Authorizing proxy for Windows (+ Opera's normal operation with NTLM as a bonus)
The following features of my life path inspired me to write this topic:
Having scattered my things around the new workplace and having the computer at my disposal, I immediately started littering it with the usual set of software, which, of course, included Opera.
Not having time to rejoice at the new and powerful computer that the boss gave me, I found that Opera forces me to enter the proxy login / password for each of the open tabs ...
At first it surprised me, but when I noticed that it wasrespected and warmly by everyone Internet Explorer’s favorite, officially supported by our IT department, doesn’t suffer from such a disaster.
Uncle Google told me a lot of interesting and new things for me then on this subject ... and about how long ago Opera users have been complaining about it, and how to fix it simply by installing some kind of "fox" :)
In addition, I realized that there is NTLM authentication, and that Opera is not particularly friendly with it.
Newly made colleagues joyfully advised me not to show off and throw out my "not very popular browser."
BUT. This state of affairs did not suit me, and the desire to change the browser familiar to me somehow did not arise. Therefore, I decided to try to find a solution to this annoying problem (naturally, in my free time).
Most of the recommendations came down to the fact that it is necessary to pull the box EnableNTLM in Opera (opera: config -> Network -> EnableNTLM).
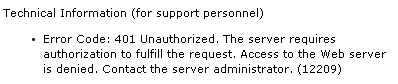
Unfortunately, in my case, the option did not bring me the desired unity with the browser:
We could not find anything more efficient, so I had to try a more cardinal solution - my own proxy, which will be authorized on the corporate proxy.
Then I found only NTLMAPS .
For some time I used this proxy - in general, it performs its function, but there were some unpleasant moments:
Everyone has probably guessed that there is still a worthy and more convenient NTLMAPS replacement, which I want to talk about. And her name is CNTLM .
It is this proxy that I have been using at work for the past few years (colleagues working under Linux also opted for CNTLM). A lot of time has passed since then ... At first it turned out that we were using squid, ISA and something else ... Then a secret transparent proxy appeared without authorization at all. But I still use CNTLM.
So, for starters, I will give the advantages of CNTLM compared to NTLMAPS:
How can this solution be useful:
This is just a list of the applications that came to my mind. I am sure that many will be able to come up with something else.
Under Windows, we are offered an installer that will do everything well: create a service and unzip files to the right place.
Nevertheless, you still have to work with your hands.
Since CNTLM uses Cygwin, which by default pours events into the eventlog, we have a frantic amount of garbage in the Application log (Event for each HTTP request is Event ID 0 Source Cygwin):
The description for Event ID 0 from source Cygwin cannot be found. Either the component that raises this event is not installed on your local computer or the installation is corrupted. You can install or repair the component on the local computer.
If the event originated on another computer, the display information had to be saved with the event.
The following information was included with the event:
127.0.0.1 GET s.w3bsit3-dns.com/forum/style_emoticons/default/thank_you.gif You
can live with this, of course, but finding something really useful in the log is quite difficult.
If someone prompts an elegant solution - I will be grateful.
The only thing that has occurred to me so far is to remove all syslog () calls in the source.
Fig. 1. Check the execution time of the request with wget. Please note that the time of the 1st and subsequent request when using NTLMAPS is almost the same (~ 2 sec). In the case of CNTLM - the first request is 5 times faster, the next one - already 15 times - there is connection caching.
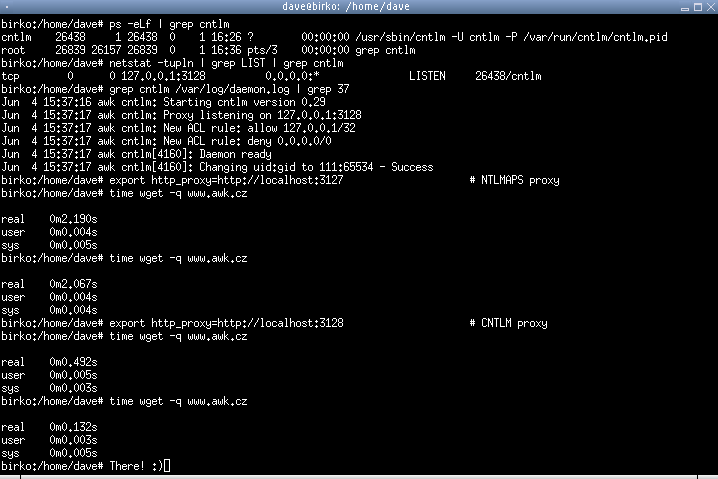
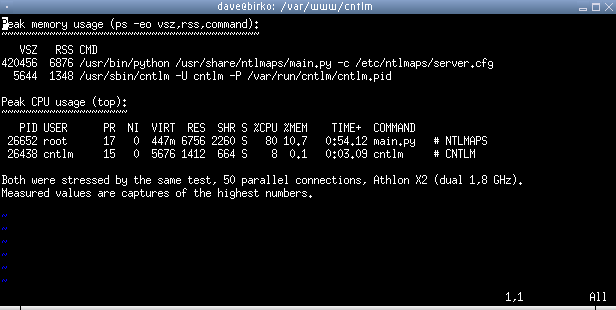
Fig. 2. We look at CPU and RAM consumption with 50 parallel connections.
- A couple of years ago I got a job in a fairly large company, where I met proxies in general and proxies with authorization in particular and found out about Opera jambs in such an environment
- Admins force us to change the password in the domain \ proxy often enough
- There was no similar article on Habré :) - I hope that this info will be useful to someone
Background
Having scattered my things around the new workplace and having the computer at my disposal, I immediately started littering it with the usual set of software, which, of course, included Opera.
Not having time to rejoice at the new and powerful computer that the boss gave me, I found that Opera forces me to enter the proxy login / password for each of the open tabs ...
At first it surprised me, but when I noticed that it was
Uncle Google told me a lot of interesting and new things for me then on this subject ... and about how long ago Opera users have been complaining about it, and how to fix it simply by installing some kind of "fox" :)
In addition, I realized that there is NTLM authentication, and that Opera is not particularly friendly with it.
Newly made colleagues joyfully advised me not to show off and throw out my "not very popular browser."
BUT. This state of affairs did not suit me, and the desire to change the browser familiar to me somehow did not arise. Therefore, I decided to try to find a solution to this annoying problem (naturally, in my free time).
Search for a solution
Most of the recommendations came down to the fact that it is necessary to pull the box EnableNTLM in Opera (opera: config -> Network -> EnableNTLM).
Unfortunately, in my case, the option did not bring me the desired unity with the browser:
- EnableNTLM = 1 -> we get one password request for each tab
- EnableNTLM = 0 -> only one request, but all internal resources that require domain authorization fall off:

We could not find anything more efficient, so I had to try a more cardinal solution - my own proxy, which will be authorized on the corporate proxy.
Then I found only NTLMAPS .
For some time I used this proxy - in general, it performs its function, but there were some unpleasant moments:
- A decent drop in network speed, especially with a large number of simultaneous requests
- quite noticeable CPU load
- lack of regular ability to work as a service (had to additionally use srvany )
- the need to keep the password clear in the config file
- inability to use special characters in the password, etc.
Result and Buns
Everyone has probably guessed that there is still a worthy and more convenient NTLMAPS replacement, which I want to talk about. And her name is CNTLM .
It is this proxy that I have been using at work for the past few years (colleagues working under Linux also opted for CNTLM). A lot of time has passed since then ... At first it turned out that we were using squid, ISA and something else ... Then a secret transparent proxy appeared without authorization at all. But I still use CNTLM.
So, for starters, I will give the advantages of CNTLM compared to NTLMAPS:
- almost (I'm afraid to write “absolutely”) an inconspicuous drop in speed (see the end of the article)
- lack of noticeable CPU load and low memory consumption (see end of article)
- service mode operation
- the ability to store a hash in the config instead of the password itself
- the ability to specify multiple parent proxies at once
- the ability to enable gateway mode, etc.
- the ability to specify NoProxy resources (i.e. those for which you do not need to use proxies at all - eg local resources)
- ...
How can this solution be useful:
- Opera no longer asks for username / password - mission accomplished :)
- All software goes to the Internet through CNTLM. When is the
day of judgmentday password change sufficiently to change it only in the config CNTLM.
Previously, I had to do this in a heap of places ... Take for example a computer of a spherical IT specialist in a vacuum: 3 browsers, dropbox, hamachi, teamviewer, miranda, skype, DM, antivirus, kitty, etc. + Many applications that just need an Internet to check for updates.
In addition, after changing the password, all the software continues to crash into the Internet with the old password, which leads to a temporary ban on the proxy ... I hope it’s already clear - I and my colleagues were not very comfortable). - As it turned out, not all modern programs can go to the Internet through proxies with authorization. CNTLM really helps out in this situation
- All virtual machines and the necessary machines in LAN can also be uploaded to the Internet via CNTLM (turning on gateway mode in the config)
- Let's say the main corporate proxy has a habit of regularly falling. We drive into the config all available proxies and CNTLM will be transparent for us to iterate over them in the list if the main proxy fails.
This is just a list of the applications that came to my mind. I am sure that many will be able to come up with something else.
Getting started
Under Windows, we are offered an installer that will do everything well: create a service and unzip files to the right place.
Nevertheless, you still have to work with your hands.
- We drive our data into % PROGRAMFILES% \ Cntlm \ cntlm.ini.
In general, we are interested in the following parameters:
Username -> our proxy or domain login
Domain ->
Proxy domain name -> IP address \ parent proxy name +
Listen port -> local port on which CNTLM will be waiting for us with open arms
Specify the necessary data and restart the CNTLM service. - Find out the details of the “dialect” of the corporate proxy and drive the password \ hash into the desired config parameter.
This info can be pulled from the admins, but you can try to solve this issue with CNTLM tools. To do this, run CNTLM with the keys -I and -M and the address of any external site:cntlm.exe -I -M ya.ru
drive the password with your hands and see something like this output: From here it is clear that NTLMv2 is used. In addition, CNTLM immediately shows us the hash of the entered password. So we got the last missing PassNTLMv2 parameter . We paste it into the CNTLM config and restart the service.Auth NTLMv2
PassNTLMv2 4AC6525378DF8C69CF6B6234532943AC - We drive in the browser \ ICQ \ ... proxy localhost: X, where X is our local port specified in the config.
A spoon of tar
Since CNTLM uses Cygwin, which by default pours events into the eventlog, we have a frantic amount of garbage in the Application log (Event for each HTTP request is Event ID 0 Source Cygwin):
The description for Event ID 0 from source Cygwin cannot be found. Either the component that raises this event is not installed on your local computer or the installation is corrupted. You can install or repair the component on the local computer.
If the event originated on another computer, the display information had to be saved with the event.
The following information was included with the event:
127.0.0.1 GET s.w3bsit3-dns.com/forum/style_emoticons/default/thank_you.gif You
can live with this, of course, but finding something really useful in the log is quite difficult.
If someone prompts an elegant solution - I will be grateful.
The only thing that has occurred to me so far is to remove all syslog () calls in the source.
PS
I bring the promised comparison of performance with NTLMAPS (these data were previously indicated on the CNTLM website, but have recently been removed).Fig. 1. Check the execution time of the request with wget. Please note that the time of the 1st and subsequent request when using NTLMAPS is almost the same (~ 2 sec). In the case of CNTLM - the first request is 5 times faster, the next one - already 15 times - there is connection caching.

Fig. 2. We look at CPU and RAM consumption with 50 parallel connections.

