XSS vulnerability on the site Futurico.ru
I found a semi-active XSS vulnerability on the site Futurico.ru.
It's simple: enter a message on the site (a small phrase).
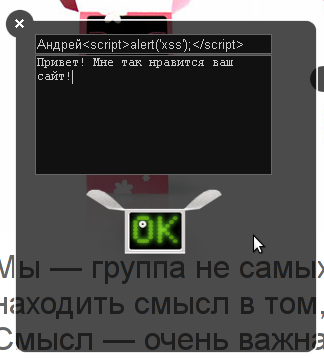
Then we find out the message id - we capture the POST parameters during loading:

Now just pass the futurico.ru/map/getPointInfo.php?point= **** POST parameter using the GET method and see our message:
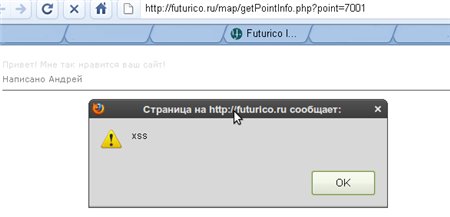
There is no filtering.
At the moment, the developers have partially disabled the "small phrases", but you can still write messages and access them via id.
More information can be found here.
It's simple: enter a message on the site (a small phrase).

Then we find out the message id - we capture the POST parameters during loading:

Now just pass the futurico.ru/map/getPointInfo.php?point= **** POST parameter using the GET method and see our message:

There is no filtering.
At the moment, the developers have partially disabled the "small phrases", but you can still write messages and access them via id.
More information can be found here.
