Testing Palo Alto Networks Solutions: How to Deny Access to Social Networks and Applications
 Hello dear high tech lovers. We continue our series of articles about advanced pieces of iron.
Hello dear high tech lovers. We continue our series of articles about advanced pieces of iron. Today I will talk about Palo-Alto Networks solutions and show how to configure various policies, in particular prohibiting the use of a social network or other kind of application to a specific user.
Palo Alto Networks produces pretty good firewalls, content filters, etc. things in one device. As I understand it from the words of the company representative, the main developers left Juniper networks, where they worked to create a series of SSG devices.
Anyway. Most of this is not interesting, and everyone is waiting for screenshots. Let's go:
1. Home and dashboard . In principle, everything is clear here (I hope).
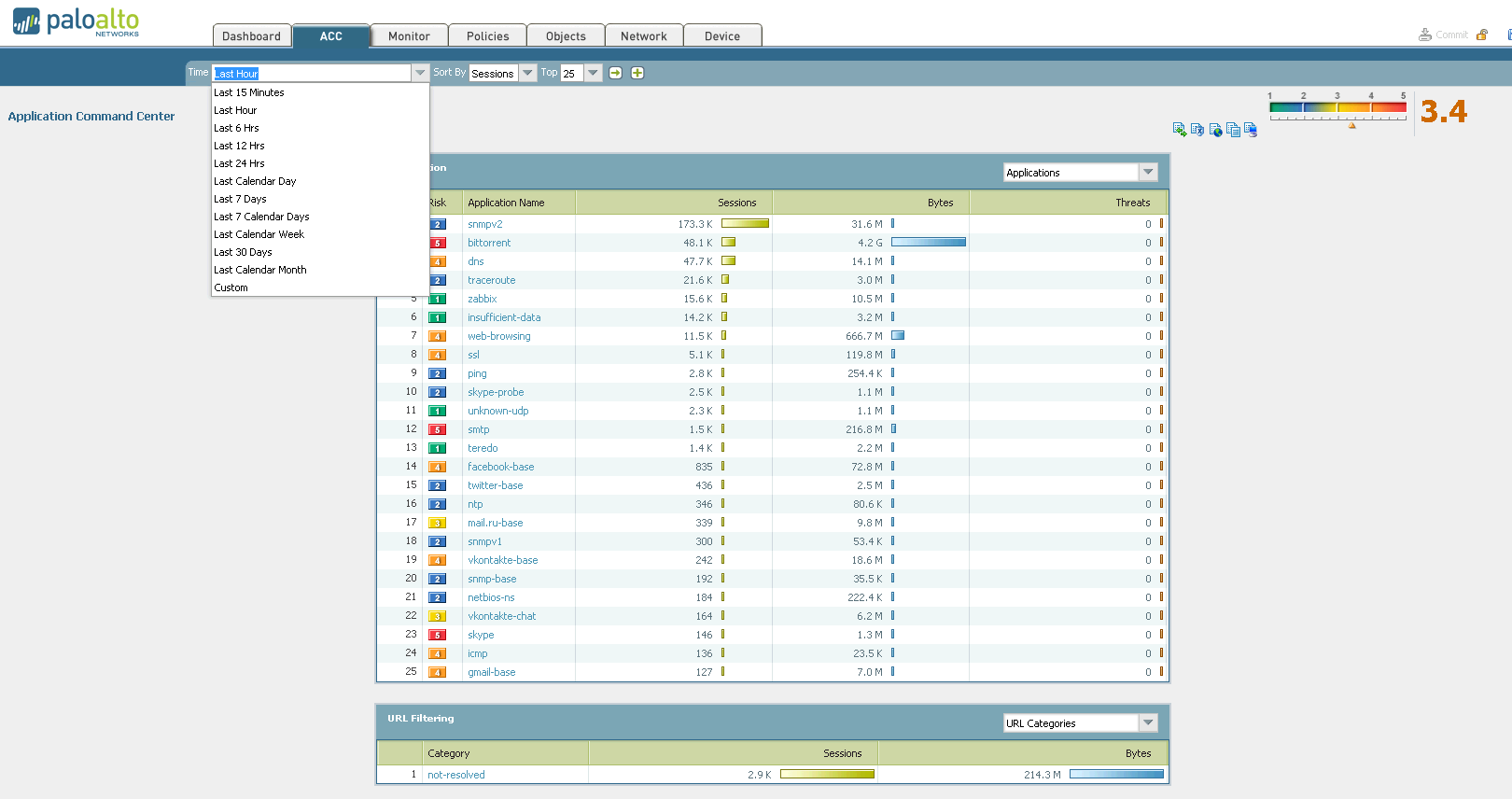
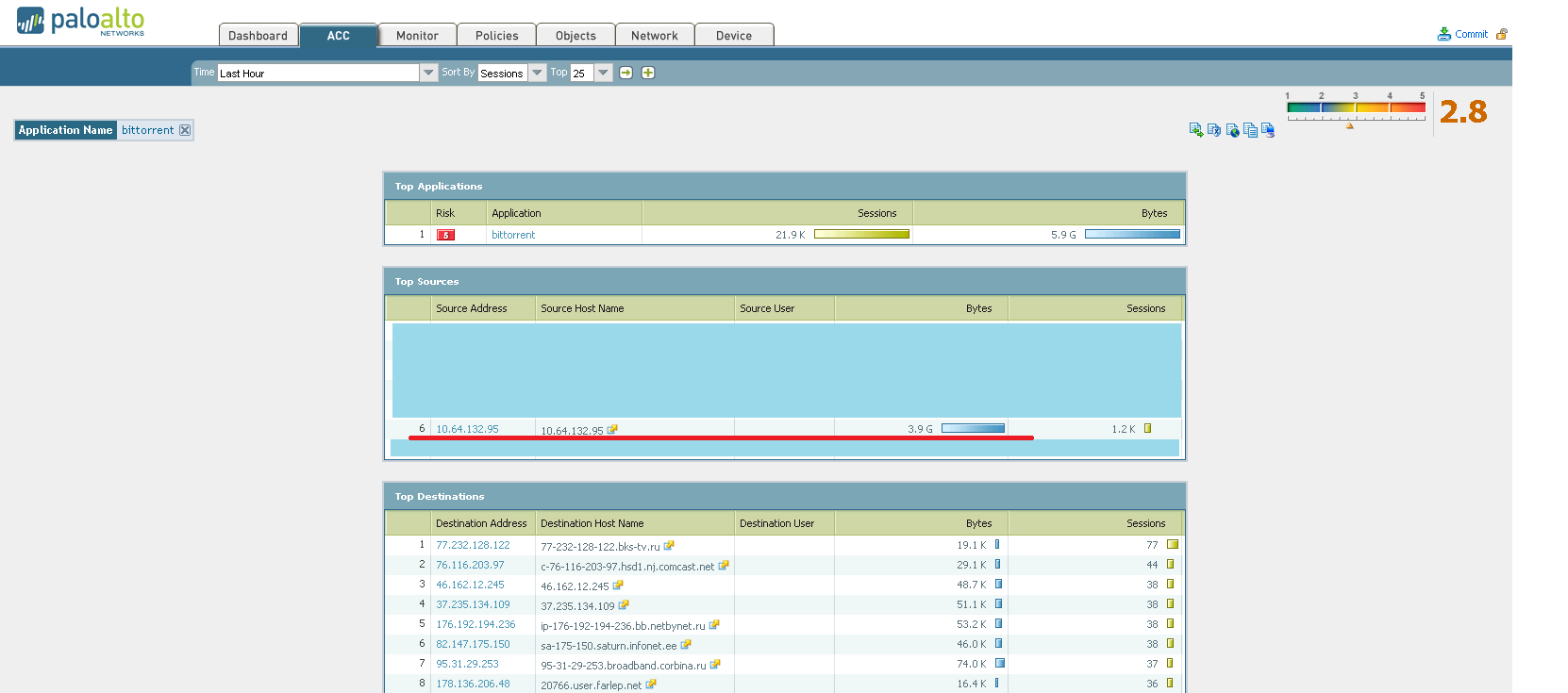
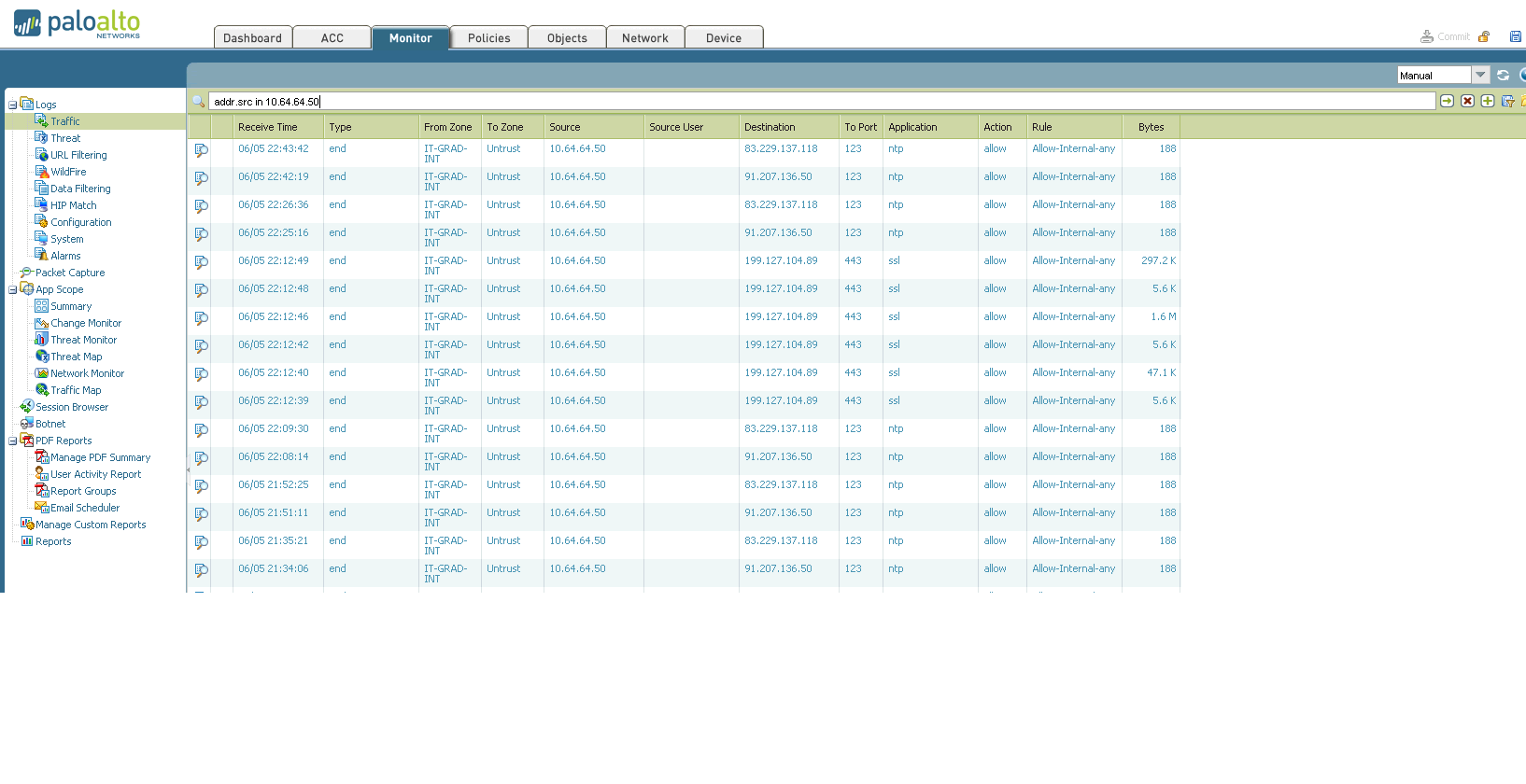
2. ACC (or Application Command Center). Here we can see what type of traffic was seen in a given period of time, who was the generator or initiator of the traffic, etc. The following screenshot clearly shows how one of our guests is struggling to pump out the latest version of the image with a freely distributed operating system. 3. Go ahead - the Monitoring tab. I think it makes no sense to explain its meaning. I only note that it is very convenient for her to use when debugging, because Among the total bacchanalia of IP packets, we can filter out only what we need. 4. Politicians.
Here you can set the relationship policies between security zones (which are described later), NAT pools and rules, and other things that are undoubtedly important in our lives: QoS, Captive portal, DoS protection, etc. 5. Objects. On this tab, various entities are presented, which we can group according to various criteria, set new ones, etc. In the future, we can use these newly created settings in various access policies. Among other things, application signatures are defined here (and since Palo Alto can recognize them, we can separately filter the traffic of an application. This is described in more detail at the end of the article). 6. Network.
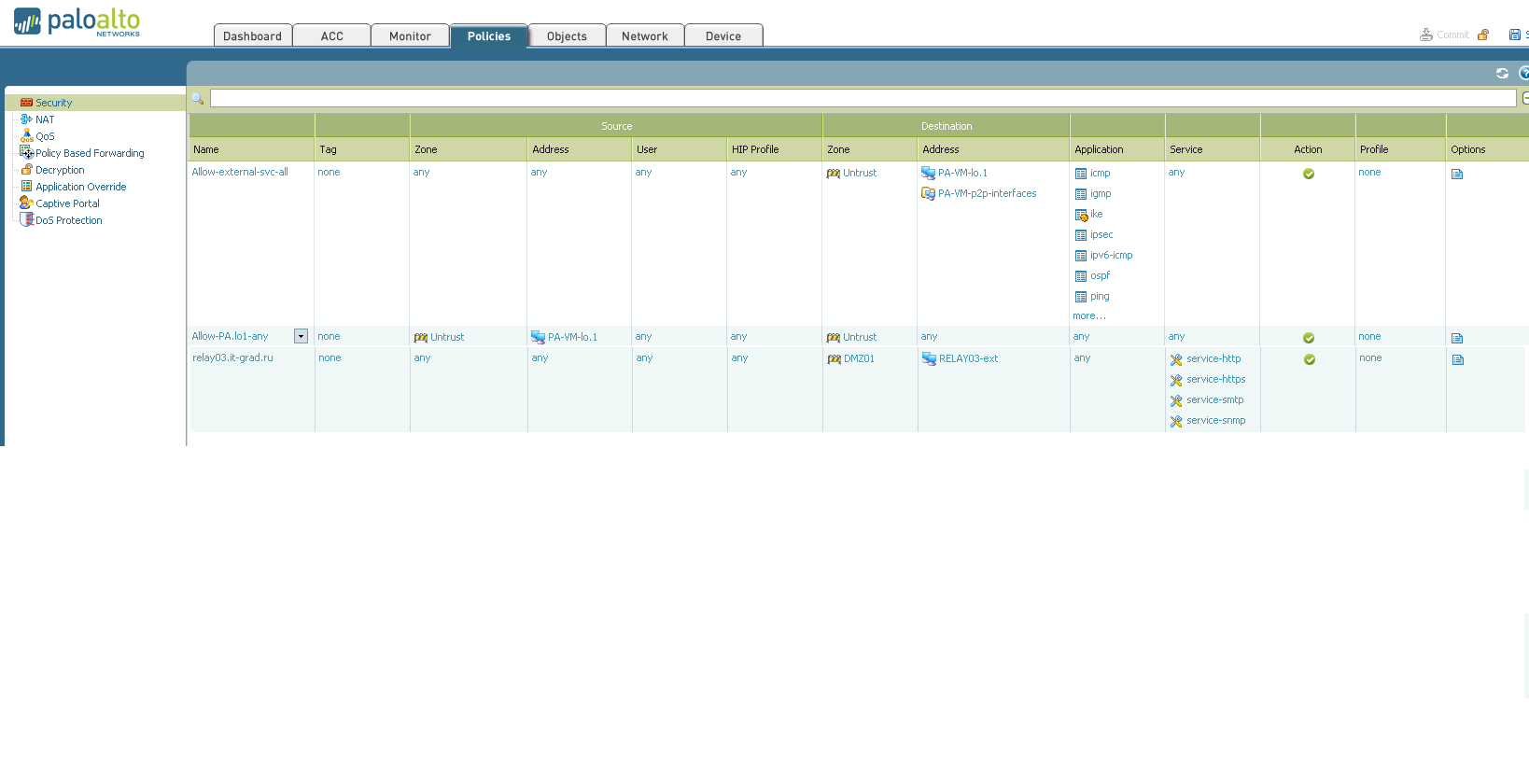
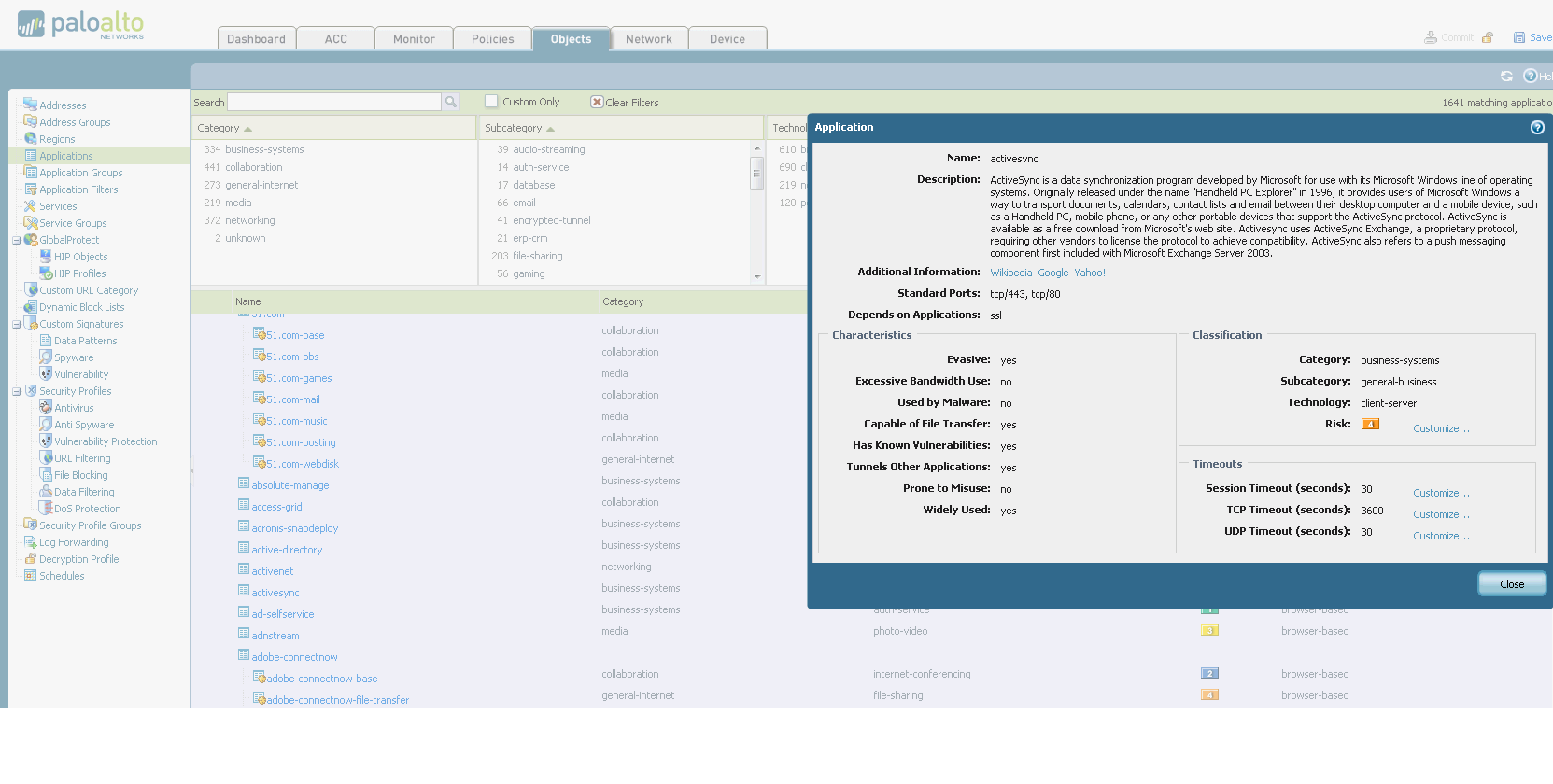
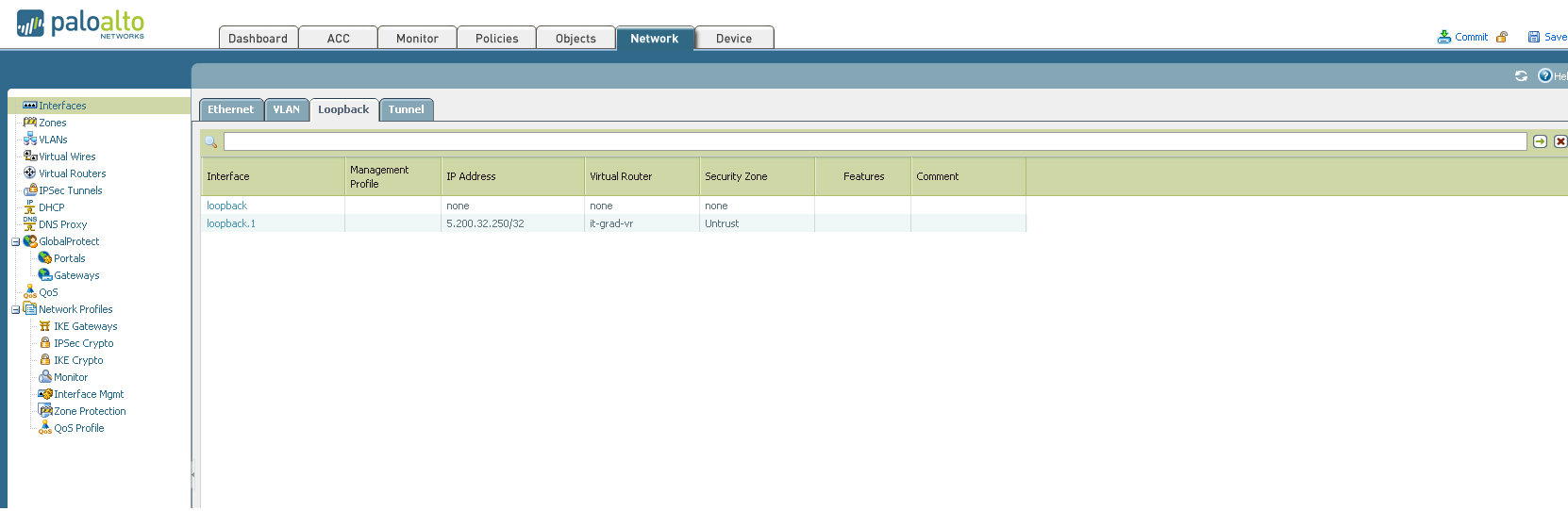
The purpose of this tab is to configure everything that relates to the network in our device. Starting from issuing addresses to interfaces and ending with setting up IPSec tunnels (Yes! Palo Alto supports IPSec tunnels). 7. Device. Various global device settings are stored here. Everything that can be configured is on the left on the screen. Let's try to write a policy prohibiting the use of a social network for schoolchildren to one computer (since the user of this computer behaved badly): 1. 2. 3. 4. 5. The user tries to get to Vkontakte and here - BAM! Does not work. And we triumphantly observe his useless attempts:
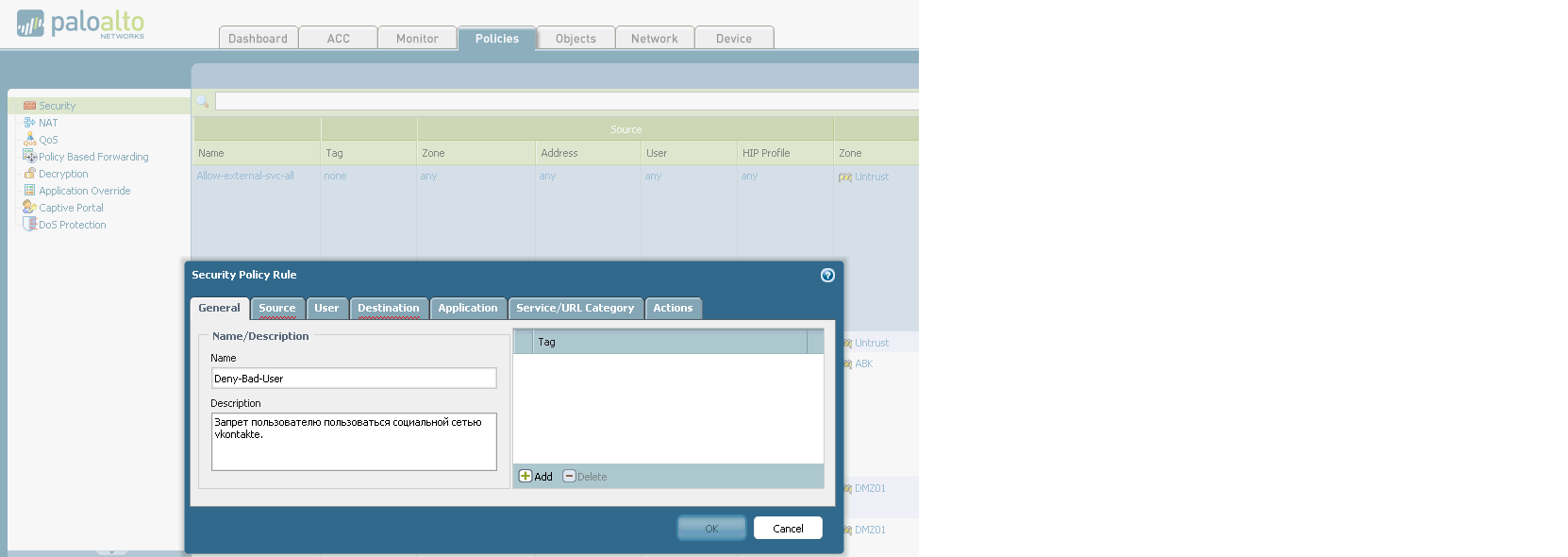
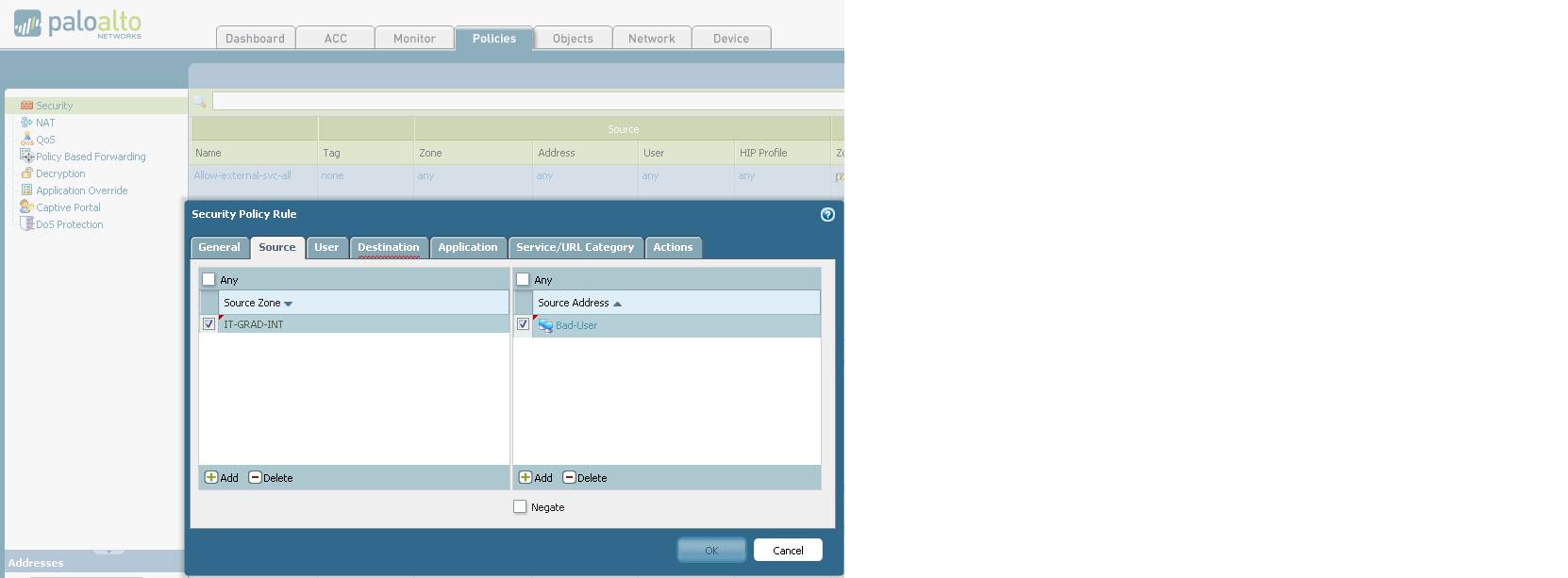
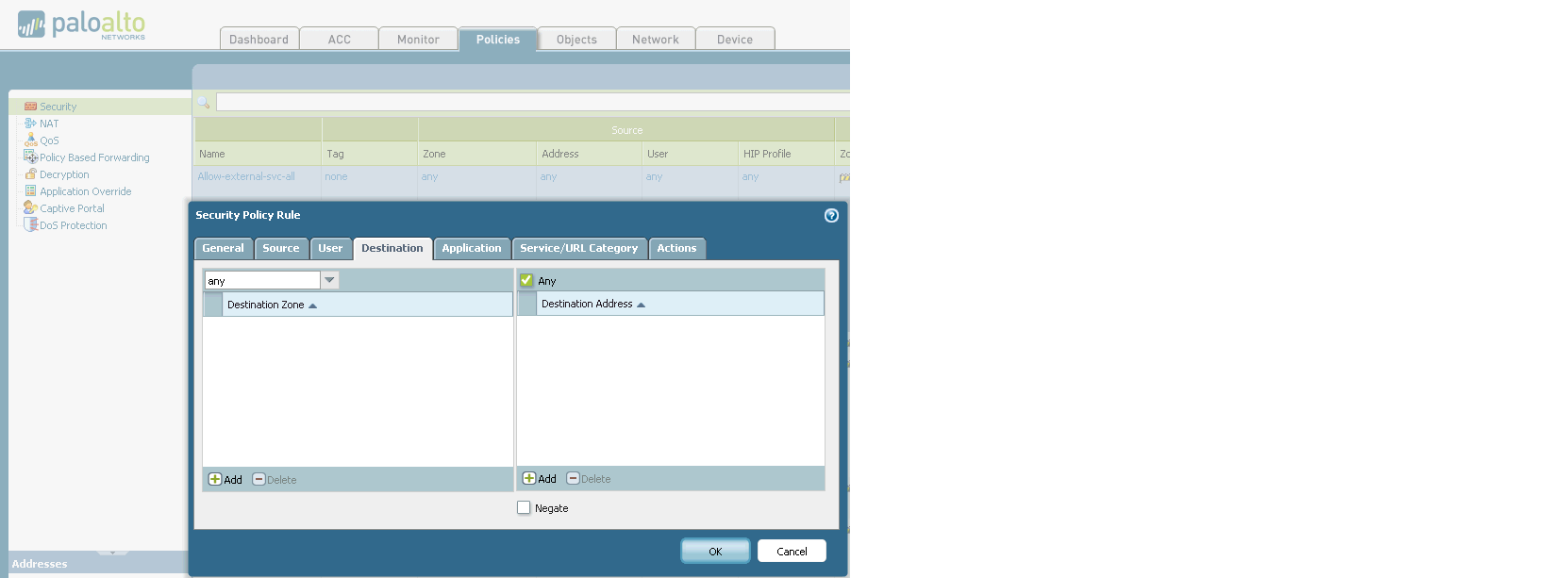


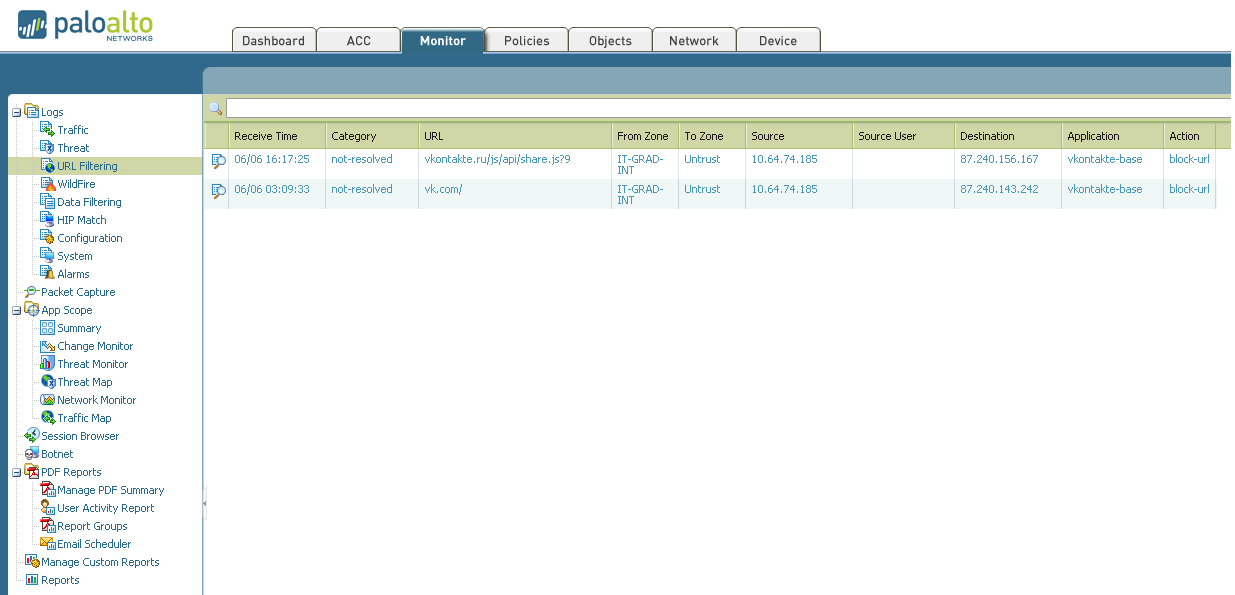
On the other hand, you will not surprise anyone with such filtering now. I partially understand you, so let's complicate the task a bit. Let's try to filter out the application that is used to access another social network, but at the same time leave access there via WEB.
So, imagine that we are building another floor of our 18-story office. Everywhere in the building there is a wifi access point with an open SSID (yes, we are not greedy for the Internet). On the 18th floor, workers are completing repairs. One of them (let's call it Ashot), instead of finishing laying 30 square meters of tile, connected to the network and is using an instant messenger to conduct active correspondence with another “lady of the heart”. At the same time, suppose that for some reason we need to prohibit everyone from using the messenger, while leaving work available through the browser.
Configure the policy:

Then we specify the security zone where the connection will be initiated from (at the same time, we will forbid everyone from any address to use this client).

We’ll indicate which zone traffic will go to (so as not to soar — we

’ll point to any zone): Now we need to ban this same messenger. We look for it in the signature database and set it:

The final rule is to block all traffic from the application:

Apply and save the configuration. We look at what we have: Actually, we succeeded in blocking the application. Now let's see if there is access to the site from a web browser: In principle, everything that was intended was implemented. Questions?


