Security Week 35: winter is near, how to collect a trojan, Tesla's hijacking
For a long time we did not have a digest in the hodgepodge genre, let's try to perform in it. Moreover, a lot of interesting, but completely diverse news came up in a week. Let's start with a new modification of the known cold boot attack, which uses natural freezing of RAM microcircuits.

The original research work on this type of attack was published in 2008 (here is a PDF ). Although it is believed that when power is turned off, data from the RAM instantly disappears, this is not quite so. Even at room temperature and even after removing the memory module from the motherboard, the data is stored in a more or less intact form for a few seconds.
If the module is cooled, the data can be saved even longer - for analysis on the same computer, or you can rearrange the modules altogether to another machine. Cooling to –50 degrees (with a simple can of compressed air) gives another 10 minutes of data integrity. Liquid nitrogen and cooling to –196 degrees freeze information for an hour. Many secrets can be stolen from memory, in some cases even data encryption keys.
In response to the study, the Trusted Computing Group consortium introduced a system of forced memory rewriting when the computer was turned on. It turns out, at least, laptops with soldered RAM chips are protected from such an attack. Last week it became clear that this is not entirely true.
Researchers from the company F-Secure found a way to cancel the overwriting of memory cells when you restart the computer (for a detailed article on English here ). The attack works in the following scenario: the victim is abducted a laptop that is in sleep mode, and the contents of the RAM is saved. Then the laptop is opened, and the cell rewriting system is somehow turned off. How exactly - not reported. In the spring, we covered another study of F-Secure about the security of hotel keys, and there, too, the experts were extremely unspecific when it came to technical details. But they shoot a video with the dramatization of the process:
It is only known that the memory chips themselves are modified. After the forced erasure of memory (and it sounds good!) Was turned off, a traditional cold boot attack occurs. The memory freezes to survive a brief power outage, the laptop restarts, boots from external media, and then begins analyzing the contents from the previous incarnation. The researchers claim that the whole process can take no more than two minutes. Such an interesting method of attack, as if coming straight from the James Bond movies.
Reducing the likelihood of success is quite simple. As the authors themselves say, hibernation and authorization will help before the start of the OS boot process from somewhere. Well, encryption of everything and everything, of course. If there is no encryption, all these manipulations with frozen memory are completely optional.
Troyan kibergruppirovki LuckyMouse uses a stolen certificate and adopts open source
study .
Most recently, we mentioned a study by specialists of the Laboratory of the combined attack of the Lazarus group . On September 10, another study of a nontrivial attack, initiated, judging by a number of signs, appeared by the Chinese-language cyber-grouping LuckyMouse.
The functionality of the Trojan program is quite traditional: it provides the ability to connect remotely to an infected machine, conducts reconnaissance of the local network, communicates with the command server and tracks the user's network traffic.
Three features of the malware are interesting. First, it is a network traffic filtering driver that uses a legitimate digital certificate issued by VeriSign for LeagSoft, a software developer (including) to monitor data leaks. Obviously, this company was hacked, and the certificate provided a covert installation of software to intercept network communications.
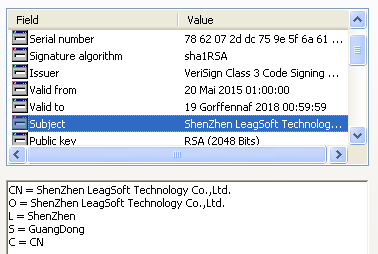
Secondly, it’s noteworthy that the authors use an open source Trojan program in C.
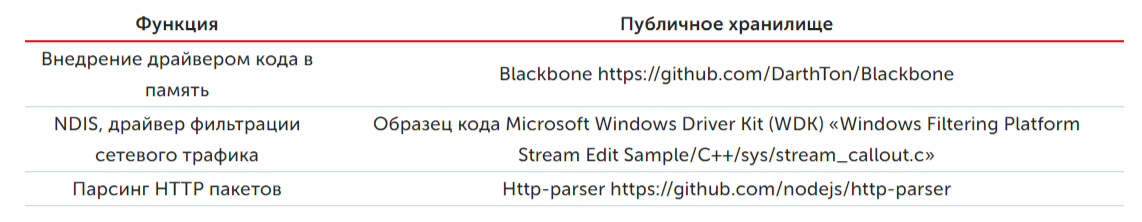
Thirdly, the specialists of “Laboratories” have found signs in the driver indicating that the malicious code, although used for real attacks, is still under development. The debug messages come across the lines [test], the code mentions the well-known ports of common network services - POP3S, SMB, MSSQL, which are not used in any way later. Such a cybercriminal agile. The use of open source, in addition to speeding up development, also complicates the attribution of malware. If the trend develops, it will be harder to attribute attacks to certain groups than when they use a completely custom "easier to write" malicious code. However, in this case, the attribution did not cause any difficulties: the Trojan contacts the server, which was previously known as belonging to the LuckyMouse group.
Tesla hijacking without severe hacking
News .

Last year, the Keen Security Lab of the Chinese company Tencent published an interesting study of Tesla car security systems. In it, an electric car was hacked the way computer hackers would do: via a wireless connection and / or a web browser embedded in the entertainment system of the machine. Using the newly discovered vulnerabilities, Chinese researchers, via the CAN control bus, reached the control systems of “vital” automobile bodies such as steering and brakes.
This is a fascinating, but not an easy way, also with incomprehensible prospects for realizing the attack in practice by real attackers. A group of researchers from Belgium took the path of real criminals and analyzed the communication between the car and the control panel. It turned out that the keyfob uses an unreliable 40-bit cipher to unlock and start the machine.
With the help of Raspberry Pi and a pair of radio communication blocks with a total cost of about $ 600, researchers have learned not only to intercept a team to open doors and play it - they were able to create a virtual copy of a key that can be used many times. The result was a very real attack: it is enough to intercept the radio transmission once between the real key and the car, and then you can control the machine from a copy. You can not only open the door, but also start the car and drive away.
How do you like that, Ilon Musk?It took almost a year to eliminate the vulnerability. Tesla not only updated the encryption of communications with the keyfob, but also introduced a new feature: to start the car, you now need to enter a PIN code. Tesla owners with a heightened sense of danger are also given the opportunity to turn off the car unlocking system without pressing buttons - by the appearance of a key fob near the car.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism. And by the way, if you are using Tor Browser, upgrade to version 8. In the previous found a serious vulnerability .

The original research work on this type of attack was published in 2008 (here is a PDF ). Although it is believed that when power is turned off, data from the RAM instantly disappears, this is not quite so. Even at room temperature and even after removing the memory module from the motherboard, the data is stored in a more or less intact form for a few seconds.
If the module is cooled, the data can be saved even longer - for analysis on the same computer, or you can rearrange the modules altogether to another machine. Cooling to –50 degrees (with a simple can of compressed air) gives another 10 minutes of data integrity. Liquid nitrogen and cooling to –196 degrees freeze information for an hour. Many secrets can be stolen from memory, in some cases even data encryption keys.
In response to the study, the Trusted Computing Group consortium introduced a system of forced memory rewriting when the computer was turned on. It turns out, at least, laptops with soldered RAM chips are protected from such an attack. Last week it became clear that this is not entirely true.
Researchers from the company F-Secure found a way to cancel the overwriting of memory cells when you restart the computer (for a detailed article on English here ). The attack works in the following scenario: the victim is abducted a laptop that is in sleep mode, and the contents of the RAM is saved. Then the laptop is opened, and the cell rewriting system is somehow turned off. How exactly - not reported. In the spring, we covered another study of F-Secure about the security of hotel keys, and there, too, the experts were extremely unspecific when it came to technical details. But they shoot a video with the dramatization of the process:
It is only known that the memory chips themselves are modified. After the forced erasure of memory (and it sounds good!) Was turned off, a traditional cold boot attack occurs. The memory freezes to survive a brief power outage, the laptop restarts, boots from external media, and then begins analyzing the contents from the previous incarnation. The researchers claim that the whole process can take no more than two minutes. Such an interesting method of attack, as if coming straight from the James Bond movies.
Reducing the likelihood of success is quite simple. As the authors themselves say, hibernation and authorization will help before the start of the OS boot process from somewhere. Well, encryption of everything and everything, of course. If there is no encryption, all these manipulations with frozen memory are completely optional.
Troyan kibergruppirovki LuckyMouse uses a stolen certificate and adopts open source
study .
Most recently, we mentioned a study by specialists of the Laboratory of the combined attack of the Lazarus group . On September 10, another study of a nontrivial attack, initiated, judging by a number of signs, appeared by the Chinese-language cyber-grouping LuckyMouse.
The functionality of the Trojan program is quite traditional: it provides the ability to connect remotely to an infected machine, conducts reconnaissance of the local network, communicates with the command server and tracks the user's network traffic.
Three features of the malware are interesting. First, it is a network traffic filtering driver that uses a legitimate digital certificate issued by VeriSign for LeagSoft, a software developer (including) to monitor data leaks. Obviously, this company was hacked, and the certificate provided a covert installation of software to intercept network communications.

Secondly, it’s noteworthy that the authors use an open source Trojan program in C.

Thirdly, the specialists of “Laboratories” have found signs in the driver indicating that the malicious code, although used for real attacks, is still under development. The debug messages come across the lines [test], the code mentions the well-known ports of common network services - POP3S, SMB, MSSQL, which are not used in any way later. Such a cybercriminal agile. The use of open source, in addition to speeding up development, also complicates the attribution of malware. If the trend develops, it will be harder to attribute attacks to certain groups than when they use a completely custom "easier to write" malicious code. However, in this case, the attribution did not cause any difficulties: the Trojan contacts the server, which was previously known as belonging to the LuckyMouse group.
Tesla hijacking without severe hacking
News .

Last year, the Keen Security Lab of the Chinese company Tencent published an interesting study of Tesla car security systems. In it, an electric car was hacked the way computer hackers would do: via a wireless connection and / or a web browser embedded in the entertainment system of the machine. Using the newly discovered vulnerabilities, Chinese researchers, via the CAN control bus, reached the control systems of “vital” automobile bodies such as steering and brakes.
This is a fascinating, but not an easy way, also with incomprehensible prospects for realizing the attack in practice by real attackers. A group of researchers from Belgium took the path of real criminals and analyzed the communication between the car and the control panel. It turned out that the keyfob uses an unreliable 40-bit cipher to unlock and start the machine.
With the help of Raspberry Pi and a pair of radio communication blocks with a total cost of about $ 600, researchers have learned not only to intercept a team to open doors and play it - they were able to create a virtual copy of a key that can be used many times. The result was a very real attack: it is enough to intercept the radio transmission once between the real key and the car, and then you can control the machine from a copy. You can not only open the door, but also start the car and drive away.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism. And by the way, if you are using Tor Browser, upgrade to version 8. In the previous found a serious vulnerability .
