Security Week 36: jailbreak robbery, farewell to RC4, porosity of routers
 When computers finally learn to plug directly into the brain, our lives will become much more interesting. Instead of SMS, we will receive mentograms, they are insinuatingly insinuating in their inner voice. I thought an interesting thought - share with your friends a slight brain movement! Remember what the wife asked to buy at the store; for only $ 2.99 without VAT. Imperfect technologies of the first bi-discrete interfaces will transfer terabytes of data per minute to a computer (smartphone, only without a screen), leaving behind powerful processors of the future the task of catching particles of meaning from the noise of electrical pulses.
When computers finally learn to plug directly into the brain, our lives will become much more interesting. Instead of SMS, we will receive mentograms, they are insinuatingly insinuating in their inner voice. I thought an interesting thought - share with your friends a slight brain movement! Remember what the wife asked to buy at the store; for only $ 2.99 without VAT. Imperfect technologies of the first bi-discrete interfaces will transfer terabytes of data per minute to a computer (smartphone, only without a screen), leaving behind powerful processors of the future the task of catching particles of meaning from the noise of electrical pulses.In short, the latest iPhone 164 will know absolutely everything about us. Having survived 34 rebranding and 8 restructuring, Google will store this data and process it further in data centers occupying more than 2 percent of the Earth’s surface. And only then, having made an incredible breakthrough in technology, they will begin to think about how to protect this data. Only after the first appearance of a collection of erotic dreams of unsuspecting citizens and women on the black market in Bangkok. Only after a scandal with a bank reading the minds of loan recipients right at the time of application. And then you have to seriously understand - what kind of data are we collecting? How to store?
But all this will come later. Interestingly, and now someone is thinking about how much the owner gives out the archive of gyro readings from a mobile phone? Security research always happens after technology enters the market, while technology makers almost never think about security. In today's digest of important information security news for the week - debriefing in software and devices today, which millions of people have been using for a long time. I remind you of the rules: every week the editorial board of the Threatpost news site selects the three most significant news, to which I add an extended and merciless comment. All episodes of the series can be found here .
Why are 5 and 12 volts fed to the head in the picture? I dont know!
Trojan stealing data from hacked iPhone
News . Research by Palo Alto Networks.
Not all reports of any vulnerability or theft can be taken and retold in simple words. This one is possible. In China, they found an iPhone app that integrates with Apple’s servers and steals passwords from the iTunes Store. Found by side signs: mass complaints of users about the theft of money from their accounts - the card for all Apple users is tied to the account with a tight sea knot, and usually nothing is required for paying for “birds” except for a password.
Cool, yeah? Not really. Only owners of jailbroken devices were attacked. Independent researchers from China, who asked to call them WeipTech, accidentally broke the C&C server of criminals and found there are more than 225 thousand users in the public domain (I didn’t know that there are so many jailbreak proponents) in the format “username, password, device GUID”. Well, then everything is clear: the malicious application is distributed through the pirate freighter of the alternative Cydia store, is embedded in the communication between the device and Apple using the man-in-the-middle technology, and sends the stolen to its server. Cherry on the cake: the key for encrypting passwords is static, uses the phrase "mischa07".

Mischa07 steals user passwords
It is unclear whether this “Misha” was able to seriously earn on KeyRaider’s attack, and that’s not the point. The main thing in this news is this: an iPhone with a jailbreak in terms of security is worse than Android. If you break the (very strong) protection of iOS, then there are no further checks? Do whatever you want? Quite a typical situation for well-guarded systems, by the way: powerful firewalls, physical protection, everything is disconnected from the Internet, the fly will not fly around the perimeter. Inside - a computer on the fourth stump and with Windows XP unpatched since 2003. And if the perimeter can be circumvented? Actually, in the context of iOS, the same question arises: if a simple, valid, massive root exploit suddenly appears - what will happen? Does the vendor have a plan B? Or it suddenly turns out that Android has a big advantage in this situation, since it’s been clear with him for a long time,
Google, Mozilla and (even earlier) Microsoft say goodbye to RC4 in 2016
News .
In the previous series (in relation to the man-on-the-side DDoS attack on GitHub), we focused on the fact that using HTTPS is good for both the user and the owner of the web service. And this is so, the only problem is that not all HTTPS implementations are equally useful, and some using ancient encryption methods are even harmful. Examples - SSLv3 in a POODLE attack, and generally everything that uses the RC4 cipher. If SSLv3 recently celebrated its 18th anniversary and can now legally buy alcohol, then RC4 has its roots in the 80s of the last century. With regard to the web, it cannot be said yet that a connection using RC4 guarantees a compromised connection. Earlier, the Internet Engineering Task Force noted that theoretical attacks against RC4 are “on the verge of being put into practice.”
Indeed, here is an example of a recent study : rolling back from a normal cipher to RC4 when connecting to the site allows you to decrypt the transmitted cookies (which means to hijack the session) justin 52 hours. To do this, you need to intercept a few cookies, and roughly understanding what will be output, brute force with a slightly higher probability of success than usual. Maybe? Yes, but with reservations. In practice use? But who knows? In the leaks, Snowden hinted that the security services could break RC4 with a high degree of reliability.

In general, the news is positive: the potentially vulnerable encryption algorithm has not even been broken to the end (at least not in bulk), but it will soon be completely blocked. Yes, and now it is used extremely rarely - for Chrome it is 0.13% of all connections (in absolute terms, this is still a lot of
I can not help but dilute optimism with a drop of skepticism. The victims of such upgrades are usually either crooked and few-needed sites, or time-critical critical web services in which it is difficult to change something. It is possible that in February we will see a heated discussion on the forums about how users, after updating the browser, cannot get into some super-secure Internet bank. We will see.
Vulnerabilities in Belkin N600 Routers
News . CERT Advisory .
I really like the news about vulnerabilities in routers. Unlike the computers, smartphones and other devices that we use every day, the router usually gathers dust somewhere in the corner, it has been ignored for years, especially if the router is good and works without failures. At the same time, to be honest, no one knows what is really happening in this black box. Even if you personally rolled custom firmware based on OpenWRT on it. Especially if you are not a techie, but the provider has installed and configured the router. At the same time, the router contains a key to all your data - if you want to go into your home file share, if you want to - intercept traffic, replace Internet banking pages, put ads in Google search results. It is enough to access only once through a single vulnerability or, more often, not even a vulnerability,
At the end of the post, I added a survey on the regularity of updating the firmware of the router. And I myself would like to answer that I myself update the firmware of the router often as soon as a fresh update comes out, but this is not so. In the best case, once every six months, and this is due to the fact that a reminder appears in the web interface of the router. More often I updated the previous router, but only because I tried to defeat the constant freezes. And for a while, my router personally was exposed to this vulnerability that allowed remote access.

So what happened with Belkin routers? They immediately found five vulnerabilities that somehow affect security. For instance:
- Predictable transaction IDs when querying DNS, allowing, in theory, to substitute another server in response, for example, when requesting a firmware update server. Not very scary.
- Default HTTP for important operations, for example, for the same firmware update requests. Scary.
- No default password for the web interface. You can change anything at all, though already inside the local network. The average level of fear.
- Bypassing user password authentication when accessing the web interface. The bottom line is that the browser tells the router whether it is logged in or not, and not vice versa. Replace the value of a pair of parameters in the information transmitted to the router, and the password can be omitted. 76% scary.
- CSRF If you force the user to click on the prepared link, you can remotely change something in the settings of the router. This is especially easy if the password for the web interface is not set. Scary already horror.
Well, ok, we found a lot of holes in the router, which is not the most common among us, well, okay. The problem is that not many people are searching for vulnerabilities in routers, and the fact that they found it at Belkin but could not be found at another manufacturer does not mean that the other manufacturer is more reliable. It’s just that his hands still haven’t reached him. This selection of news makes it clear that everything in this area is very, very bad. Conclusion? You need to protect your local network with at least the means that you have: passwords for the web interface, no WiFi with WEP, disable WPS and other unused features like FTP server and telnet / SSH access, especially from the outside.
What else happened:
US planssanctions against China for cyber espionage. One of the most popular news of the week, but it has a peculiarity: it will not affect the cybersecurity or, if you want, the threat landscape, in any way. Solid policy.
Routers are not the most unsafe devices. Baby monitors and other user-friendly surveillance devices are even worse . Lack of encryption, authorization and other troubles.
We found a way to select groups on Facebook from owners through the Pages Manager application. The vulnerability is closed, the researcher received the promised bug bounty.
 Antiquities:
Antiquities:Andryushka Family
Very dangerous resident "ghost" viruses. COM and EXE files are affected, except for COMMAND.COM, at the start of an infected file (search in directories) and from their TSR copies (when opening, executing, renaming, etc.). Andryushka-3536, upon infection, translates EXE files into COM format (see the VASCINA virus). The virus is introduced in the middle of the file, while the part of the infected file where the virus is recorded is encrypted and appended to the end of the infected file.
They organize counters in the boot sectors of disks and, depending on their value, can destroy several sectors on the C: drive. At the same time, they play the melody and display the text:
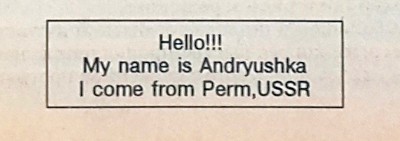
Also contain the text “insufficient memory”. It is quite difficult to work with interrupt handlers: they save part of the int 25h handler in their body, and write their code to the free space (call int 21h). When calling int 25h, the int 25h handler is restored.
Quote from the book "Computer viruses in MS-DOS" by Eugene Kaspersky. 1992 year. Page 23.
Disclaimer: This column reflects only the private opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. That's how lucky.
Only registered users can participate in the survey. Please come in.
How often do you update the firmware of the router?
- 11.3% Once a month or more 26
- 20.4% Twice a year 47
- 16.5% At least once a year 38
- 32.1% Once every couple of years or even less frequently 74
- 25.2% Never updated 58
