Authorization bypass through social networks when connecting to public Wi-Fi
It all started with the fact that I came across an article . Briefly, the video shows how two users connect to the institution’s network and enter the browser, which opens a page with a proposal to log in via VKontakte: you must enter a username / password, only the domain is not vk.com, a typical phishing site. As a result, with such authorization, credentials are transferred to a third party, and an application with unlimited rights is installed, which has round-the-clock access to your page.
If you walk, you can find a large number of companies willing to make a connection to your Wi-Fi through registration in SMM.
For owners of cafes, restaurants, hotels, etc. they offer the collection and analysis of statistics on the attendance of institutions, plus advertising through customer publications. For us, as clients, this results in an invasion of personal space, because they get full access to the page on the social network, including correspondence. Everything is done to track the client, this is confirmed by the picture from the presentation of one such company.
I became interested in how authorization is implemented through SMM, since there are a lot of ways. On the sites of those who provide such services 1 , 2 , 3, offer to collect customer information immediately after registration. I signed up for one such as the owner of a cafe in Moscow. I was given a trial period and instructions for setting up my Wi-Fi router. Everything turned out to be very simple.

They use a banal substitution of IP addresses at the DNS level , when you try to go to some page, they palm off a phishing page with authorization through a social network. The solution seems obvious: put on your device DNS that you trust. But it was decided to check, and pretending to be a fool, I wrote in those I will hold.
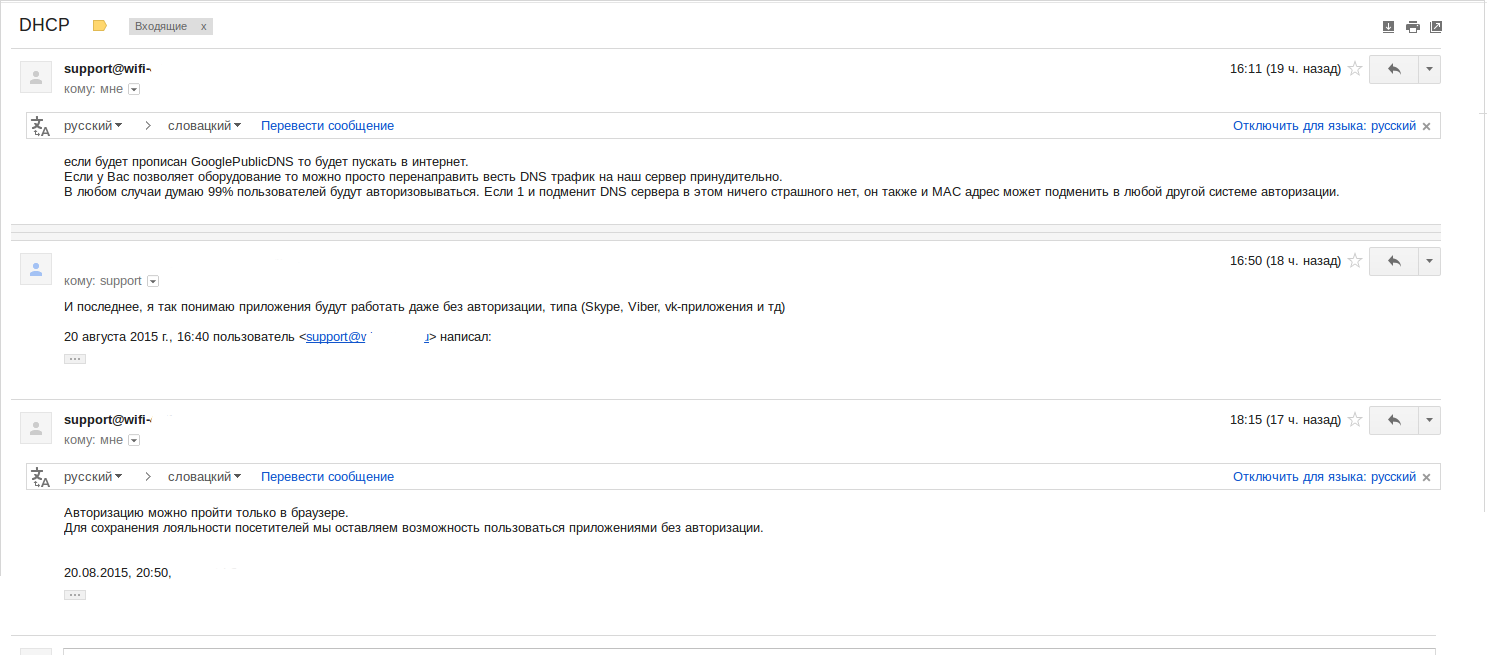
Replacing DNS with a trusted one solves the problems, but the support offers to wrap all traffic on port 53, then the NS request will still go to bad DNS. I doubt that somewhere in the cafe they do it, because for this a normal router is not suitable, but you need something like MikroTik.
If you walk, you can find a large number of companies willing to make a connection to your Wi-Fi through registration in SMM.

For owners of cafes, restaurants, hotels, etc. they offer the collection and analysis of statistics on the attendance of institutions, plus advertising through customer publications. For us, as clients, this results in an invasion of personal space, because they get full access to the page on the social network, including correspondence. Everything is done to track the client, this is confirmed by the picture from the presentation of one such company.

I became interested in how authorization is implemented through SMM, since there are a lot of ways. On the sites of those who provide such services 1 , 2 , 3, offer to collect customer information immediately after registration. I signed up for one such as the owner of a cafe in Moscow. I was given a trial period and instructions for setting up my Wi-Fi router. Everything turned out to be very simple.

They use a banal substitution of IP addresses at the DNS level , when you try to go to some page, they palm off a phishing page with authorization through a social network. The solution seems obvious: put on your device DNS that you trust. But it was decided to check, and pretending to be a fool, I wrote in those I will hold.

Replacing DNS with a trusted one solves the problems, but the support offers to wrap all traffic on port 53, then the NS request will still go to bad DNS. I doubt that somewhere in the cafe they do it, because for this a normal router is not suitable, but you need something like MikroTik.
On a note
- You came to a cafe, bar, etc., connected to Wi-Fi. Go to the browser, and you will be redirected to the authorization page via social networks.
- Exit the browser and check: do the Skype, Vk, viber, etc. applications work? If so, then all you need to bypass authorization is to replace DNS with trusted google public-dns 8.8.8.8 and 8.8.4.4.
- How to do it: Android , iPhone , Windows
- If you have already fallen for a bait, in one of the cafes. Go to the Applications on your page, delete all suspicious ones, change the password.
All beaver.
