Security Week 37: Facebook, Twitter and Inflatable Bugs
Near-marketing marketers now like to discuss that absolutely any message about a new product, technology or event is perceived better if there is a blockchain in it. Or machine learning algorithms. Similarly, any message in the field of information security becomes more resonant if it mentions the social network Facebook. The information reality, heated by the scandal over the privacy of user data, is such that if you put the words “facebook” and “vulnerability” in one application, they react and cause an uncontrolled increase in clicks.
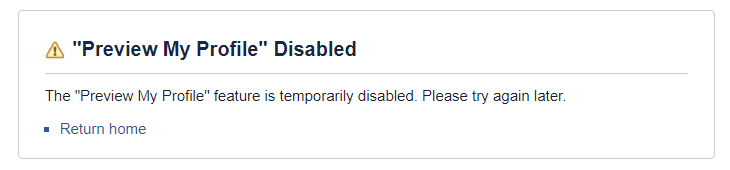
Well, let's surrender to the will of this incomprehensible chemistry and talk about what happened on Facebook last week. And at the same time remember what happened last week at Twitter. And in that case, and in the other, there were microscopic bugs, independently discovered by the company's specialists, successfully closed with the maximum number of precautions, the public was notified. But Facebook’s “problem” is being discussed by Facebook, but almost nobody noticed the bug on Twitter. How so? Now we will understand.
News . A detailed report of the social network about the event.
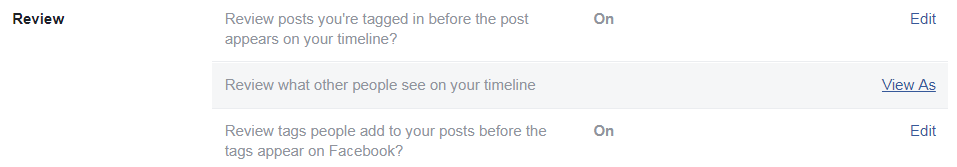
And that's what. Facebook has (more precisely, it was, it is not working now, see the screenshot at the beginning of the post) View As function . Available to all users, she allowed to see her profile as if another person was looking at him. Because of the numerous privacy settings, this is quite a useful feature: it allows you to understand what outsiders see on your page and what doesn't.
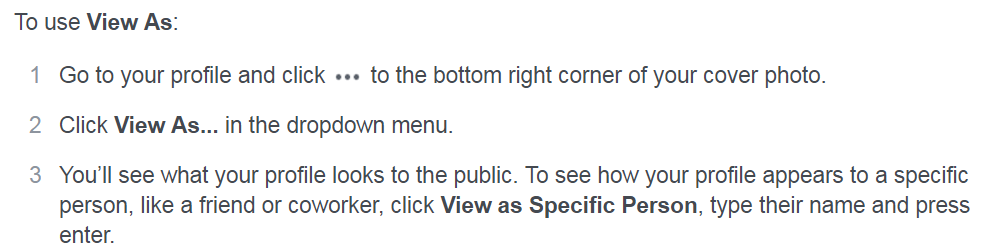
An important point: the page can be viewed with the "eyes" of some random visitor, and you can show how it looks from the point of view of a particular user, with first and last name. It is this precision and summed up the developers under the monastery.
According to Pedro Kanauati, Facebook’s vice president of engineering, security and privacy, there are three different vulnerabilities. First, there was a bug in the View As feature itself. In theory, it should switch the Facebook context to another user in “read only” mode, in the sense of “just viewing the user's page under which you are logged in.” In fact, in the View As mode, the field for posting was also generated. Secondly, this field did not work (correctly) in all cases, except one: when you want to congratulate a person on his birthday and post a video. Thirdly, when posting a video, the code for downloading this video itself generated a token, which could also be used as an access token from a mobile application.
That is, the scenario from the side of the attacker is approximately as follows. You create a profile or change the settings of an existing one so that you have a birthday today (wiii!). Using the View As function, open your profile on behalf of another user. When displaying a profile on behalf of another user, he (this other user) is invited to wish you a happy birthday and upload a cute video. When loading a video, a token is generated. You take this token from the page code and enter the mobile application on behalf of and with the rights of another user.
Next begin a little speculation. For example, do you need to be friends with the person on whose behalf you want to “see” your page? Judging by the descriptions (now broken) features on third-party sites - it is necessary. Now remember, how long have you been asked to become friends of you who are not known to you, but extremely persistent people? Having access to the token of one user, you can steal access keys to the account of one of his / her friends. And so on, theoretically, down to the scale limited by the theory of six handshakes. That is almost unlimited scale.
Cool, yeah? Interestingly, the Facebook message, published on Friday evening (in Moscow), was anticipated by complaintsusers that they were logged out both from Facebook itself and from other services for access to which the social network account was used. These were the very precautions that Facebook applied to affected users.
Or supposedly affected? We must pay tribute to the experts of Facebook - they told about the detected vulnerabilities in the most detailed and operational manner. On September 16, according to them, they noticed suspicious activity, on the 25th it became clear that what was happening, on September 28, the information was made public - immediately after the “unlocking” of the victims (which made any stolen tokens useless). But how exactly these victims suffered - here Facebook was not very specific. Perhaps they still do not know for sure.
It is known that the vulnerability appeared in the service code in July 2017. Last week, Facebook forcedly logged out 90 million users. Of these, 40 million are those for which the View As feature was applied, that is, someone on their behalf was looking at their page, not necessarily with criminal intent. Another 50 million are those affected by vulnerability. Since "affected" something? In decodingpress briefing there is more information: about 50 million Facebook users know that their tokens have been extracted. That is (speculations!) Some people used the View As feature on their birthday, and then (maybe!) They came from the same IP to a different account. And most likely, that “suspicious activity” of September 16, which was mentioned by representatives of the social network, was an attempt of mass automated exploitation of the bug, which was stopped in just over a week.
In general, Facebook has responded very well to the problem. He shared (as he could) detailed information, took action against the victims (actual or potential). 50 (or 90) million people on Facebook is not much. However, given the concern about the privacy of personal data given to social networks, it is understandable and heightened attention to this incident. There are two positive moments. First, the passwords were not stolen, and if some tools of unauthorized access to other accounts were available, they were destroyed by “carpet unlocking”. Secondly, even if you were among the alleged victims, and even if someone really accessed your data, in their hands turned out to be not all that Facebook knew about you. Because the real knowledge of Facebook users, even with the users themselvesnot divided .
And Twitter last week was lucky.
News . Technical report social network.
In a sense, the bug found on Twitter is similar to what we found on Facebook. The hole was found in the API, which allows companies to communicate with customers - in general, it is an interface for sending mass messages or receiving private messages. If you communicated with someone using this API, then under certain circumstances your correspondence could be in the hands of a third party.
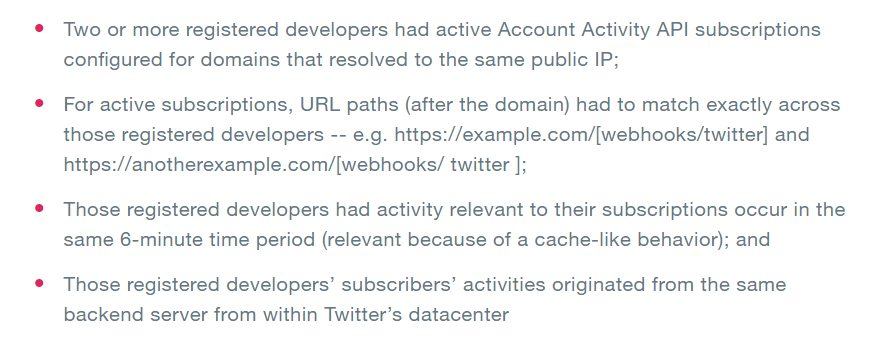
Okay, even in this form it does not sound frightening. Practice is even more boring. First, only registered Twitter partners can use the API. Secondly, in order for the bug to work and the private messages go wrong , both partners must (a) sit on the same IP, (b) work with the API using the URL that fully matches the slash(www.xxx.com/twitter_msg and www.yyy.com/twitter_msg is a coincidence), (c) unsuccessful access to Twitter servers in one piece of time, limited to six minutes.
When all this coincides, thecarriage turns into a pumpkin, a poorly tuned Twitter cache starts spitting messages anywhere, more precisely, in a strictly defined direction, a unique coincidence of pitfalls. In general, it is not surprising that a bug in Facebook caused a lot more resonance than a hole in Twitter, although the characteristics of both bugs are quite similar. And there, and there, apparently, there was an oversight when updating the code in a complex infrastructure. It is likely that someone cut off a couple of corners when they washed down a new feature in production: this often happens if a manager flies over you with the words “quickly wash my birthday vidos!”.
It affects the magnitude of the damage. Take any company smaller, and the vulnerability of 5% of the audience no one would have noticed. And here we are talking about tens of millions of people. What about this to do? The Kaspersky Lab blog is reasonably recommended not to do anything . In the long term, I recommend the following exercise. Whatever you send to the Internet, even to the most private-to-private service, imagine for a moment that you post the same message on all the pillars of your city. If the message in such a context does not seem to be innocuous anymore, it may not be worth sending it.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

Well, let's surrender to the will of this incomprehensible chemistry and talk about what happened on Facebook last week. And at the same time remember what happened last week at Twitter. And in that case, and in the other, there were microscopic bugs, independently discovered by the company's specialists, successfully closed with the maximum number of precautions, the public was notified. But Facebook’s “problem” is being discussed by Facebook, but almost nobody noticed the bug on Twitter. How so? Now we will understand.
What really happened on Facebook?
News . A detailed report of the social network about the event.

And that's what. Facebook has (more precisely, it was, it is not working now, see the screenshot at the beginning of the post) View As function . Available to all users, she allowed to see her profile as if another person was looking at him. Because of the numerous privacy settings, this is quite a useful feature: it allows you to understand what outsiders see on your page and what doesn't.

An important point: the page can be viewed with the "eyes" of some random visitor, and you can show how it looks from the point of view of a particular user, with first and last name. It is this precision and summed up the developers under the monastery.
According to Pedro Kanauati, Facebook’s vice president of engineering, security and privacy, there are three different vulnerabilities. First, there was a bug in the View As feature itself. In theory, it should switch the Facebook context to another user in “read only” mode, in the sense of “just viewing the user's page under which you are logged in.” In fact, in the View As mode, the field for posting was also generated. Secondly, this field did not work (correctly) in all cases, except one: when you want to congratulate a person on his birthday and post a video. Thirdly, when posting a video, the code for downloading this video itself generated a token, which could also be used as an access token from a mobile application.
That is, the scenario from the side of the attacker is approximately as follows. You create a profile or change the settings of an existing one so that you have a birthday today (wiii!). Using the View As function, open your profile on behalf of another user. When displaying a profile on behalf of another user, he (this other user) is invited to wish you a happy birthday and upload a cute video. When loading a video, a token is generated. You take this token from the page code and enter the mobile application on behalf of and with the rights of another user.
Next begin a little speculation. For example, do you need to be friends with the person on whose behalf you want to “see” your page? Judging by the descriptions (now broken) features on third-party sites - it is necessary. Now remember, how long have you been asked to become friends of you who are not known to you, but extremely persistent people? Having access to the token of one user, you can steal access keys to the account of one of his / her friends. And so on, theoretically, down to the scale limited by the theory of six handshakes. That is almost unlimited scale.
Cool, yeah? Interestingly, the Facebook message, published on Friday evening (in Moscow), was anticipated by complaintsusers that they were logged out both from Facebook itself and from other services for access to which the social network account was used. These were the very precautions that Facebook applied to affected users.
Or supposedly affected? We must pay tribute to the experts of Facebook - they told about the detected vulnerabilities in the most detailed and operational manner. On September 16, according to them, they noticed suspicious activity, on the 25th it became clear that what was happening, on September 28, the information was made public - immediately after the “unlocking” of the victims (which made any stolen tokens useless). But how exactly these victims suffered - here Facebook was not very specific. Perhaps they still do not know for sure.
It is known that the vulnerability appeared in the service code in July 2017. Last week, Facebook forcedly logged out 90 million users. Of these, 40 million are those for which the View As feature was applied, that is, someone on their behalf was looking at their page, not necessarily with criminal intent. Another 50 million are those affected by vulnerability. Since "affected" something? In decodingpress briefing there is more information: about 50 million Facebook users know that their tokens have been extracted. That is (speculations!) Some people used the View As feature on their birthday, and then (maybe!) They came from the same IP to a different account. And most likely, that “suspicious activity” of September 16, which was mentioned by representatives of the social network, was an attempt of mass automated exploitation of the bug, which was stopped in just over a week.
In general, Facebook has responded very well to the problem. He shared (as he could) detailed information, took action against the victims (actual or potential). 50 (or 90) million people on Facebook is not much. However, given the concern about the privacy of personal data given to social networks, it is understandable and heightened attention to this incident. There are two positive moments. First, the passwords were not stolen, and if some tools of unauthorized access to other accounts were available, they were destroyed by “carpet unlocking”. Secondly, even if you were among the alleged victims, and even if someone really accessed your data, in their hands turned out to be not all that Facebook knew about you. Because the real knowledge of Facebook users, even with the users themselvesnot divided .
And Twitter last week was lucky.
And what happened on Twitter?
News . Technical report social network.
In a sense, the bug found on Twitter is similar to what we found on Facebook. The hole was found in the API, which allows companies to communicate with customers - in general, it is an interface for sending mass messages or receiving private messages. If you communicated with someone using this API, then under certain circumstances your correspondence could be in the hands of a third party.
Okay, even in this form it does not sound frightening. Practice is even more boring. First, only registered Twitter partners can use the API. Secondly, in order for the bug to work and the private messages go wrong , both partners must (a) sit on the same IP, (b) work with the API using the URL that fully matches the slash(www.xxx.com/twitter_msg and www.yyy.com/twitter_msg is a coincidence), (c) unsuccessful access to Twitter servers in one piece of time, limited to six minutes.

When all this coincides, the
It affects the magnitude of the damage. Take any company smaller, and the vulnerability of 5% of the audience no one would have noticed. And here we are talking about tens of millions of people. What about this to do? The Kaspersky Lab blog is reasonably recommended not to do anything . In the long term, I recommend the following exercise. Whatever you send to the Internet, even to the most private-to-private service, imagine for a moment that you post the same message on all the pillars of your city. If the message in such a context does not seem to be innocuous anymore, it may not be worth sending it.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
