IB in the American way. Part 2. And can you elaborate on NIST 800-53, and where does risk management?
- Tutorial

* No matter how you look, security is your responsibility *
In his last article, “IS is American. Part 1. What is the NIST 800-53 and what do the security controls look like? ”I talked about the basis around which the entire NIST SP 800-53 document is built, namely the security controls. Those. those measures, the implementation of which can reduce the risks of information security. Thus, I hopefully interested in part of the audience. However, the full-fledged process of working with security controls is much wider and includes a host of other principles, in addition to the measures themselves. We’ll talk about how all this should work today.
Links to all parts of the article:
American-style information security. Part 1. What is the NIST 800-53 and what do the security controls look like?
IB in the American way. Part 2. And can you elaborate on NIST 800-53, and where does risk management?
IB in the American way. Part 3. What is a basic set of controls and how to determine the criticality of systems?
IB in the American way. Part 4. Understanding “fit” and “overlap” and complete this review
What is this NIST SP 800-53 rev4 about?
First of all, I allow myself to make a brief remark, once again reminding the reader that we will talk about the latest version of the NIST Special Publication 800-53 Revision 4 document (and here is the link for the most interested). We can say that the document is “fresh” - he is only a little over a year old. The same ISO 27001 (again and again we compare with it, but who else?) Was updated to the current version for as long as 8 years and only last year saw the light. But there the processes are more global. Therefore, it is probably excusable ...
So, the official name of the document can be translated as “ Security and privacy controls for federal information systems and organizations"(" Security and Privacy Controls for Federal Information Systems and Organizations "). From this, the vector of the further narration immediately becomes clear: the conversation will not be about high-level principles and concepts of information security, but about specific, well-detailed measures for ensuring information security, which we were convinced of by sorting out the control device in the previous part. Everything is very detailed and with great attention to even the smallest details.
It's also worth a little distraction to clarify the use of the word Privacy. The authors use this term not only in the title, but quite often in the body of the document when mentioning controls (namely, in this wording - “security and privacy controls”) - this suggests that privacy (read the protection of personal melons) is given in US most close attention

* That there is garbage for one can become a real treasure for another *
Standard heading: by author
Avoiding direct translation as much as possible, I should still draw the reader's attention to how the authors themselves determine the purpose of this publication. This will help to understand a little better what will be discussed later and the possible positioning of the document in the process of ensuring information security.
This document is a catalog of security and privacy controls intended for use in federal information systems and organizations, and also includes a procedure for selecting the controls necessary to ensure the protection of the organization and its functioning, related assets and individuals, as well as other organizations and the Nation from a variety of threats, including sophisticated cyber attacks, natural disasters, infrastructure problems and the human factor (both intentional and unintentional). Controls are a flexibly customizable tool for the information security risk management process and can be used across the organization. This publication also describes the process of developing specialized sets of security controls tailored to specific tasks and functions of a business, technology and work environment. In addition, it should be noted that the catalog of security controls provides security both in terms of functionality (durability and reliability of the proposed functions, security mechanisms, technologies, etc.) and in terms of guarantees (confidence that each control is implemented correctly, functions as planned and provides the expected result).
Multi-Level Risk Management
Since the document not only claims to be compatible with other NIST security publications, it is also designed for use within the organization-wide approach, i.e. approach throughout the organization, then all processes are considered accordingly. Including risk management, which is a necessary component for building a complete IS management system in an organization. So, considering the risk management process, the authors distinguish three levels operating on a different scale (shown schematically in Figure 1):
Level 1: Organization
Level 2: Business processes
Level 3: Information systems
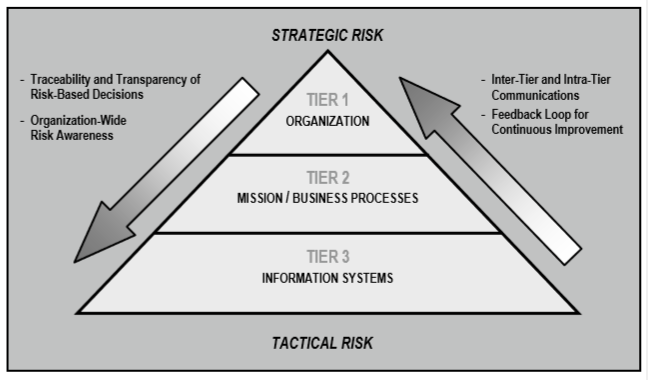
Figure 1. Layout of multi-level risk management
Such an approach allows for effective comprehensive risk management with the following clear advantages:
- Transparency and ease of tracking of risk-based solutions
- Organization-wide risk awareness
- Interaction both within and between different levels
- Feedback loop for continuous improvement
Level 1
It provides the opportunity to prioritize business tasks and organization functions that translate into an investment strategy and budgeting decisions, thereby providing cost-effective and cost-effective IT solutions that meet the requirements of productivity, as well as the goals and objectives of the organization.
Level 2
Includes:
- Definition of business processes necessary to ensure the business objectives and functions of the organization;
- Definition of security categories of dedicated information systems necessary for the execution of business processes;
- The inclusion of information security requirements in business processes;
- The choice of IT architecture (including information security) to facilitate the implementation of information security requirements in the organization’s information systems and their operational environment.
Level 3
To handle risks at the level of information systems, the Risk Management Framework (or RMF for short) is used - the set of risk management tools presented below in Figure 2. This Framework is one of the fundamental and connecting links of many NIST publications on topics of information security, IT and management. risks. For more information on its implementation, see NIST SP 800-37. The publication NIST SP 800-53 (and accordingly the entire cycle of these articles) is devoted in particular to the second step of RMF: the choice of security controls.
Risk management framework

Figure 2. Risk Management Framework
Although a full description and guidance on the application of the Risk Management Framework is a separate document (and to be completely accurate, this is exactly this publication NIST SP 800-37 ), I consider it necessary to provide the reader with a brief overview of this tool to improve understanding the process of choosing controls and its place among other processes in risk management. So, RMF answers the security questions that arise in the organization in the process of designing, developing, implementing, operating and disposing of IPs and their operating environment. The framework uses data on the existing architecture and data on the organization as input (this is described in more detail in the lists presented in Figure 2).
Briefly consider the steps in this cycle:
- Step 1. Categorization of IP based on FIPS Publication 199 “threat assessment”;
- Step 2. Choosing a set of initial security controls, based on the results of categorizing IP, and applying the “tailoring” manual * adaptation *;
- Step 3. Implementation of security controls, documenting the processes of design, development and implementation of controls;
- Step 4. Evaluation of security controls to determine to what extent the controls are correctly implemented, work as expected, and provide the necessary result in the sense of achieving IS requirements for IP.
- Step 5. Authorization of IP operation, based on risks arising for the organization, individuals, etc. as a result of the functioning and use of IP, and the decision to take these risks;
- Step 6. Monitoring security controls in the IS and the operating environment on an ongoing basis to determine the effectiveness of the controls, the need for changes to the IS and the functioning environment, and compliance with legal requirements.

* Maybe they changed jobs, but they are still in business *
And briefly about FIPS 200
As you can see in the figure, the second step of the Framework refers to the FIPS 200 document (Federal Information Processing Standards Publication “Minimum security requirements for federal information and information systems”), in addition to the publication we already know (for which we actually gathered here). This document is dedicated to defining the minimum security requirements for confidential information and information systems. In fact, the document operates with security measures, divided into the same families of controls that we examined in the first part. However, since the essence of the document is in the minimum requirements, IS measures there appear only the most basic ones and they are described in plain text in just a few sentences for each family. Next comes the explanation, that the definition of a security category must be made in accordance with FIPS 199 (more on this will be described later). Then, based on the category obtained, it is necessary to develop a set of security controls, taking as a basis one of the basic sets of controls that are presented in NIST 800-53. This process will be discussed in more detail below. This is how FIPS got a small document, which, however, plays a big role, obliging everyone to comply with current best practices, as it refers to the regularly updated NIST 800-53. This process will be discussed in more detail below. This is how FIPS got a small document, which, however, plays a big role, obliging everyone to comply with current best practices, as it refers to the regularly updated NIST 800-53. This process will be discussed in more detail below. This is how FIPS got a small document, which, however, plays a big role, obliging everyone to comply with current best practices, as it refers to the regularly updated NIST 800-53.
Instead of a conclusion
In this article, we familiarized ourselves with the basis necessary to understand how the process of ensuring information security through the implementation of controls correlates with other processes in the organization.
The following articles will tell you how to categorize information systems, choose the correct sets of security controls and other activities associated with the difficult task of ensuring information security.
