Security Week 26: spam on Google services
Most often in our weekly digests we discuss some new facts or events related to information security. In some cases, such discoveries are of purely theoretical interest: for example, Specter vulnerabilities in modern processors are unlikely to be exploited en masse in the near future. But freshly discovered critical vulnerabilities in common programs, as a rule, require immediate action if these programs are used in your work or personal infrastructure. Of the recent events, these include zero-day on Windows , a vulnerability in the Exim mail server, or even a completely fresh hole in the VLC player .
But there are security issues that have existed for a long time, evolve slowly and are exploited in large numbers. Less attention is paid to them in the information space: well, it’s clear that there is spam and the widespread fraud associated with it, and now what? Let's take a look at this boring topic for a change, especially since there is a reason. Recently, a detailed review was published on the Kaspersky Lab blog.spamming techniques through numerous Google services. If you're out of luck, you have come across such annoying attacks yourself. This happened with one of the authors of this digest. In this post we will supplement the overview of methods with recommendations and talk about privacy issues using spam as an example. More specifically, how access to your services is essentially limited to two sequences of letters and numbers that everyone knows.
Let's start with the "captain" statement: access to any service in your Google account is possible at your email address. It’s convenient for you as a user: register your mail and immediately receive a messenger, a place to store photos and other files, a calendar and contact manager, and much more. This design is doubly convenient for spammers, and for some time spam has begun to take on new forms. This is now not only sending unsolicited messages to your inbox. With access to the metadata of millions of accounts, Google fights traditional spam quite well, and in the mid-2000s this was a major advantage at the time of the new GMail email service.
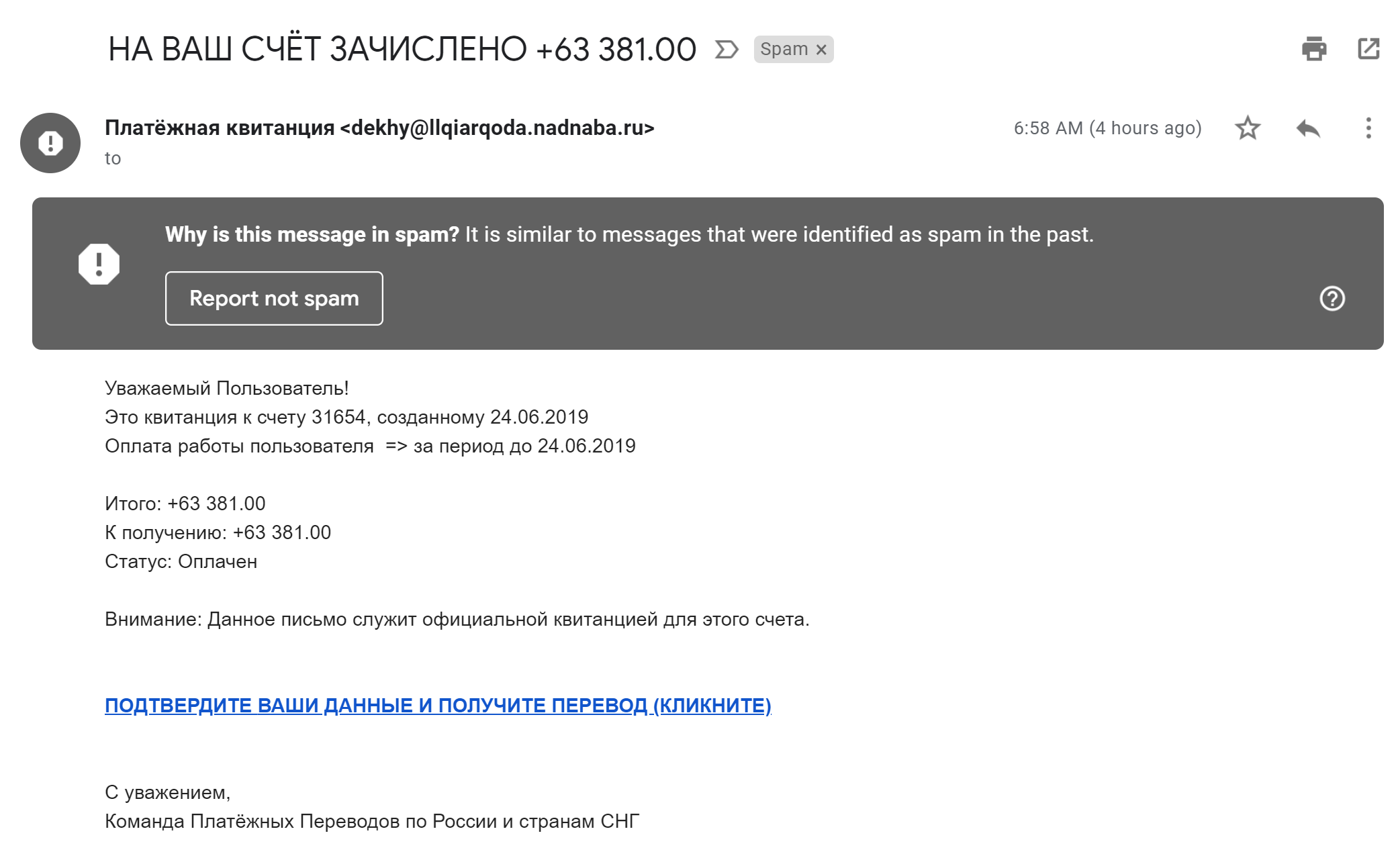
Such messages will appear in the Spam folder with a probability close to 100%. Therefore, spammers began to exploit other Google services: by performing an action on this service, you can cause a message to be sent to the victim using the company's own servers. So spam appeared through Google forms.
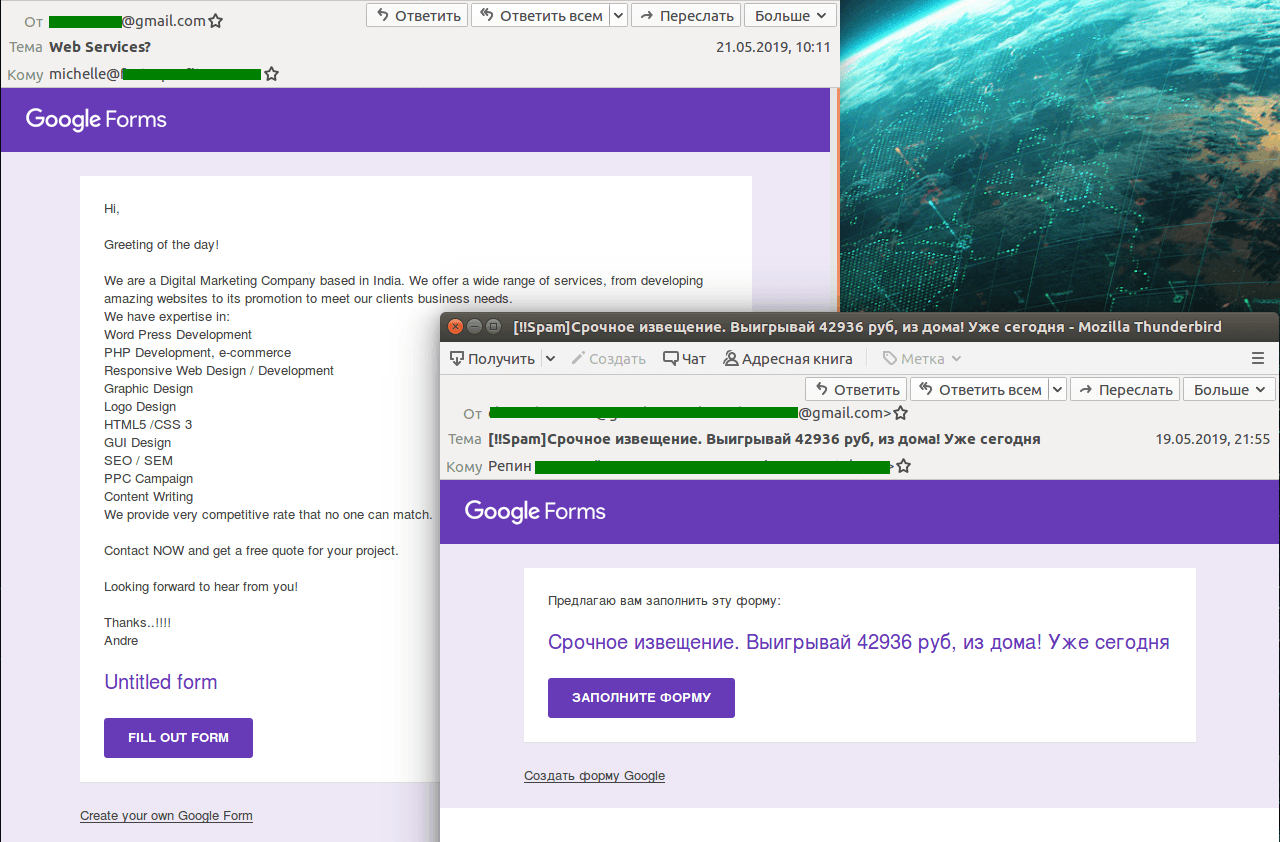
That is: a form is created, it is filled out, your address is indicated, a notification is sent to you (thanks for filling out the form “You received a lot of money, get them soon”). By manipulating the names of the form and individual fields, you can create a message pleasing to the criminal, with reference to fraud with questionnaires, with some inoperative financial schemes, with inflated crypto exchanges. Today we will not investigate what exactly spammers are trying to get from you, this is not important in the context of this story. Such spam can be both mass and targeted.
It should be noted that, according to the subjective impressions of the author of these lines, the peak of spam via Google forms was a year or two ago, now there are almost no such messages. But any third-party services are operated, in the logic of which there is sending e-mail to the user. As a result, your e-mail accounts are registered in online stores, trying to insert a spam link in the "username" field, attack web forms with the "fill and get message" mechanics, and operate technical support systems. This also affects the business, as a rule, a small one that has only basic tools for working with users on the site. However, back to Google. Apparently, it was possible to limit or eliminate spam through Forms, but right now another hole in the logic is being actively exploited: spam via Calendar.
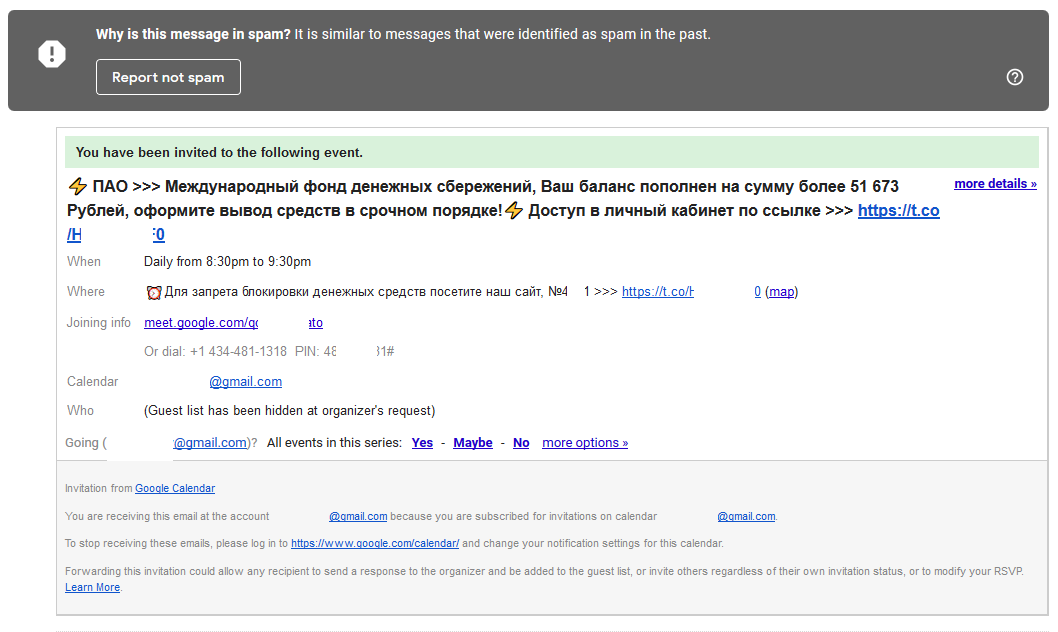
What do we see here? Someone creates an event and sends an invitation to random users on the network, including you. Actually, “spam content” is the name of the event, but it is interesting here that the event is not a one-time event, but a daily one. Wait, but GMail has correctly identified this message as spam - is that all right? And here it is: with the default calendar settings, all invitations are automatically added to your schedule, regardless of the status in the mail.
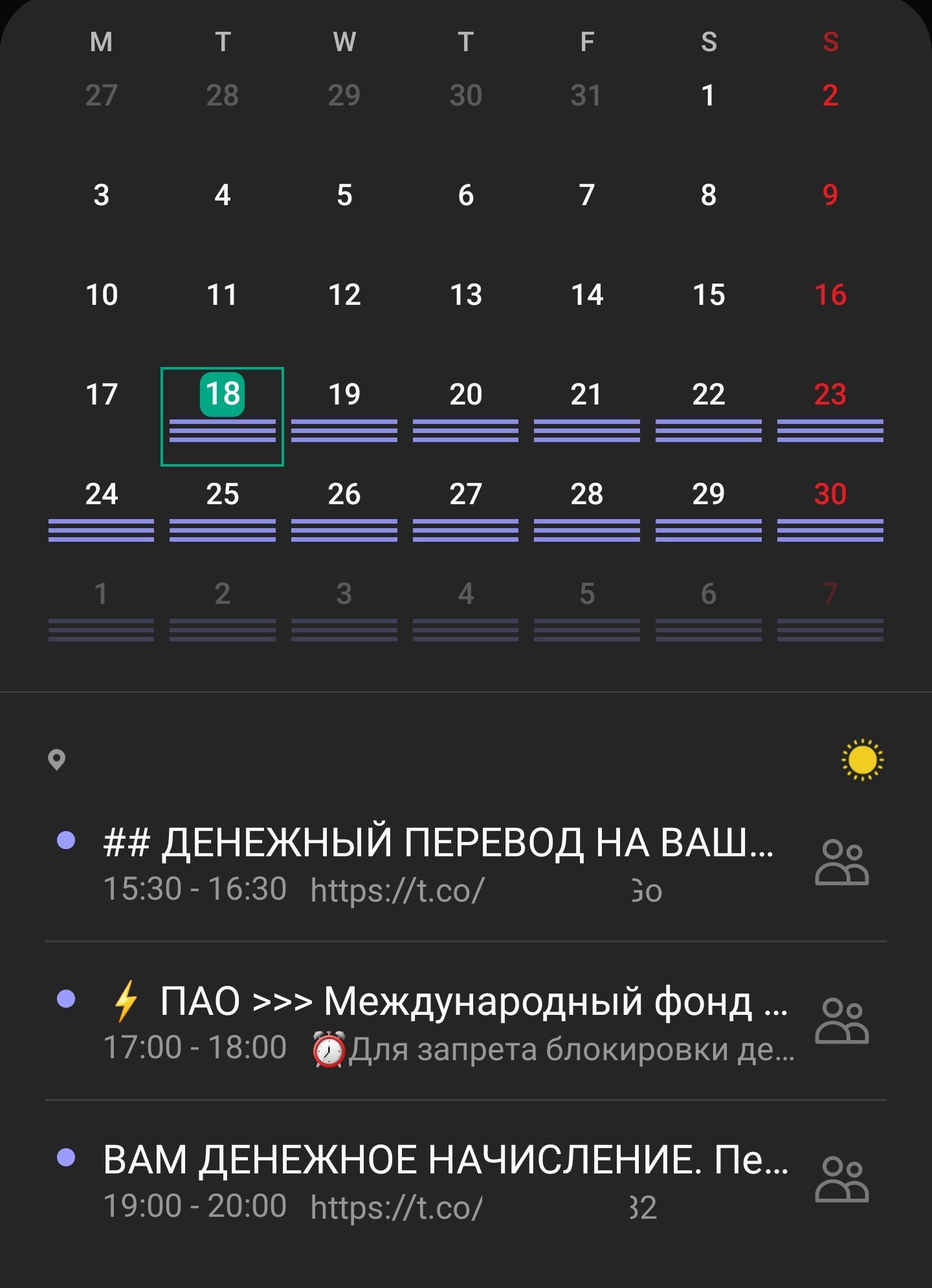
And now this is a real pain, which leads to the actions of spammers, and the approach of Google, which, of course, wants to simplify the use of its services as much as possible. If spam through Forms was a little annoying because it occasionally punched Google filters (which usually does not happen in other cases), then here you get a notification on your phone with sound and it is possible that at night.
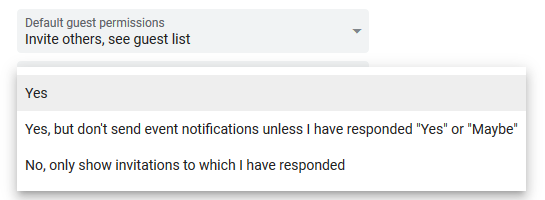
This setting solves the problem once and for all. If you select the third option “show only invitations to which there was an answer”, then the spam in the calendar and on the phone disappears (not counting those “events” that have already managed to get there - they must be deleted from the calendar manually). Interestingly, this setting is not available from a mobile phone and is present only in the desktop version. All for your convenience!

The article provides two more examples of unconventional spam through Google services: notifications from Google Photos and spam through documents on Google Drive. You can add spam through the Google messenger, which has changed over a dozen names in its history. After analyzing all these examples, we can limit ourselves to the recommendation "do not click on suspicious links and do not open suspicious files." And this is really the first thing to keep in mind when receiving spam by any means. But it's not only that.
ZDNet published last weekanother victim of a SIM swap. The attacker gained access to the author’s phone number: he called the mobile operator, provided the owner’s personal data and requested a SIM card reissue. After that, he entered the Google account, seized access to Twitter and disconnected the owner of the Internet (also provided by Google). Thus, he made it most difficult to restore access to accounts, and even tried (fortunately, unsuccessfully) to buy bitcoins from the victim's bank account for 25 thousand dollars. Two interesting points in this article: the SIM card was replaced by an outsider twice (!), And attempts to contact Google support were successful, but not immediately.
It seems that this is not directly related to spam, but in fact you can outline a common problem: in a typical scenario, access to the most important digital assets is tied to your phone number and email address. That is, what is known to many people and in most cases is easily detected by attackers. In the worst case, this leads to loss of time, money and reputation, as described in the ZDNet article and in many other examples. At best, this leads to a loss of time, phone calls in the middle of the night, and a mess in the mailbox. But wait, there’s nothing good in that either!
If your mailbox is used to communicate with a large number of people, especially for a business, you are unlikely to change it due to spam attacks. It can be considered an inevitable evil. Service providers (this applies not only to Google) should definitely improve the user's protection from malicious users exploiting these services. Users can be advised not to put all their eggs in one basket: for access to the most important digital resources (for some it can be a bank account, for someone it can be a Twitter account) have a separate mailing address and even a phone number that they don’t know no one. Yes, this is inconvenient! In 2004, when the GMail mail service appeared, Google gained a competitive advantage by making mail convenient (before that, making search convenient). The next leader in the digital services market will be able to become one,
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.

But there are security issues that have existed for a long time, evolve slowly and are exploited in large numbers. Less attention is paid to them in the information space: well, it’s clear that there is spam and the widespread fraud associated with it, and now what? Let's take a look at this boring topic for a change, especially since there is a reason. Recently, a detailed review was published on the Kaspersky Lab blog.spamming techniques through numerous Google services. If you're out of luck, you have come across such annoying attacks yourself. This happened with one of the authors of this digest. In this post we will supplement the overview of methods with recommendations and talk about privacy issues using spam as an example. More specifically, how access to your services is essentially limited to two sequences of letters and numbers that everyone knows.
Let's start with the "captain" statement: access to any service in your Google account is possible at your email address. It’s convenient for you as a user: register your mail and immediately receive a messenger, a place to store photos and other files, a calendar and contact manager, and much more. This design is doubly convenient for spammers, and for some time spam has begun to take on new forms. This is now not only sending unsolicited messages to your inbox. With access to the metadata of millions of accounts, Google fights traditional spam quite well, and in the mid-2000s this was a major advantage at the time of the new GMail email service.

Such messages will appear in the Spam folder with a probability close to 100%. Therefore, spammers began to exploit other Google services: by performing an action on this service, you can cause a message to be sent to the victim using the company's own servers. So spam appeared through Google forms.

That is: a form is created, it is filled out, your address is indicated, a notification is sent to you (thanks for filling out the form “You received a lot of money, get them soon”). By manipulating the names of the form and individual fields, you can create a message pleasing to the criminal, with reference to fraud with questionnaires, with some inoperative financial schemes, with inflated crypto exchanges. Today we will not investigate what exactly spammers are trying to get from you, this is not important in the context of this story. Such spam can be both mass and targeted.
It should be noted that, according to the subjective impressions of the author of these lines, the peak of spam via Google forms was a year or two ago, now there are almost no such messages. But any third-party services are operated, in the logic of which there is sending e-mail to the user. As a result, your e-mail accounts are registered in online stores, trying to insert a spam link in the "username" field, attack web forms with the "fill and get message" mechanics, and operate technical support systems. This also affects the business, as a rule, a small one that has only basic tools for working with users on the site. However, back to Google. Apparently, it was possible to limit or eliminate spam through Forms, but right now another hole in the logic is being actively exploited: spam via Calendar.

What do we see here? Someone creates an event and sends an invitation to random users on the network, including you. Actually, “spam content” is the name of the event, but it is interesting here that the event is not a one-time event, but a daily one. Wait, but GMail has correctly identified this message as spam - is that all right? And here it is: with the default calendar settings, all invitations are automatically added to your schedule, regardless of the status in the mail.

And now this is a real pain, which leads to the actions of spammers, and the approach of Google, which, of course, wants to simplify the use of its services as much as possible. If spam through Forms was a little annoying because it occasionally punched Google filters (which usually does not happen in other cases), then here you get a notification on your phone with sound and it is possible that at night.

This setting solves the problem once and for all. If you select the third option “show only invitations to which there was an answer”, then the spam in the calendar and on the phone disappears (not counting those “events” that have already managed to get there - they must be deleted from the calendar manually). Interestingly, this setting is not available from a mobile phone and is present only in the desktop version. All for your convenience!

The article provides two more examples of unconventional spam through Google services: notifications from Google Photos and spam through documents on Google Drive. You can add spam through the Google messenger, which has changed over a dozen names in its history. After analyzing all these examples, we can limit ourselves to the recommendation "do not click on suspicious links and do not open suspicious files." And this is really the first thing to keep in mind when receiving spam by any means. But it's not only that.
ZDNet published last weekanother victim of a SIM swap. The attacker gained access to the author’s phone number: he called the mobile operator, provided the owner’s personal data and requested a SIM card reissue. After that, he entered the Google account, seized access to Twitter and disconnected the owner of the Internet (also provided by Google). Thus, he made it most difficult to restore access to accounts, and even tried (fortunately, unsuccessfully) to buy bitcoins from the victim's bank account for 25 thousand dollars. Two interesting points in this article: the SIM card was replaced by an outsider twice (!), And attempts to contact Google support were successful, but not immediately.
It seems that this is not directly related to spam, but in fact you can outline a common problem: in a typical scenario, access to the most important digital assets is tied to your phone number and email address. That is, what is known to many people and in most cases is easily detected by attackers. In the worst case, this leads to loss of time, money and reputation, as described in the ZDNet article and in many other examples. At best, this leads to a loss of time, phone calls in the middle of the night, and a mess in the mailbox. But wait, there’s nothing good in that either!
If your mailbox is used to communicate with a large number of people, especially for a business, you are unlikely to change it due to spam attacks. It can be considered an inevitable evil. Service providers (this applies not only to Google) should definitely improve the user's protection from malicious users exploiting these services. Users can be advised not to put all their eggs in one basket: for access to the most important digital resources (for some it can be a bank account, for someone it can be a Twitter account) have a separate mailing address and even a phone number that they don’t know no one. Yes, this is inconvenient! In 2004, when the GMail mail service appeared, Google gained a competitive advantage by making mail convenient (before that, making search convenient). The next leader in the digital services market will be able to become one,
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
