0day vulnerability in iOS apps: Gmail, Google+ and FB Messenger
- Transfer

Intro
Normal people spend nights watching movies, reading articles, talking on social networks or (yes, I know - this is strange) falling asleep on the bed.
I spend my nights reading documentation and testing a wide variety of applications and services.
One night I just read the documentation on tel links , because I was delighted with the old technologies that were used so far, their shortcomings and the fact that people never read the RFC, which leads them to RTFM PWNAGE (as I used to call).
Need to try
As soon as I finished reading the documentation on tel - I looked at my iPhone and said: Cool, you need to try! I put together a small HTML page and uploaded it to Safari, here is the code:

As soon as I clicked on the link, a dialog box appeared asking me if I really want to call 0000.
Apple
At this stage, there was only my interest in tel links, I was not looking for a vulnerability. But then it dawned on me: Apple very much likes to change something and do things better, maybe Apple has its own TEL documentation? And I was right
The line that I fell in love with
Apple's tel documentation is very short and easy to read. Reading the first paragraph, something caught my attention:
When the user taps the tel link on the page, iOS displays an alert that asks if the user really wants to dial the phone number and initializes the dialing if the user clicks "Agree." When a user opens a URL with a tel link through the installed application, iOS does not display an alert and initiates a call without further confirmation by the user.
Original
When a user taps a telephone link in a webpage, iOS displays an alert asking if the user really wants to dial the phone number and initiates dialing if the user accepts. When a user opens a URL with the tel scheme in a native app, iOS does not display an alert and initiates dialing without further prompting the user.
Therefore, if I click on the link in Safari, I will receive a window that will ask me if I really want to call, but if I click on the link in the webView of the installed application, the call will begin without my confirmation.
Do people read documentation?
Not. And this is sad.
After reading it, I was tormented by doubts about such "big players" as Facebook, Twitter, Google, LinkedIn and so on. I thought that such "giants" could take care of such a small "hole", but as it turned out, I was wrong.
Testing on the Facebook Messenger App
I sent the link to the page via Facebook Messenger, clicked on it to get through the webView to the previously created page (social applications do not want you to leave the application and that is why such applications use webView), and then clicked on the “click me” link:
Clicking on the link initiates a call. Wait a minute ... this is not very good.
Making the link self-clicking
Many people believe that things like links can only be clicked by the user. No matter how it is! Using a tricky but terribly simple javascript script, I made the link “self-clicking”.

See what happens

Note: you can also do a redirect on the server side by throwing the user a tel link using header ("Location: tel: // 0000")
Can this be considered a security problem?
I can make you dial any phone number with a single click on the link in any application in which the processing of tel links is not adjusted. So yes, this is a security issue.
Just imagine - I registered a paid phone number and sent you a link in Facebook Messenger or Twitter. You clicked and called me, I picked up the phone to withdraw some money from your account.
It is not right! Who is to blame?
Well ... Apple is not to blame. People do not read the documentation at all. The first paragraph on the tel link describes everything to the smallest detail - what, when and how it happens, and also clearly states that however installed applications can be configured to show their own alerts.
Who is not RTFM?
Facebook messenger

Gmail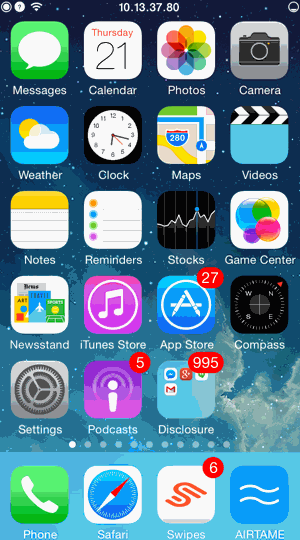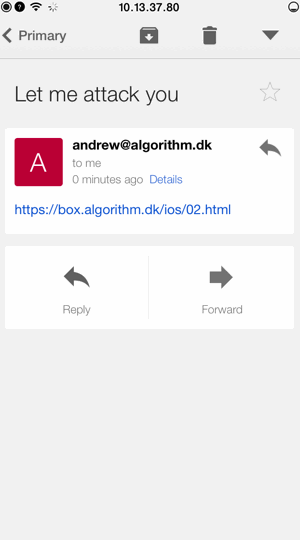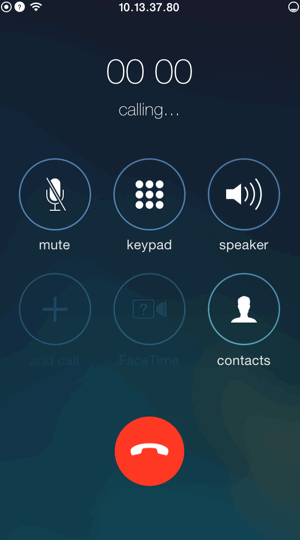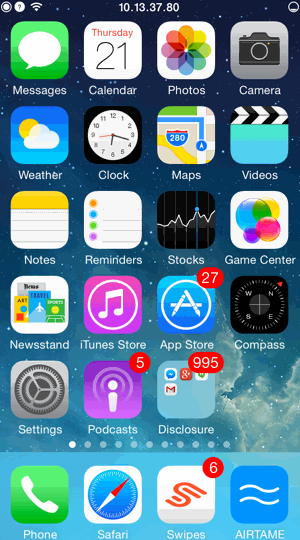

Google+

And now for everyone ...
be careful
While I tested this vulnerability on only a few applications of large companies, it can also be assumed that companies and smaller platforms did not even think about patching this vulnerability.
Author's note: By the way, all the same is done perfectly well with iFrame.
