Conference BLACK HAT USA. A botnet of a million browsers. Part 2
- Transfer
Conference BLACK HAT USA. A botnet of a million browsers. Part 1
Matt Johanson: I'll show you how to enter this code now. There are many ad networks, but we chose this one because it allows us to do what we want.
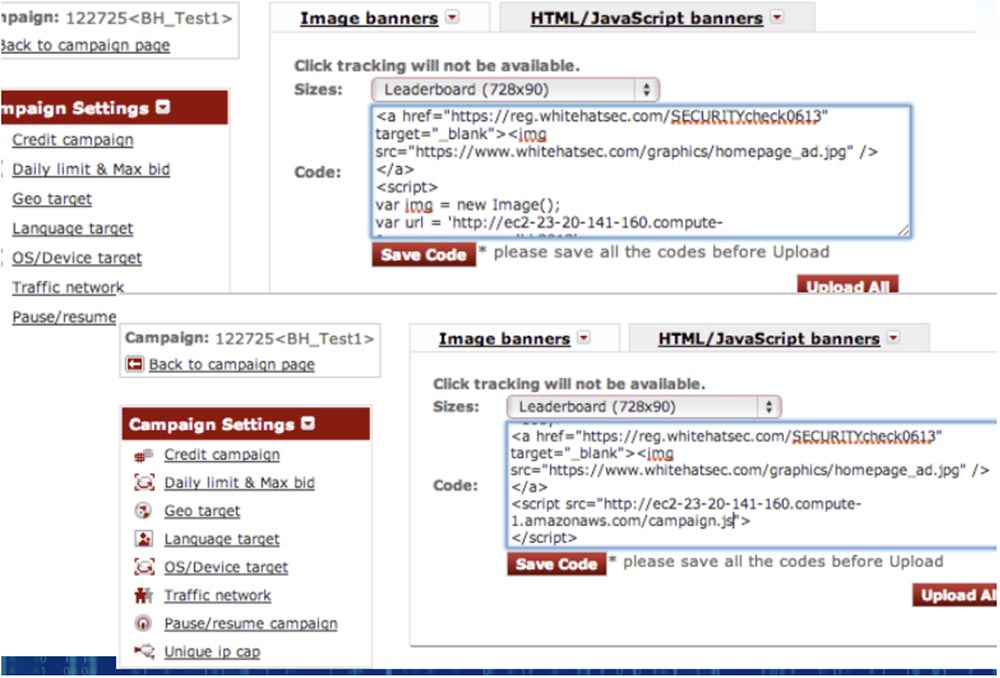
You can choose a banner image of a sufficiently large size, insert it here and assign it a URL, so that after clicking on the banner the user will go to the desired site. The owners of this ad network provide the option of HTML JavaScript, this sounds very good.
We started with what is shown at the top of the slide and had to go through the entire approval process, which was probably the most difficult part of our research. This happened not for the reasons you thought about, but because they do not very well represent the meaning of JavaScript and do not care much about it. In fact, they made sure that the ad looked beautiful and worked like an advertisement, so I couldn’t continue to walk our invisible path and just mark our mystical JavaScript code somewhere in the background.
We inserted a script for executing the code that Jeremy designed, you see it in the text field in the bottom window, and it was approved by the advertisers without any problems. However, we wanted to be able to reconfigure it at any time in order to diversify research, because things like URLs change frequently. But if we wanted to try something new, we would have to go through the approval process again. It doesn’t take much time, but it’s just annoying, because sometimes they approved it, and sometimes they didn’t like it and we had to make changes.
For example, once the email application opened the script tags, all the JavaScript code disappeared, and I had to move it. I had to explain to them why they need to put less than 1 character here, and 1 more sign there, after which they said that the ads were not displayed properly, in general, it was fun.
So, we placed the code directly in the advertising banner, having entered there only the source script, where our file was located, which we could change at any time without any approval from the owners of the advertising network. Thus, even if they somehow hired people versed in the static analysis of JavaScript code, we could just change our file to quite benign JavaScript. So it would be very difficult to detect our frauds with this method of introducing malicious code.
The next slide shows our ad banner.
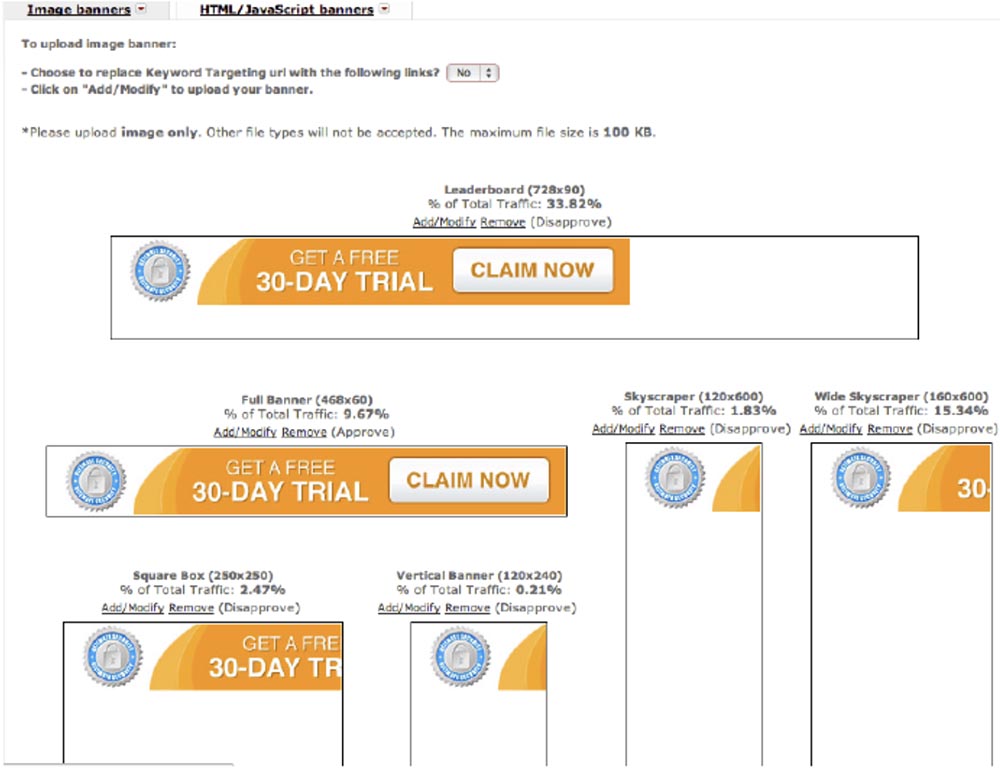
They approved one of these design options. I was too lazy to look for other images, so I just took this idea from the WhiteHat corporate site. The text is very simple: “Get a free 30-day trial period, ask now!”, So click on the banner, it's completely free!
Jeremy Grossman: inside the banner code was the script tag for the location of our campaign.js file at: ec2-23-20-141-160.compute-1.amazonaws.com/campaign.js , which looked like this:
We could change it at any time and without any approval. We did not know how long these browsers had to view our ads in this particular ad network, so instead of 100, 200 or 300 views, we immediately stopped at 10,000, hoping for the best.
Matt Johanson: Starting small, we wanted to see if we could get users to contact us. We could see it at our end of the network, we saw all the people who went through our link, because the requests came from their browsers and we could determine their IP addresses. At first we wanted to see how we deployed this thing and how the code works, because it was not the service where you pay for clicks, we paid for the guaranteed time of views.
Jeremy Grossman:Here is another screenshot, this is a “light” demonstration, which we prepared specifically for BlackHat.

Below on the left, you see the Amazon AWS server, which is still running right now. The initial metric is shown below: the server’s operating time in the Matt ad network is 8 minutes, the total number of accesses is 4130, this is not the number of unique visitors to the site, but actual web requests with a total traffic volume of 1.9 MB, the number of simultaneous requests is 5. We see the protocol of registration of metrics, logs of the web server, as well as the number of minutes of real time visits to the site that we paid.
Matt Johanson: if you look at the next slide, you can see a jump that occurred between 8 and 10 minutes - the total number of accesses has increased to 15 thousand.

All this can make only 1 ad posted on the advertising network. If you can simply add more funds to the ad network, it will look like a “peak in the valley”. I want to say that all this was made possible thanks to the purchased browser minutes, and within 10 minutes of the server’s work with the advertising network, we received about 15,000 requests.
Then we noticed an interesting thing. Let me remind you that we did not have a traditional advertising network, we paid for the browser minutes, that is, someone provided us with a browser so that it became part of this magical network, actually selling us the time of its browser and the time of its processor. We decided to see what is happening in the background of this network, what browsers are used there, we wanted to play around with Firefox and the like.
And here we found that a whole bunch of calls from PhantomJS come into our network. Who is familiar with PhantomJS? I see only a few people.
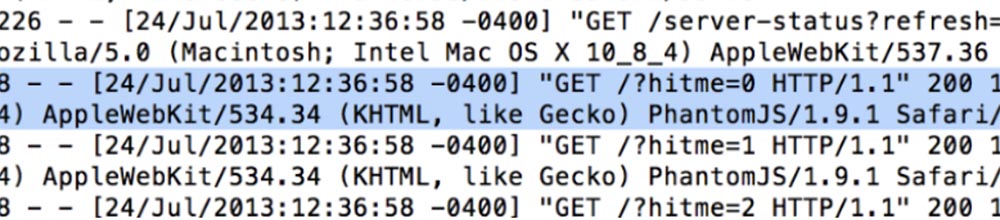
PhantomJS is a “headless” browser, that is, a browser that can be run on devices without a screen, such as a server. That is, it is not someone sitting on the Internet and clicking on the browser tabs on your desktop, but a robot. It can be used for unit tests and it is run from the command line. That is, someone led their game in our system, trying to get a minute. So other people are abusing these in various ways, and it was fun to watch. We made sure that the minutes are not real people clicking on their browser, but PhantomJS bots.
Jeremy Grossman:The following slides show the development of the process: in 15 minutes we received 28,000 requests, in 20 minutes almost 44,000 requests, in 22 minutes the number of requests reached 61500.
Matt Johanson: you may notice that the total traffic is very small, we just send them a URL -address that does not exist, so 8.5 MB in 20 minutes means that users simply received a 404 error.
Jeremy Grossman: almost 26 minutes, and we get 82 thousand views, more than 35 minutes, 9 simultaneous requests and almost 102 thousand access
Matt Johanson:we saved our money to the end in order to make a decisive blow with our “impressions”, which cost almost $ 20 after the ad network lasts from 30 to 45 minutes in the usual way. Actually, I intended to spend a maximum of $ 10 per day on this research. So, after 43 minutes, we had 255 requests, 133.5 thousand accesses, and our network reached its peak in 54 minutes — 256 requests and 244425 visits.

Look at the simultaneous requests we are targeting - 255, the Apache server will not work faster, then in the screenshots you can see that the server does not want to reboot to update the metrics data. After the number of hits reached 130 thousand, and the traffic was 36 MB, we decided to slightly increase the server bandwidth and indicated to them the load of the “Aplication Security Specialist (ASS)” application, so now we have even more certified “asses” in the field of security. After that, the traffic volume increased dramatically to 117 MB. After 55 minutes we had 256 thousand visits with traffic of 253 MB.
Jeremy Grossman:finally, after 59 minutes and 48 seconds, that is, an hour after the server started and 20 minutes after the image was loaded, the amount of traffic reached 1 GB. After that we decided to just leave it for a while, for example, for seven hours, let it work.
On the next slide, you see the result of our system after 8 hours: more than 4 million visits, 114.7 GB of traffic.

Matt Johanson:we made the same mistake as the first time we - we went for lunch. So before we started playing the advertising network, you know, we had, for example, 30,000 views per heap of hours, and we were still messing with our code, so we thought we would get ten thousand more views during lunch time. When we returned, we looked, aha, well, a little more than 30 thousand, but then we realized that not 30 thousand, but an order of magnitude more - 300,000 views!
If we spent more money, we would get a lot more “impressions” much faster, but in our case, after 18 hours 42 minutes of the server’s operation, we had almost a million views and 240 GB of traffic, so hosting Amazon cost us more than breaking into advertising network.
Jeremy Grossman:finally, after 1 day and 6 hours with traffic of 241 GB, we had almost one and a half million views. As can be seen from this slide, at that time we spent almost all our minutes in the system, and decided that we do not need more minutes. However, we didn’t know how things would go further and what would happen in the middle of the night, so we started e-commerce for BlackHat and bought another minute.
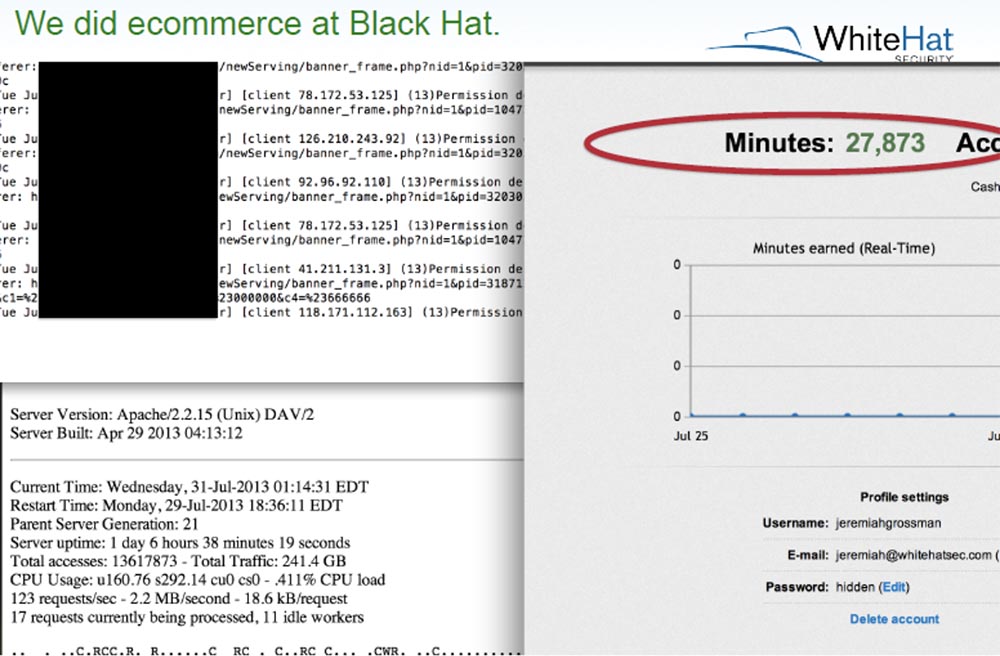
Matt Johanson: I do not recommend this to you, because I had to break my rule not to spend more than $ 10 a day.

Jeremy Grossman: now we had almost 250 GB of traffic. You see lines running fast on the screen, these are Apache server logs, then you see the screenshot “This page is not available” because the server did not cope with the load and died safely. We could go through all the logs to the end, but it would take too much time. So, for all the fun, we paid only $ 20 and at the end received a classic DoS service refusal, expressed in the failure of the image upload request. After that, I just turned off the loading of images, simply resetting the settings. I could turn it on again, but I don't want to show you my root password.
Matt Johanson:notice we turned off the image because we noticed that the actual visits slowed down when we provided the image. We have not even exhausted the entire limit of compounds. We did not use Firefox for this hacking, we only had 6 simultaneous connections per browser. We were very nervous, so we didn’t press this big red button to start the FTP traversal, because we didn’t know what might happen. We settled on legal methods, but even the use of legal methods impressed us enough.

Therefore, even without trying hacker methods and not spending a lot of money, you can achieve decent results. The slide shows that after 1 day 20 hours and 40 minutes, 243 GB of traffic was spent on views, that is, its volume remained almost unchanged, since the pictures were no longer loaded. When we met here this morning before the conference, I thought we would have about 15 million, so now, in a few hours, we just got 20 million page views with a 404 error.
Jeremy Grossman:the only reason we were unable to “pump” more traffic was the server's performance. We could use a more powerful platform and achieve 100 million or billion views, but for one relatively slow Apache server this is an impossible task.
Matt Johanson: so our results are not particularly impressive, but you guys can get an idea of the scaling process, so causing damage to normal sites will not require so much money.
Jeremy Grossman: Well, now that we’ve achieved this result, we’ll try to bypass the browser’s limitations on the number of connections using FTP, run our script and see what happens.
Matt Johanson:Yes, a lot of people come to Las Vegas to spend their money on slot machines, and we spend our money on advertising networks here.
Jeremy Grossman: So, we looped 400 FTP connections to the Amazon server, so who knows what will happen now?
We got the server metric, then disappeared again, the web page is again inaccessible, but you see how quickly the lines of the log entries flash. Let's just reboot, because the server is actually dead and the browser takes time out.
Matt Johanson:we do not know how FTP will behave in relation to ad networks and we don’t know what would have happened if it was not bots that were used here, but real users' browsers. I hope that you guys understand that we didn’t hack anyone, but simply figure out how the network works, for which purpose we rented servers. We fully complied with the legal side of the issue, and you got ideas on how to have fun in advertising networks.
We didn’t even try to break the law, went through this approval process, we had relatively benign, and not malicious JavaScript, we didn’t even touch “adult” ad networks, although you saw that they often don't care what happens to ad banners.
Jeremy Grossman: I heard a good question - where do Apache logs come from?
Indeed, by default there are no logs in Apache. Perhaps I will tell about it later. We have Austin Apache, I just downloaded and installed it. Let me run it - you see, there are no logs here, this is a local server. On the Amazon server, you see error 408 — the server is not responding because the page request timeout has been exceeded. HTTP sending is not used here, but port 80 is still open and holds many connections. Let's return to our slides - here we are fine, we can close them.
So, you saw what we did, staying on the right side of the law. Obviously, as Matt said, we could go much further, as it usually happens in the world of information security. Advertising networks that you know about have a large number of software developers. But believe us, in reality they are not software developers, but simply manage their ad networks on their advertising sites.

One of the tools that they widely use is OpenX - ad server, or ad engine. This software is open source.
It is used by many ad networks, and as is usually the case, a few weeks ago someone discovered serious vulnerabilities in it that put millions of advertising platform users at risk. This ad server can be hacked by executing random PHP code that creates the conditions for an XSS cross-site scripting attack.
So if you do not want to pay them your money, but you just want to use the advertising network, you can do it by simply hacking it and uploading an exploit there, so that you can control everyone who views your advertisement.
Matt Johanson:we actually just invested money in the slot machine that placed our ad, and it is very difficult to find out who made this ad, which is an iframe. We investigated how iframe destroys the code and bothered to hack the browser, but the point of our research was that we tried to use the browser so that other people hacked themselves with their own hands.
Jeremy Grossman: this study will continue, we use our Amazon server and try to gather together some of our partners to try to attack sites with DDoS protection and see how much traffic we can send to them, because we are not defending, but attacking - This is the essence of our research.
Matt Johanson:we will try to see how you can crack the ad network hash, so we have metrics that give a good idea that javascript can do this as quickly as we want. We can relate this to the dollar amount to find out how many MD5 hashes can be cracked for 50 cents.

Jeremy Grossman: I will repeat again - we can mobilize a million browsers, perhaps not at the same time, but you can get this million browsers for about $ 500 and create a powerful botnet.
I have worked enough in the field of web security, and I remember that I said a long time ago that we have to hack the Internet to ensure its security, hack existing business models on the Internet, to know from what and how to protect them. Dan Kaminsky told me on December 21, 2010: “No one can hack the Internet, dude. Not now, not ever. ” Until now, he was right.
But now we see the problem. I do not know whose problem is ad networks, or the problem of browser vendors, or the problem of site owners, but it does exist. And we do not know whose responsibility it is and who should fix it.
Matt Johanson:we showed you what you can do by simply uploading a picture to the advertising network, but we did not go further, we did not cause any damage to people, although we had all the possibilities for this. And we do not know how to protect against this - we just showed you a mechanism that attackers can use.
Jeremy Grossman: so, as you can see, there is a reason why browsers suggest using an ad blocker. Turn on the ad blocker and your browser will not be vulnerable to this type of attack.
Matt Johanson: or as an option - disconnect from the Internet altogether.
Jeremy Grossman: I hear the question of how much an Amazon server costs us - for now, probably about $ 100.
Matt Johanson:Today, when we really dumped money into the advertising network, we paid $ 75 before our performance, and I tried to squeeze out of them everything that was possible.
And I will answer the last question about the IP address - when we received the approval of our banner, we saw the IP address of the person who made this approval, but he could not see our IP address and could not know anything about us except the email address mail.
Thanks to everyone who came to listen to us!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Matt Johanson: I'll show you how to enter this code now. There are many ad networks, but we chose this one because it allows us to do what we want.

You can choose a banner image of a sufficiently large size, insert it here and assign it a URL, so that after clicking on the banner the user will go to the desired site. The owners of this ad network provide the option of HTML JavaScript, this sounds very good.
We started with what is shown at the top of the slide and had to go through the entire approval process, which was probably the most difficult part of our research. This happened not for the reasons you thought about, but because they do not very well represent the meaning of JavaScript and do not care much about it. In fact, they made sure that the ad looked beautiful and worked like an advertisement, so I couldn’t continue to walk our invisible path and just mark our mystical JavaScript code somewhere in the background.
We inserted a script for executing the code that Jeremy designed, you see it in the text field in the bottom window, and it was approved by the advertisers without any problems. However, we wanted to be able to reconfigure it at any time in order to diversify research, because things like URLs change frequently. But if we wanted to try something new, we would have to go through the approval process again. It doesn’t take much time, but it’s just annoying, because sometimes they approved it, and sometimes they didn’t like it and we had to make changes.

For example, once the email application opened the script tags, all the JavaScript code disappeared, and I had to move it. I had to explain to them why they need to put less than 1 character here, and 1 more sign there, after which they said that the ads were not displayed properly, in general, it was fun.
So, we placed the code directly in the advertising banner, having entered there only the source script, where our file was located, which we could change at any time without any approval from the owners of the advertising network. Thus, even if they somehow hired people versed in the static analysis of JavaScript code, we could just change our file to quite benign JavaScript. So it would be very difficult to detect our frauds with this method of introducing malicious code.
The next slide shows our ad banner.

They approved one of these design options. I was too lazy to look for other images, so I just took this idea from the WhiteHat corporate site. The text is very simple: “Get a free 30-day trial period, ask now!”, So click on the banner, it's completely free!
Jeremy Grossman: inside the banner code was the script tag for the location of our campaign.js file at: ec2-23-20-141-160.compute-1.amazonaws.com/campaign.js , which looked like this:
for (var i = 0; i < 10000; i++) {
var img = newImage();
var url = 'http://<amazon_aws>/iclick/id?' + i;
img.src = url;
}We could change it at any time and without any approval. We did not know how long these browsers had to view our ads in this particular ad network, so instead of 100, 200 or 300 views, we immediately stopped at 10,000, hoping for the best.
Matt Johanson: Starting small, we wanted to see if we could get users to contact us. We could see it at our end of the network, we saw all the people who went through our link, because the requests came from their browsers and we could determine their IP addresses. At first we wanted to see how we deployed this thing and how the code works, because it was not the service where you pay for clicks, we paid for the guaranteed time of views.
Jeremy Grossman:Here is another screenshot, this is a “light” demonstration, which we prepared specifically for BlackHat.

Below on the left, you see the Amazon AWS server, which is still running right now. The initial metric is shown below: the server’s operating time in the Matt ad network is 8 minutes, the total number of accesses is 4130, this is not the number of unique visitors to the site, but actual web requests with a total traffic volume of 1.9 MB, the number of simultaneous requests is 5. We see the protocol of registration of metrics, logs of the web server, as well as the number of minutes of real time visits to the site that we paid.
Matt Johanson: if you look at the next slide, you can see a jump that occurred between 8 and 10 minutes - the total number of accesses has increased to 15 thousand.

All this can make only 1 ad posted on the advertising network. If you can simply add more funds to the ad network, it will look like a “peak in the valley”. I want to say that all this was made possible thanks to the purchased browser minutes, and within 10 minutes of the server’s work with the advertising network, we received about 15,000 requests.
Then we noticed an interesting thing. Let me remind you that we did not have a traditional advertising network, we paid for the browser minutes, that is, someone provided us with a browser so that it became part of this magical network, actually selling us the time of its browser and the time of its processor. We decided to see what is happening in the background of this network, what browsers are used there, we wanted to play around with Firefox and the like.
And here we found that a whole bunch of calls from PhantomJS come into our network. Who is familiar with PhantomJS? I see only a few people.

PhantomJS is a “headless” browser, that is, a browser that can be run on devices without a screen, such as a server. That is, it is not someone sitting on the Internet and clicking on the browser tabs on your desktop, but a robot. It can be used for unit tests and it is run from the command line. That is, someone led their game in our system, trying to get a minute. So other people are abusing these in various ways, and it was fun to watch. We made sure that the minutes are not real people clicking on their browser, but PhantomJS bots.
Jeremy Grossman:The following slides show the development of the process: in 15 minutes we received 28,000 requests, in 20 minutes almost 44,000 requests, in 22 minutes the number of requests reached 61500.
Matt Johanson: you may notice that the total traffic is very small, we just send them a URL -address that does not exist, so 8.5 MB in 20 minutes means that users simply received a 404 error.
Jeremy Grossman: almost 26 minutes, and we get 82 thousand views, more than 35 minutes, 9 simultaneous requests and almost 102 thousand access
Matt Johanson:we saved our money to the end in order to make a decisive blow with our “impressions”, which cost almost $ 20 after the ad network lasts from 30 to 45 minutes in the usual way. Actually, I intended to spend a maximum of $ 10 per day on this research. So, after 43 minutes, we had 255 requests, 133.5 thousand accesses, and our network reached its peak in 54 minutes — 256 requests and 244425 visits.

Look at the simultaneous requests we are targeting - 255, the Apache server will not work faster, then in the screenshots you can see that the server does not want to reboot to update the metrics data. After the number of hits reached 130 thousand, and the traffic was 36 MB, we decided to slightly increase the server bandwidth and indicated to them the load of the “Aplication Security Specialist (ASS)” application, so now we have even more certified “asses” in the field of security. After that, the traffic volume increased dramatically to 117 MB. After 55 minutes we had 256 thousand visits with traffic of 253 MB.
Jeremy Grossman:finally, after 59 minutes and 48 seconds, that is, an hour after the server started and 20 minutes after the image was loaded, the amount of traffic reached 1 GB. After that we decided to just leave it for a while, for example, for seven hours, let it work.
On the next slide, you see the result of our system after 8 hours: more than 4 million visits, 114.7 GB of traffic.

Matt Johanson:we made the same mistake as the first time we - we went for lunch. So before we started playing the advertising network, you know, we had, for example, 30,000 views per heap of hours, and we were still messing with our code, so we thought we would get ten thousand more views during lunch time. When we returned, we looked, aha, well, a little more than 30 thousand, but then we realized that not 30 thousand, but an order of magnitude more - 300,000 views!
If we spent more money, we would get a lot more “impressions” much faster, but in our case, after 18 hours 42 minutes of the server’s operation, we had almost a million views and 240 GB of traffic, so hosting Amazon cost us more than breaking into advertising network.
Jeremy Grossman:finally, after 1 day and 6 hours with traffic of 241 GB, we had almost one and a half million views. As can be seen from this slide, at that time we spent almost all our minutes in the system, and decided that we do not need more minutes. However, we didn’t know how things would go further and what would happen in the middle of the night, so we started e-commerce for BlackHat and bought another minute.

Matt Johanson: I do not recommend this to you, because I had to break my rule not to spend more than $ 10 a day.

Jeremy Grossman: now we had almost 250 GB of traffic. You see lines running fast on the screen, these are Apache server logs, then you see the screenshot “This page is not available” because the server did not cope with the load and died safely. We could go through all the logs to the end, but it would take too much time. So, for all the fun, we paid only $ 20 and at the end received a classic DoS service refusal, expressed in the failure of the image upload request. After that, I just turned off the loading of images, simply resetting the settings. I could turn it on again, but I don't want to show you my root password.
Matt Johanson:notice we turned off the image because we noticed that the actual visits slowed down when we provided the image. We have not even exhausted the entire limit of compounds. We did not use Firefox for this hacking, we only had 6 simultaneous connections per browser. We were very nervous, so we didn’t press this big red button to start the FTP traversal, because we didn’t know what might happen. We settled on legal methods, but even the use of legal methods impressed us enough.

Therefore, even without trying hacker methods and not spending a lot of money, you can achieve decent results. The slide shows that after 1 day 20 hours and 40 minutes, 243 GB of traffic was spent on views, that is, its volume remained almost unchanged, since the pictures were no longer loaded. When we met here this morning before the conference, I thought we would have about 15 million, so now, in a few hours, we just got 20 million page views with a 404 error.
Jeremy Grossman:the only reason we were unable to “pump” more traffic was the server's performance. We could use a more powerful platform and achieve 100 million or billion views, but for one relatively slow Apache server this is an impossible task.
Matt Johanson: so our results are not particularly impressive, but you guys can get an idea of the scaling process, so causing damage to normal sites will not require so much money.
Jeremy Grossman: Well, now that we’ve achieved this result, we’ll try to bypass the browser’s limitations on the number of connections using FTP, run our script and see what happens.
Matt Johanson:Yes, a lot of people come to Las Vegas to spend their money on slot machines, and we spend our money on advertising networks here.
Jeremy Grossman: So, we looped 400 FTP connections to the Amazon server, so who knows what will happen now?
We got the server metric, then disappeared again, the web page is again inaccessible, but you see how quickly the lines of the log entries flash. Let's just reboot, because the server is actually dead and the browser takes time out.
Matt Johanson:we do not know how FTP will behave in relation to ad networks and we don’t know what would have happened if it was not bots that were used here, but real users' browsers. I hope that you guys understand that we didn’t hack anyone, but simply figure out how the network works, for which purpose we rented servers. We fully complied with the legal side of the issue, and you got ideas on how to have fun in advertising networks.
We didn’t even try to break the law, went through this approval process, we had relatively benign, and not malicious JavaScript, we didn’t even touch “adult” ad networks, although you saw that they often don't care what happens to ad banners.
Jeremy Grossman: I heard a good question - where do Apache logs come from?
Indeed, by default there are no logs in Apache. Perhaps I will tell about it later. We have Austin Apache, I just downloaded and installed it. Let me run it - you see, there are no logs here, this is a local server. On the Amazon server, you see error 408 — the server is not responding because the page request timeout has been exceeded. HTTP sending is not used here, but port 80 is still open and holds many connections. Let's return to our slides - here we are fine, we can close them.
So, you saw what we did, staying on the right side of the law. Obviously, as Matt said, we could go much further, as it usually happens in the world of information security. Advertising networks that you know about have a large number of software developers. But believe us, in reality they are not software developers, but simply manage their ad networks on their advertising sites.

One of the tools that they widely use is OpenX - ad server, or ad engine. This software is open source.
It is used by many ad networks, and as is usually the case, a few weeks ago someone discovered serious vulnerabilities in it that put millions of advertising platform users at risk. This ad server can be hacked by executing random PHP code that creates the conditions for an XSS cross-site scripting attack.
So if you do not want to pay them your money, but you just want to use the advertising network, you can do it by simply hacking it and uploading an exploit there, so that you can control everyone who views your advertisement.
Matt Johanson:we actually just invested money in the slot machine that placed our ad, and it is very difficult to find out who made this ad, which is an iframe. We investigated how iframe destroys the code and bothered to hack the browser, but the point of our research was that we tried to use the browser so that other people hacked themselves with their own hands.
Jeremy Grossman: this study will continue, we use our Amazon server and try to gather together some of our partners to try to attack sites with DDoS protection and see how much traffic we can send to them, because we are not defending, but attacking - This is the essence of our research.
Matt Johanson:we will try to see how you can crack the ad network hash, so we have metrics that give a good idea that javascript can do this as quickly as we want. We can relate this to the dollar amount to find out how many MD5 hashes can be cracked for 50 cents.

Jeremy Grossman: I will repeat again - we can mobilize a million browsers, perhaps not at the same time, but you can get this million browsers for about $ 500 and create a powerful botnet.
I have worked enough in the field of web security, and I remember that I said a long time ago that we have to hack the Internet to ensure its security, hack existing business models on the Internet, to know from what and how to protect them. Dan Kaminsky told me on December 21, 2010: “No one can hack the Internet, dude. Not now, not ever. ” Until now, he was right.
But now we see the problem. I do not know whose problem is ad networks, or the problem of browser vendors, or the problem of site owners, but it does exist. And we do not know whose responsibility it is and who should fix it.
Matt Johanson:we showed you what you can do by simply uploading a picture to the advertising network, but we did not go further, we did not cause any damage to people, although we had all the possibilities for this. And we do not know how to protect against this - we just showed you a mechanism that attackers can use.
Jeremy Grossman: so, as you can see, there is a reason why browsers suggest using an ad blocker. Turn on the ad blocker and your browser will not be vulnerable to this type of attack.
Matt Johanson: or as an option - disconnect from the Internet altogether.
Jeremy Grossman: I hear the question of how much an Amazon server costs us - for now, probably about $ 100.
Matt Johanson:Today, when we really dumped money into the advertising network, we paid $ 75 before our performance, and I tried to squeeze out of them everything that was possible.
And I will answer the last question about the IP address - when we received the approval of our banner, we saw the IP address of the person who made this approval, but he could not see our IP address and could not know anything about us except the email address mail.
Thanks to everyone who came to listen to us!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
