The developers of Windows 10 implemented protection against ransomware viruses. It can be bypassed by injection DLL
In Windows 10, a ransomware protection mechanism called Controlled Folder Access has appeared. It prevents files from changing in the specified protected folders by unknown programs. Information Security Researcher from Fujitsu System Integration Laboratories Ltd. discovered a way to bypass this protection using dll injections.
What is the problem
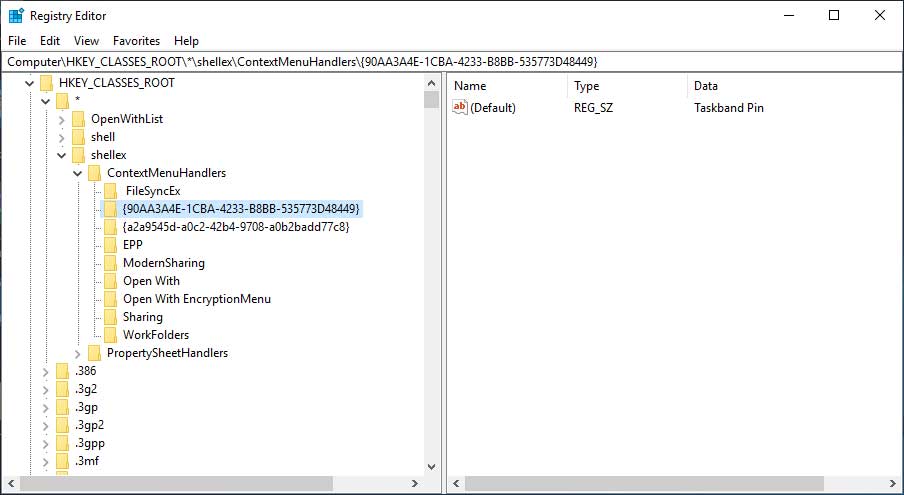
Soya Aoyama managed to inject a malicious DLL into the Windows Explorer — and explorer.exe is in the trusted list of Controlled Folder Access programs. To realize his intention, the researcher used the fact that when launching explorer.exe loads the DLLs found in the registry key HKEY_CLASSES_ROOT \ * \ shellex \ ContextMenuHandlers:
The HKEY_CLASSES_ROOT tree is the "merge" of the register information found in HKEY_LOCAL_MACHINE and HKEY_CURRENT_US. When implementing this "merge", Windows assigns information from HKCU priority. This means that if a key exists in HKCU, then it will take precedence over the same key in HKLM, and this data will flow into the HKEY_CLASSES_ROOT tree.
When starting explorer.exe, Shell32.dll is loaded by default. It is located in the HKEY_LOCAL_MACHINE \ SOFTWARE \ Classes \ CLSID \ {90AA3A4E-1CBA-4233-B8BB-535773D48449} \ InProcServer32 key. To load the malicious DLL into Explorer, Aoyama simply created the HKCU \ Software \ Classes \ CLSID \ {90AA3A4E-1CBA-4233-B8BB-535773D48449} \ InProcServer32 key and set the necessary library for it.
After this, after completing and restarting the explorer.exe process, instead of the Shell32.dll, the program started the DLL created by the hacker.
The results of the study Aoyama shared at the conference DerbyCon:
How to protect
The researcher also found out that many antiviruses, including Windows Defender, Avast, ESET, Malwarebytes Premium and McAfee, do not recognize the attack scheme found by him.
At the same time, according to Aoyama, Microsoft representatives do not believe that he discovered a vulnerability. The researcher sent information about his findings to the company, but there they were told that he was not entitled to any rewards, and they would not release a patch, because an attacker needs access to the victim’s computer and does not exceed access rights.
However, in combination with other vulnerabilities, the attack vector found by Aoyama may be interesting for attackers. Basically, the infrastructure of large companies is built on Windows. Knowing this, the attackers are developing special tools for attacks under this operating system.
Tomorrow, October 18 at 2:00 pm , experts from PT Expert Security Center will disassemble the three hacking tools that allow you to quickly develop an attack in the Windows infrastructure: impacket, CrackMapExec and Koadic. Students will learn how they work, what activity they create in network traffic, and most importantly, how to detect their use in time. The webinar will be of interest to employees of the SOC, blue teams and IT departments.
To participate you must register .
