Burger King and the secret recording of the screen of your phone
UPD2:
UPD:
Hi, Habr! I am 18 andI bearded in my spare time I pick different applications. Today, my hands have reached the popular and popular Burger King app (the one where “burger is free”, “nut” and promotional codes for friends).
I launch their application, I watch the traffic. And here I find it:
What it is? If there are no ideas, look under the cut.
UPD:
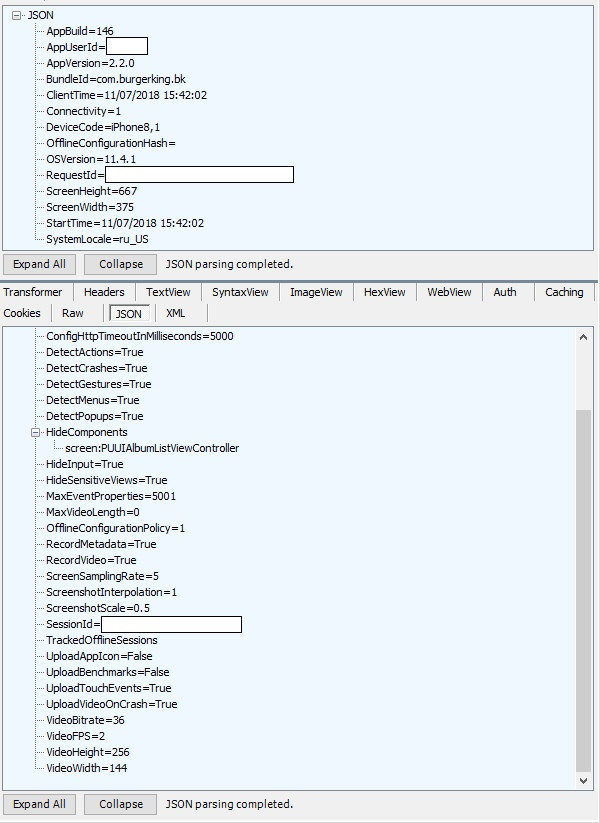
And this is a request from the application to the server (above) with information like its version, phone model, launch time, display resolution. It seems to be all right, but ...
In response, the phone receives information (from below) on how to record video from the screen.
Moreover, the MaxVideoLength parameter (maximum video length) is specified as “0”, which means infinite recording (while the application is running).
That is, the application does not just write the screen, but does it continuously, and in exactly the same way continuously sends the recording to the server. Users of the mobile Internet (that is, almost all) appreciated this “feature”, I think.
Screen recording is transmitted as a regular * .mp4 stream:
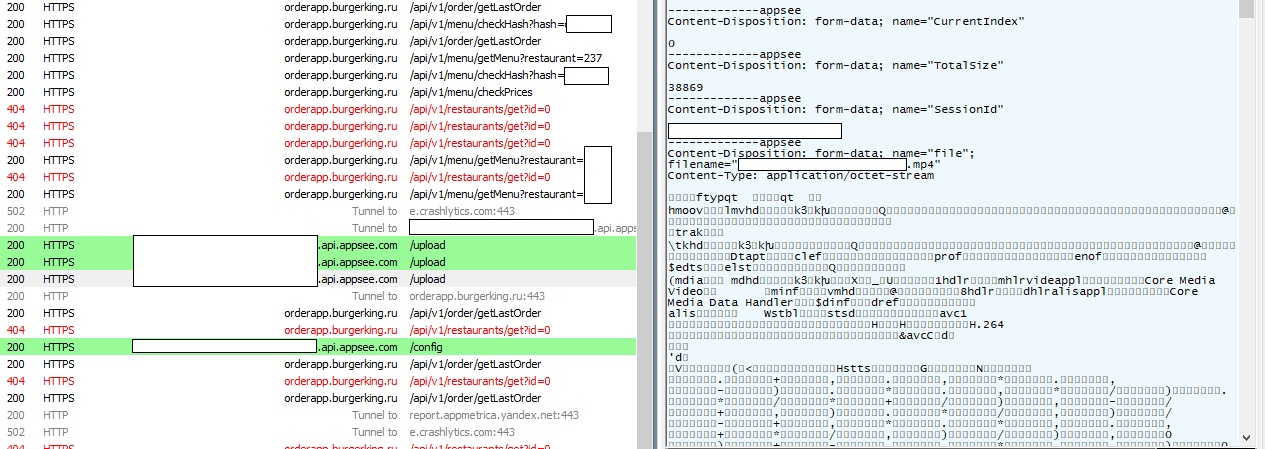
Pay attention to the address * .appsee.com / upload (AppSee is a video metric for applications) on the left and the * .mp4 file itself on the right (in the header is encoding information, just below it is * .mp4 itself).
Well, the cherry on the cake: the screen is recorded even when you enter your bank card data in the application (and this is necessary for the implementation of the order). Notice all the data.
And the final cherry: not only is the screen recording a very dubious task, not only the developers of the Burger King application have access to recorded videos, but also various AppSee partners (that is, completely left-handed people with unknown intentions), and AppSee itself also.
Let me remind you - the video is recorded even when you specify the data of your bank card. And it has access to just anyone.
This is what the video itself looks like:
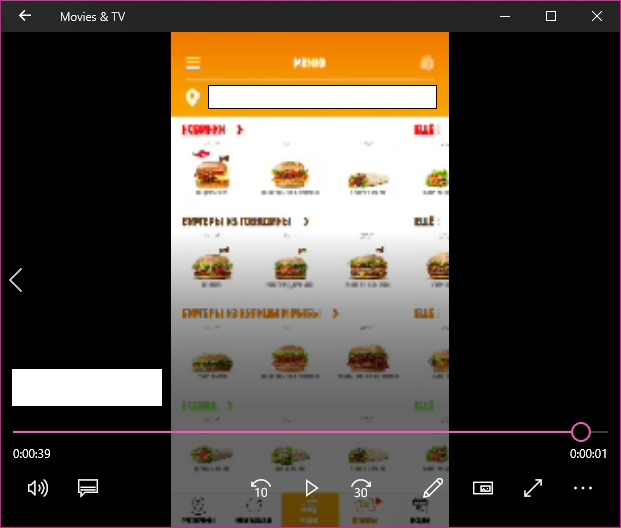
PS: yes, you could read this post in a similar way on another site, but such a burger fire is clearly a place on Habré. I hope for understanding of all and UFO.
Made a second post with evidence and a refutation of the statements of Burger King. Read here .
UPD:
fennikami
I provided video evidence that the data entry fields (including bank cards) are not hidden + the video is sent every time you start (which you can verify by monitoring the application traffic).
Thus, I have a refutation of the official answer of Burger King that “personal information is hidden” and that sample is allegedly used by 10% of users.
It is worth noting that none of the official Burger King videos (where they allegedly demonstrate the concealment of personal data) does not show the bank card binding menu.
In this video it is shown.
I also want to note that after the publication of the original investigation, hacker attacks started on my blog (brutfors admin panel, search for exploits, DDoS attempt).
I am preparing a second post on this topic.
Stay tuned, more info in my blog .
Hi, Habr! I am 18 and
I launch their application, I watch the traffic. And here I find it:

What it is? If there are no ideas, look under the cut.
UPD:
3amynoKUPD moderator Habr:
I would say they walk on awesome thin ice. I see tachi - transitions between fields, but I did not find any tapes on the keyboard in their data. yadi.sk/d/tjxg2OJ83Z6YB8 I went back to the form, entered 123456 in the card number ... What I see is the opening of the card form "BurgerKing.PYCardInput", "s": 132000 where s is time, then I watched all TouchEvents tacos from this time and marked them on the screen. Actions values confused, there is “h”: 216 that there is a keyboard height and there are some events with “i” in succession 1, 2, 4. I think this is the choice of the date of the card when you select it in the drum.
We contacted the participants of the story and received comments - follow them in our article .
And this is a request from the application to the server (above) with information like its version, phone model, launch time, display resolution. It seems to be all right, but ...
In response, the phone receives information (from below) on how to record video from the screen.
Moreover, the MaxVideoLength parameter (maximum video length) is specified as “0”, which means infinite recording (while the application is running).
That is, the application does not just write the screen, but does it continuously, and in exactly the same way continuously sends the recording to the server. Users of the mobile Internet (that is, almost all) appreciated this “feature”, I think.
Screen recording is transmitted as a regular * .mp4 stream:

Pay attention to the address * .appsee.com / upload (AppSee is a video metric for applications) on the left and the * .mp4 file itself on the right (in the header is encoding information, just below it is * .mp4 itself).
Well, the cherry on the cake: the screen is recorded even when you enter your bank card data in the application (and this is necessary for the implementation of the order). Notice all the data.
And the final cherry: not only is the screen recording a very dubious task, not only the developers of the Burger King application have access to recorded videos, but also various AppSee partners (that is, completely left-handed people with unknown intentions), and AppSee itself also.
Let me remind you - the video is recorded even when you specify the data of your bank card. And it has access to just anyone.
This is what the video itself looks like:

PS: yes, you could read this post in a similar way on another site, but such a burger fire is clearly a place on Habré. I hope for understanding of all and UFO.
