Using Fujitsu PalmSecure Technology for Two-Factor Authentication
Information technology is becoming increasingly diverse and pervasive, while at the same time, our personal data is at greater risk. Today, only the lazy one does not say that such an aspect of information security as user authentication needs reliable security features. Therefore, the two-factor authentication method, i.e. user recognition not by any one parameter (personal password, smart card, fingerprint, etc.), but by several (or rather two) provided at the same time when entering the system or when requesting access to a particular service. Our material will focus on the solution presented at the Fujitsu World Tour 2014 conference, which uses a two-factor authentication method based on a contactless RFID card and Fujitsu Palm Secure palm vein scanner, as well as on PalmSecure technology itself .

Wherever we go - to the bank, fitness center, private clinic - everywhere we are surrounded by certain authentication methods and technologies. The simplest example is that your pass to work is probably equipped with a small RFID tag, which contains information about you as an employee of the company. More advanced methods are common, for example, in some ATMs in Europe , where in addition to the pin code, your identity is confirmed by a fingerprint or using the same Fujitsu PalmSecure vein scanner. You can also find such a scanner at the entrance to the fitness center (a similar system is installed in fitness clubsUK Gym EasyGym ): just have your fitness club’s RFID card with you and put your palm on the PalmSecure sensor and you’ll be passed inside.
In one of our previous blogs, we have already described in some detail the Fujitsu PalmSecure technology and its features. Today we will talk about a real-life solution created by Russian development companies in which this technology has been successfully applied.
Of course, in addition to the examples described above, there are many ways to effectively apply PalmSecure vein scan technology. One of such cases is the touch kiosk presented at the conference (or rather, the general access terminal, TOD) - a project of AMT-GROUP , made on the basis of Indeed ID software and a kiosk from Zorgtech , equipped with a Fujitsu PalmSecure palm scanner and a contactless RFID card reader .
What is a touch kiosk in its most general form? As a rule, this is a hardware-software complex assembled on the basis of a personal computer and equipped with a touch monitor, designed to provide the user with various information without involving additional personnel. Such touch kiosks are becoming increasingly popular and are used in almost all areas of business, from clinics, universities, government agencies and ending with shops. And naturally, in all areas of application of such complexes, reliable user authentication is the most important condition for successful operation.
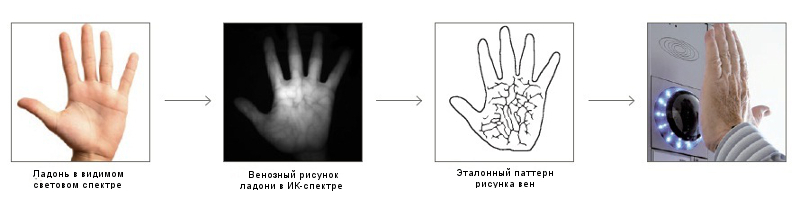
PalmSecure identification technology, as one of the authentication methods, was selected by AMT-GROUP specialists in this projectdue to a significant advantage over fingerprint reading. In the case of using a fingerprint scanner during reading, a direct contact of the finger with the sensor occurs, which, when used actively, leads to its rapid contamination and the need for frequent maintenance.
For touch kiosks, the problem described above is especially relevant, because being installed in public places (for example, in transport hubs - train stations, airports, etc.) or in the offices of large corporations, more than one hundred people will use such terminals. It is easy to imagine what will become of the fingerprint scanner in this case. Scanning the palm is free from this drawback - the palm does not come into contact with the scanning surface of the device during operation.

Using an RFID card in the project allowed several advantages:
• Adding an additional factor to the authentication scheme. As a result, authentication is two-factor: on the card (what the user has) and on the palm (what the user is)
• The authentication procedure is simplified by the fact that you do not need to enter your name - it is automatically determined by the contactless card by the
Software Provider Indeed ID acted for this TOD. Its Indeed Enterprise Authentication (Indeed EA) software solution enables strong authentication technologies when accessing Microsoft Active Directory domain resources.. The system frees users from the need to remember and store passwords in secret and eliminates the need to manually enter passwords from the keyboard. This allows you to increase the efficiency of working with the terminal, reduce information security risks, significantly reduce the number of calls to the help desk service (by minimizing the number of incidents "forgotten password" and "locked account") and ultimately reduce infrastructure maintenance costs.
When installed on a shared terminal, Indeed EA software functioned in kiosk mode. A feature of this mode is that the terminal is used by a large number of users and switching between their working sessions should be carried out very quickly. For maximum convenience in this mode, a contactless smart card (RFID) and an optional palm vein scanner are used. The scenario for accessing the required services is as follows:
1. The user is presented with a Indeed Enterprise Authentication (IEA) authentication window, offering to put a palm on the scanning device and a card on the reader.
2. After these operations are performed by the user, the IEA automatically determines the username and transfers the authenticator received from the user to the server for verification.
3. The server processing the application, upon receipt of an authentication request, retrieves the user’s reference authenticator from the database, compares it with the data provided, and logs the corresponding event. In case of successful authentication, the server returns the user password for entering the domain to the terminal.
4. Having received the password from the server, the terminal authenticates the user in the domain, and he gets access to the requested service.
5. After the terminal has finished using, when the user picks up the card, the terminal exits the system and returns to standby mode.
Thus, the authentication procedure is extremely simplified, which eliminates the occurrence of conflict situations at this stage. The user accesses the terminal, identifies through a contactless RFID card, confirms his identity through a Fujitsu palm scanner, after which the system boots up and provides access to the necessary information resources.
Fujitsu PalmSecure palm vein recognition technology can be applied to a wide variety of business areas as one of the most reliable, fast and accurate authentication methods. By contacting your Fujitsu representative, you can get detailed information about the possibility of using it in your business and order the appropriate PalmSecure scanner model in the required quantity, while receiving full technical support for the product.
Wherever we go - to the bank, fitness center, private clinic - everywhere we are surrounded by certain authentication methods and technologies. The simplest example is that your pass to work is probably equipped with a small RFID tag, which contains information about you as an employee of the company. More advanced methods are common, for example, in some ATMs in Europe , where in addition to the pin code, your identity is confirmed by a fingerprint or using the same Fujitsu PalmSecure vein scanner. You can also find such a scanner at the entrance to the fitness center (a similar system is installed in fitness clubsUK Gym EasyGym ): just have your fitness club’s RFID card with you and put your palm on the PalmSecure sensor and you’ll be passed inside.
In one of our previous blogs, we have already described in some detail the Fujitsu PalmSecure technology and its features. Today we will talk about a real-life solution created by Russian development companies in which this technology has been successfully applied.
Sharing terminal
Of course, in addition to the examples described above, there are many ways to effectively apply PalmSecure vein scan technology. One of such cases is the touch kiosk presented at the conference (or rather, the general access terminal, TOD) - a project of AMT-GROUP , made on the basis of Indeed ID software and a kiosk from Zorgtech , equipped with a Fujitsu PalmSecure palm scanner and a contactless RFID card reader .
What is a touch kiosk in its most general form? As a rule, this is a hardware-software complex assembled on the basis of a personal computer and equipped with a touch monitor, designed to provide the user with various information without involving additional personnel. Such touch kiosks are becoming increasingly popular and are used in almost all areas of business, from clinics, universities, government agencies and ending with shops. And naturally, in all areas of application of such complexes, reliable user authentication is the most important condition for successful operation.
PalmSecure identification technology, as one of the authentication methods, was selected by AMT-GROUP specialists in this projectdue to a significant advantage over fingerprint reading. In the case of using a fingerprint scanner during reading, a direct contact of the finger with the sensor occurs, which, when used actively, leads to its rapid contamination and the need for frequent maintenance.
For touch kiosks, the problem described above is especially relevant, because being installed in public places (for example, in transport hubs - train stations, airports, etc.) or in the offices of large corporations, more than one hundred people will use such terminals. It is easy to imagine what will become of the fingerprint scanner in this case. Scanning the palm is free from this drawback - the palm does not come into contact with the scanning surface of the device during operation.
Using an RFID card in the project allowed several advantages:
• Adding an additional factor to the authentication scheme. As a result, authentication is two-factor: on the card (what the user has) and on the palm (what the user is)
• The authentication procedure is simplified by the fact that you do not need to enter your name - it is automatically determined by the contactless card by the
Software Provider Indeed ID acted for this TOD. Its Indeed Enterprise Authentication (Indeed EA) software solution enables strong authentication technologies when accessing Microsoft Active Directory domain resources.. The system frees users from the need to remember and store passwords in secret and eliminates the need to manually enter passwords from the keyboard. This allows you to increase the efficiency of working with the terminal, reduce information security risks, significantly reduce the number of calls to the help desk service (by minimizing the number of incidents "forgotten password" and "locked account") and ultimately reduce infrastructure maintenance costs.
When installed on a shared terminal, Indeed EA software functioned in kiosk mode. A feature of this mode is that the terminal is used by a large number of users and switching between their working sessions should be carried out very quickly. For maximum convenience in this mode, a contactless smart card (RFID) and an optional palm vein scanner are used. The scenario for accessing the required services is as follows:
1. The user is presented with a Indeed Enterprise Authentication (IEA) authentication window, offering to put a palm on the scanning device and a card on the reader.
2. After these operations are performed by the user, the IEA automatically determines the username and transfers the authenticator received from the user to the server for verification.
3. The server processing the application, upon receipt of an authentication request, retrieves the user’s reference authenticator from the database, compares it with the data provided, and logs the corresponding event. In case of successful authentication, the server returns the user password for entering the domain to the terminal.
4. Having received the password from the server, the terminal authenticates the user in the domain, and he gets access to the requested service.
5. After the terminal has finished using, when the user picks up the card, the terminal exits the system and returns to standby mode.
Thus, the authentication procedure is extremely simplified, which eliminates the occurrence of conflict situations at this stage. The user accesses the terminal, identifies through a contactless RFID card, confirms his identity through a Fujitsu palm scanner, after which the system boots up and provides access to the necessary information resources.

Fujitsu PalmSecure palm vein recognition technology can be applied to a wide variety of business areas as one of the most reliable, fast and accurate authentication methods. By contacting your Fujitsu representative, you can get detailed information about the possibility of using it in your business and order the appropriate PalmSecure scanner model in the required quantity, while receiving full technical support for the product.
