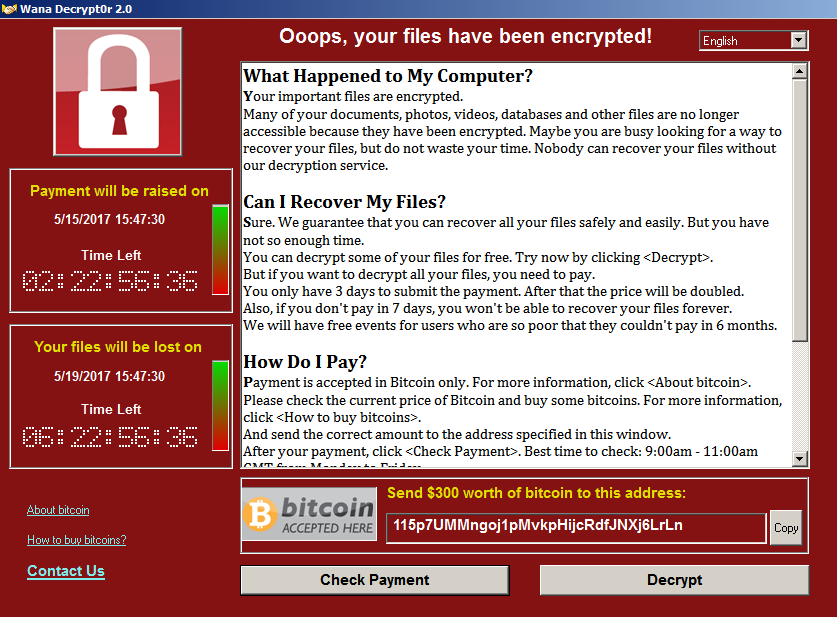
A massive attack with a cryptor Wana decrypt0r 2.0
At the moment, we can observe a large-scale attack with a Trojan-decryptor "Wana decrypt0r 2.0". The
attack is observed in different networks that are completely unrelated between themselves.

A ransomware spreading in the lab at the university ( from here )
Some companies advise their users to turn off their computers and wait for further instructions.

Contacting former colleagues, I was surprised by similar stories.
As for me, today I prepared several new Windows images for our cloud system, among them was Windows Server 2008 R2.
What is most interesting is that when I just installed Windows and set up a static IP address on it, it was immediately infected for several minutes.
All Windows images were obtained from MSDN, the hashes are the same, so the possibility of image infection is excluded.
And this is despite the fact that the firewall configuration for a single network interface looking outward has been configured as a “Public Network”.
Nmap does not find open ports. The nmap output shows that even in this case, some ports are open outside by default:
Host is up (0.017s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
49154/tcp openunknownThe only thing that was installed in the system is Virtio drivers that were loaded when you installed Windows from an external CD.
The ISO image was also obtained from an official source - the Fedora repository, the hash of the amount is also the same.
At the moment, it is not fully known how exactly the infection occurred and which specific Windows versions are vulnerable..
If you have similar cases, share information about them.
Several links on the topic:
- Virustotal Link
- Information on Mmalwr
- Details of WannaCry on GitHub
- Wenta Decrypt0r 2.0 cipher analysis from Pentestit
other links, see the comments to this news.
We are waiting for further news, all with Friday, and here's a nice wallpaper for your desktop:
UPD: Apparently, for attack the vulnerability of the SMBv1 protocol is used.
Patches to fix this vulnerability can be downloaded on the official website:
- Microsoft Security Bulletin MS17-010
- Patch, for older systems (Windows XP, Winows Server 2003R2)
Vulnerability can also be closed by completely disabling SMBv1 support. To do this, simply run the following command in the command line running as Administrator (works in Windows 8.1 and higher versions):
dism /online /norestart /disable-feature /featurename:SMB1ProtocolIt is still recommended to install patches.
UPD2: According to numerous requests, information is added on how to check whether you are afraid or not. The following steps will help you understand if a patch is installed that covers this vulnerability in your system:
- Follow the link above and check the update code for your system, for example for Windows 7 or Windows Server 2008 R2, the code will be
4012212either4012215 - Open
cmd.exe(command line) - Write:
wmic qfe list | findstr4012212 - Press enter
- If you see something like this in the answer, it means that you already have the patch installed and you can sleep in peace:
http://support.microsoft.com/?kbid=4012212 P2 SecurityUpdate KB4012212 NT AUTHORITY\система 3/18/2017 - If the answer returns an empty string to you, try checking the next patch from the list.
- If no patch is found, it is recommended to immediately install the update from the link above or from the direct link from UPD9
As it turned out, this method is not 100% working and everyone can have their own nuances.
If you are still sure that the security update is installed, and you still receive a blank line in response, try checking the update through the Windows update log or reading comments on this article.
UPD3: There are interesting details on this incident on the Internet :
Yes, that is right. A set of FuzzBunch exploits appeared, which the Shadow Brokers group of hackers stole from the Equation Group, hackers from the Nat Agency. US security.
Microsoft has quietly covered the holes with an MS 17-010 update, perhaps the most important update in the last ten years.
While the exploit kit has been in the public domain for a week now https://github.com/fuzzbunch/fuzzbunch with instructional videos.
In this set there is a dangerous tool DoublePulsar.
In short, if port 445 is open and the MS 17-010 update is not installed, then DoublePulsar taps
this port, intercepts system calls and injects malicious code into memory.
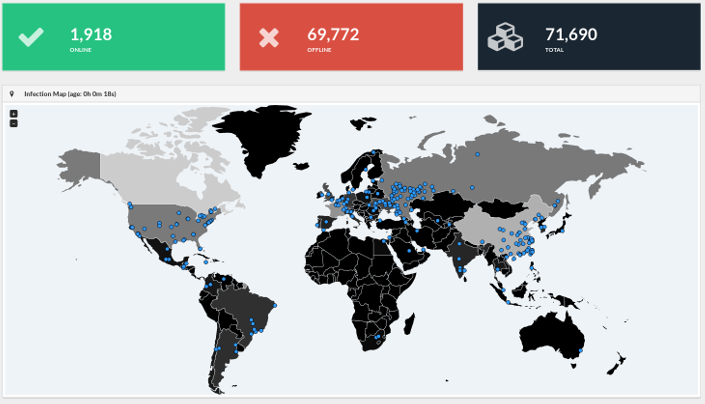
UPD4: Interactive infection map:
UPD5: Video showing the visual use of the exploit:
UPD6: Found an interesting flaw in the code:
The spread of the ransomware virus WannaCrypt was suspended by registering the domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com.
A security specialist who tweets @MalwareTechBlog found that the virus for some reason was accessing this domain and decided to register it in order to monitor the activity of the program.
As it turned out later, the virus code stated that if the access to this domain is successful, then the infection should be stopped; if not, continue. Immediately after registering a domain, tens of thousands of queries came to him.
The ransomware virus began to spread on May 12th. It blocks the computer and requires $ 300 for unlocking. Tens of thousands of infections were registered in 99 countries, including Russia, where Megafon, the Interior Ministry and the UK became victims. In other countries, telecommunications companies, banks, and consulting firms suffered. In the UK, the health care system computers have failed.
Registering the aforementioned domain did not help those who were already infected, but allowed others to install a Windows update, after which the virus does not work.
UPD7: Microsoft has released a patch for older systems (Windows XP and Windows Server 2003R2)
UPD8: Copypaste with 2ch.hk
Those who started this attack haveShadow brokers
merged exploits Network Scanner which they themselves wrote on a C / Python
Linux server
How it works?The scanner script runs on a Linux server. It
drives in a specific IP range or an entire country.
The script scans the range to an open 445 port.
In case of successful detection of the SMB service, it sends an exploit that causes a buffer overflow
.
UPD9: official direct links to this patch for various systems:
Windows XP: download.windowsupdate.com/d/csa/csa/secu/2017/02/windowsxp-kb4012598-x86-custom-rus_84397f9eeea668b975c0c2cf9aaf0e2312f50077.exe
Windows XP x64: http://download.windowsupdate.com/d/csa/csa/secu/2017/02/windowsserver2003-kb4012598-x64-custom-enu_f24d8723f246145524b9030e4752c96430981211.exe
Windows Vista x86: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.0-kb4012598-x86_13e9b3d77ba5599764c296075a796c16a85c745c.msu
Windows Vista x64: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.0-kb4012598-x64_6a186ba2b2b98b2144b50f88baf33a5fa53b5d76.msu
Windows 7 x86: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.1-kb4012212-x86_6bb04d3971bb58ae4bac44219e7169812914df3f.msu
Windows 7 x64: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.1-kb4012212-x64_2decefaa02e2058dcd965702509a992d8c4e92b3.msu
Windows 8 x86: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8-rt-kb4012214-x86_5e7e78f67d65838d198aa881a87a31345952d78e.msu
Windows 8 x64: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8-rt-kb4012214-x64_b14951d29cb4fd880948f5204d54721e64c9942b.msu
Windows 8.1 x86: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8.1-kb4012213-x86_e118939b397bc983971c88d9c9ecc8cbec471b05.msu
Windows 8.1 x64: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8.1-kb4012213-x64_5b24b9ca5a123a844ed793e0f2be974148520349.msu
Windows 10 x86: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windows10.0-kb4012606-x86_8c19e23de2ff92919d3fac069619e4a8e8d3492e.msu
Windows 10 x64: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windows10.0-kb4012606-x64_e805b81ee08c3bb0a8ab2c5ce6be5b35127f8773.msu
Windows 10 (1511) x86: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windows10.0-kb4013198-x86_f997cfd9b59310d274329250f14502c3b97329d5.msu
Windows 10 (1511) x64: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windows10.0-kb4013198-x64_7b16621bdc40cb512b7a3a51dd0d30592ab02f08.msu
Windows 10 (1607) x86: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windows10.0-kb4013429-x86_8b376e3d0bff862d803404902c4191587afbf065.msu
Windows 10 (1607) x64: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/03/windows10.0-kb4013429-x64_ddc8596f88577ab739cade1d365956a74598e710.msu
Windows Server 2003 x86: http://download.windowsupdate.com/c/csa/csa/secu/2017/02/windowsserver2003-kb4012598-x86-custom-rus_62e38676306f9df089edaeec8924a6fdb68ec294.exe
Windows Server 2003 x64: http://download.windowsupdate.com/c/csa/csa/secu/2017/02/windowsserver2003-kb4012598-x64-custom-rus_6efd5e111cbfe2f9e10651354c0118517cee4c5e.exe
Windows Server 2008 x86: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.0-kb4012598-x86_13e9b3d77ba5599764c296075a796c16a85c745c.msu
Windows Server 2008 x64: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.0-kb4012598-x64_6a186ba2b2b98b2144b50f88baf33a5fa53b5d76.msu
Windows Server 2008 R2: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windows6.1-kb4012212-x64_2decefaa02e2058dcd965702509a992d8c4e92b3.msu
Windows Server 2012: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8-rt-kb4012214-x64_b14951d29cb4fd880948f5204d54721e64c9942b.msu
Windows Server 2012 R2: http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windows8.1-kb4012213-x64_5b24b9ca5a123a844ed793e0f2be974148520349.msu
Windows Server 2016: http://download.windowsupdate.com/d/msdownload/update/software/secu/2017/03/windows10.0-kb4013429-x64_ddc8596f88577ab739cade1d365956a74598e710.msu
UPD10: Encryption versions appeared, ignoring the killswitch method described in UPD6 .
Thanks to xsash , Inflame , Pulse , nxrighthere , waisberg , forajump , Akr0n , LESHIY_ODESSA , Pentestit , alguryanow and others for the many additions to this article.
Only registered users can participate in the survey. Sign in , please.