NSA infected more than 50,000 networks worldwide with viruses
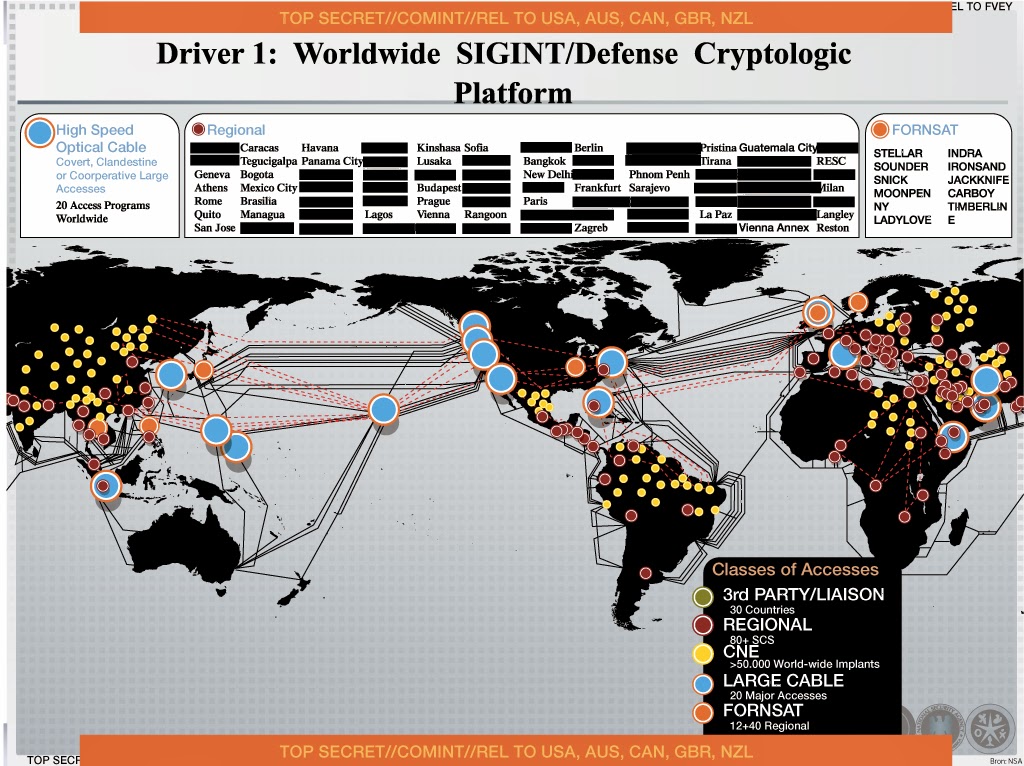
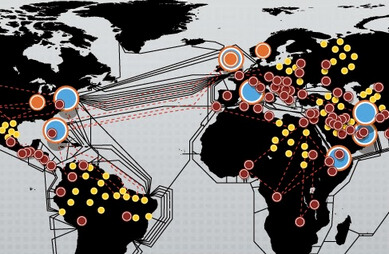 The Dutch newspaper NRC Handelsblad publishes a new batch of documents from a former NSA employee, Edward Snowden . The slide of the NSA presentation from 2012 shows ways to obtain information from around the world, including using the so-called CNE ( Computer Network Exploitation - a method of obtaining information from closed computer networks by infecting individual machines). According to the information on the slide, already in 2012, more than 50 thousand around the world were compromised in this way, some of which, judging by the presented map, are located in Russia.
The Dutch newspaper NRC Handelsblad publishes a new batch of documents from a former NSA employee, Edward Snowden . The slide of the NSA presentation from 2012 shows ways to obtain information from around the world, including using the so-called CNE ( Computer Network Exploitation - a method of obtaining information from closed computer networks by infecting individual machines). According to the information on the slide, already in 2012, more than 50 thousand around the world were compromised in this way, some of which, judging by the presented map, are located in Russia. To carry out such computer attacks, the NSA created a special unit of TAO ( Tailored Access Operations) According to open sources, more than a thousand professional hackers work in this unit. In an anonymous interview with Bloomberg Businessweek, former US officials said the unit uses an automated system to hack and collect information from compromised networks, which has a “catch” of about 2 PB per hour.

In August 2013, The Washington Post published an article.on special operations of the Tailored Access Operations unit, in which the number of penetrations was estimated at 20,000 cases in 2008 alone. It turns out that by 2012 the number of successful attacks increased to 50,000. The cyber operations units of all TAOs are becoming increasingly important to the NSA. Computer hacks are relatively inexpensive and make it possible to obtain information that the special services would not have access to otherwise.
One example of this method was already discovered in September 2013 at the Belgian telecommunications company Belgacom. For several years, the British intelligence service ( GCHQ) used a Trojan on the Belgacom network to intercept the communications of the company's customers. The Belgacom network was compromised by infecting certain computers of company employees who were lured for infection to the specially created Linkedin fake page.
Recent data suggests that NSA network compromise programs operate in many countries around the world, including those that are rather poorly developed in the field of IT security, such as Venezuela and Brazil. In such countries, attacks on critical government resources may simply go unnoticed for years. This has already happened, for example, in Iran, where the Stuxnet virus for a long time quietly spread and successfully completed its task of disabling centrifuges for the separation of uranium isotopes in a factory in Natanz.
