New virus spreading through flash drives
Some time ago, VirusBlokAda experts reported the discovery of a new virus spread through USB-carriers. A feature of the work of this malware is the following:
1. A well-known vulnerability with autorun.inf is not used for implementation in the system. This time, the work is built on an absolutely fresh vulnerability that affects all versions of the Windows system. The essence of this vulnerability: shortcut files with the following name are created on the media: Each shortcut, when processed by the system to display the shortcut image, launches the ~ wtr4141.tmp Trojan library (or ~ wtr4132.tmp, the numbers may be different). Exploit option is currently publicly available
, which makes us think that something else will happen - the vulnerability is still not covered and is a tidbit for the virmakers.
2. After infection, 2 files are placed in the% SystemRoot% \ System32 \ drivers directory: mrxnet.sys and mrxcls.sys, one of which works as a file system filter driver, and the second as an injector of malicious code. The% SystemRoot% \ inf directory contains 2 files oem6c.pnf and oem7a.pnf, the contents of which are encrypted. The drivers are signed with a valid digital signature issued by Realtec Semiconductor:



At the moment, this certificate has been revoked . However, a new version of the malware, similar in functionality, is signed by a certificate from JMicron Technology:
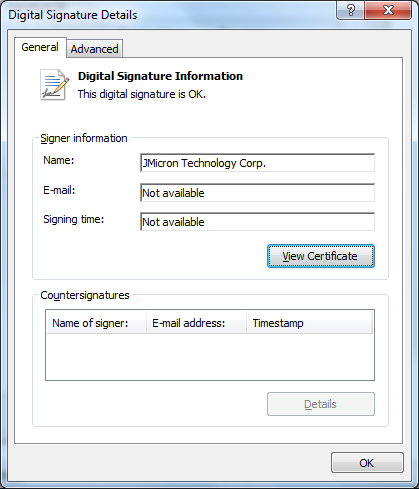
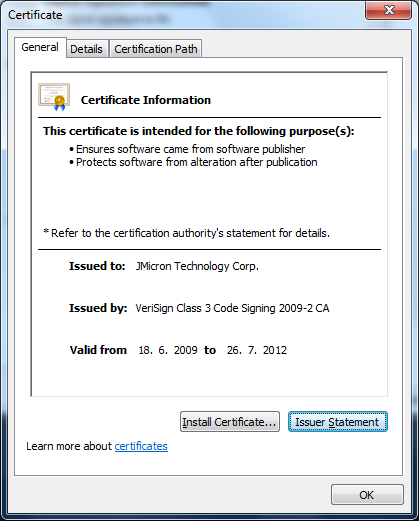
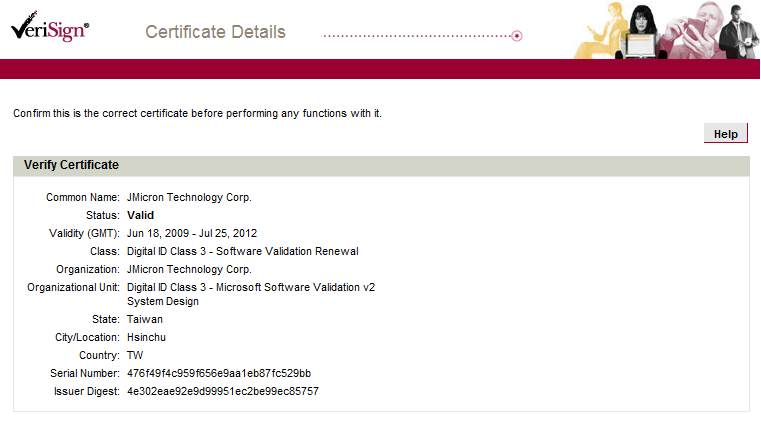
Please note: this certificate is not expired, as in the case of Realtec.
3. Immediately after infection, without rebooting, the rootkit launches additional threads in system processes, hiding the modules from which these threads were launched, and installs hooks in the system processes services.exe, svchost.exe, lsass.exe, possibly winlogon .exe. This allows you to hide the above malware files and implement malicious functionality.
At the moment, the largest number of victims of the malware recorded in India, Iran and Indonesia, however, isolated cases have been noted in other countries, including the CIS countries.
At the moment, the study of the virus continues, in particular, the mechanisms of malicious activity are not fully understood. There is an opinionthat the malware is engaged in industrial espionage, connecting to specialized Siemens Simatic WinCC systems. However, a final analysis is not yet available.
Currently, for ordinary users, the danger is not even this malware (already named Trojan-Dropper.Win32.Stuxnet, Rootkit.TmpHider, SScope.Rookit.TmpHider.2, etc.), and the open new concept of the possibility of infection via USB carriers. The only way to prevent infection with new options that have not yet been included in the anti-virus database is to disable the display of icons for shortcuts, as well as the WebClient service.
AddOn : While the message is undergoing scans and evaluations, I found it seems like the first worthy analysis of Stuxnet . Therefore, I decided to mention it.
1. A well-known vulnerability with autorun.inf is not used for implementation in the system. This time, the work is built on an absolutely fresh vulnerability that affects all versions of the Windows system. The essence of this vulnerability: shortcut files with the following name are created on the media: Each shortcut, when processed by the system to display the shortcut image, launches the ~ wtr4141.tmp Trojan library (or ~ wtr4132.tmp, the numbers may be different). Exploit option is currently publicly available
"Copy of Copy of Copy of Copy of Shortcut to.lnk"
"Copy of Copy of Copy of Shortcut to.lnk"
"Copy of Copy of Shortcut to.lnk"
"Copy of Shortcut to.lnk", which makes us think that something else will happen - the vulnerability is still not covered and is a tidbit for the virmakers.
2. After infection, 2 files are placed in the% SystemRoot% \ System32 \ drivers directory: mrxnet.sys and mrxcls.sys, one of which works as a file system filter driver, and the second as an injector of malicious code. The% SystemRoot% \ inf directory contains 2 files oem6c.pnf and oem7a.pnf, the contents of which are encrypted. The drivers are signed with a valid digital signature issued by Realtec Semiconductor:



At the moment, this certificate has been revoked . However, a new version of the malware, similar in functionality, is signed by a certificate from JMicron Technology:



Please note: this certificate is not expired, as in the case of Realtec.
3. Immediately after infection, without rebooting, the rootkit launches additional threads in system processes, hiding the modules from which these threads were launched, and installs hooks in the system processes services.exe, svchost.exe, lsass.exe, possibly winlogon .exe. This allows you to hide the above malware files and implement malicious functionality.
At the moment, the largest number of victims of the malware recorded in India, Iran and Indonesia, however, isolated cases have been noted in other countries, including the CIS countries.
At the moment, the study of the virus continues, in particular, the mechanisms of malicious activity are not fully understood. There is an opinionthat the malware is engaged in industrial espionage, connecting to specialized Siemens Simatic WinCC systems. However, a final analysis is not yet available.
Currently, for ordinary users, the danger is not even this malware (already named Trojan-Dropper.Win32.Stuxnet, Rootkit.TmpHider, SScope.Rookit.TmpHider.2, etc.), and the open new concept of the possibility of infection via USB carriers. The only way to prevent infection with new options that have not yet been included in the anti-virus database is to disable the display of icons for shortcuts, as well as the WebClient service.
AddOn : While the message is undergoing scans and evaluations, I found it seems like the first worthy analysis of Stuxnet . Therefore, I decided to mention it.
