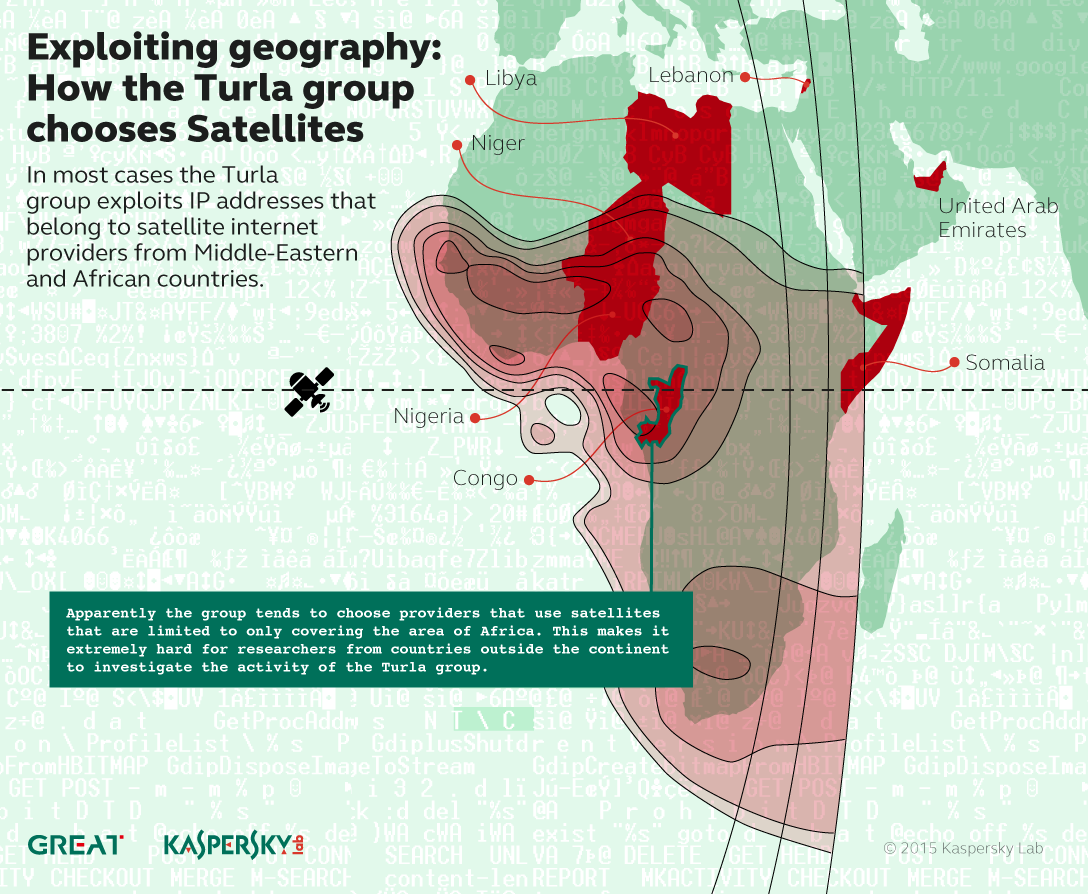
Further traces are lost.
What else happened: We
discovered another ransomware Trojan for Android, which communicates with the command server via XMPP. Chats and other IMs have long been using malware on PCs to coordinate work, so the news confirms once again: mobile threats develop similarly to desktop ones, only faster.
Regular patches of critical vulnerabilities in Google Chrome (update to version 45).
In the "wireless" hard drives, Seagate found a sweet pair of telnet unsecured access and a hard-coded root password. Important news, but we have already discussedThis topic is detailed last time in relation to routers. Conclusion: to everything that distributes WiFi, you need to protect especially carefully. And now WiFi is even given out by cameras.
 Antiquities:
Antiquities:“Manowar-273”
A resident harmless virus that infects COM and EXE files by default when they are executed (the COMMAND.COM file is infected using the Lehigh algorithm). Contains the text "Dark Lord, I summon thee! MANOWAR. "
"Iron-Maiden" A
non-resident very dangerous virus that infects COM files in the current directory by default. Since August 1990, depending on the current time, it can erase two random sectors on disks. Contains the text "IRON MAIDEN".
Quote from the book "Computer viruses in MS-DOS" by Eugene Kaspersky. 1992 year. Pages 70.75.
Disclaimer: This column reflects only the private opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. That's how lucky.
Only registered users can participate in the survey. Please come in.
Do I need a password manager to prevent hacking according to the Bugzilla script?
- 61% needed 61
- 42% not needed 42
Do you use a password manager?
- 51% I use 70
- 51.8% Don't use 71
