Attack MOSQUITO: protocol for covert data transmission between speakers and headphones in the form of ultrasound
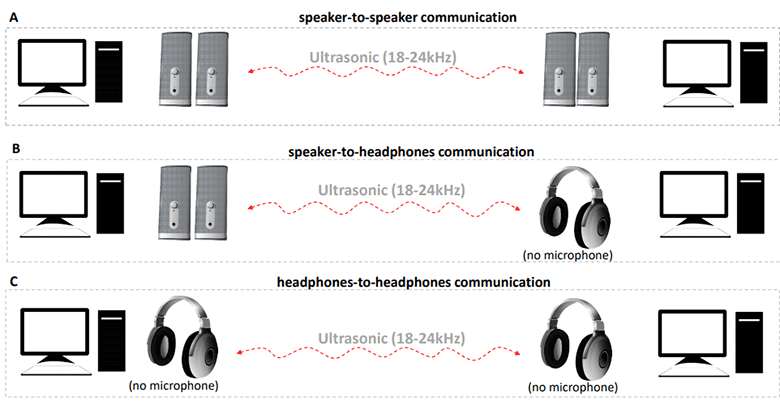
Three scenarios for a hypothetical secret data channel: speakers-speakers, headphones-headphones (without a microphone) and headphones-headphones (without microphones)
Specialists from the Ben-Gurion University Computer Security Research Center in recent years have presented many creative ways to remove information from an isolated computer: the blinking of the HDD LED , the electromagnetic radiation from the USB connector , the noise of the GPU cooler, and so on.
At the end of 2016, they presented the program Speake (a) r , which imperceptibly for the user turns his headphones into a microphone. Now experts have described the attack MOSQUITO with a description of the protocol for data exchange between speakers and headphones on different computers located at a distance of up to 10 meters.
At the hardware level, the microphone and speakers / headphones work on a similar principle. The microphone converts sound into electrical signals, and passive speakers or headphones perform the reverse operation. In both devices there is a small diaphragm that oscillates in a magnetic field to generate / detect sound waves. A similar hardware device allows you to use a microphone instead of headphones or headphones instead of a microphone .
The feature of the program Speake (a) r is that it imperceptibly changes the purpose of the audio jack, where the headphones are connected. Instead of audio output (line out), the connector starts to work on receiving data (line in).
The MOSQUITO attack envisages that the malware is somehow installed on a computer isolated from external data transfer channels (air-gapped) and then transmits the secret information found on this computer — local files — by generating sound through connected speakers or headphones.
Information is received on another PC. It is assumed that this second computer either belongs to the attacker or is also infected with the malware, but is also connected to the Internet, so that it can “merge” information into the outside world. The receiving computer receives the audio signal through the connected speakers or headphones and restores the original files. It should be noted that the active speakers can not be used as microphones. In this quality, only passive speakers or regular headphones work.
The researchers published the details of the data transfer protocol and tested it at distances from 1 to 9 meters. The maximum transmission speed was 1200-1800 bps if the speakers of two computers are directed at each other, and the sound is emitted in the audible range (below 18 kHz).
If we consider more realistic scenarios, when the data transfer is required to hide from the people present, and the columns are deployed in different directions, then the transmission speed is significantly reduced. The problem is that speakers for home users are often optimized for better sound exclusively at mid frequencies, which are best perceived by human hearing. Accordingly, the speakers that are not perceived by humans as ultra-low and ultra-high frequencies do not work very well.
The transmission speed is also reduced if, instead of speakers for sound transmission, to use in-ear headphones - from 300 to 600 bps, and in the case of head-mounted microphones even less - up to 250 bps. The reason is that closed headphones direct sound in one direction and isolate it fairly well in others, so that successful data transfer is possible only at a very small distance.
Under laboratory conditions, at a distance of 3 meters in the range from 18 kHz to 24 kHz with an error rate of no more than 1%, the transfer of a kilobyte file was made at a speed of 166 bit / s. At a distance of 4 to 9 meters with the same error rate, the speed drops to 10 bit / s.
Among other factors that limit the speed of data transmission, scientists call ambient noises, including music and human speech. But many interferences can be avoided by transmitting information in the range above 18 kHz.
Researchers believe that the most effective way to protect against such an attack is to disconnect headphones and speakers from the computer, but this is not always possible.
