Checked electronic voting

In recent days there have been three posts on the hub of electronic voting:
FIDO / FTN distributed voting system
About electronic secret voting
Open electronic voting (evidence from the contrary) ,
but a complete solution providing secret electronic voting, the results of which could be checked by every voter, not found.
It seems to me that there is such a solution.
Task
Electronic voting must meet the following conditions:
- Anonymity - no one should be able to correlate a specific voice with a specific voter.
- Openness - voting results should be available to everyone.
- Verifiability - each voter should be able to test his vote. Any person should be able to calculate the final results and check for the absence of “stuffing”.
The key technology for solving this problem is blind signature - a way of signing the body of an encrypted message without decrypting it.
Voting procedure
- The voter generates a key pair and registers his public key with the CEC. According to the results of registration, a list of addresses of voters is uploaded to the public. Something like this:
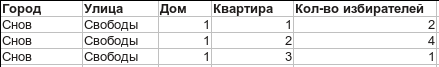
Already at this stage, everyone can verify that he is on the lists, another 146 people have not registered in his apartment, and a new neighborhood has not grown in the neighborhood overnight. - The voter generates his ballot of the form:
Next, he encrypts the ballot (the key can be any), signs it with his private key and sends it to the CEC - The CEC verifies the signature. After making sure that this signature is on the voters list, he signs the ballot with a blind signature and sends it to the voter. After that, the CEC in the public voter list increments the voter counter:
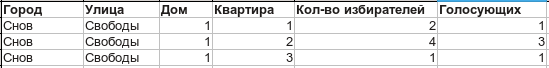
Here, the voter can make sure that he is counted. - The voter decrypts the ballot, verifies the signature of the CEC and sends the decrypted, signed by the CEC ballot back to the CEC.
- The CEC receives the ballot, verifies the validity of its signature, encrypts it and immediately puts it in the public domain a couple [random number of the ballot (from point 2), encrypted ballot]. The ballot is encrypted by the CEC, the encryption key is kept secret until the end of the vote.
- After voting ends, the key to the cipher of ballots is published.
What do we have as a result?
In general access there is:
- The list of voters addresses from point 3. Everyone can check the number of voters, make sure that there are no “stuffing”.
- The list of ballots from paragraph 5. Each voter can find his vote by the random number that he generated at the stage of creating the ballot. Anyone can calculate the voting results and compare the number of ballots with the number of voters who voted.
None of the stages of the CEC or anyone else can match the voter and his vote. During the voting process, you can track changes in public lists, identifying the suspicious dynamics of changes. Each voter can check if his vote is correctly counted. Anyone can independently calculate the voting results. Home registrations can be identified.
What do you think will work?
Upd:
Thank you all for your feedback!
mihaild painted the points more clearly:
1. The voter sends the IzbPub1 key and his address to the CEC.
2. The voter makes the ballot (random number + vote), encrypts it with the key Izb2, signs with the key IzbPriv1, sends it to the CEC.
3. The CEC verifies the signature with the key IzubPub1, blindly signs the encrypted ballot with the key CycPriv1, sends the result back to the voter.
4. The CEC notes that it received a vote from the corresponding address.
5. The voter, using the encrypted signed ballot and the Izb2 key, receives an unencrypted ballot signed by the Cypriv1 key.
6. The voter sends the signed unencrypted ballot back to the CEC.
7. The CEC verifies the signature using the CycPub1 key.
8. The CEC publishes a pair (number, ballot, encrypted Cube Pub2) and takes into account the vote of the voter.
9. At the end of the election, the CEC publishes the CivPriv2.
vics001drew attention to the fact that the commutability of signature operations and the masking factor can lead to the creation of several fake ballots.
Exit - at the second stage, the hash of the previous part is added to the bulletin, which will make the selection of the masking factor unrealistic.
edhell correctly noted - in the first paragraph I did not indicate that registration is offline with the presentation of a passport. This is a one-time procedure that allows you to vote in the future, and may well be combined with a passport and a change of residence permit.
