Samba4 as AD + file server
- Tutorial
In this article, I will look at the steps to prepare for using Samba4 as a domain controller, along with an additional file server based on Samba4 as well. What will we get in the end? Two configured servers with samba4, the first in the role of domain controller, the second in the role of member server with user files. I worked for this bundle for about a month, but I don’t have the right to share the final recipe ... I have a

little background: the company uses a file server based on samba3.6 with LDAP Backend, which contains a list of all users and groups with access rights. Access rights to directories are set using xattr_acl (Extended file attributes), a list of users with access groups is stored in LDAP. Actually, you need to move from this infrastructure to samba4 ...
1) We are preparing two servers for samba4, I am using the SUSE Linux Enterprise 11 Service Pack 3 (SLES11 SP3) distribution as an enterprise standard, so I will deploy everything based on it. Then you can build samba from the sources, if you wish, I use a ready-made assembly from sernet, which you can get for free just by registering on the portal - Portal Enterprise Samba
Sernet builds samba for several distributions - Debian, Ubuntu, RHEL, CentOS, SLES, openSUSE .
I used Samba4 version 4.1.6
2) On the first server, which will act as a DC for us, install sernet-samba-ad. If you have problems, you can look at the official instructions - Samba AD DC HOWTO. It is unforgettable to register the name of our future domain in your DNS server with an indication of our new server.
Next, we create the domain using samba-tools.
The system will ask you for several parameters that you need to specify, for example, such as a domain name, etc., as well as ask for a password. Actually only the domain name and you need to specify, all other questions can be left with answers by default. The administrator password must comply with the standard password policies in Windows, i.e. have at least one small and one large letter, as well as numbers, plus at least 8 characters.
Copy the newly configured samba config Kerberos to the default location.
To verify that Kerberos is working correctly, you can install krb5-client and verify that authentication works.
klist should show information on tickets, if everything is ok - go ahead.
It is necessary to correct the file / etc / default / sernet-samba.
Edit the line SAMBA_START_MODE = to the following.
After that, you can run the samba itself
If the launch was successful, you can assume that our domain controller has already been deployed.
We edit the file /etc/nsswitch.conf so that the system would see users of the domain and group, and also could normally set the rights to files. We bring these two lines to the following form:
Restart the system and see if it works ... using getent passwd and getent group. We should see groups and users from our domain. You can read the official instructions in more detail about this step - Samba4 / Winbind It
remains to enter any Windows machine for administration into the domain, I think there will be no problems with this.
3) On the Windows machine that we entered into the domain, install admin pack. We use equipment for user management in AD.
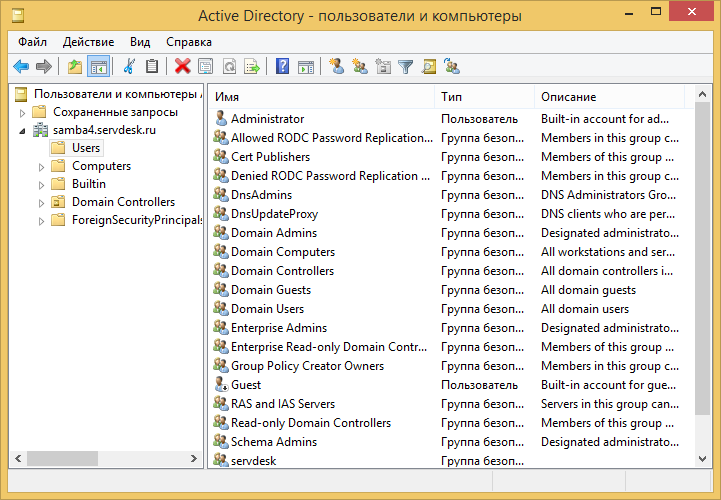
Each group and user needs to be assigned unix uid \ gid for the future normal operation of xattr_acl on our second server.
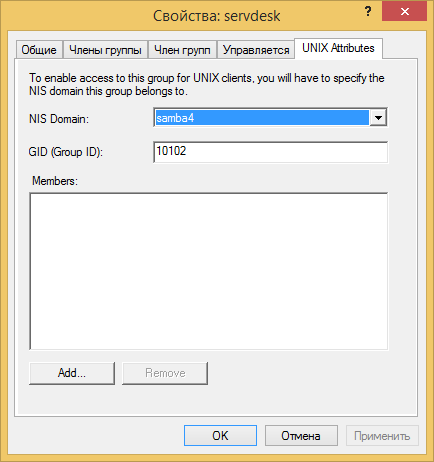
4) It's time to start preparing our second server, which will act as a member server and will be a file server in the domain.

Install sssd, in the standard SLES11 repository there is version 1.9.4, it is quite suitable for us. Also install sssd-tools. sssd is needed to get users with unix attributes from our domain. You can read more about configuration in the official instructions - Local user management and authentication / sssd
We will configure communication with AD through Kerberos.
On the first server (DC), you need to export keytab from Kerberos.
For security, we’ll chop off the extra rights. Copy the keytab file to our second server in the same way.
Editing sssd.conf
Remember to fix the name of your DC and your domain on your own. We put sssd in autorun, we reboot the server.
Next, you can reset the cache and check our groups with users.
The list should include our groups and users with uid \ gid, which we specified in the AD snap-in on Windows.
5) We proceed to configure samba4 on the second server, install sernet-samba-nmbd, sernet-samba-smbd, sernet-samba-winbind and all the dependencies for them. You can read more about the configuration in the official instructions - Samba / Domain Member
Create smb.conf, my file looks like this:
Do not forget to fix the config for yourself, you need to change the domain name to yours.
We correct our hosts file in it, we must directly specify the name of our member server, otherwise the DNS zones will not be automatically updated in AD.
Run the procedure for entering our domain.
You will be required to enter the administrator password.
Actually after this, our member server is already in the domain.
You can try the machine from Windows to connect to it under your login password and create some folder to check the rights ...
Create folder 123, check the rights.
As you can see, all rights are set correctly.
Next, you can start transferring users to our new domain, as well as set permissions for folders in accordance with your wishes.
You can also use glusterfs coupled with samba4 to create a fault-tolerant file server, but that's another story ...
If anyone has any questions, I will be happy to help.

little background: the company uses a file server based on samba3.6 with LDAP Backend, which contains a list of all users and groups with access rights. Access rights to directories are set using xattr_acl (Extended file attributes), a list of users with access groups is stored in LDAP. Actually, you need to move from this infrastructure to samba4 ...
1) We are preparing two servers for samba4, I am using the SUSE Linux Enterprise 11 Service Pack 3 (SLES11 SP3) distribution as an enterprise standard, so I will deploy everything based on it. Then you can build samba from the sources, if you wish, I use a ready-made assembly from sernet, which you can get for free just by registering on the portal - Portal Enterprise Samba
Sernet builds samba for several distributions - Debian, Ubuntu, RHEL, CentOS, SLES, openSUSE .
I used Samba4 version 4.1.6
2) On the first server, which will act as a DC for us, install sernet-samba-ad. If you have problems, you can look at the official instructions - Samba AD DC HOWTO. It is unforgettable to register the name of our future domain in your DNS server with an indication of our new server.
Next, we create the domain using samba-tools.
samba-tool domain provision --use-rfc2307 --interactive
The system will ask you for several parameters that you need to specify, for example, such as a domain name, etc., as well as ask for a password. Actually only the domain name and you need to specify, all other questions can be left with answers by default. The administrator password must comply with the standard password policies in Windows, i.e. have at least one small and one large letter, as well as numbers, plus at least 8 characters.
Copy the newly configured samba config Kerberos to the default location.
cp /var/lib/samba/private/krb5.conf /etc/krb5.conf
To verify that Kerberos is working correctly, you can install krb5-client and verify that authentication works.
kinit administrator@EXAMPLE.COM
klist
klist should show information on tickets, if everything is ok - go ahead.
It is necessary to correct the file / etc / default / sernet-samba.
Edit the line SAMBA_START_MODE = to the following.
SAMBA_START_MODE="ad"
After that, you can run the samba itself
/etc/init.d/sernet-samba-ad start
If the launch was successful, you can assume that our domain controller has already been deployed.
We edit the file /etc/nsswitch.conf so that the system would see users of the domain and group, and also could normally set the rights to files. We bring these two lines to the following form:
passwd: compat winbind
group: compat winbind
Restart the system and see if it works ... using getent passwd and getent group. We should see groups and users from our domain. You can read the official instructions in more detail about this step - Samba4 / Winbind It
remains to enter any Windows machine for administration into the domain, I think there will be no problems with this.
3) On the Windows machine that we entered into the domain, install admin pack. We use equipment for user management in AD.

Each group and user needs to be assigned unix uid \ gid for the future normal operation of xattr_acl on our second server.

4) It's time to start preparing our second server, which will act as a member server and will be a file server in the domain.

Install sssd, in the standard SLES11 repository there is version 1.9.4, it is quite suitable for us. Also install sssd-tools. sssd is needed to get users with unix attributes from our domain. You can read more about configuration in the official instructions - Local user management and authentication / sssd
We will configure communication with AD through Kerberos.
On the first server (DC), you need to export keytab from Kerberos.
samba-tool domain exportkeytab /etc/krb5.sssd.keytab --principal=имя_вашего_DC$
chown root:root /etc/krb5.sssd.keytab
chmod 600 /etc/krb5.sssd.keytab
For security, we’ll chop off the extra rights. Copy the keytab file to our second server in the same way.
Editing sssd.conf
[sssd]
services = nss, pam
config_file_version = 2
domains = default
[nss]
[pam]
[domain/default]
ad_hostname = smbad.samba4.servdesk.ru
ad_server = smbad.samba4.servdesk.ru
ad_domain = samba4.servdesk.ru
ldap_schema = rfc2307bis
id_provider = ldap
access_provider = simple
# on large directories, you may want to disable enumeration for performance reasons
enumerate = true
auth_provider = krb5
chpass_provider = krb5
ldap_sasl_mech = gssapi
ldap_sasl_authid = smbad$@SAMBA4.SERVDESK.RU
krb5_realm = SAMBA4.SERVDESK.RU
krb5_server = smbad.samba4.servdesk.ru
krb5_kpasswd = smbad.samba4.servdesk.ru
ldap_krb5_keytab = /etc/krb5.sssd.keytab
ldap_krb5_init_creds = true
ldap_referrals = false
ldap_uri = ldap://smbad.samba4.servdesk.ru
ldap_search_base = dc=samba4,dc=servdesk,dc=ru
dyndns_update=false
ldap_id_mapping=false
ldap_user_object_class = user
ldap_user_name = samAccountName
ldap_user_uid_number = uidNumber
ldap_user_gid_number = gidNumber
ldap_user_home_directory = unixHomeDirectory
ldap_user_shell = loginShell
ldap_group_object_class = group
ldap_group_name = cn
ldap_group_member = member
Remember to fix the name of your DC and your domain on your own. We put sssd in autorun, we reboot the server.
Next, you can reset the cache and check our groups with users.
sss_cache -UG
getent group
...
Schema Admins:*:10110:Administrator
Domain Users:*:10103:
DnsAdmins:*:10117:
servdesk:*:10102:test
The list should include our groups and users with uid \ gid, which we specified in the AD snap-in on Windows.
5) We proceed to configure samba4 on the second server, install sernet-samba-nmbd, sernet-samba-smbd, sernet-samba-winbind and all the dependencies for them. You can read more about the configuration in the official instructions - Samba / Domain Member
Create smb.conf, my file looks like this:
[global]
workgroup = SAMBA4
security = ADS
realm = SAMBA4.SERVDESK.RU
# map untrusted to domain = Yes
idmap config *:backend = tdb
idmap config *:range = 70001-80000
# idmap config SAMBA4:default = yes
idmap config SAMBA4:backend = ad
idmap config SAMBA4:schema_mode = rfc2307
idmap config SAMBA4:range = 500-40000
# idmap_ldb:use rfc2307 = yes
winbind nss info = rfc2307
winbind trusted domains only = no
winbind use default domain = yes
# winbind enum users = yes
# winbind enum groups = yes
#create mask = 0777
#directory mask = 0777
vfs objects = acl_xattr btrfs
map acl inherit = Yes
store dos attributes = Yes
[data1]
path = /data1/
read only = no
Do not forget to fix the config for yourself, you need to change the domain name to yours.
We correct our hosts file in it, we must directly specify the name of our member server, otherwise the DNS zones will not be automatically updated in AD.
127.0.0.1 localhost
127.0.0.1 samba3.samba4.servdesk.ru samba3
Run the procedure for entering our domain.
net ads join -U administrator
You will be required to enter the administrator password.
Actually after this, our member server is already in the domain.
You can try the machine from Windows to connect to it under your login password and create some folder to check the rights ...
Create folder 123, check the rights.
getfacl /data1/123
# file: data1/123
# owner: test
# group: Domain\040Users
user::rwx
user:test:rwx
group::r-x
group:servdesk:rwx
group:Domain\040Users:r-x
mask::rwx
other::r-x
default:user::rwx
default:user:test:rwx
default:group::r-x
default:group:servdesk:rwx
default:group:Domain\040Users:r-x
default:mask::rwx
default:other::r-x
As you can see, all rights are set correctly.
Next, you can start transferring users to our new domain, as well as set permissions for folders in accordance with your wishes.
You can also use glusterfs coupled with samba4 to create a fault-tolerant file server, but that's another story ...
If anyone has any questions, I will be happy to help.
