Information Security? No have not heard
A friend of mine asked me about digital hygiene today. I will try to briefly outline the principles by following which you will increase your security level in the network.
In this article, I tried to go from very trivial advice to quite difficult to implement. Everyone must decide for themselves what level of security is acceptable to him personally. Everything is exactly the same as with safes: there is a safe for one hundred dollars, there is a safe for one hundred thousand dollars. It is foolish to keep millions of dollars in the first, and a handful of little things in the second.
If you have important information, and you are afraid of losing it, and the mere thought that this information may reach your enemies scares you, then you should think about information security.

Well, taking data protection seriously when data is worth nothing is just a waste of time.
If you want to protect your information, the first thing you need to do is to understand the basic principles.
If you have experience in information security, then feel free to scroll to the next chapter.
To the fullest extent, you can read about this in the book by Kevin Mitnick, which is called The Art of Deception. There are a lot of stories about what problems companies got into because they did not train their employees in the basic principles of protecting their information.
But if you still give a couple of universal tips, they will be:
You will learn more from the book. Many interesting stories are described there, and although some of them are already out of date due to progress, the essence itself will hardly ever cease to be relevant.
People often ask this question when it comes to data protection. Something like: “Why does the company need my data?” Or “Why does a hacker hack me?” I don’t understand that they can’t be hacked. The service itself can be hacked, and all users registered in the system will suffer. That is, it is important not only to comply with the rules of information security, but also to choose the right tools that you use. In order to make it clearer, I will give a few examples:
When a little sharpened
Just a couple of days ago, we all learned that the Burger King app, which is in Google Play and the Apple Store, records everything that a user does. And there is not impersonal data at all, as representatives of Burger King tell us. Everything is recorded literally: how the user enters his first name, last name, address, and even credit card details. Video is always recorded.
Do you think that this is the only app that captures everything you do in it?
AppSee
I work for a software company. And we had a couple of cases.
In February 2016, a client came to us with a mobile application and asked to add some functionality there.
We looked at the code and saw that the analytics thing was being used, called AppSee. They asked the customer for access to it, and he replied that he himself did not know where it came from, and that there was no access to it. We talked with support for a long time and spent a lot of time trying to regain access. And they saw that the previous developer set up AppSee to record video from some screens. And some screens were those where the user entered credit card or paper data.
Encrypt passwords The
second case was when a customer came to us with a fairly large project, which was about two million registered users. We started work, the customer gave us access to the code and database. And in the database all user passwords are unencrypted.
I think you understand what the consequences would be if the base fell into the wrong hands.
Are you sure that all the services you use are very sensitive to security, do not merge your data, and will never use your data against you? I'm not sure.
And the worst thing is: what if services for storing passwords, such as 1password, LastPass cannot safely store your passwords? What if they flow away? Personally, I am even afraid to think about it.
How do I see the way out? In my opinion, this is Open Source.
Using the Open Source application you get one big plus and one big minus. Minus - in the absence of support, all the risks - only for you. The advantage is that there is no other link that stores your data: you exclude the possibility that this link will lose, sell or compromise your data. Of course, Open Source by itself is not a panacea, and does not guarantee that a developer will not put anything bad in the code. Trust is only those projects in which a large community.
Then I will talk about what I personally use.
Not by chance in the first place. After all, this is the most important part in your safety. Everything is stored here. And, having lost access to the password manager, you can get a huge pile of problems.
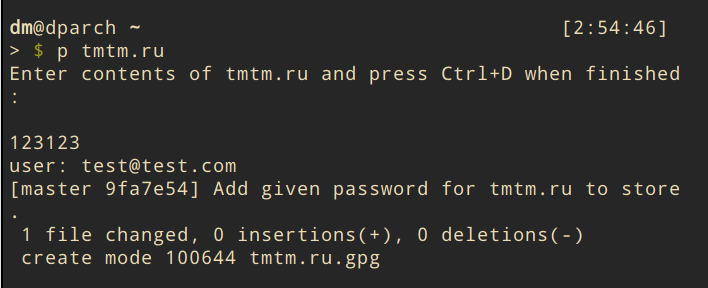
As I said earlier, I have no idea what will happen if all my passwords are leaked. Therefore, I use the pass. This is a terminal program in which you can store your passwords in encrypted form.
It is for all operating systems. There are applications for iOS and Android. And there are also plugins for Chrome and Firefox.
The program is completely open and free, uses the free GPG library. It encrypts each entry with your GPG key. In my opinion, this is the safest option.



In my opinion, the most secure are open source open source operating systems. There are a lot of them. You can start with the easiest to install and use - Ubuntu. But personally, I don’t like it very much because there are various services in it, like the popularity-contest, which send some data to the developers.
In addition, Ubunt has already undermined its reputation a bit, using the so-called “spying search” to version 16.04.
Personally, I made my choice in favor of arch linux, although it is more difficult to install. Although there are quite a few analogues, I can’t say that they are worse.
In my opinion a great open source OS - LineageOS. It is very stable and is updated quite often. Now it is very fresh Android 8.1.0, which works fine. Do not forget to install the bootloader after installation.
Together with the free OS, I recommend using a free software store called F-Droid.
Think about how you unlock your smartphone.
In my opinion, unlocking in the face is not a very reliable method, there are a huge number of problems.
Fingerprint is also a rather controversial method. In fact, if you do not trust Google or Apple and do not use their operating systems, but at the same time unlocked the phones with your fingerprint, you can assume that your fingerprint is already compromised. And you can no longer use a fingerprint to protect something important.
Instead of Google Drive or Dropbox, I use NextCloud on my server. There are several advantages.
Probably the same as with the previous points. It is best to use open source browsers: Firefox, Chromium, Brave, Icecat. For ease of use and other characteristics, they are not inferior to the same chrome.
I do not really like the fact that the search engine knows about me too much. Here are examples of what Google knows about you.
myactivity.google.com/myactivity
maps.google.com/locationhistory
adssettings.google.com/authenticated?hl=en I
must say that Google is really good at looking. Free analogs that respect your privacy are quite small. In fact, there is only DuckDuckGo, which is not perfect looking.
There are programs such as TrueCrypt that allow you to encrypt your information on the fly.
The TrueCrypt program itself was considered the most reliable for full disk encryption or the creation of containers. But only the developers published a message in which they advised all users to switch to Bitlocker. In this message, the community saw the so-called “testimony of the canary,” that is, an attempt to say something without saying anything and giving a hint of insincerity. Since the developers have always ridiculed Bitlocker.
In addition, some users wanted to fork the project. But the author of TrueCrypt answered briefly and succinctly: “It’s a pity, but I think that you are asking for the impossible. I don’t think TrueCrypt fork is a good idea. ”
Based on this, I believe that TrueCrypt, and all its analogs like VeraCrypt, are not secure.
I do not know other analogues. Although I heard about Tomb, I always wanted to try it, but I could not reach it. If you can advise something, write in the comments.
Encrypt the entire disk
Do you know what will happen if you lose your laptop and a bad person finds it? It will turn it on with any bootable USB flash drive and calmly get access to all your data.
Therefore, it is very important to encrypt the entire disk. That at loss of your device the person could not get access to it.
Make backups (and encrypt them)
In the same way, it’s important not to lose all your data yourself. For this, make backups. And be sure to encrypt them. Well, by itself, do not store backups on the same media.
Keep track of access
When you sell your devices, then do not forget to remove them from your accounts. It is very important.
myaccount.google.com/device-activity
www.dropbox.com/account/security
www.icloud.com/#settings
Keep track of what level of access applications and plugins require from you.
There are situations when you put any application, but it requires full access to the Dropbox folder. Although it would seem, this application absolutely does not need such access. Well, in an extreme case, the Access type: “App folder” would be enough for him. Such things for Dropbox can be checked here:
www.dropbox.com/account/connected_apps
And some applications require access to Google Drive. I do not really understand why they have access to my documents. You can check this link:
myaccount.google.com/permissions
Two-factor authentication
Use two-factor authentication wherever possible. This very effective additional level of security. There are several types of them.
In this article, I tried to go from very trivial advice to quite difficult to implement. Everyone must decide for themselves what level of security is acceptable to him personally. Everything is exactly the same as with safes: there is a safe for one hundred dollars, there is a safe for one hundred thousand dollars. It is foolish to keep millions of dollars in the first, and a handful of little things in the second.
If you have important information, and you are afraid of losing it, and the mere thought that this information may reach your enemies scares you, then you should think about information security.

Well, taking data protection seriously when data is worth nothing is just a waste of time.
Safety principles
If you want to protect your information, the first thing you need to do is to understand the basic principles.
If you have experience in information security, then feel free to scroll to the next chapter.
To the fullest extent, you can read about this in the book by Kevin Mitnick, which is called The Art of Deception. There are a lot of stories about what problems companies got into because they did not train their employees in the basic principles of protecting their information.
But if you still give a couple of universal tips, they will be:
- Do not use light passwords: passwords that may be associated with you or found in the dictionary.
- Do not use the same passwords for different services.
- Do not store passwords in clear form (recent history with google-documents that were indexed by Yandex, it showed).
- Do not tell anyone the password. Even support staff.
- Do not use free Wi-Fi networks. And if you use, be careful and try not to work on sites without https-connection.
You will learn more from the book. Many interesting stories are described there, and although some of them are already out of date due to progress, the essence itself will hardly ever cease to be relevant.
"Yes, who needs me?"
People often ask this question when it comes to data protection. Something like: “Why does the company need my data?” Or “Why does a hacker hack me?” I don’t understand that they can’t be hacked. The service itself can be hacked, and all users registered in the system will suffer. That is, it is important not only to comply with the rules of information security, but also to choose the right tools that you use. In order to make it clearer, I will give a few examples:
When a little sharpened
Just a couple of days ago, we all learned that the Burger King app, which is in Google Play and the Apple Store, records everything that a user does. And there is not impersonal data at all, as representatives of Burger King tell us. Everything is recorded literally: how the user enters his first name, last name, address, and even credit card details. Video is always recorded.
Do you think that this is the only app that captures everything you do in it?
AppSee
I work for a software company. And we had a couple of cases.
In February 2016, a client came to us with a mobile application and asked to add some functionality there.
We looked at the code and saw that the analytics thing was being used, called AppSee. They asked the customer for access to it, and he replied that he himself did not know where it came from, and that there was no access to it. We talked with support for a long time and spent a lot of time trying to regain access. And they saw that the previous developer set up AppSee to record video from some screens. And some screens were those where the user entered credit card or paper data.
Encrypt passwords The
second case was when a customer came to us with a fairly large project, which was about two million registered users. We started work, the customer gave us access to the code and database. And in the database all user passwords are unencrypted.
I think you understand what the consequences would be if the base fell into the wrong hands.
Are you sure that all the services you use are very sensitive to security, do not merge your data, and will never use your data against you? I'm not sure.
And the worst thing is: what if services for storing passwords, such as 1password, LastPass cannot safely store your passwords? What if they flow away? Personally, I am even afraid to think about it.
Possible Solution
How do I see the way out? In my opinion, this is Open Source.
Using the Open Source application you get one big plus and one big minus. Minus - in the absence of support, all the risks - only for you. The advantage is that there is no other link that stores your data: you exclude the possibility that this link will lose, sell or compromise your data. Of course, Open Source by itself is not a panacea, and does not guarantee that a developer will not put anything bad in the code. Trust is only those projects in which a large community.
Then I will talk about what I personally use.
I know that any topic in which talk about what is better is beginning: mac or win, win or linux, rolls down into a futile argument. Please do not do this.
The operating system is just a tool. And professionals are unlikely to argue about whether they should use a screwdriver or a hammer. For each case, they will find the most appropriate tool. Let us treat operating systems and other software in the same way.
Password Manager
Not by chance in the first place. After all, this is the most important part in your safety. Everything is stored here. And, having lost access to the password manager, you can get a huge pile of problems.
As I said earlier, I have no idea what will happen if all my passwords are leaked. Therefore, I use the pass. This is a terminal program in which you can store your passwords in encrypted form.
It is for all operating systems. There are applications for iOS and Android. And there are also plugins for Chrome and Firefox.
The program is completely open and free, uses the free GPG library. It encrypts each entry with your GPG key. In my opinion, this is the safest option.




operating system
In my opinion, the most secure are open source open source operating systems. There are a lot of them. You can start with the easiest to install and use - Ubuntu. But personally, I don’t like it very much because there are various services in it, like the popularity-contest, which send some data to the developers.
In addition, Ubunt has already undermined its reputation a bit, using the so-called “spying search” to version 16.04.
Personally, I made my choice in favor of arch linux, although it is more difficult to install. Although there are quite a few analogues, I can’t say that they are worse.
Smartphone
In my opinion a great open source OS - LineageOS. It is very stable and is updated quite often. Now it is very fresh Android 8.1.0, which works fine. Do not forget to install the bootloader after installation.
Together with the free OS, I recommend using a free software store called F-Droid.
Think about how you unlock your smartphone.
In my opinion, unlocking in the face is not a very reliable method, there are a huge number of problems.
Fingerprint is also a rather controversial method. In fact, if you do not trust Google or Apple and do not use their operating systems, but at the same time unlocked the phones with your fingerprint, you can assume that your fingerprint is already compromised. And you can no longer use a fingerprint to protect something important.

File storage
Instead of Google Drive or Dropbox, I use NextCloud on my server. There are several advantages.
- Security. I am sure that no one else has access to my data. And even if it appears, all data on NextCloud is encrypted. Like Dropbox, it has clients for all operating systems, including mobile ones.
- Flexibility. I can use the amount of storage I need. I can easily make both 100GB and 20TB.
- Plugins NextCloud offers quite handy add-ons. Such as notes, calendar, task manager. And all this is synchronized and also works on the smartphone.
Browser
Probably the same as with the previous points. It is best to use open source browsers: Firefox, Chromium, Brave, Icecat. For ease of use and other characteristics, they are not inferior to the same chrome.
Search engine
I do not really like the fact that the search engine knows about me too much. Here are examples of what Google knows about you.
myactivity.google.com/myactivity
maps.google.com/locationhistory
adssettings.google.com/authenticated?hl=en I
must say that Google is really good at looking. Free analogs that respect your privacy are quite small. In fact, there is only DuckDuckGo, which is not perfect looking.
Encryption on the fly
There are programs such as TrueCrypt that allow you to encrypt your information on the fly.
The TrueCrypt program itself was considered the most reliable for full disk encryption or the creation of containers. But only the developers published a message in which they advised all users to switch to Bitlocker. In this message, the community saw the so-called “testimony of the canary,” that is, an attempt to say something without saying anything and giving a hint of insincerity. Since the developers have always ridiculed Bitlocker.
In addition, some users wanted to fork the project. But the author of TrueCrypt answered briefly and succinctly: “It’s a pity, but I think that you are asking for the impossible. I don’t think TrueCrypt fork is a good idea. ”
Based on this, I believe that TrueCrypt, and all its analogs like VeraCrypt, are not secure.
I do not know other analogues. Although I heard about Tomb, I always wanted to try it, but I could not reach it. If you can advise something, write in the comments.
Important additions
Encrypt the entire disk
Do you know what will happen if you lose your laptop and a bad person finds it? It will turn it on with any bootable USB flash drive and calmly get access to all your data.
Therefore, it is very important to encrypt the entire disk. That at loss of your device the person could not get access to it.
Make backups (and encrypt them)
In the same way, it’s important not to lose all your data yourself. For this, make backups. And be sure to encrypt them. Well, by itself, do not store backups on the same media.
Keep track of access
When you sell your devices, then do not forget to remove them from your accounts. It is very important.
myaccount.google.com/device-activity
www.dropbox.com/account/security
www.icloud.com/#settings
Keep track of what level of access applications and plugins require from you.
There are situations when you put any application, but it requires full access to the Dropbox folder. Although it would seem, this application absolutely does not need such access. Well, in an extreme case, the Access type: “App folder” would be enough for him. Such things for Dropbox can be checked here:
www.dropbox.com/account/connected_apps
And some applications require access to Google Drive. I do not really understand why they have access to my documents. You can check this link:
myaccount.google.com/permissions
Two-factor authentication
Use two-factor authentication wherever possible. This very effective additional level of security. There are several types of them.
- Time synchronized passwords. In my opinion, one of the most common, secure and most successful two-factor authentication options. You will be shown a QR code that you need to take a photo of the application, and you will have a line with your one-time password that changes every 30 seconds. I recommend that you somehow store pictures of these QR codes or use applications that can export the base with your records.
- Hardware key FIDO U2F. In my opinion, this is also a pretty good option, but some moments confuse me. For example, it is not clear what to do if this key breaks and simply stops working. Still, this is a technique, and any technique someday, yes it breaks. I also don’t understand what to do if I just lose it.
- A one-time passwords list is a decent option if nothing else. The problem with this option is that the user will most often store the password and the list of one-time passwords in one place.
- SMS authentication. I absolutely do not like this method, and I try not to use it, although sometimes it does not work, as some services offer it only. The problem is that there are so many ways to get hold of your phone number.
