NIST is asking for help in creating secure post-quantum data encryption methods
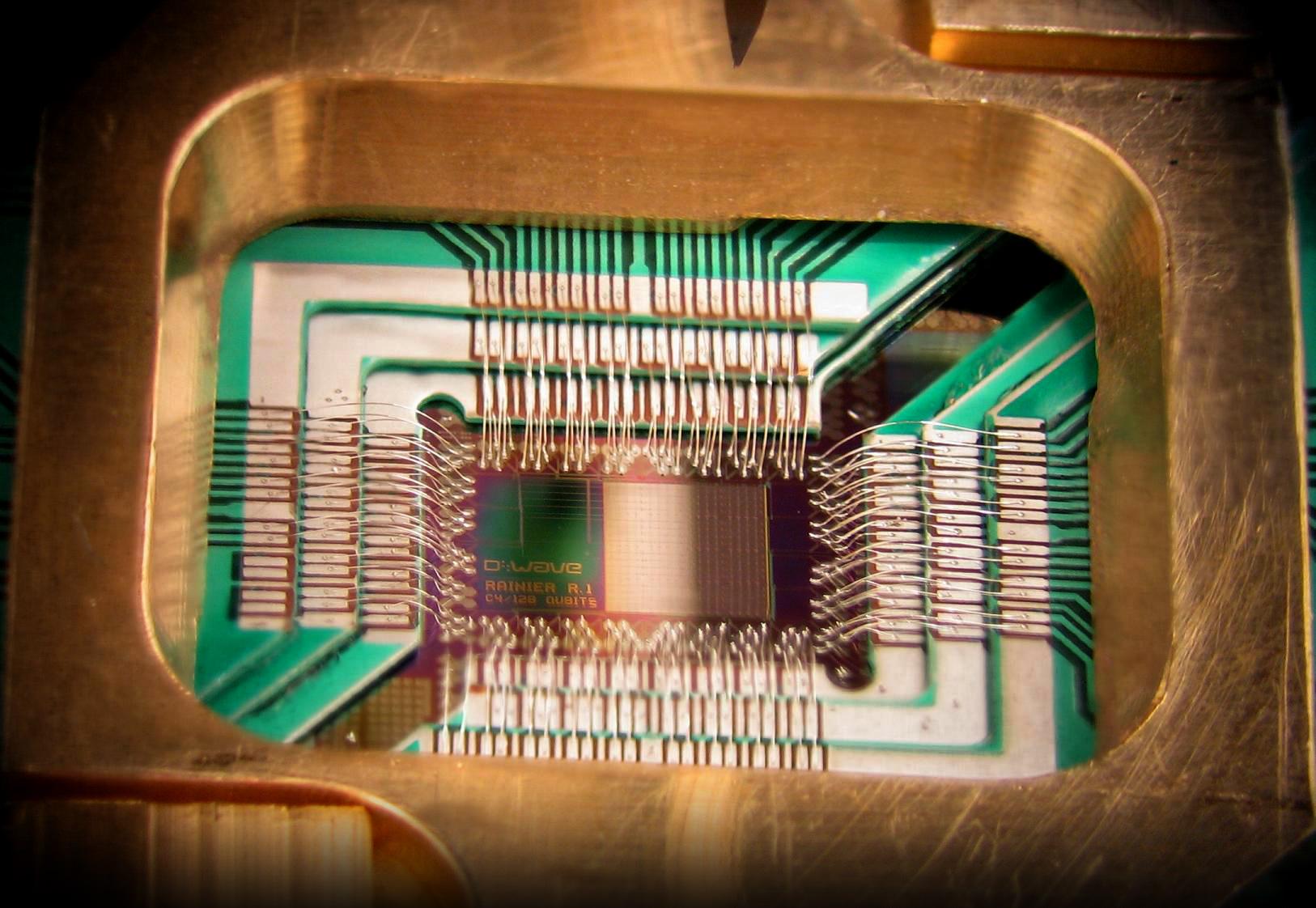
The National Institute of Standards and Technology ( National Institute of Standards and Technology , NIST) has recently appealed to the public to help solve the problem that representatives of the institute call the “impending threat to information security.” The point is that quantum computers, whose prototypes are already working, in the future will be able to easily break into any encryption codes that are used to protect information.
NIST representatives ask cybersecurity experts, scientists and ordinary users to arrange brainstorming on the issue of “post-quantum cryptography”, algorithms that would be inaccessible for quantum computers. The request of the organization is officially registered in the Federal Register .
NIST is committed to working with the American National Standards Institute ( ANSI ) to develop standards and specifications for software solutions used in both the US public sector and commercial applications. The main mission of the institute is to ensure the innovative and industrial competitiveness of the United States by developing the sciences of measurement, standardization and technology in order to improve economic security and improve the quality of life.
In general, the problem outlined by NIST can indeed be called very serious. The fact is that now the majority of traditional cryptosystems rely on the problem of factorization of integers or the problem of discrete logarithms. But such tasks are easy to solve on powerful quantum computers that work withShor algorithm .
It is worth noting that the term “post-quantum cryptography” is quite well-established. It denotes a part of cryptography, which will remain relevant even with the advent of quantum computers and quantum attacks. In general, post-quantum cryptography is based on five different approaches that can solve the problem of quantum attacks. Here are these approaches:
1. Cryptography, which is based on he-functions. Here we are talking, for example, about Merkle's signature with a public key based on a hash tree. The method itself was proposed by Ralph Charles Merklom in 1979. Even then, he considered his idea an interesting alternative to digital signatures RSA and DSA. The problem with the method is that for any public key based on the hash function there is a limit on the number of signatures that can be obtained from the corresponding set of private keys. Therefore, the method was not used. He was remembered only when it came to systems that are resistant to quantum computers;
2. Cryptography based on error correction codes . This method is considered one of the most promising. A classic example is McEliece and Niederreiter encryption schemes ;
3. Lattice-based cryptography . Another promising method. Here, Ring-Learning with Errors can be considered an example, as well as NTRU and GGH ;
4. Cryptography based on multidimensional quadratic systems . This method was proposed in 1996, it is a signature with the public key of Jacques Patarin HFE;
5. Encryption with a secret key . And here we are talking about the Rijndael cipher, proposed in 1998 and subsequently renamed AES (Advanced Encryption Standard).
As mentioned above, despite the fact that quantum computingare in their infancy, to solve the problem of the reliability of cryptographic methods in this area is needed now. They adopt quantum ideas and classic computers .
Dustin Moody, a mathematician at NIST, confirms what has been said, saying that the main task now is to develop new encryption methods for the stored and transmitted information. “We want to replace the three existing NIST cryptographic standards that may be most vulnerable to the impact of cryptographic computing,” says Moody. These standards are FIPS 186-4 , NIST SP 800-56A and NIST SP 800-56B .
The public has almost a year to feed their ideas. Their reception ends in November next year. After that NIST will consider the received applications. Proposals that comply with post-quantum cryptography standards set by NIST will be announced at a public seminar in 2018.
