Security Week 33: for whom the monitor oscillates?
 Neil Stevenson’s book Kryptonomicon, about which we had a blog post , describes various types of information leaks through third-party channels. There are practical, like van Eyck interception , and purely theoretical, for red wits: tracking a person’s movements on the beach on the other side of the ocean, building a city map by how its inhabitants overcome the curbstone at intersections (this can now be implemented with accelerometers, only curbs everywhere cut down
Neil Stevenson’s book Kryptonomicon, about which we had a blog post , describes various types of information leaks through third-party channels. There are practical, like van Eyck interception , and purely theoretical, for red wits: tracking a person’s movements on the beach on the other side of the ocean, building a city map by how its inhabitants overcome the curbstone at intersections (this can now be implemented with accelerometers, only curbs everywhere cut down On August 21, scientists from universities in the United States and Israel published a work that implements a similar idea: how to reconstruct a picture by tracking radiation from a monitor. They used a rather easy-to-use sound as a side channel for data leakage. It probably happened to you too: it is worth inaccurately putting wires or an unsuccessful combination of a monitor and speakers gets caught - and you start to hear a nasty squeak that also changes depending on the direction of scrolling the text with the mouse. The work is devoted to the analysis of such sound radiation. Scientists managed to “see” large text on the attacked system, identify the visited site and even spy on the password typed on the on-screen keyboard.
Considering other discoveries in the sphere of attacks along the side channels, it is possible that we are confidently moving towards the moment when this line of research will change not only qdɐɓnǝvɐʞ, but also all our ideas about digital privacy.
Sources of today's post: news in Russian, a detailed description of human words in English, and the original research paper .
Initially, the researchers wanted to determine if there was any sound exhaust from the monitor in the easiest situation for leaks, when black and white bands were exchanged on the screen. The installation for "listening" looked like this:
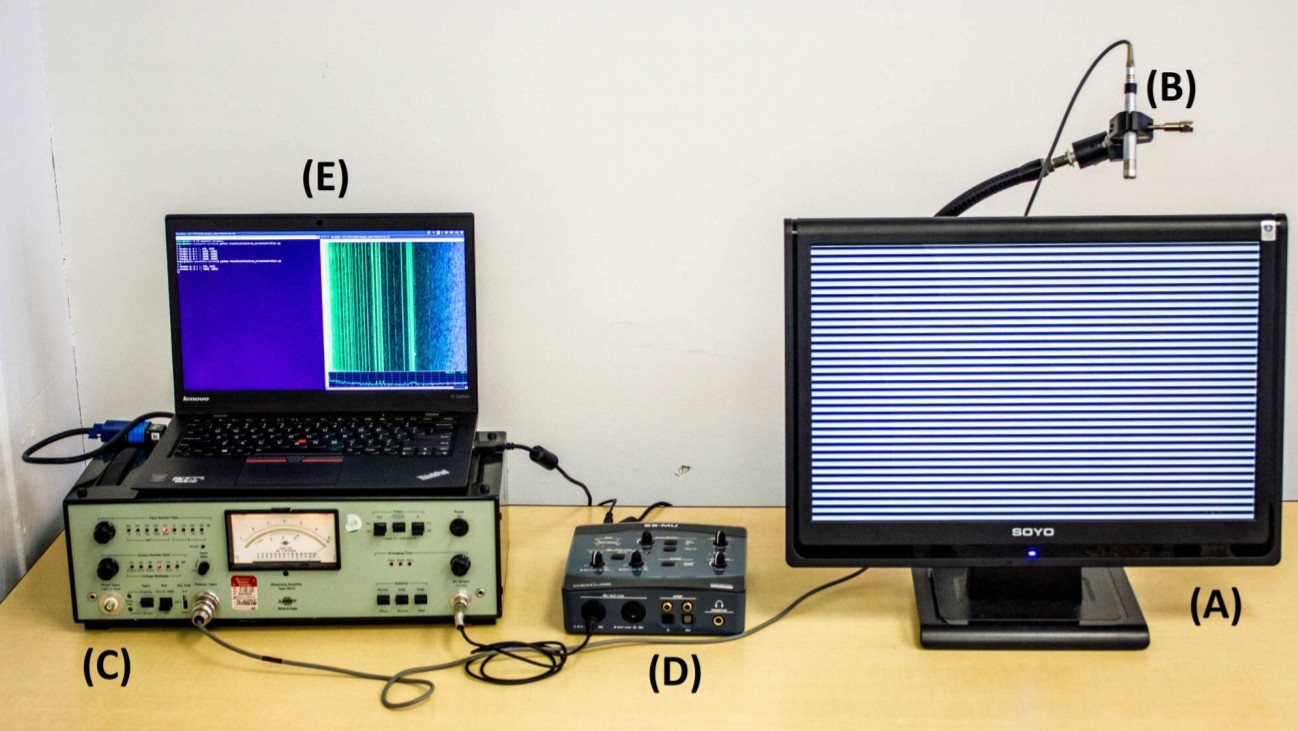
A very high-quality microphone and a preamp were used, but a regular sound card was used to capture the signal.
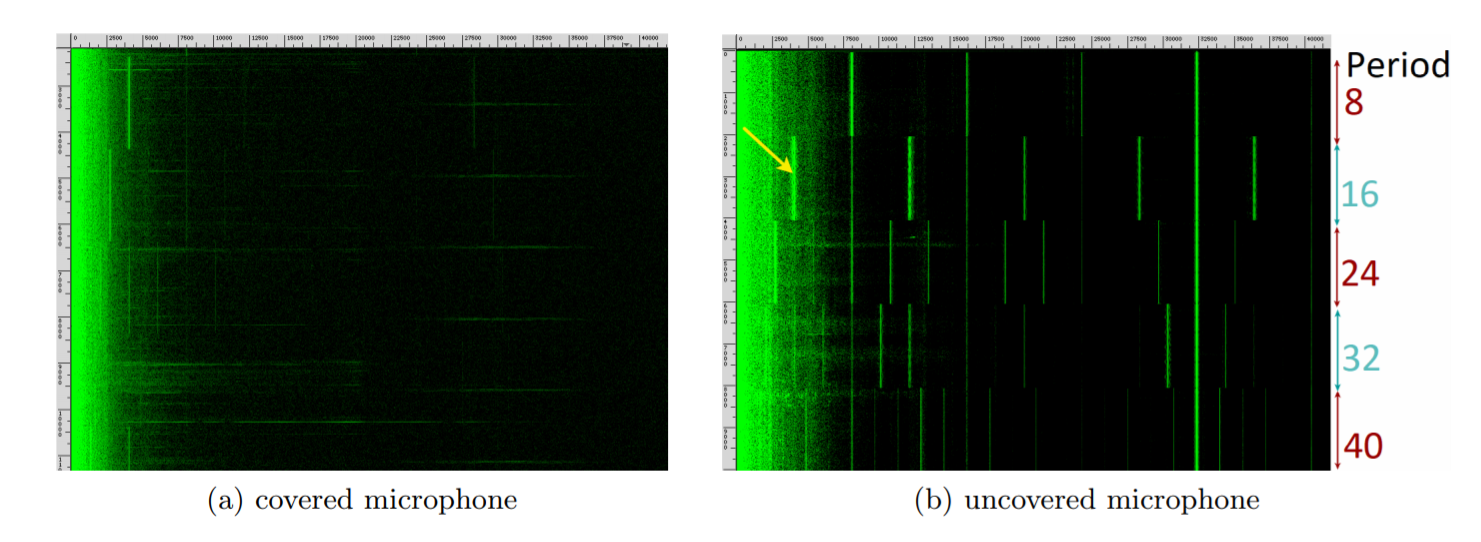
Here you can see how the bands on the monitor generate a clear pattern, both in the ultrasound region and in the audible range. The picture on the left is that the researchers checked that they were dealing with sound, and not with electromagnetic radiation, which was accidentally aimed at wires, at a laptop or at a preamplifier. All in the best traditions of captaincy: if you close the microphone with a rag, the sound disappears. Different monitors were tried - from the freshest to 16-year-old products, with different types of backlighting. “Noise,” in one way or another, published everything; it remains only to extract some meaning from this sound pollution.
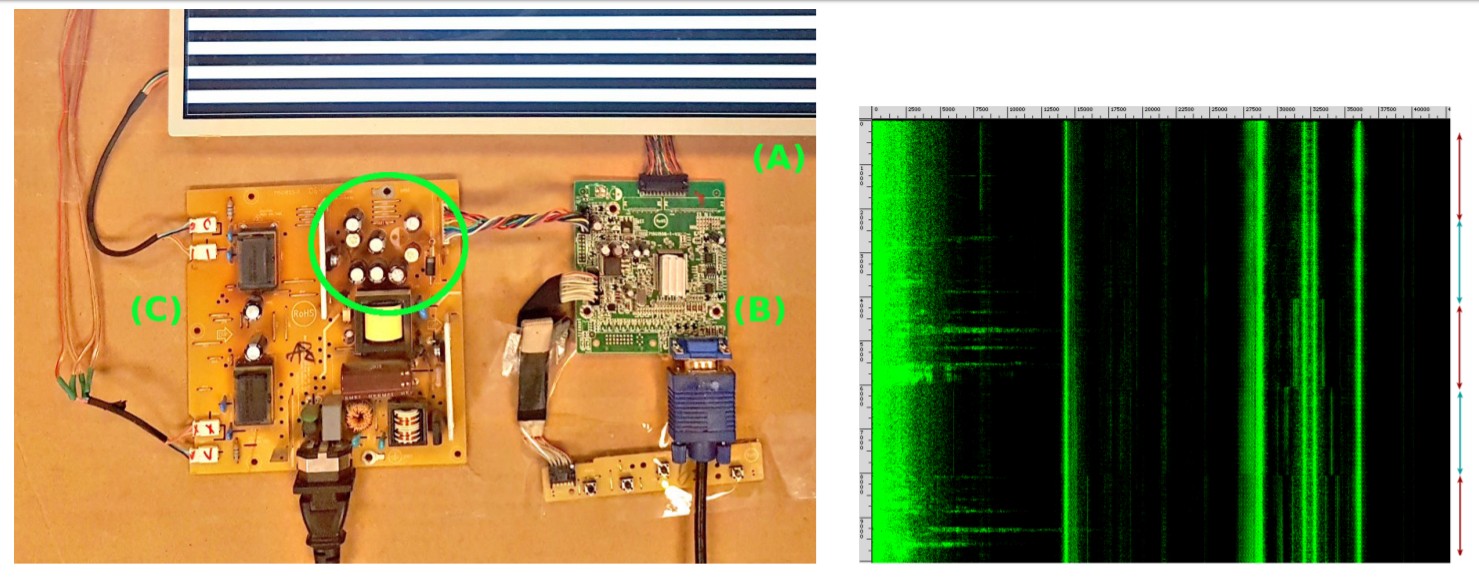
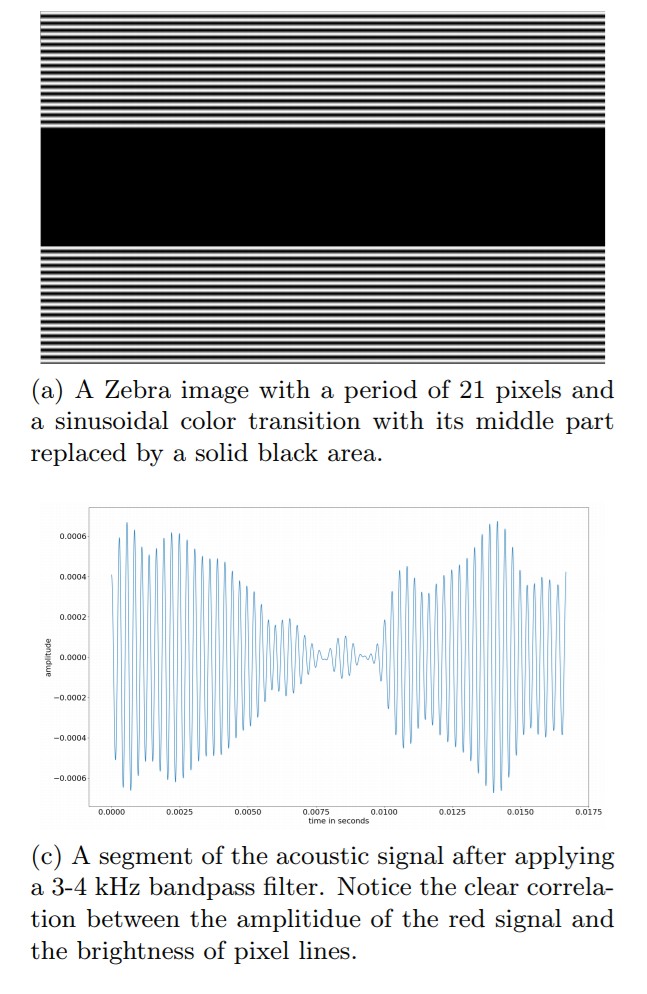
Oh yeah, at first it would be nice to identify, and who, in fact, makes a noise. To do this, one of the monitors was disassembled and was able to localize the source: it turned out, the power supply. The frequency of the radiation varies depending on the size of the image, the size of the individual element (originally tried to draw a chessboard) and the frame refresh rate. Then they began to change the image, inserting, for example, a black rectangle between black and white stripes. The amplitude of the signal accordingly fell where the monitor did not need to display anything on the screen.
At this stage, scientists are faced with a lot of difficulties, starting with the "floating" frame refresh rate, which, albeit slightly, was different from the reference 60 hertz. The difficulties were heroically overcome. Moreover, it turned out that to record the radiation does not necessarily use a high-quality microphone. Enough lying under the screen of the phone. Or a webcam with a microphone, which is usually bolted to the display. Or even standing next to a smart column from Google or Amazon. In all cases, the signals necessary for analysis are preserved.
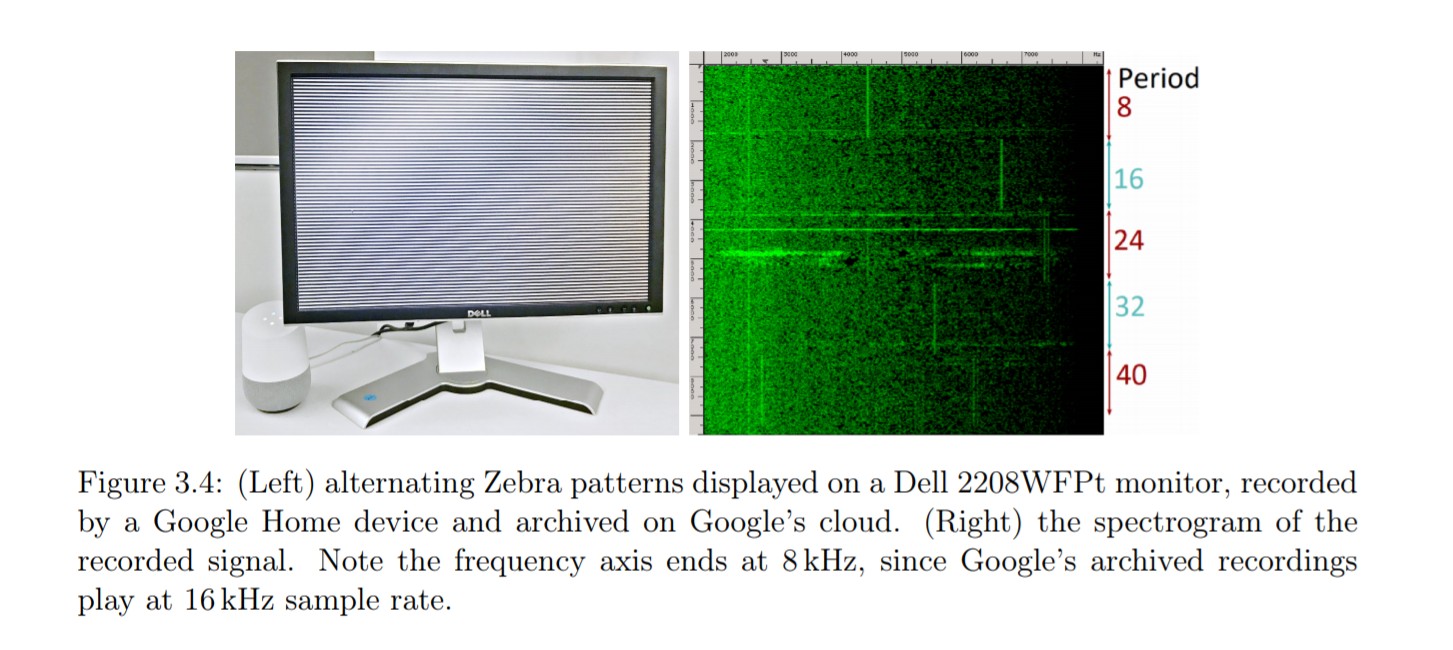
But for data analysis, machine learning algorithms were used, more precisely, convolutional neural networks. For training, a combination of a screenshot of the screen and a half-second sound recording made in the corresponding time interval was used. As a result:
- Almost guaranteed (with a probability of up to 100%) it was possible to intercept the password entered using the on-screen keyboard.
- With a high (88–98%) probability, it was possible to recognize the text displayed on the monitor.
- From the same high (from 90.9%) accuracy, it turned out to identify the displayed website, one of the 97 from the list of the most frequently visited.
And now the text in small print. All experiments one way or another have their limitations. For example, the password entered on the on-screen keyboard consisted only of letters of the English alphabet. Recognized with high probability text - it was the letters height of 175 pixels. The most important thing is that in order to carry out this attack, it is advisable to steal a monitor at night, to train a neural network on it, and then return it back so that no one will notice. The fact is that the accuracy of data identification drops sharply even when replacing a monitor with a neighboring model in the line of the same manufacturer.
But this is a research work, the authors did not need to follow someone really, the main thing is to show the opportunity. And if you start making unfounded assumptions (for example, that now someone will develop this topic before practical application), the situation turns out, ahem, interesting. If you are such an important person that they can eavesdrop on you, it turns out that they can also watch you through the same microphone. Moreover, it is not even necessary to enclose a bug: the “prepared” smartphone of the victim will fix the necessary audio data. With a high probability, something interesting will be stolen from your display during a Skype conference call. And the existing recordings of your voice can be analyzed after the fact regarding the contents of the screen nearby.
What are the recommended ways to protect? Isolate the “sounding” component of the monitor with
It is possible that with time all these small achievements of science and technology will gain a critical mass and radically change our world, shift the paradigm and blow up (no matter how literally) the Internet. Or do not change and do not blow up, remaining purely technical experiments. We are still monitoring.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
