AWS: IAM Roles for Servers
- Tutorial
Hello! 
I want to talk about the feature of IAM roles for servers in AWS. A role is a collection of access rights that can be applied to a server. We can consider using a specific example - to give the server access to S3, without clogging any keys manually.
Let's start with an example.
We go to the IAM console and create the S3 role there.
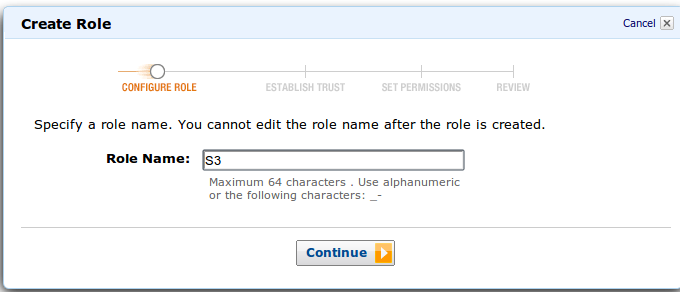
Next, select Amazon EC2

Next Amazon S3 Full Access

Next, Next, Next.
Let's start a regular server with Amazon Linux (all necessary tools are immediately installed on it). In Advanced Details, select the role that you just created:
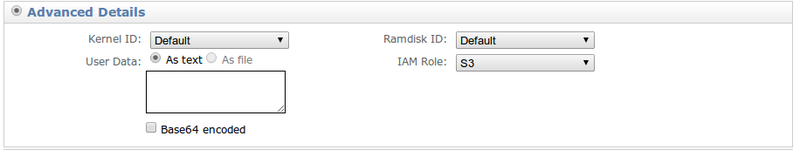
And start the server.
By logging in via ssh to the server we can get access keys by contacting at
http://169.254.169.254/latest/meta-data/iam/security-credentials/S3 You
can parse the JSON response and extract the necessary data from it:
Further, a matter of technology. We can carry out all operations with services to which we have access.

I want to talk about the feature of IAM roles for servers in AWS. A role is a collection of access rights that can be applied to a server. We can consider using a specific example - to give the server access to S3, without clogging any keys manually.
Let's start with an example.
1. Create a role with the necessary rights
We go to the IAM console and create the S3 role there.

Next, select Amazon EC2

Next Amazon S3 Full Access

Next, Next, Next.
Let's start the server.
Let's start a regular server with Amazon Linux (all necessary tools are immediately installed on it). In Advanced Details, select the role that you just created:

And start the server.
3. Testing.
By logging in via ssh to the server we can get access keys by contacting at
http://169.254.169.254/latest/meta-data/iam/security-credentials/S3 You
can parse the JSON response and extract the necessary data from it:
{
"Code" : "Success",
"LastUpdated" : "2012-11-29T16:23:50Z",
"Type" : "AWS-HMAC",
"AccessKeyId" : "ASIAI6G6HHSLUCRSUCQA",
"SecretAccessKey" : "15WdeWs2H182T+j3ZKkK+JBOssFqWdxdVpsHHgBm",
"Token" : "AQoDYXdzEDIagAL1yc69LLX+jH3tyDdf1rSk++Y1+4TrpYo4VUhHzcdFh3M9aWzUx1JCrWVoOr1Ghnkd3ALgUPBPtFrviuanVOSoXZBbuF0CKl3iVVLTJpEmOMStAAs0myrezYnUNVwIxIawSczxQkKIAuHDszV2mDFBBQ8RbKYu7wHAh+lQvUmfppyIcZ2kCHy/DtGuB9pYXxiNbTnFEN15LtOCojHdVicJSW4s5ynDd36GjsYYcAGmtDGNZXkUI/AS/ljgOtK1+7o9xN+M2RKJj7niL/iRv0LjWuTyTD9Z/D+p9k4KeLCiujKLTIt7g2VDiKqOg0r1OwI76Uh4q0MokEVH+PGuiccNILyY3oUF",
"Expiration" : "2012-11-29T22:38:49Z"
}
Further, a matter of technology. We can carry out all operations with services to which we have access.
