[Translation] Investigation of manipulations with the control panel. Part 1
- Transfer
- Recovery mode
Hello! Today we bring to your attention a translation of the article “Control Panel Forensics: Evidence of Time Manipulation and More ...” , author Chad Tilbury worked as a special agent in the US Air Force Special Investigation Office, and after that he began to deal with piracy in the American Film Distributors Association . This guy does not know about computer crime investigations from textbooks. So, let's begin!
The control panel is a long-known Windows tool that allows you to change a huge number of system settings. Using the control panel can be limited by using Group Policies, but in any case, some panel elements are available for most accounts (for some changes you need administrator rights). During the investigation, we can audit the use of the control panel in order to identify a wide range of user actions, such as:
The process of identifying individual changes in the system allows, at a minimum, to show which applets from the control panel were launched by the user and when this happened. Artifacts i.e. traces left in the system may provide additional information for our investigation. Particularly important is the context, the sequence of actions. Imagine that you identify how the control panel was used and see the following picture:
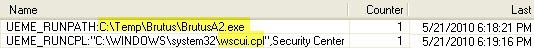
Access to the support center (this applet is called the Security Center in the English version) is not particularly interesting in itself. But it must be borne in mind that this applet was opened immediately after launching the well-known tool for selecting passwords on routers. As they say, feel the difference!
The Windows control panel consists of several applets, each represented by a * .cpl file. Applets
are usually stored in the% system root% \ System32 folder. The file 'control.exe' is used to open applets, but, like for other actions on Windows, there are an infinite number of ways - how to access the applet:
Using different methods leaves different traces in the system. Unfortunately, in some cases there may not be any traces at all, it depends on the applet execution methods and the version of Windows. The good news is that traces of using the control panel remain in different places of the system - you can almost always find the necessary data for an investigation.
Windows Prefetch Engine
The Windows Prefetch engine tracks application execution. Unlike regular applications, applets do not leave * .pf files in the C: \ Windows \ prefetch folder. We can assume that the “Control.exe” file will provide us with proof of the applet launch, but unfortunately its prefetch file (if it exists) only indicates that the Control Panel was open. In order to find out which of the applets started, we need to dig more deeply! When you run the applet, a link is created in the prefetch file for the RunDLL32.exe process. Multiple links in the prefetch files of the RunDLL32.exe process, pointing to the same applet, indicate that the applet was launched in various ways. Such links can be created as a result of the hash function calculation algorithm of the Windows Prefetch mechanism, which is well describedHexacorn’s blog.
The prefetch file for the RunDLL32.exe process may also contain a link to the applet (but not always - depending on the applet and on which process it was called). Finding such links in the prefetch files of the RunDLL32 and DLLHost processes is a laborious task, but it is not in vain that we celebrate the holiday of spring and labor , I promise a reward in the form of useful information - you will receive the time of the first and last applet launches in the system, and you will also learn how many times the applet has been run.
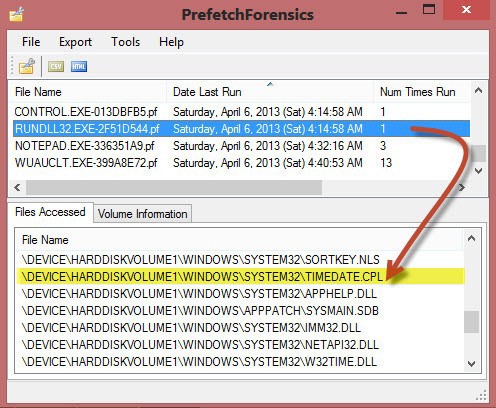
In the figure below, we see that the information extracted from the RUNDLL32.EXE-2F51D544.pf file indicates that the Date and Time applet was run at least once, on April 6, 2013 at 04:14:58 UTC.
While researching the prefetch files of the RunDLL32 process, I recommend that you carefully monitor various system applications, for example, the MMC plugins (COMPMGMT.MSC). An excellent tool for researching prefetch files was created by Mark Woan .
Windows Registry: Userassist (XP / Vista only)
Prefetch files are more or less reliable evidence, but their significant drawback is that they do not associate actions performed on the system with the user account. The "userassist" key, contained in the NTUSER.dat registry hive (NTUSER.DAT \ Software \ Microsoft \ Windows \ Current \ Version \ Explorer \ UserAssist), allows us to fill this gap.
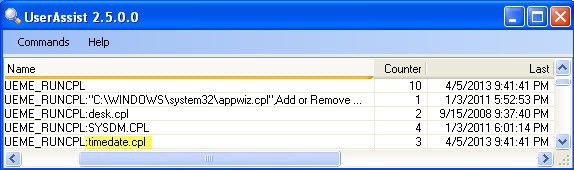
The figure shows the record about using the Control Panel made in Windows XP. It is necessary to pay attention to the prefix “UEME_RUNCPL”, with which each line begins. This is the identifier used in XP and Vista to indicate actions that are related specifically to the execution of Control Panel applets. In our case, we see that the user launched four different applets, only 10 times. The last time the applet was launched on May 4, 2013 at 21:41:41. UserAssist Evidence Tool was developed by Didier Stevens.
With the release of Windows 7, the UserAssist mechanism has undergone significant changes. The collection of reliable evidence of the launch of applets is not supported on Windows7 | 8 systems; instead, we can use the so-called. jump lists (jumplists), a source of information containing traces of applet launch in modern operating systems.
We will talk about this in the next part.
The control panel is a long-known Windows tool that allows you to change a huge number of system settings. Using the control panel can be limited by using Group Policies, but in any case, some panel elements are available for most accounts (for some changes you need administrator rights). During the investigation, we can audit the use of the control panel in order to identify a wide range of user actions, such as:
- Changes to the Firewall settings (firewall.cpl) are necessary in order to use unauthorized software in the future;
- Adding / changing accounts (nusrmgr.cpl);
- Disabling System Restore and Shadow Backup services (sysdm.cpl);
- Change the system time (timedate.cpl);
- Interaction with third-party applications that change security settings.
The process of identifying individual changes in the system allows, at a minimum, to show which applets from the control panel were launched by the user and when this happened. Artifacts i.e. traces left in the system may provide additional information for our investigation. Particularly important is the context, the sequence of actions. Imagine that you identify how the control panel was used and see the following picture:

Access to the support center (this applet is called the Security Center in the English version) is not particularly interesting in itself. But it must be borne in mind that this applet was opened immediately after launching the well-known tool for selecting passwords on routers. As they say, feel the difference!
Control Panel Overview
The Windows control panel consists of several applets, each represented by a * .cpl file. Applets
are usually stored in the% system root% \ System32 folder. The file 'control.exe' is used to open applets, but, like for other actions on Windows, there are an infinite number of ways - how to access the applet:
- Via the graphic interface of the Control Panel;
- Via the Start menu> Run;
- Using the Taskbar (for example, "Setting the date and time");
- Using the command line (syntax: control.exe timedate.cpl);
- Using the Windows 8 start screen, write “Control Panel”.
Using different methods leaves different traces in the system. Unfortunately, in some cases there may not be any traces at all, it depends on the applet execution methods and the version of Windows. The good news is that traces of using the control panel remain in different places of the system - you can almost always find the necessary data for an investigation.
Applet Launch Evidence Collection
Windows Prefetch Engine
The Windows Prefetch engine tracks application execution. Unlike regular applications, applets do not leave * .pf files in the C: \ Windows \ prefetch folder. We can assume that the “Control.exe” file will provide us with proof of the applet launch, but unfortunately its prefetch file (if it exists) only indicates that the Control Panel was open. In order to find out which of the applets started, we need to dig more deeply! When you run the applet, a link is created in the prefetch file for the RunDLL32.exe process. Multiple links in the prefetch files of the RunDLL32.exe process, pointing to the same applet, indicate that the applet was launched in various ways. Such links can be created as a result of the hash function calculation algorithm of the Windows Prefetch mechanism, which is well describedHexacorn’s blog.
The prefetch file for the RunDLL32.exe process may also contain a link to the applet (but not always - depending on the applet and on which process it was called). Finding such links in the prefetch files of the RunDLL32 and DLLHost processes is a laborious task, but it is not in vain that we celebrate the holiday of spring and labor , I promise a reward in the form of useful information - you will receive the time of the first and last applet launches in the system, and you will also learn how many times the applet has been run.
In the figure below, we see that the information extracted from the RUNDLL32.EXE-2F51D544.pf file indicates that the Date and Time applet was run at least once, on April 6, 2013 at 04:14:58 UTC.

While researching the prefetch files of the RunDLL32 process, I recommend that you carefully monitor various system applications, for example, the MMC plugins (COMPMGMT.MSC). An excellent tool for researching prefetch files was created by Mark Woan .
Windows Registry: Userassist (XP / Vista only)
Prefetch files are more or less reliable evidence, but their significant drawback is that they do not associate actions performed on the system with the user account. The "userassist" key, contained in the NTUSER.dat registry hive (NTUSER.DAT \ Software \ Microsoft \ Windows \ Current \ Version \ Explorer \ UserAssist), allows us to fill this gap.

The figure shows the record about using the Control Panel made in Windows XP. It is necessary to pay attention to the prefix “UEME_RUNCPL”, with which each line begins. This is the identifier used in XP and Vista to indicate actions that are related specifically to the execution of Control Panel applets. In our case, we see that the user launched four different applets, only 10 times. The last time the applet was launched on May 4, 2013 at 21:41:41. UserAssist Evidence Tool was developed by Didier Stevens.
With the release of Windows 7, the UserAssist mechanism has undergone significant changes. The collection of reliable evidence of the launch of applets is not supported on Windows7 | 8 systems; instead, we can use the so-called. jump lists (jumplists), a source of information containing traces of applet launch in modern operating systems.
We will talk about this in the next part.
