GitLab to NAS

If you have a working NAS with a docker , installing Gitlab does not present any particular difficulties.
This article is just a good example in the NAS series. And it shows how easy it is to manipulate services on an already finished platform, even if it was built independently, without a development team specially tailored by the OS and application stores.
Why gitlab?
There are several systems for managing Git repositories.
- Bitbucket — платная и закрытая система, хотя и популярная в корпоративном секторе. Предполагается интеграция с другими продуктами Atlassian, которые я не использую. Реализован на Java. Не особенно подходящее решение, особенно учитывая политику, что платить надо всё, даже за плагины (хотя есть и бесплатные).
- Gogs — система, похожая на Gitlab. Реализована на Go. Когда я последний раз смотрел на её возможности, там не было возможности ревью кода. Да и вообще отстаёт по функционалу от Gitlab, т.к. система намного более новая:
- Легковесен.
- По интерфейсу похож на Github.
- Управление пользователями.
- Баг-трэкер.
- Wiki.
- Нет ревью кода.
- Поддержка Git хуков.
- Доступ по HTTPS/SSH.
- Реализован на Go.
- Есть форк Gitea.
- Имеется LDAP плагин.
- Gitea — форк Gogs. Имеет то, чего не хватает в Gogs:
- Code review.
- Хранилище для больших файлов.
- Метки.
- Доработанный поиск.
- Прогресс задач с чекбоксами.
- LDAP тоже поддерживается.
- Kallithea — форк RhodeCode.
- Очень развитое управление пользователями и группами.
- Синхронизация с удалёнными репозиториями.
- Баг-трэкер.
- Wiki.
- Есть ревью кода.
- Поддержка Git хуков.
- Доступ по HTTPS/SSH.
- Реализован на Python.
- Интегрируется с LDAP.
- Есть образ Docker.
- Phacility — система от Facebook. Функционал широкий, есть не только ревью, но даже система управления задачами и проектами. Подробно я её не рассматривал.
- Gerrit — предназначен, в основном для обсуждения и ревью кода, с некоторым функционалом для управления репозиториями.
- Sr.ht — порекомендовали в комментариях. Судя по всему, функционал достаточно широкий. Но система пока в стадии активной разработки.
I worked with Gitlab before, and besides, it has built-in CI functionality, which will come in handy in the future. The system is mature, there is a lot of documentation for it, and over the years of development Gitlab has acquired many possibilities. Because I chose him.
General settings
I use the Gitlab image from sameersbn .
In docker-compose.yml(the file is also given at the end of the article) you need to change the following variables:
DB_PASS- password to the Gitlab database. Must match the password in the containerpostgresql.GITLAB_SECRETS_DB_KEY_BASE,GITLAB_SECRETS_SECRET_KEY_BASE,GITLAB_SECRETS_OTP_KEY_BASE- baseline values for key generation.GITLAB_ROOT_EMAIL- e-mail administrator.GITLAB_ROOT_PASSWORD- default administrator password, which can later be changed from the Web interface.GITLAB_EMAIL,GITLAB_EMAIL_REPLY_TO,GITLAB_INCOMING_EMAIL_ADDRESS- the address for mail notification.SMTP_HOST,SMTP_PORT,SMTP_USER,SMTP_PASS- the SMTP settings for e-mail alerts.IMAP_HOST,IMAP_PORT,IMAP_USER,IMAP_PASS- Gitlab can not just send e-mail, but also to take on IMAP. He can make inquiries by e-mail.
LDAP configuration
In order for NAS users to log in to Gitlab, it needs to provide an LDAP server as an authorization provider.
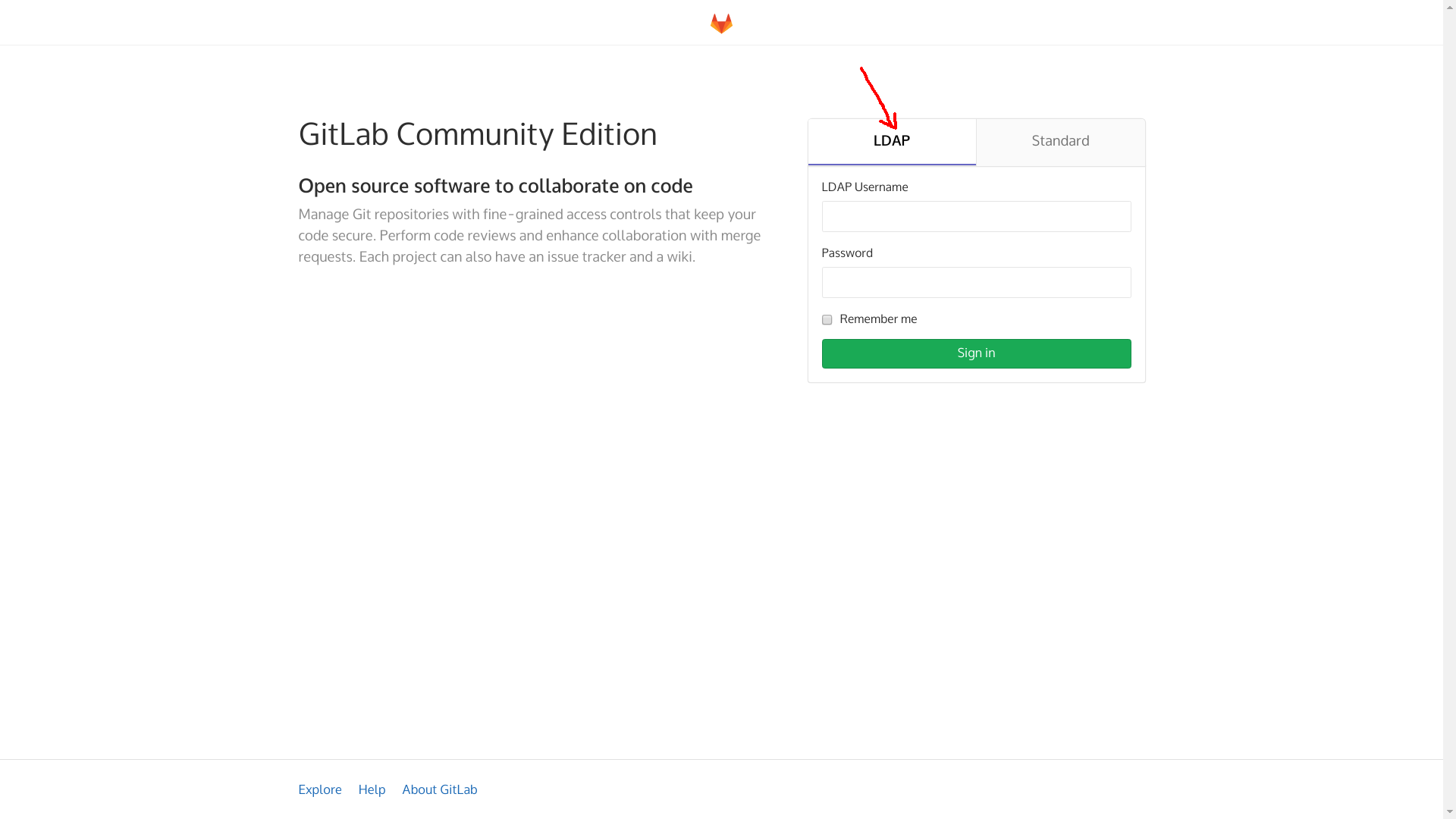
Note that when LDAP is configured, there will be two tabs on logging into Gitlab: LDAP and Standard.
The administrator will be able to log in only on the Standard tab, because he is registered locally, and users only on the LDAP tab.
Local administrator registration is useful in case the connection to the LDAP server is lost.
This is easily done by setting variables in the docker-compose configuration file:
LDAP_ENABLED=true- enable LDAP authorization.LDAP_HOST=172.21.0.1- LDAP server address.LDAP_PORT=389- port.LDAP_METHOD=plain- access method without encryption, because LDAP server within the host network. It is also possible to use StartTLS.LDAP_UID=uid- User UID field. In the case of OpenLDAP, in the configuration that was configured, this isuid.LDAP_BIND_DN=cn=admin,dc=nas,dc=nas- the user and domain under which Gitlab is authorized on the LDAP server.LDAP_PASS=<LDAP_PASSWORD>- the password for the LDAP user under which Gitlab is authorized on the LDAP server.LDAP_BLOCK_AUTO_CREATED_USERS=false- The LDAP user will appear in Gitlab after its first login. If it is installed heretrue, it will be blocked. The administrator can unblock it.LDAP_BASE=ou=users,dc=nas,dc=nas- This is the base address where user accounts are located.LDAP_USER_FILTER=memberOf=cn=users_code,ou=groups,dc=nas,dc=nas- filter. This indicates that I want to receive only members of the groupusers_code.LDAP_ALLOW_USERNAME_OR_EMAIL_LOGIN=true- allow the user to log in not only by UID, but also by e-mail.
Pay attention to the parameter LDAP_USER_FILTER. In a previous article , user groups in LDAP were entered, and this option only allows users in the group to access Gitlab users_code.
Gitlab ci
Configuring CI is described in detail in the Gitlab articles and documentation . It makes no sense to repeat.
In short, everything that needs to be done:
- Go to the build agents page: https://git.NAS.cloudns.cc/admin/runners and copy:
- Address ( https://git.NAS.cloudns.cc/ ).
- Token.
- Register an agent. He will ask for the address and token during the registration process.
Registration is done by the following command:
docker-compose exec gitlab-runner /entrypoint registerIt’s possible to read about the agents in Gitlab in the documentation .
I did not include the Docker Registry, because I do not need it. For what it is and why you need it, read on the Gitlab website .
Below is a spoiler configuration file for Gitlab, which is also available in the repository .
# https://github.com/sameersbn/docker-gitlab
version: '2'
networks:
gitlab:
docker0:
external:
name: docker0
services:
redis:
restart: always
image: sameersbn/redis:latest
command:
- --loglevel warning
networks:
- gitlab
volumes:
- /tank0/apps/gitlab/redis:/var/lib/redis:Z
postgresql:
restart: always
image: sameersbn/postgresql:9.6-2
volumes:
- /tank0/apps/gitlab/postgresql:/var/lib/postgresql:Z
networks:
- gitlab
environment:
- DB_USER=gitlab
- DB_PASS=<DB_PASSWORD>
- DB_NAME=gitlabhq_production
- DB_EXTENSION=pg_trgm
# plantuml:
# restart: always
# image: plantuml/plantuml-server
# image: plantuml/plantuml-server:jetty
# ports:
# - "127.0.0.1:9542:8080"
# ports:
# - "plantuml:8080:8080"
# expose:
# - 8080
# networks:
# - gitlab
gitlab:
restart: always
image: sameersbn/gitlab:10.6.3
depends_on:
- redis
- postgresql
ports:
- "11022:22"
expose:
- 443
- 80
- 22
volumes:
- /tank0/apps/repos:/home/git/data/repositories:Z
- /tank0/apps/repos/system/backup:/home/git/data/backups:Z
- /tank0/apps/repos/system/builds:/home/git/data/builds:Z
- /tank0/apps/repos/system/lfs-objects:/home/git/data/shared/lfs-objects:Z
- /tank0/apps/repos/system/public:/uploads/-/system:Z
- /tank0/apps/gitlab/logs:/var/log/gitlab
- /tank0/apps/gitlab/gitlab:/home/git/data:Z
networks:
- gitlab
- docker0
environment:
- "VIRTUAL_HOST=git.*,gitlab.*"
- VIRTUAL_PORT=443
- VIRTUAL_PROTO=https
- CERT_NAME=NAS.cloudns.cc
- DEBUG=false
# Default: 1
- NGINX_WORKERS=2
# Default: 3
- UNICORN_WORKERS=3
# Default: 25
- SIDEKIQ_CONCURRENCY=10
- DB_ADAPTER=postgresql
- DB_HOST=postgresql
- DB_PORT=5432
- DB_USER=gitlab
- DB_PASS=<DB_PASS>
- DB_NAME=gitlabhq_production
- REDIS_HOST=redis
- REDIS_PORT=6379
- TZ=Europe/Moscow
- GITLAB_TIMEZONE=Moscow
- GITLAB_HTTPS=true
- SSL_SELF_SIGNED=true
#- SSL_VERIFY_CLIENT=true
- NGINX_HSTS_MAXAGE=2592000
- GITLAB_HOST=git.NAS.cloudns.cc
#- GITLAB_PORT=11443
- GITLAB_SSH_PORT=11022
- GITLAB_RELATIVE_URL_ROOT=
- GITLAB_SECRETS_DB_KEY_BASE=<DB_KEY_BASE>
- GITLAB_SECRETS_SECRET_KEY_BASE=<SC_KEY_BASE>
- GITLAB_SECRETS_OTP_KEY_BASE=<OTP_KEY_BASE>
- GITLAB_SIGNUP_ENABLED=false
# Defaults to 5iveL!fe.
- GITLAB_ROOT_PASSWORD=
- GITLAB_ROOT_EMAIL=root@gmail.com
- GITLAB_NOTIFY_ON_BROKEN_BUILDS=true
- GITLAB_NOTIFY_PUSHER=false
- GITLAB_EMAIL=GITLAB@yandex.ru
- GITLAB_EMAIL_REPLY_TO=noreply@yandex.ru
- GITLAB_INCOMING_EMAIL_ADDRESS=GITLAB@yandex.ru
- GITLAB_BACKUP_SCHEDULE=daily
- GITLAB_BACKUP_TIME=01:00
- GITLAB_MATTERMOST_ENABLED=true
- GITLAB_MATTERMOST_URL=""
- SMTP_ENABLED=true
- SMTP_DOMAIN=www.example.com
- SMTP_HOST=smtp.yandex.ru
- SMTP_PORT=25
- SMTP_USER=GITLAB@yandex.ru
- SMTP_PASS=<SMTP_PASSWORD>
- SMTP_STARTTLS=true
- SMTP_AUTHENTICATION=login
- IMAP_ENABLED=true
- IMAP_HOST=imap.yandex.ru
- IMAP_PORT=993
- IMAP_USER=GITLAB@yandex.ru
- IMAP_PASS=<IMAP_PASSWORD>
- IMAP_SSL=true
- IMAP_STARTTLS=false
- OAUTH_ENABLED=false
- OAUTH_AUTO_SIGN_IN_WITH_PROVIDER=
- OAUTH_ALLOW_SSO=
- OAUTH_BLOCK_AUTO_CREATED_USERS=true
- OAUTH_AUTO_LINK_LDAP_USER=false
- OAUTH_AUTO_LINK_SAML_USER=false
- OAUTH_EXTERNAL_PROVIDERS=
- OAUTH_CAS3_LABEL=cas3
- OAUTH_CAS3_SERVER=
- OAUTH_CAS3_DISABLE_SSL_VERIFICATION=false
- OAUTH_CAS3_LOGIN_URL=/cas/login
- OAUTH_CAS3_VALIDATE_URL=/cas/p3/serviceValidate
- OAUTH_CAS3_LOGOUT_URL=/cas/logout
- OAUTH_GOOGLE_API_KEY=
- OAUTH_GOOGLE_APP_SECRET=
- OAUTH_GOOGLE_RESTRICT_DOMAIN=
- OAUTH_FACEBOOK_API_KEY=
- OAUTH_FACEBOOK_APP_SECRET=
- OAUTH_TWITTER_API_KEY=
- OAUTH_TWITTER_APP_SECRET=
- OAUTH_GITHUB_API_KEY=
- OAUTH_GITHUB_APP_SECRET=
- OAUTH_GITHUB_URL=
- OAUTH_GITHUB_VERIFY_SSL=
- OAUTH_GITLAB_API_KEY=
- OAUTH_GITLAB_APP_SECRET=
- OAUTH_BITBUCKET_API_KEY=
- OAUTH_BITBUCKET_APP_SECRET=
- OAUTH_SAML_ASSERTION_CONSUMER_SERVICE_URL=
- OAUTH_SAML_IDP_CERT_FINGERPRINT=
- OAUTH_SAML_IDP_SSO_TARGET_URL=
- OAUTH_SAML_ISSUER=
- OAUTH_SAML_LABEL="Our SAML Provider"
- OAUTH_SAML_NAME_IDENTIFIER_FORMAT=urn:oasis:names:tc:SAML:2.0:nameid-format:transient
- OAUTH_SAML_GROUPS_ATTRIBUTE=
- OAUTH_SAML_EXTERNAL_GROUPS=
- OAUTH_SAML_ATTRIBUTE_STATEMENTS_EMAIL=
- OAUTH_SAML_ATTRIBUTE_STATEMENTS_NAME=
- OAUTH_SAML_ATTRIBUTE_STATEMENTS_FIRST_NAME=
- OAUTH_SAML_ATTRIBUTE_STATEMENTS_LAST_NAME=
- OAUTH_CROWD_SERVER_URL=
- OAUTH_CROWD_APP_NAME=
- OAUTH_CROWD_APP_PASSWORD=
- OAUTH_AUTH0_CLIENT_ID=
- OAUTH_AUTH0_CLIENT_SECRET=
- OAUTH_AUTH0_DOMAIN=
- OAUTH_AZURE_API_KEY=
- OAUTH_AZURE_API_SECRET=
- OAUTH_AZURE_TENANT_ID=
- LDAP_ENABLED=true
#- LDAP_LABEL=nas
- LDAP_HOST=172.21.0.1
- LDAP_PORT=389
#- LDAP_METHOD=start_tls
- LDAP_METHOD=plain
- LDAP_UID=uid
- LDAP_BIND_DN=cn=admin,dc=nas,dc=nas
- LDAP_PASS=<LDAP_PASSWORD>
#- LDAP_CA_FILE=
# Default: false.
#- LDAP_BLOCK_AUTO_CREATED_USERS=true
- LDAP_BASE=ou=users,dc=nas,dc=nas
- LDAP_ACTIVE_DIRECTORY=false
#- LDAP_USER_FILTER=(givenName=)
- LDAP_USER_FILTER=memberOf=cn=users_code,ou=groups,dc=nas,dc=nas
- LDAP_ALLOW_USERNAME_OR_EMAIL_LOGIN=true
gitlab-runner:
container_name: gitlab-runner
image: gitlab/gitlab-runner:latest
networks:
- gitlab
volumes:
- /tank0/apps/gitlab/gitlab-runner/data:/home/gitlab_ci_multi_runner/data
- /tank0/apps/gitlab/gitlab-runner/config:/etc/gitlab-runner
environment:
- CI_SERVER_URL=https://gitlab.NAS.cloudns.cc
restart: always
# registry:
# container_name: docker-registry
# restart: always
# image: registry:2.4.1
# volumes:
# - /srv/gitlab/shared/registry:/registry
# - /srv/certs:/certs
# environment:
# - REGISTRY_LOG_LEVEL=info
# - REGISTRY_STORAGE_FILESYSTEM_ROOTDIRECTORY=/registry
# - REGISTRY_AUTH_TOKEN_REALM=http://git.labs.lc:10080/jwt/auth
# - REGISTRY_AUTH_TOKEN_SERVICE=container_registry
# - REGISTRY_AUTH_TOKEN_ISSUER=gitlab-issuer
# - REGISTRY_AUTH_TOKEN_ROOTCERTBUNDLE=/certs/registry-auth.crt
# - REGISTRY_STORAGE_DELETE_ENABLED=true
# - REGISTRY_HTTP_TLS_CERTIFICATE=/certs/registry.crt
# - REGISTRY_HTTP_TLS_KEY=/certs/registry.key
# ports:
# - "0.0.0.0:5000:5000"
# networks:
# mynet:
# aliases:
# - registry.git.labs.lc
#