How we defended the administration of the Kaluga region from spam

As a corporate cloud provider, we offer our customers the maximum number of services related to the storage and transmission of data - including spam protection. In this post we want to talk about how the Cloud4Y antispam service based on SpamTitan for the VMware platform works on the example of one of our clients - the administration of the Kaluga region. We want to talk about the functional features and basic settings of SpamTitan, as well as how we had to solve the licensing problem that arose during the client’s work.
Opportunities
In this post, it makes no sense to list all the functionality of the system, we give only the most interesting features:
- Rapid deployment on VMware virtual machines with off-the-shelf virtual appliance
- it is possible to create a clustered mail gateway to optimize the load;
- convenient custom reports and notifications
- flexible access policies for users and administrators
- dual anti-virus protection
Other features can be found at www.spamtitan.com/about-us/about-spamtitan
SpamTitan versus other cloud4y.ru/cloud-services/antispam systems
Customization
Setting up SpamTitan usually does not take much time, and consists of the following steps that are worth paying attention to:
- Deployment of a virtual machine image based on the client’s virtual infrastructure. For the VMware platform, we used the Virtual appliance, which can be downloaded from the manufacturer’s website.
- Setting the network parameters of the virtual machine is done from the local console via the interface in the form of a text menu and should not cause any problems.
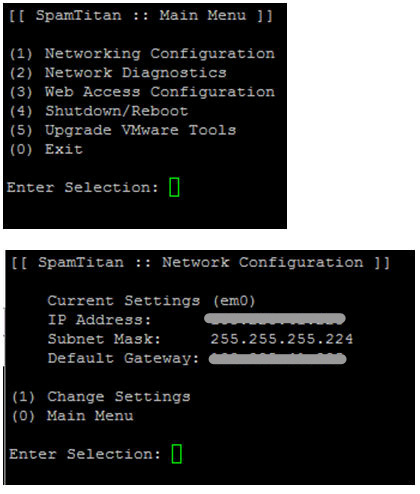
Further configuration is already going through the web interface available at http: // ip-your-server.
The first thing to do after setting up the network and rebooting is to add a license key. The key can be obtained either trial (for 10 days without restrictions) or purchase a commercial one. This is done in the “System setup” “Licensing” section.


Then update the system to the latest version in System Updates. At the time of writing, the current version is 6.0.4.
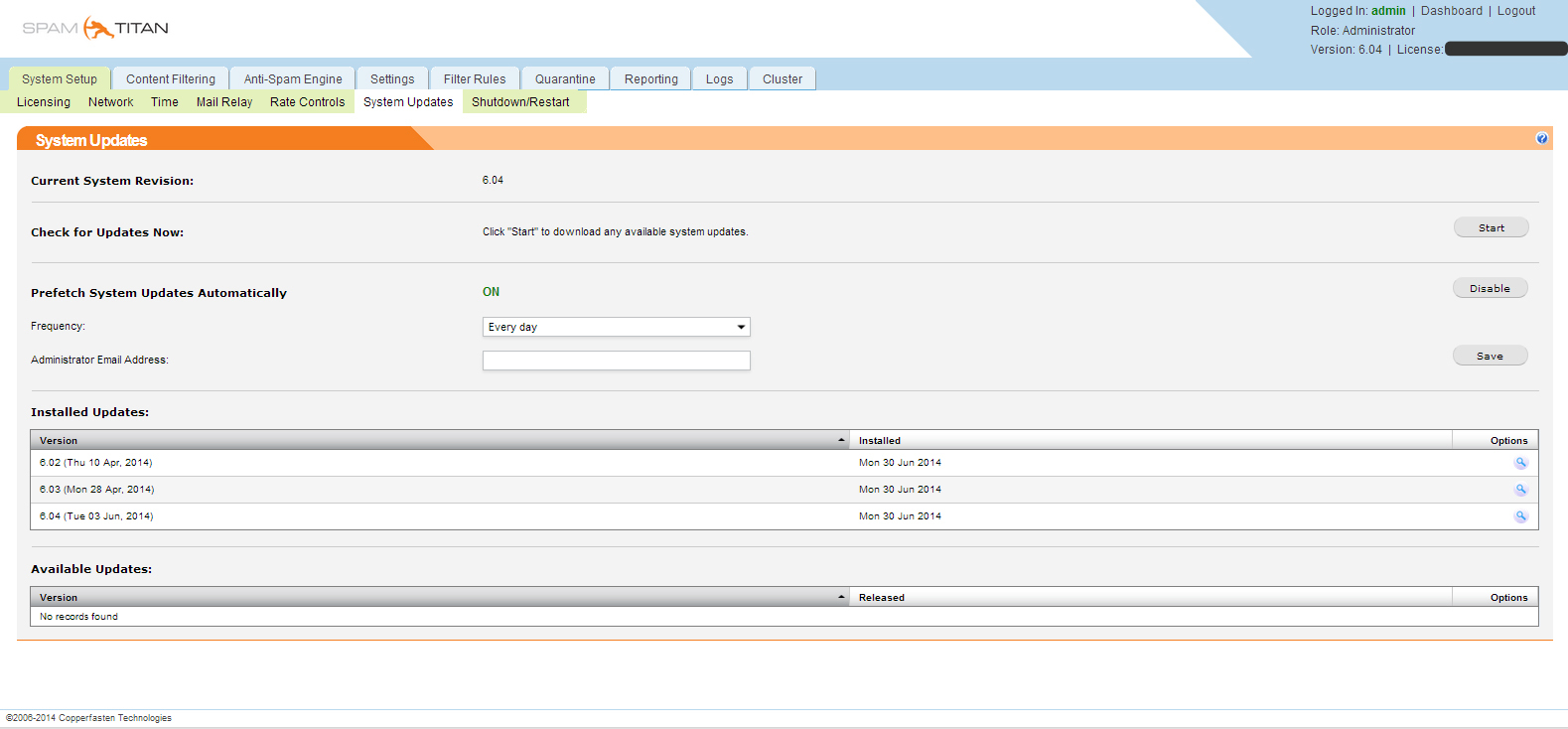
In the Network section, configure the network Network configuration DNS Settings.
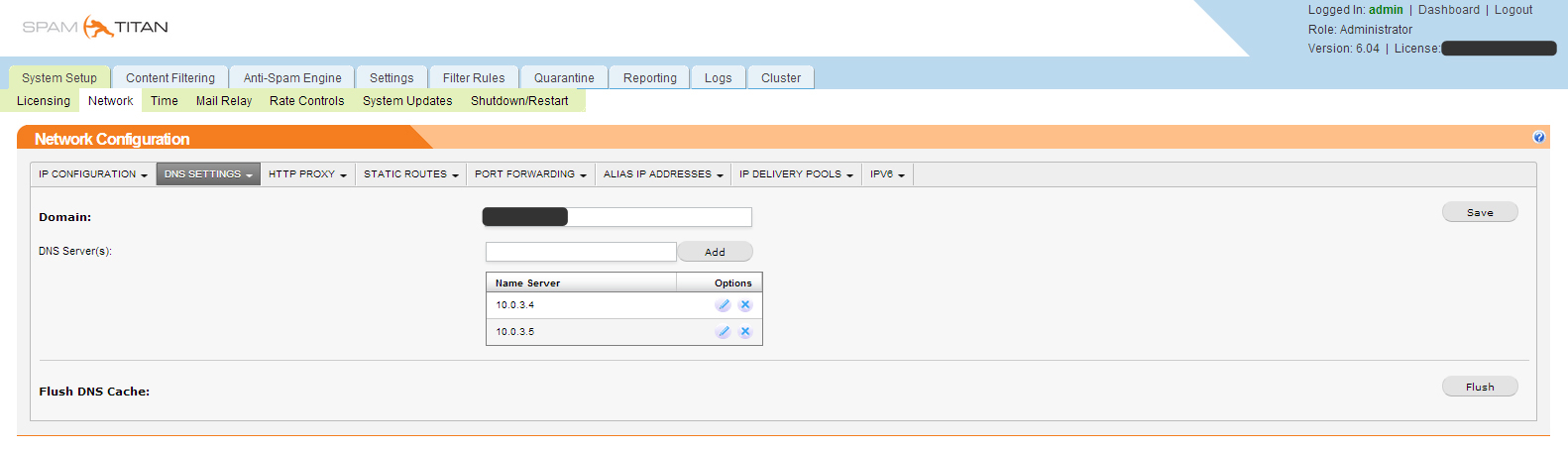
We configure time synchronization.
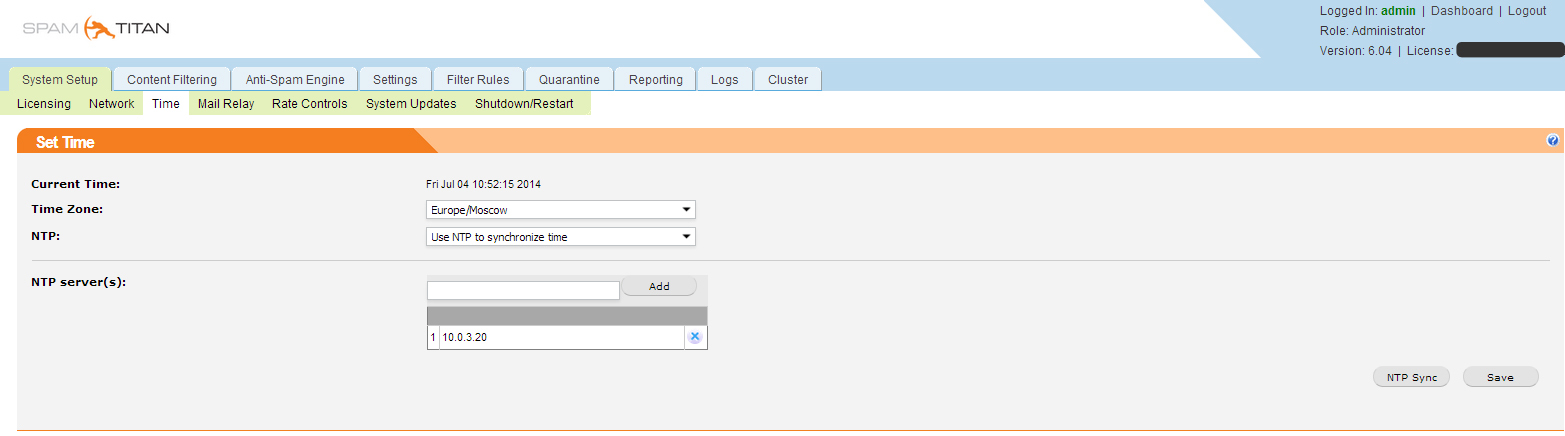
We configure Mail relay for the required domain.
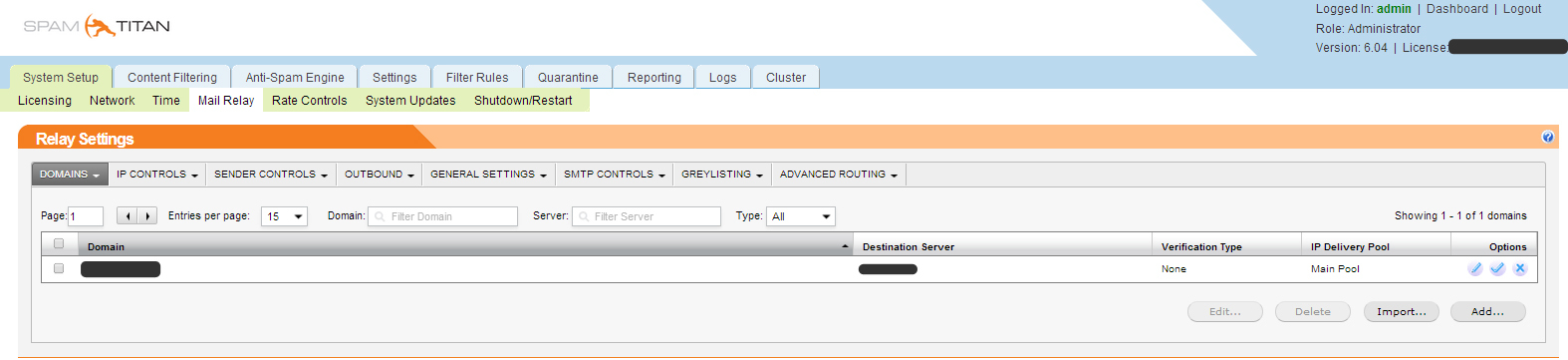

It is necessary to register the domain name, the address of the SMTP server that is serving this domain now. Several connection modes are possible:
with checking the existence of the box and without checking the existence of the box.
On the IP CONTROLS tab, you can configure white and black lists of SMTP servers and enable support for RBLs (Realtime Blackhole Lists), in our case this was not relevant, since we were for SMTP Relay and accept all mail from one server.
In GENERAL SETTING, you must specify the hostname of the spam filter, which must correspond to the dns record.
Content Filtering -> Viruses
Configure virus scan settings, update the Clam AV, Kasperky AV databases
Content Filtering-> Spam
Turn on spam checking and update spam lists
Anti-Spam Engine-> Settings
Enable network tests Razor V2, Pyzor, RBLs
Anti-Spam Engine-> Domain policies / User-Policies
You can set global domain policies and policies for individual users. For example, the global domain policy discards all spam emails by default, and for other users to quarantine
Anti-Spam Engine-> Roles and permissions / Admins / Domain Groups
You can create user roles, global administrators and domain administrators.
Settings-> Access / Authentification
You can configure how users authenticate to the quarantine web interface
We used authentication through a Windows domain through LDAP. In this case, each client receives its own quarantined partition, which is logged in via the web interface, login and password are the same as credentials for entering email.
Filter Rules
You can bookmark global white and black lists of email addresses and domains.
Quarantine
A complete list of quarantined messages.
Reporting Graphs
Report on all processed messages, detected viruses, CPU, memory and disk system load for periods of 1 day, week, month, year:
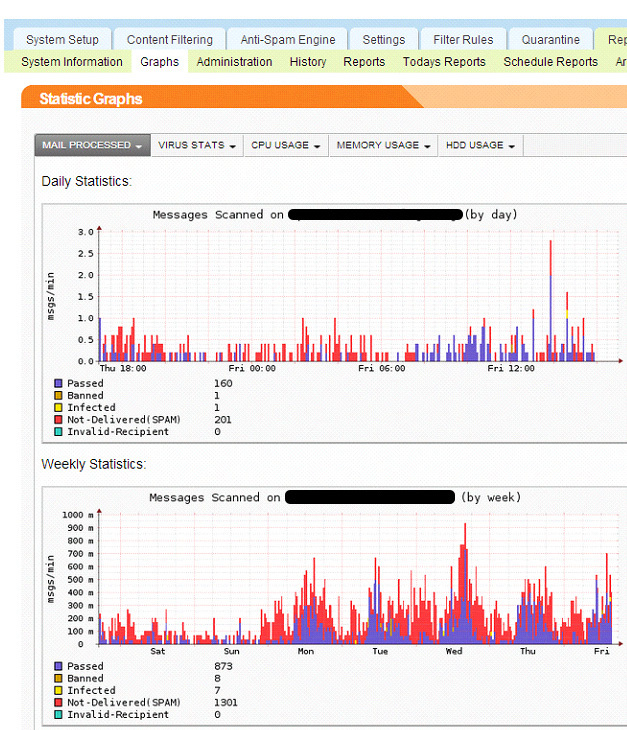

Reporting History
A complete message log with the ability to sort by fields.
Logs
Raw logs from / var / logs: Maillog, messages, and CFMA
Cluster directories.
Section for configuring a cluster configuration.
Full documentation about SpamTitan can be found here .
Problem
In the course of work, it turned out that out of 3,500 mailboxes, only 500 had to be protected from spam, while licenses were purchased for only 500 mailboxes and it was not planned to expand them.
The logic for calculating the necessary licenses is as follows: every 24 hours, the average number of mailboxes received by mail for the last 5 working days is calculated, minus 20% for eliases (only 20% is given because, as a rule, aliases are not used with the same intensity as the main mailbox). Information about current usage is displayed in the management console.
If the number of boxes is exceeded, the system will issue a warning and the license will need to be expanded.
For example, your organization has 100 mailboxes, but only 50 of them you need to protect from spam. Since the system considers the total number of boxes passing through it, in the case of passing 51 boxes, the system will be blocked. You will have to buy licenses or use the solution described below.
Decision
As an example, we give the real part of the customer’s infrastructure.
In order for SpamTitan not to block, he needs to “say” which boxes he should protect.
Therefore, first a list of mailboxes that will pass through the spam filter was compiled. This list is entered into the gateway, for example, SMTP Relay Postfix. After the letters go through the Kerio Firewall, they go to SMTP Relay, in which the reconciliation with the list compiled earlier occurs. If the mailbox is in the list of protected ones, then the letter is sent to SpamTitan, if it is absent, then the letter is sent to the mail server.
An example of an ideal model for passing mail messages and refined taking into account the specifics of licensing SpamTitan:
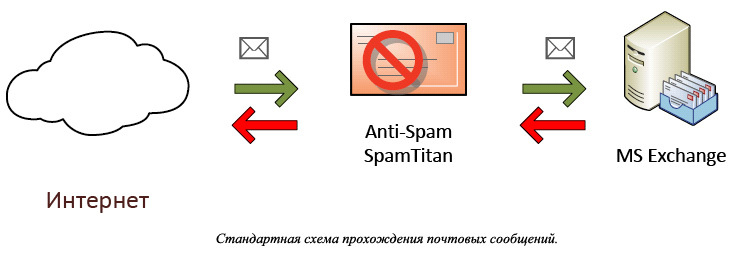
The client wanted to leave the old firewall in the appendage to spamtitan. Spam titanium is located after Kerio. During the installation process, it turned out that the client bought licenses for a smaller amount than required. I had to look for a way that does not violate the licensing conditions, but allows you to use the full functionality of the system.
An example of a modified SpamTitan licensing model:
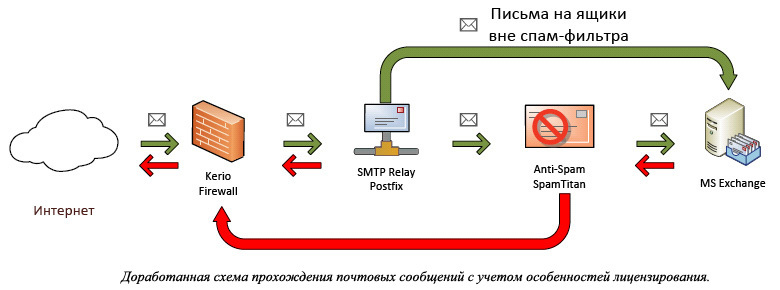
An SMTP relay was deployed to the client on which the rules for routing messages based on mailbox lists were posted. Messages for mailboxes from the list are sent to titanium spam, passed through the filter and sent to the mail server, and all the rest directly to the mail server.
Result
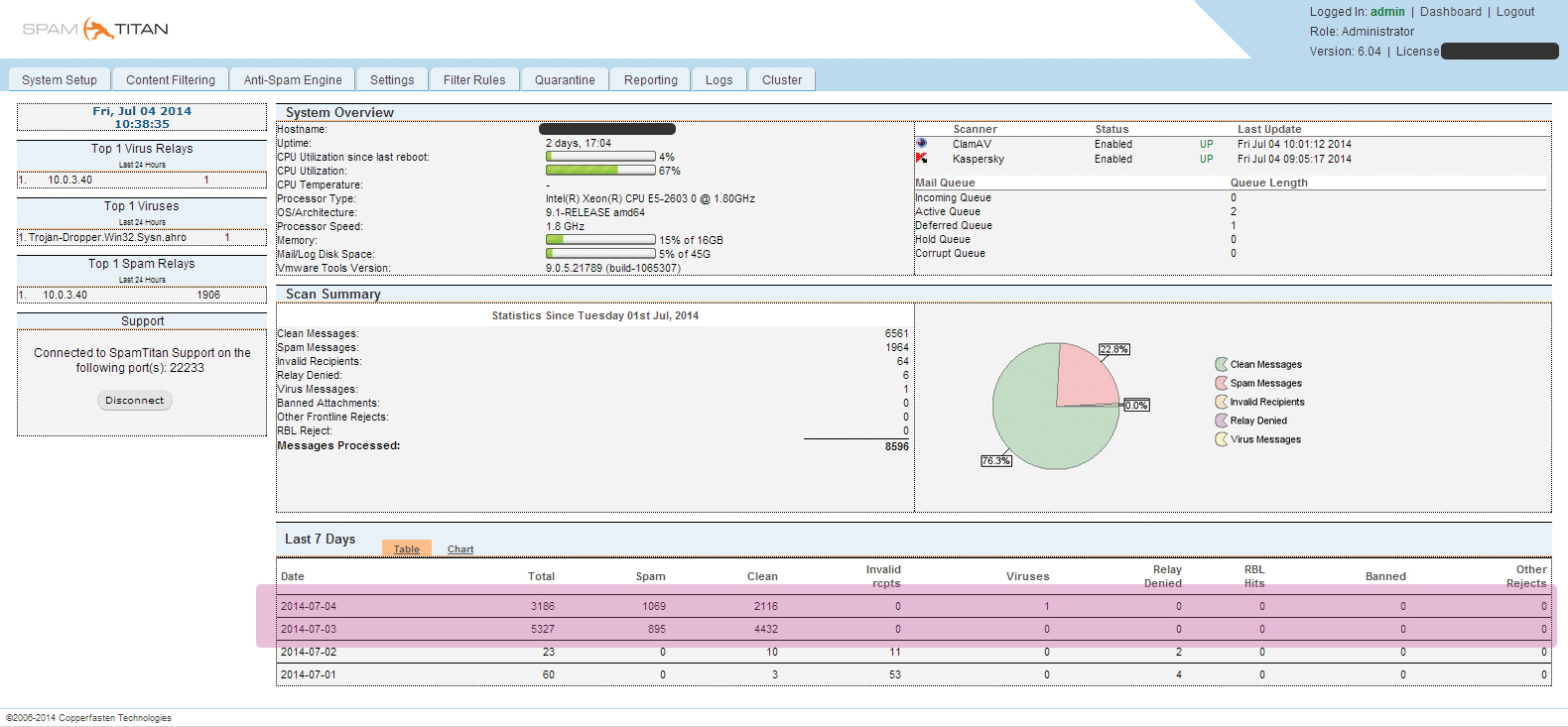
In this case study, the work of "SpamTitan" allows you to filter out daily from the total number of 24% of messages that are classified as spam. At the same time, the client has a tool for flexible configuration of the list of mailboxes that must be protected from spam without additional costs for the purchase of licenses.
Separately, we want to thank the IT specialists of the Kaluga Region Administration for their professionalism.
Thank you for your attention and, as always, we welcome your comments.
