Logjam - a new vulnerability in TLS
A new vulnerability called Logjam was discovered in various implementations of the TLS protocol. The vulnerability is similar to another called FREAK, which was written about earlier . Logjam also belongs to the “downgrade” type and allows the client to reduce the encryption strength to 512 bits of DH, provided the server supports the DHE_EXPORT cipher, which is set during the “handshake” between the client and server. T. about. it is much easier for an attacker to organize an attack like Man-in-the-Middle (MitM). The vulnerability affects both server software using OpenSSL ( Logjam, FREAK and Upcoming Changes in OpenSSL ) , and web browsers.

Vulnerabilities are affected by web browsers Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, Apple Safari. At the moment, the vulnerability is fixed only in IE, for which the update MS15-055 was released . Other browsers, in turn, are expecting updates, as is the OpenSSL freeware package. The vulnerability is also relevant for OS X, iOS, Android.
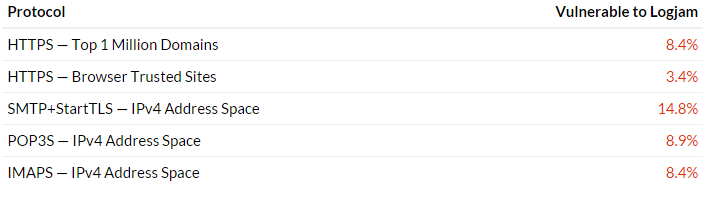
Fig. Statistics of vulnerable systems.
The vulnerability was made possible for the same reason as FREAK, due to a special US law imposing restrictions on the export of strong ciphers ( export restrictions mandated by the US government during the Clinton administration ). That is, when using TLS outside the United States, its strength can be specially reduced.
When establishing a connection between the client and the server, attackers can interfere in this process and quietly switch sides using a weak cipher with 512-bit keys, and then try to decrypt the traffic.
Attackers with the ability to monitor the connection between an end user and a Diffie-Hellman-enabled server that supports the export cipher can inject a special payload into the traffic that downgrades encrypted connections to use extremely weak 512-bit key material.
Actions and corrections required by system administrators can be found at this link weakdh.org/sysadmin.html .
Add. links to research.
The Logjam Attack
weakdh.org
Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice [PDF]
weakdh.org/imperfect-forward-secrecy.pdf
Logjam: the latest TLS vulnerability explained
blog.cloudflare.com/logjam-the-latest-tls-vulnerability-explained
Logjam is latest security flaw to affect secure communication protocols
www.symantec.com / connect / blogs / logjam-latest-security-flaw-affect-secure-communication-protocols
https-crippling attack threatens tens of thousands of web and mail servers
arstechnica.com/security/2015/05/https-crippling-attack-threatens -tens-of-thousands-of-web-and-mail-servers

Vulnerabilities are affected by web browsers Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, Apple Safari. At the moment, the vulnerability is fixed only in IE, for which the update MS15-055 was released . Other browsers, in turn, are expecting updates, as is the OpenSSL freeware package. The vulnerability is also relevant for OS X, iOS, Android.

Fig. Statistics of vulnerable systems.
The vulnerability was made possible for the same reason as FREAK, due to a special US law imposing restrictions on the export of strong ciphers ( export restrictions mandated by the US government during the Clinton administration ). That is, when using TLS outside the United States, its strength can be specially reduced.
When establishing a connection between the client and the server, attackers can interfere in this process and quietly switch sides using a weak cipher with 512-bit keys, and then try to decrypt the traffic.
Attackers with the ability to monitor the connection between an end user and a Diffie-Hellman-enabled server that supports the export cipher can inject a special payload into the traffic that downgrades encrypted connections to use extremely weak 512-bit key material.
Actions and corrections required by system administrators can be found at this link weakdh.org/sysadmin.html .
Add. links to research.
The Logjam Attack
weakdh.org
Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice [PDF]
weakdh.org/imperfect-forward-secrecy.pdf
Logjam: the latest TLS vulnerability explained
blog.cloudflare.com/logjam-the-latest-tls-vulnerability-explained
Logjam is latest security flaw to affect secure communication protocols
www.symantec.com / connect / blogs / logjam-latest-security-flaw-affect-secure-communication-protocols
https-crippling attack threatens tens of thousands of web and mail servers
arstechnica.com/security/2015/05/https-crippling-attack-threatens -tens-of-thousands-of-web-and-mail-servers
