Windows Crash Dump Analysis
How often do you have to see the Windows death screen (BSoD)? BSoD can occur in different cases: both when working with the system, and in the process of loading the operating system. How to determine what caused the appearance of BSoD and fix this problem? The Windows operating system is able to save a memory dump when an error occurs, so that the system administrator can analyze the dump data and find the cause of the BSoD.
There are two types of memory dumps - small (minidump) and full. Depending on the settings of the operating system, the system may save full or small dumps, or take no action if an error occurs.
A small dump is located on the % systemroot% \ minidump path and has a name like Minixxxxxx-xx.dmp
A full dump is located on the % systemroot% path and has a name like Memory.dmp
To analyze the contents of memory dumps, you should use a special utility - Microsoft Kernel Debugger.
You can get the program and the components necessary for its operation directly from the Microsoft site - Debugging Tools.
When choosing a debugger, you should take into account the version of the operating system on which you will have to analyze memory dumps. For a 32-bit OS, a 32-bit version of the debugger is required, and for a 64-bit OS, it is preferable to use a 64-bit version of the debugger.
In addition to the Debugging Tools for Windows package itself, you will also need a set of debugging symbols - Debugging Symbols. The set of debugging symbols is specific to each OS on which BSoD has been fixed. Therefore, you will have to download the character set for each OS, the analysis of which you will have to. A 32-bit Windows XP will require a character set for Windows XP 32-bit, a 64-bit OS will require a character set for Windows XP 64-bit. For other operating systems of the Windows family, character sets are selected in accordance with the same principle. You can download debugging symbols from here . It is recommended to install them at the address % systemroot% \ symbols
After installing the debugger and debugging symbols, we start the debugger. The debugger window after startup looks as follows.
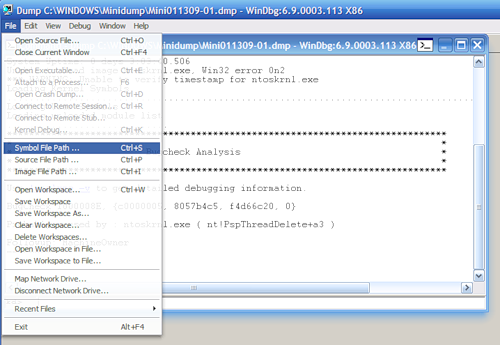
Before analyzing the contents of a memory dump, you will need to make a small debugger setup. Specifically, tell the program which way to look for debugging symbols. To do this, select File> Symbol File Path ... from the menu ... Click the Browse ... button and specify the folder in which we installed the debugging symbols for the memory dump in question.
You can request information about the required debugging symbols directly over the Internet, from the Microsoft public server. This way you will have the newest version of the characters. You can do this as follows - in the File> Symbol File Path ... menu, enter: SRV *% systemroot% \ symbols * http: //msdl.microsoft.com/download/symbols
After specifying the path to the debugging symbols, select File> Save from the menu workspace and confirm the action by clicking on the OK button.
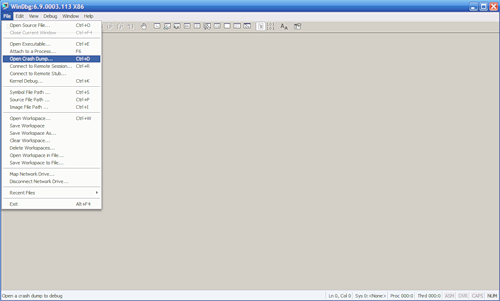
To begin the analysis of a memory dump, select File> Open Crash Dump ... from the menu and select the file required for consideration.
The system will analyze the content, at the end of which it will give a result about the alleged cause of the error.
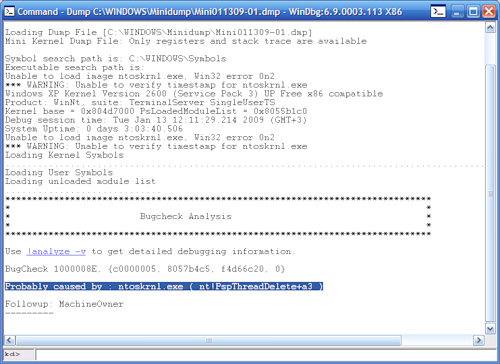
The! Analyze -v command given to the debugger on the command line will display more detailed information.
You can complete debugging by choosing the menu item Debug> Stop Debugging.
Thus, using the Debugging Tools for Windows package, you can always get a fairly complete picture of the causes of system errors.
There are two types of memory dumps - small (minidump) and full. Depending on the settings of the operating system, the system may save full or small dumps, or take no action if an error occurs.
A small dump is located on the % systemroot% \ minidump path and has a name like Minixxxxxx-xx.dmp
A full dump is located on the % systemroot% path and has a name like Memory.dmp
To analyze the contents of memory dumps, you should use a special utility - Microsoft Kernel Debugger.
You can get the program and the components necessary for its operation directly from the Microsoft site - Debugging Tools.
When choosing a debugger, you should take into account the version of the operating system on which you will have to analyze memory dumps. For a 32-bit OS, a 32-bit version of the debugger is required, and for a 64-bit OS, it is preferable to use a 64-bit version of the debugger.
In addition to the Debugging Tools for Windows package itself, you will also need a set of debugging symbols - Debugging Symbols. The set of debugging symbols is specific to each OS on which BSoD has been fixed. Therefore, you will have to download the character set for each OS, the analysis of which you will have to. A 32-bit Windows XP will require a character set for Windows XP 32-bit, a 64-bit OS will require a character set for Windows XP 64-bit. For other operating systems of the Windows family, character sets are selected in accordance with the same principle. You can download debugging symbols from here . It is recommended to install them at the address % systemroot% \ symbols
After installing the debugger and debugging symbols, we start the debugger. The debugger window after startup looks as follows.

Before analyzing the contents of a memory dump, you will need to make a small debugger setup. Specifically, tell the program which way to look for debugging symbols. To do this, select File> Symbol File Path ... from the menu ... Click the Browse ... button and specify the folder in which we installed the debugging symbols for the memory dump in question.

You can request information about the required debugging symbols directly over the Internet, from the Microsoft public server. This way you will have the newest version of the characters. You can do this as follows - in the File> Symbol File Path ... menu, enter: SRV *% systemroot% \ symbols * http: //msdl.microsoft.com/download/symbols
After specifying the path to the debugging symbols, select File> Save from the menu workspace and confirm the action by clicking on the OK button.
To begin the analysis of a memory dump, select File> Open Crash Dump ... from the menu and select the file required for consideration.

The system will analyze the content, at the end of which it will give a result about the alleged cause of the error.

The! Analyze -v command given to the debugger on the command line will display more detailed information.
You can complete debugging by choosing the menu item Debug> Stop Debugging.
Thus, using the Debugging Tools for Windows package, you can always get a fairly complete picture of the causes of system errors.
