Biometric signature on the document
In this post, we will talk about a method of authenticating a person by the dynamics of writing a handwritten password (signature). Recently, great interest has been shown in this area, and this is primarily due to the proliferation of mobile devices with touch screens. Agree, it would be great to receive a document by mail, open it, draw your signature with your finger and send it to the addressee. In this case, the document will have legal force. Abroad - this has long been a reality. In Russia, so far they trust a signed paper document or an electronic document with an officially registered digital signature.
A significant drawback of EDS is that it can be transferred to another person, i.e. unlike a traditional signature, it is alienated from its owner. At the same time, the legal significance of documents signed by EDS by an outsider will remain, which in some cases may be unacceptable. If you combine the digital signature and the biometric signature in electronic document management, you can solve the problem of inalienability of the legally significant digital signature from its owner!

Let us dwell on the technology itself ... To begin with, you should understand that from the point of view of the authentication method there is no difference what you will use as a password: a fixed handwritten word or signature. The main thing is that the spelling dynamics and geometry of your handwritten word remain more or less stable.
The author of this post as part of the team of the KASIB Scientific and Technical Center has been engaged in research and development of algorithms in this area for more than 10 years. 2 PhD theses defended (3rd in the near future), more than 5 R&D completed. 5-6 years ago, to implement the authentication method for the dynamics of writing a handwritten password (signature), it was necessary to purchase additional equipment - a graphic tablet (digitizer) with a light pen ( Wacom ). The evolution of mobile devices in recent years towards the use of touch input screens has made this technology as accessible as possible. At the end of 2012, our center created the cloud service SignToLoginthat implements user authentication by the dynamics of writing handwritten passwords as a service, and later the app of the same name appeared in the App Store. Further description of the technology will be accompanied by examples of this cloud platform.
The authentication procedure boils down to the fact that for each user, a handwritten password template must first be created. The process of creating a standard is reduced to the sequential input of 10 handwritten password implementations on the touch screen of a mobile tablet (possibly using a stylus), which can take an average of 3 minutes.

The user must write a handwritten word in his usual handwriting. After entering the required number of implementations, their statistical processing is performed to obtain the signs necessary in the future to authenticate the dynamic characteristics of writing the user's handwritten password. As a rule, these are only functions of the cursor speed in the plane of the touch screen. But if the user signs with a light pen that is sensitive to clicking on the plane of a graphics tablet (such as Wacom), then the pressure function will also be used. This will increase authentication reliability. SignToLogin
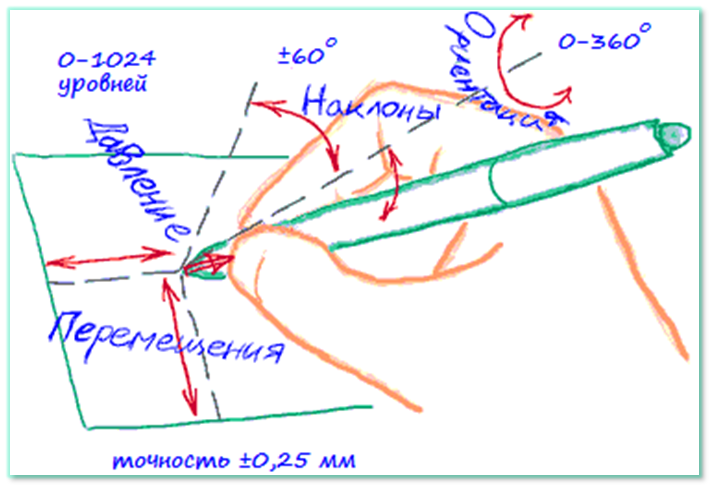
Cloud Serviceforms reference values of all necessary characteristics of the user and "remembers" them. During the authentication procedure, each entered handwritten password implementation will be processed in the same way as the implementations included in the standard. In authentication mode, the processed implementation is compared with reference values using special algorithms and methods that make the SignToLogin serviceas user-friendly as possible. The entered implementations of the handwritten word (signature) are automatically scaled and are not sensitive to rotations in the plane of the screen! In case of successful user authentication, the entered handwritten word implementation is added to the standard, displacing the latest implementation from it. Thus, the handwritten password pattern is always updated and becomes insensitive to changes in the user's handwriting.
So that all our scientific results do not “gather dust” on the shelves, we decided to create a useful toolkit in the form of APIs for developers of web and iOS applications, which will allow using this technology in real practice. Here you can find all the necessary documentation.
We also developed an iOS application.for signing PDF documents, which demonstrates the use of SignToLogin Mobile API. It is fundamentally different from the analogues on the market: SignNow , HelloSign , PDFpenPro , Signosign / 2 , QuickSign .

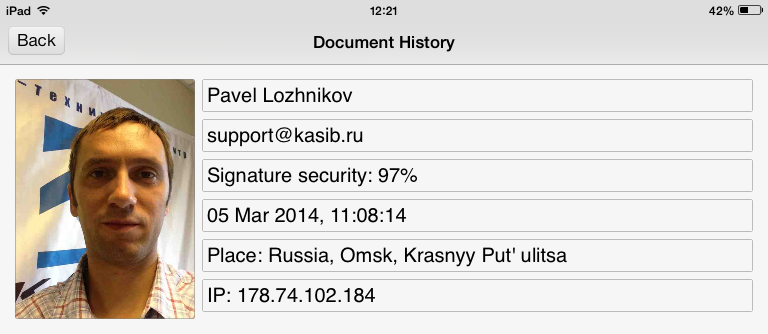
Using our application, you can recognize handwritten signatures on documents of your remote partners. Sign the document and the caption will contain a link to the Signtologin API website. By clicking it, you can find out:
Agree that there is more trust to a document with such an informative signature!
Application developers would like to give a number of recommendations on the practical and future use of our technology and API:
A significant drawback of EDS is that it can be transferred to another person, i.e. unlike a traditional signature, it is alienated from its owner. At the same time, the legal significance of documents signed by EDS by an outsider will remain, which in some cases may be unacceptable. If you combine the digital signature and the biometric signature in electronic document management, you can solve the problem of inalienability of the legally significant digital signature from its owner!

Let us dwell on the technology itself ... To begin with, you should understand that from the point of view of the authentication method there is no difference what you will use as a password: a fixed handwritten word or signature. The main thing is that the spelling dynamics and geometry of your handwritten word remain more or less stable.
The author of this post as part of the team of the KASIB Scientific and Technical Center has been engaged in research and development of algorithms in this area for more than 10 years. 2 PhD theses defended (3rd in the near future), more than 5 R&D completed. 5-6 years ago, to implement the authentication method for the dynamics of writing a handwritten password (signature), it was necessary to purchase additional equipment - a graphic tablet (digitizer) with a light pen ( Wacom ). The evolution of mobile devices in recent years towards the use of touch input screens has made this technology as accessible as possible. At the end of 2012, our center created the cloud service SignToLoginthat implements user authentication by the dynamics of writing handwritten passwords as a service, and later the app of the same name appeared in the App Store. Further description of the technology will be accompanied by examples of this cloud platform.
The authentication procedure boils down to the fact that for each user, a handwritten password template must first be created. The process of creating a standard is reduced to the sequential input of 10 handwritten password implementations on the touch screen of a mobile tablet (possibly using a stylus), which can take an average of 3 minutes.

The user must write a handwritten word in his usual handwriting. After entering the required number of implementations, their statistical processing is performed to obtain the signs necessary in the future to authenticate the dynamic characteristics of writing the user's handwritten password. As a rule, these are only functions of the cursor speed in the plane of the touch screen. But if the user signs with a light pen that is sensitive to clicking on the plane of a graphics tablet (such as Wacom), then the pressure function will also be used. This will increase authentication reliability. SignToLogin

Cloud Serviceforms reference values of all necessary characteristics of the user and "remembers" them. During the authentication procedure, each entered handwritten password implementation will be processed in the same way as the implementations included in the standard. In authentication mode, the processed implementation is compared with reference values using special algorithms and methods that make the SignToLogin serviceas user-friendly as possible. The entered implementations of the handwritten word (signature) are automatically scaled and are not sensitive to rotations in the plane of the screen! In case of successful user authentication, the entered handwritten word implementation is added to the standard, displacing the latest implementation from it. Thus, the handwritten password pattern is always updated and becomes insensitive to changes in the user's handwriting.
So that all our scientific results do not “gather dust” on the shelves, we decided to create a useful toolkit in the form of APIs for developers of web and iOS applications, which will allow using this technology in real practice. Here you can find all the necessary documentation.
We also developed an iOS application.for signing PDF documents, which demonstrates the use of SignToLogin Mobile API. It is fundamentally different from the analogues on the market: SignNow , HelloSign , PDFpenPro , Signosign / 2 , QuickSign .

Using our application, you can recognize handwritten signatures on documents of your remote partners. Sign the document and the caption will contain a link to the Signtologin API website. By clicking it, you can find out:
- who signed the document,
- the percentage of coincidence of the owner’s signature,
- when the document was signed
- in what place on the planet is the document signed (when the option is enabled),
- Signatory IP Address
- photo of the partner at the time of signing (if he so desires).

Agree that there is more trust to a document with such an informative signature!
Application developers would like to give a number of recommendations on the practical and future use of our technology and API:
- Do not use this method as the main authentication method, since the result depends on the psycho-emotional state of the person.
- For greater reliability of authentication, for example, of your remote employees, you can organize their registration in the presence of employees of the corresponding security service of your company.
- If possible, use a biometric signature paired with a legally significant digital signature. In the future, this will provide an opportunity to organize a full-fledged hybrid workflow.
