Five technologies used in Iran
The authorities of any country in the world are filtering network content. It `s naturally. Each filters something of its own. In America, casino sites are blocked, in Europe - sites with Nazi symbols, in China and Belarus are blocked sites of political opponents. Recently, Iran joined the “censors”, and some of the technological methods used there are something new, we have not seen this even in China.
Here is a list of technologies that Iran’s authorities used to censor the Internet during recent mass riots. The list is based on a document compiled by the human rights hacker organization NedaNet .
IP Blocking
The standard methodology used by the governments of many countries, including Belarus and Russia. Ineffective against P2P communications, as well as against a network of proxy servers.
Traffic Classification (QoS)
A more advanced monitoring technology when traffic that is transmitted through certain protocols and certain ports is damaged. This is done in order to reduce the total amount of traffic in the local Internet segment (throughput of external communication channels is estimated at 6 Gb / s), and to reduce the load on monitoring systems, which are quite resource-intensive, especially in the case of deep filtering by content.
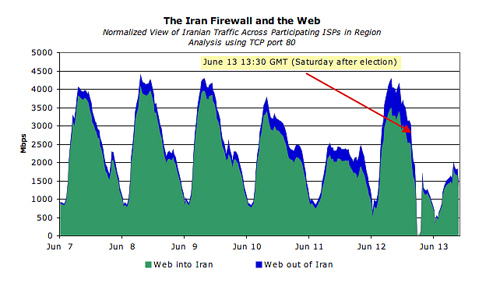
The diagram shows the amount of traffic on Iranian backbones per election week (TCP, port 80). As you can see, at some point the authorities simply blocked the external channel.
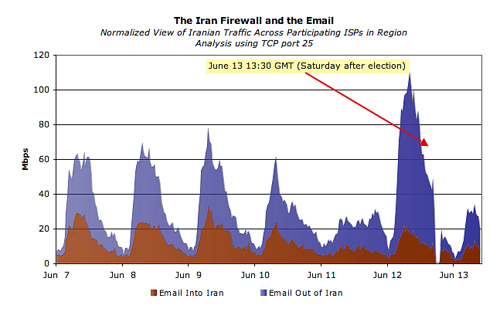
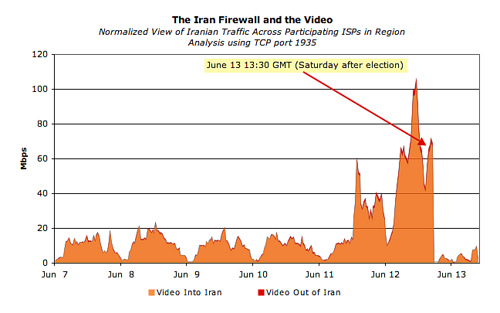
And here are the volumes of mail traffic (port 25) and video (port 1935). Here, the fact of filtering is even more obvious.
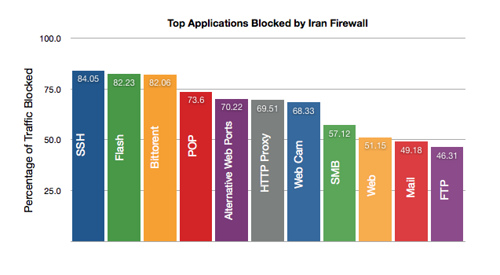
Experts estimate the percentage of blocked traffic this way, depending on the protocol.
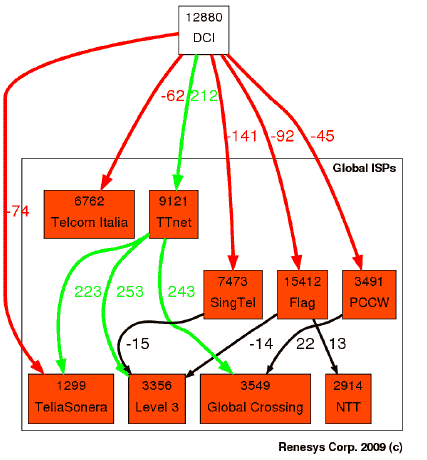
The following diagram shows a decrease in the amount of traffic passing through the networks of each of the Iranian providers in the days after the election (red arrows), while only TTNet (Turk Telecom) began to pass more traffic. This is due to the fact that the Turkish provider has more efficient content filtering systems than competitors.
Package Header Analysis
In fact, header analysis is a form of deep packet inspection (DPI, see below). Only packet headers are analyzed here, and nothing more. Although this technique is much less effective than DPI, it was used more often in Iran because it is suitable for processing much larger amounts of information. For example, in this way, you can easily identify all SSL packets that use deeper analysis methods.
The widespread use of heading analysis allows human rights activist hackers to trick the enemy, which they successfully did in Iran when they wrapped SSL traffic in FTP packet headers.
Package Feature Analysis
This is a more advanced filtering method, because it analyzes not only the packet headers, but also their bit length, transmission frequency and other characteristics by which the content can be determined.
In Iran, this technique was used to block SSH traffic, but at the same time maintain the working capacity of corporate VPNs that use the same protocol.
Deep packet inspection / Content filtering
The most advanced and resource-intensive filtering method when analyzing the contents of packages. Even if cryptography is used, this protection cannot be circumvented, because in combination with other methods of verification, authorities can easily determine what they are dealing with.
Iranian activists have not been able to find a way around this protection, except that sometimes they found holes that could be used, but the authorities quickly closed them.
via Network World
Here is a list of technologies that Iran’s authorities used to censor the Internet during recent mass riots. The list is based on a document compiled by the human rights hacker organization NedaNet .
IP Blocking
The standard methodology used by the governments of many countries, including Belarus and Russia. Ineffective against P2P communications, as well as against a network of proxy servers.
Traffic Classification (QoS)
A more advanced monitoring technology when traffic that is transmitted through certain protocols and certain ports is damaged. This is done in order to reduce the total amount of traffic in the local Internet segment (throughput of external communication channels is estimated at 6 Gb / s), and to reduce the load on monitoring systems, which are quite resource-intensive, especially in the case of deep filtering by content.
The diagram shows the amount of traffic on Iranian backbones per election week (TCP, port 80). As you can see, at some point the authorities simply blocked the external channel.

And here are the volumes of mail traffic (port 25) and video (port 1935). Here, the fact of filtering is even more obvious.


Experts estimate the percentage of blocked traffic this way, depending on the protocol.

The following diagram shows a decrease in the amount of traffic passing through the networks of each of the Iranian providers in the days after the election (red arrows), while only TTNet (Turk Telecom) began to pass more traffic. This is due to the fact that the Turkish provider has more efficient content filtering systems than competitors.

Package Header Analysis
In fact, header analysis is a form of deep packet inspection (DPI, see below). Only packet headers are analyzed here, and nothing more. Although this technique is much less effective than DPI, it was used more often in Iran because it is suitable for processing much larger amounts of information. For example, in this way, you can easily identify all SSL packets that use deeper analysis methods.
The widespread use of heading analysis allows human rights activist hackers to trick the enemy, which they successfully did in Iran when they wrapped SSL traffic in FTP packet headers.
Package Feature Analysis
This is a more advanced filtering method, because it analyzes not only the packet headers, but also their bit length, transmission frequency and other characteristics by which the content can be determined.
In Iran, this technique was used to block SSH traffic, but at the same time maintain the working capacity of corporate VPNs that use the same protocol.
Deep packet inspection / Content filtering
The most advanced and resource-intensive filtering method when analyzing the contents of packages. Even if cryptography is used, this protection cannot be circumvented, because in combination with other methods of verification, authorities can easily determine what they are dealing with.
Iranian activists have not been able to find a way around this protection, except that sometimes they found holes that could be used, but the authorities quickly closed them.
via Network World
