How to create an OS certified according to class I protection
A first-hand account of how it is created, and then prepared for certification for working with data under the heading of "special importance" protected OS Astra Linux.


Astra is a domestic Linux distribution that combines components from the community distributed under open licenses such as GPL, MPL, Xiph License, etc., and proprietary software of the same group of companies. The user functionality is mostly closed by components from open source software - standard Linux mechanisms are used to perform basic tasks, such as launching applications, virtualization, hardware support, or Steam. Components of our own development basically solve two key tasks: ensuring security, as well as the interaction of the graphical interface of the operating system and humans.
From the point of view of licensing, the distribution is a complex object (concept from part 4 of the Civil Code of the Russian Federation), i.e. composite work, so its distribution as a whole has some limitations. Although all the components of open source software included in the product retain their free status. Versions of Astra Linux exist for a wide variety of platforms. Moreover, the name of the platform is “hidden” in the first digit of the version number:
It would seem that an unusual solution is to take the platform type to the first position, having received a strange sequence of versions - 1.6, 2.12.13, 8.1, etc. But this was done deliberately in order to simplify the life of technical support, since visually the graphical interface of the operating system looks the same on any hardware platform, regardless of the target area of application of the computer: from the server to the smartphone. So in a conversation with the user, you can quickly understand what kind of platform in question.
By the way, the version for each platform has its own code name in honor of one of the hero cities of Russia. There are no guidelines here, we rely on a sense of beauty.
Among the developed versions of Astra there are as usualdistributions, as well as protected ones (Special Edition), oriented to work with confidential data, certified according to the information security requirements of all certification systems in Russia. From the point of view of the user set of functions, the versions are almost the same. However, the protection system in them is built in different ways. Some components of the special version required to work with confidential data, although they are not necessarily redundant for ordinary users and businesses, are not included in the regular version, because The regulatory and legal framework of the Russian Federation requires their mandatory certification.
The regular version of Astra Linux is aimed at corporate customers. For home users, when used for non-commercial purposes, the license is free - but in development we strive to satisfy the needs of the corporate segment. In the end, we are also a commercial company, and the segment of home users is very difficult. There are various Linux distributions for them, including free ones.
The regular version of Astra Linux uses a discretionary access control model - users decide for themselves whom they can grant access rights to their files. Third-party programs (browsers, office suites, etc.) run in exactly the same way as in other Linux distributions.
Like any other software, the regular version of Astra Linux can be downloaded or purchased (for organizations) electronically without any physical media. By the way, this version is also posted on the resource of the international Linux community, where there is a good external channel.
Following global trends, the version is actively developing in the direction of supporting new equipment and technologies.
In addition to regular versions, Astra Linux has so-called special versions - Special Edition, which are developed with the expectation of certification by the FSTEC of Russia and other certification systems. From the point of view of user functionality, the special version is practically no different from the usual one. However, it implements additional components to increase security (just self-written), in particular:
Of course, this is not a complete list. There are tons of other modules and components. All these tools work independently of each other, providing a sort of separation of the security system. All of the listed security functions are implemented on the basis of original domestic developments in the field of computer security without the use of SELinux developed by the NSA.
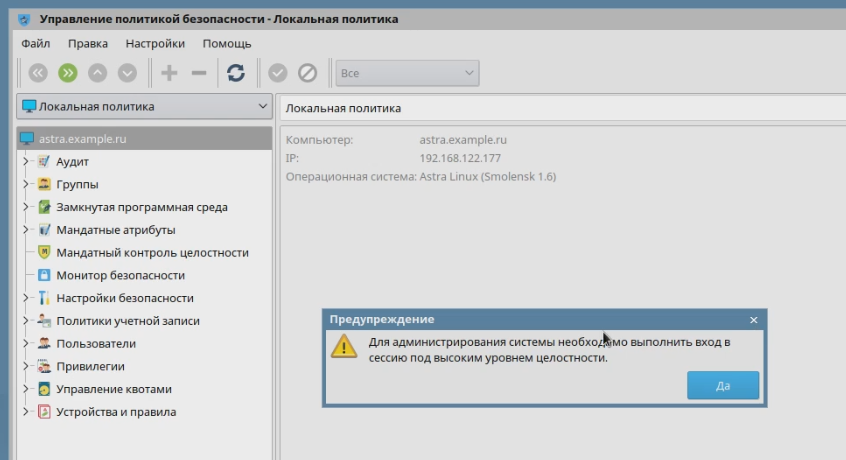
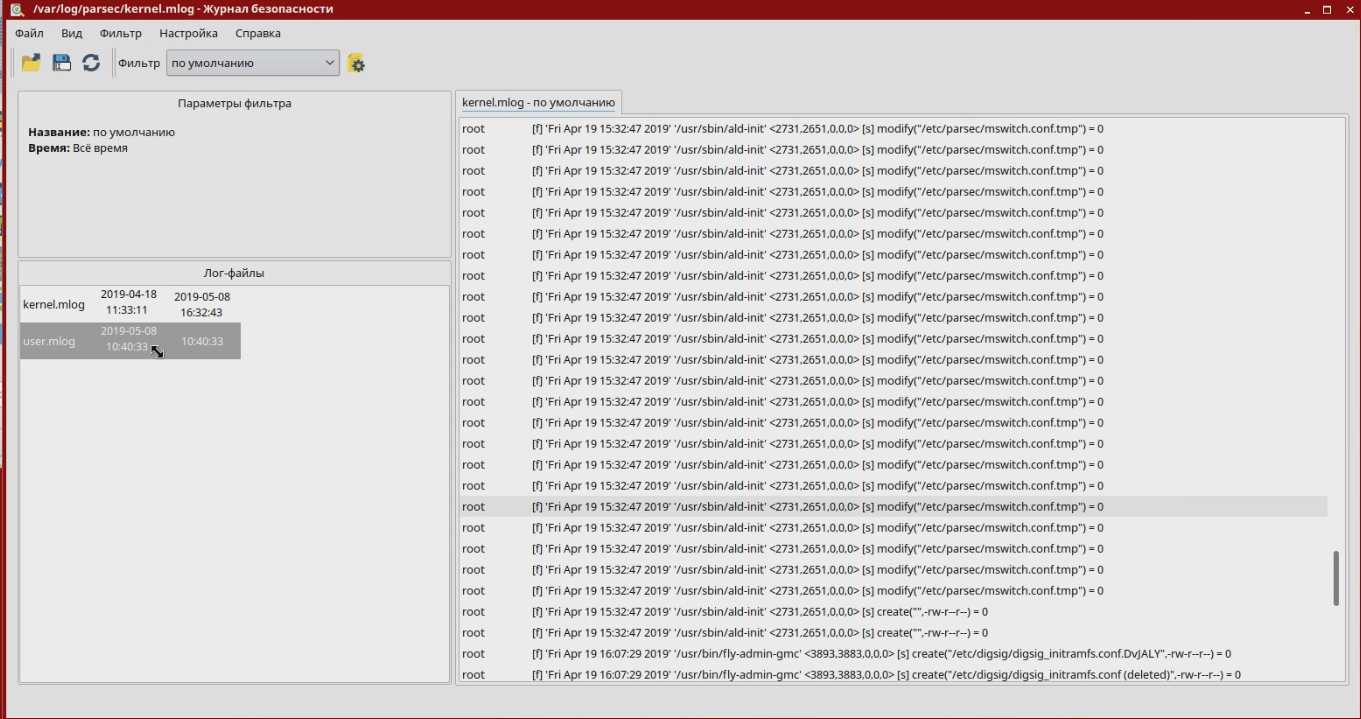
At the same time, they are turned on and off independently of each other (by the system administrator). For some components, there are different operating modes. For example, for the EDS verification tool, you can enable the training mode when files with the wrong EDS (or which do not have it) are still launched, but a warning is issued at the system level. All these mechanisms are configured by the administrator according to the security policy defined by the management. At the same time, almost all the configuration is already carried out as in graphic mode. Of course, administrators have access to the entire console-based toolset to automate the tasks of setting up and configuring security subsystems. The current version of Astra Linux Special Edition is Smolensk 1.6.
A special version is developing, like the regular one, but innovations get into it only after testing and running in a regular release.
Each security officer and system administrator in their own way prioritize information security issues. Ask them to create a project for protecting a certain IT infrastructure, and each one will offer his own solution, because he will see some of his threats and accents. When it comes to commercial companies, the decision about whose opinion to listen to is made by the business at your own risk.
At the state level, any risk must be minimized, therefore, we need general mechanisms for assessing the effectiveness of protection, or rather, confirming that information systems can resist a certain set of threats. To do this, certain security functions must be implemented in systems (for example, password verification, access control functions, etc.), and on the other hand, the development process and the code of this system itself must meet certain trust requirements. The task of the certification system and the certification body is to check a specific product for compliance with all functional conditions and trust requirements.
Depending on the functionality of information systems, various departments are involved in issues of their certification for the possibility of using them in work with important data. For example, FSTEC of Russia is engaged in certification of information security tools. However, the FSB and the Ministry of Defense also have their own certification systems for protective equipment. By the way, Astra Linux Special Edition is the only OS that has all the certificates in our country.

With regard to restricted access data processing systems, the nature of this data plays an important role - this is information for free distribution, personal data, valuable medical information, state secret, including information of special importance. It is logical that for each degree of secrecy there is a list of functional requirements and criteria for assessing the "power of attorney" of the code of information systems - its own protection class, which includes the level of trust. The list of requirements for each subsequent level includes a list for the previous level, as well as some additional conditions. A similar practice exists in many countries. At the same time, each insists on some of its own criteria and even in its own way shares the data by levels. Six classes are accepted in Russia, with the sixth being the lowest, and the first the highest.
The lower grades - from the sixth to the fourth - are requirements for the protection of personal data, as well as commercial and official secrets. In the Russian market, products corresponding to these classes are no longer rare. We’ll talk about certification for the upper classes - from third to first - with the stamps "secret", "top secret" and "of special importance" (living examples - drawings of the new Sukhoi fighter or general data on the state of critical infrastructure in the country, not so long ago equated to state secret). And here the most difficult part is not even functional requirements (in the end, to develop something is not a problem), but to confirm trust in the OS. This requires a correct mathematical model of data access control and justification of the correspondence of a real software product to this mathematical model. Those. system development procedure
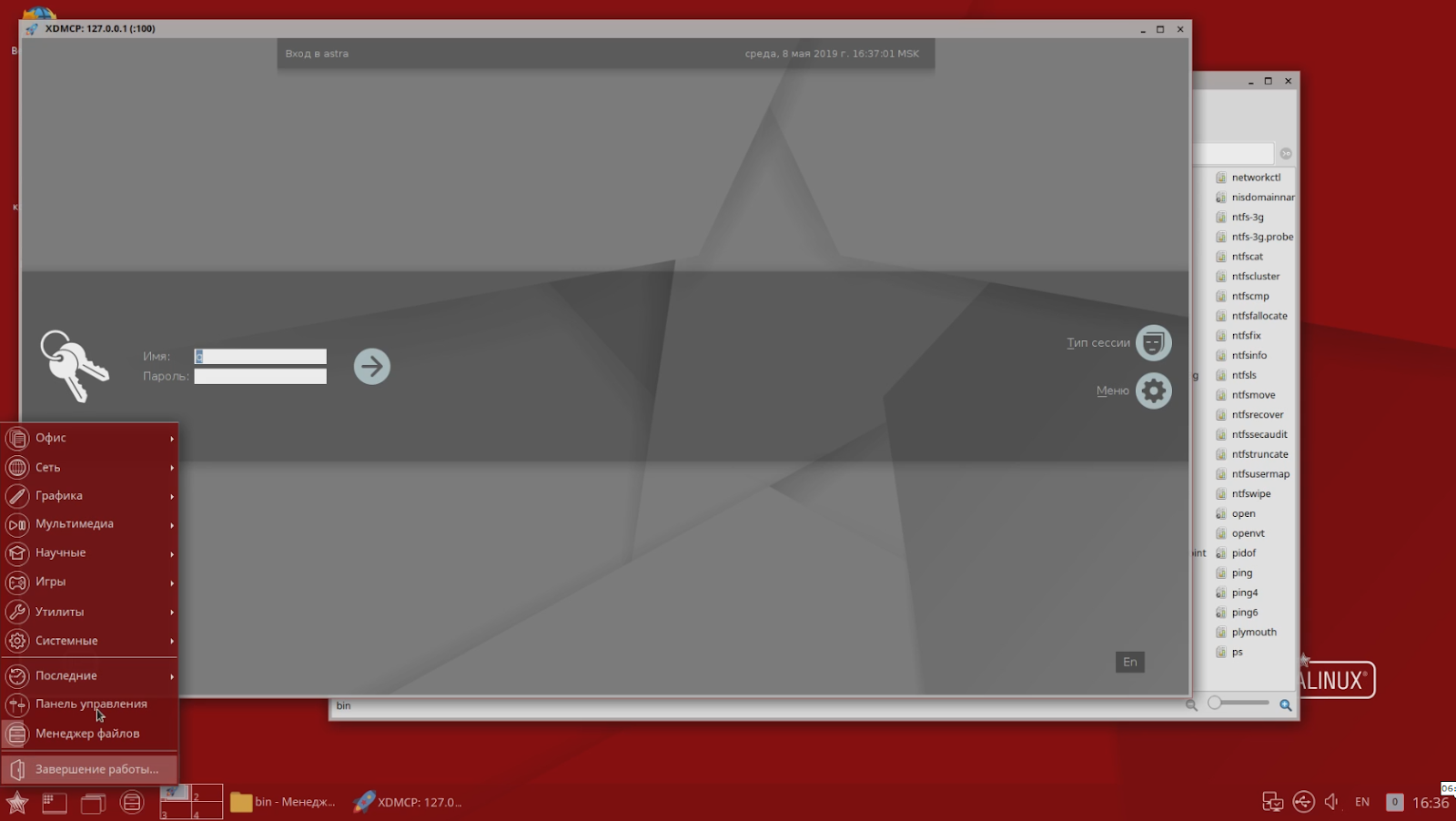
Here is an example of the system’s reaction to the inclusion of the MLS (multi level security) policy in SELinux in the Fedora distribution:
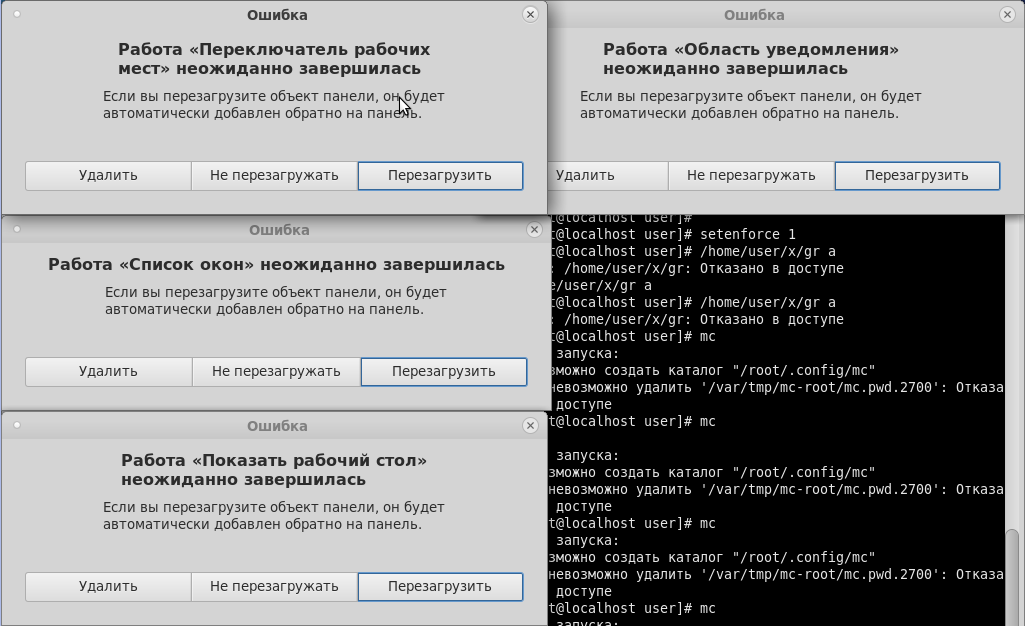
As we can see, neither the graphical shell nor console applications can correctly handle the situation when the policy for working with several security levels is enabled in the system. Accordingly, all this is necessary either to recycle or to do your own, which is done in Astra Linux.
By the way, certification does not limit the freedom of system administrators in terms of enhanced protection. Passing certification reflects the satisfaction of minimum requirements, however, each company, government agency and even each individual security guard can improve the system as they see fit. Certification only confirms the “necessary minimum” of the availability of information security functionality and the correctness of its work, as well as the vendor’s commitment to maintain this functionality throughout the entire life cycle, for example:
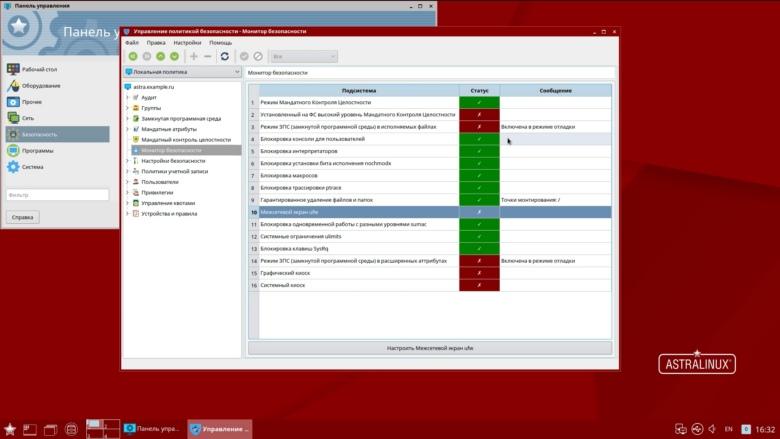
The certification procedure in practice is quite lengthy. However, the mentioned release was certified for only six months, which is fast enough, since this is the sixth version that has been tested. The previous five releases (and this is about ten years of development) Astra Linux went to get certificates up to the second class, and without these developments it would not be possible to debug all protection mechanisms, adapt the code for verification, pass the necessary checks and “swipe” at first grade.
It should be noted that at present, certification is not a product freeze, but the mandatory prompt elimination of identified vulnerabilities in a certified solution.
The most important thing that has happened over the past six months is that the Astra Linux Special Edition has gone through a multi-level procedure for checking and analyzing program code. However, different parts of the product were tested differently.
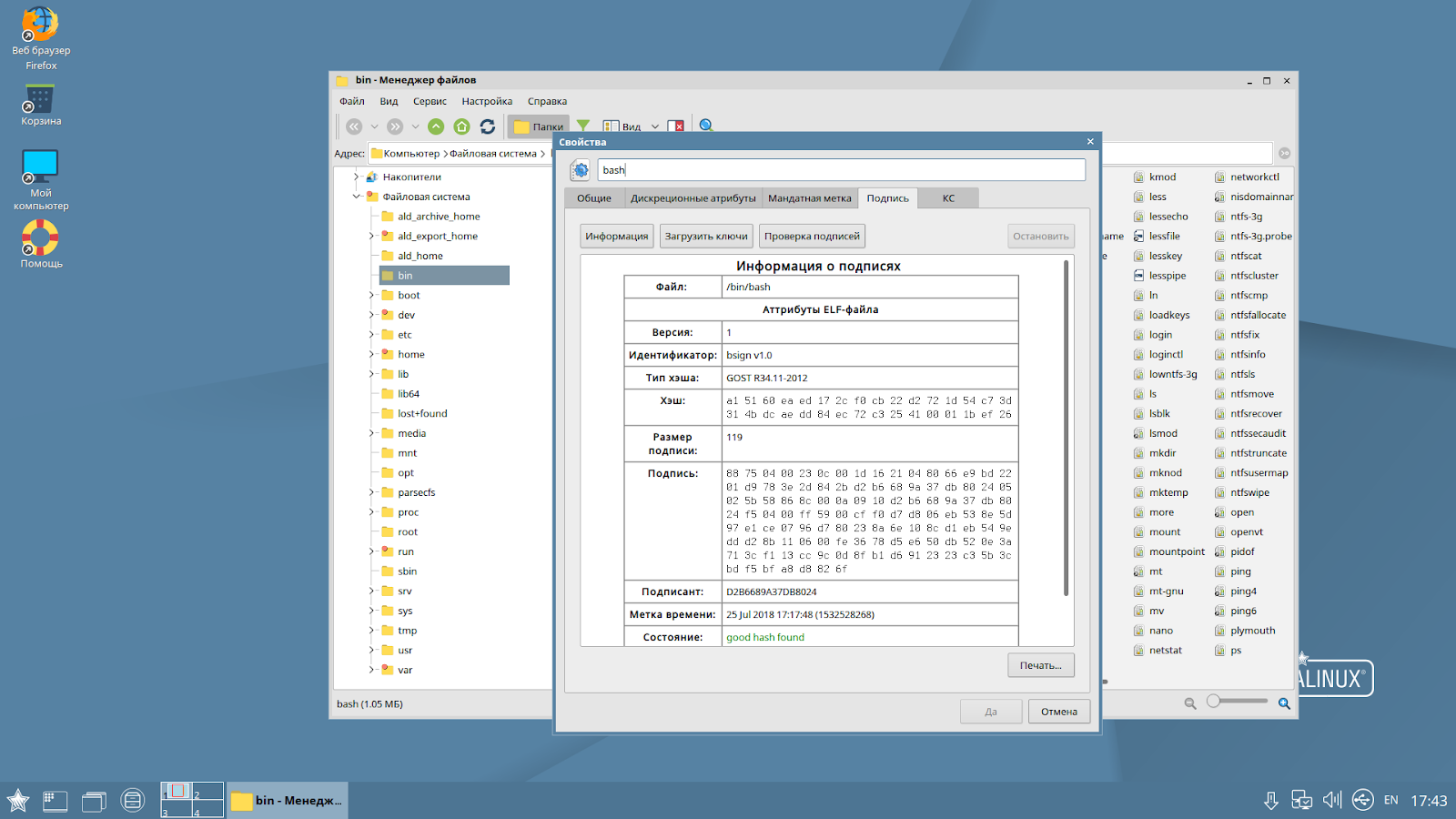
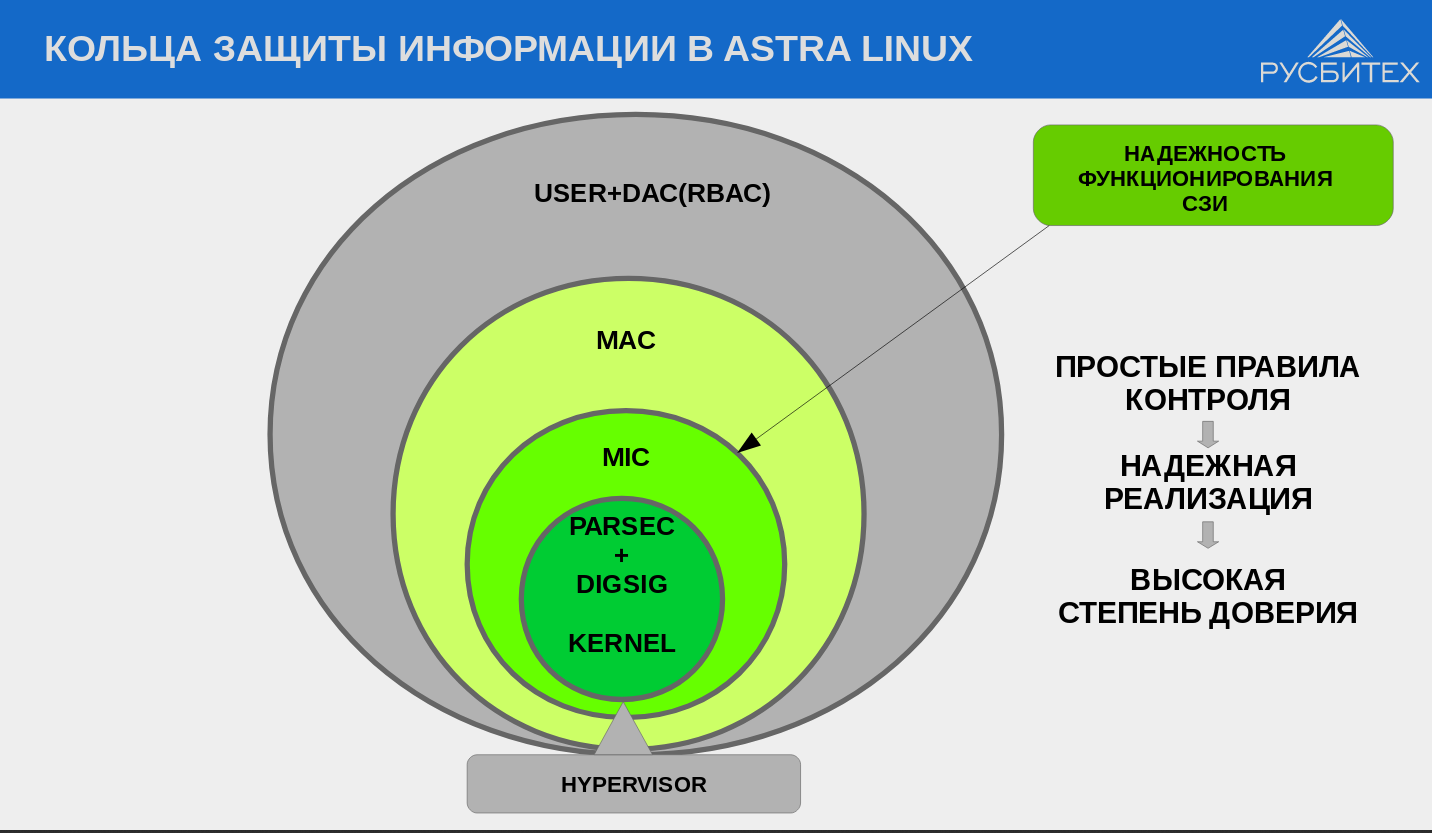
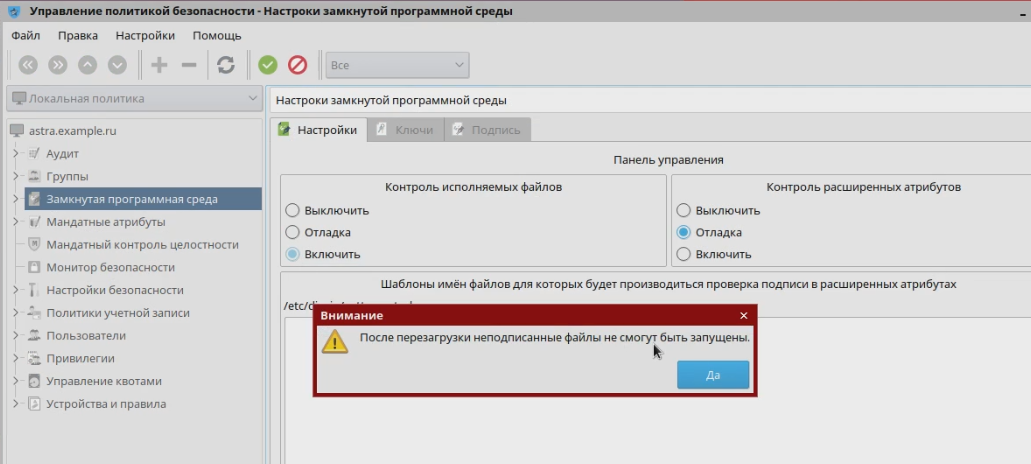
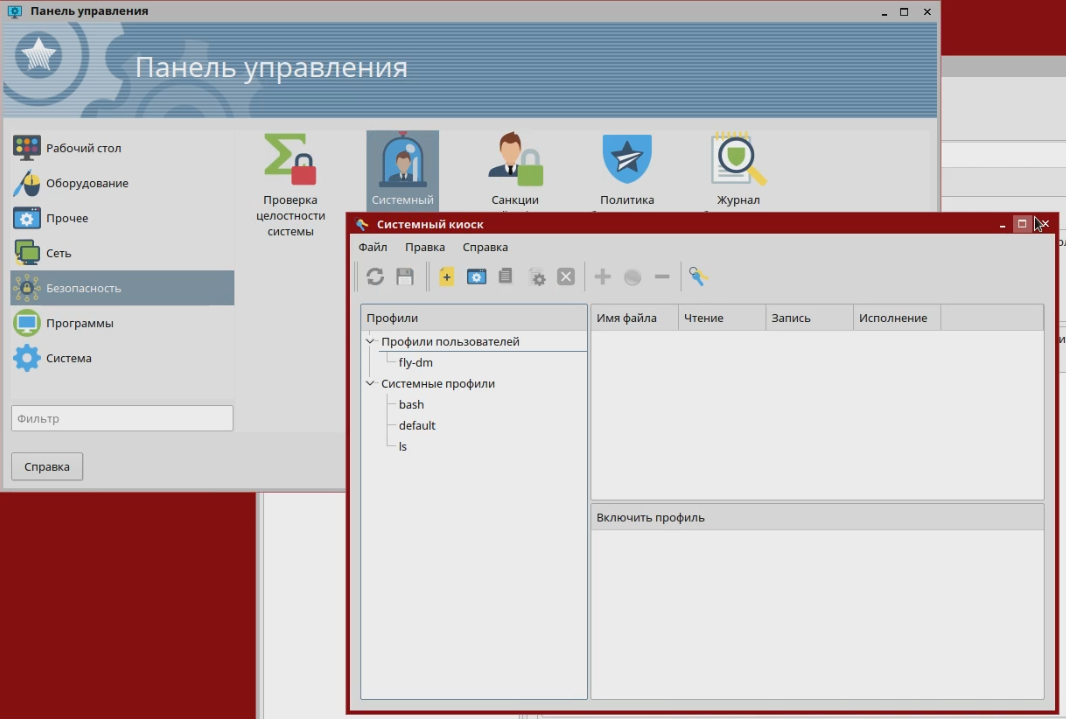
The most serious security system was tested. In addition to the standard discretionary one, it uses a mandated role-based model of access control and integrity control, which supports the degree of information security existing in Russia - “secret”, “top secret”, etc. According to this model, each user account, process, file or directory is assigned a privacy label by which access rights are determined. For example, files created by a top secret tank production department are not available to other departments with a secret level or lower. In addition, an integrity label is assigned to all user accounts, processes, files or directories, as a result, for example, user low-integrity processes cannot modify system high-integrity files.
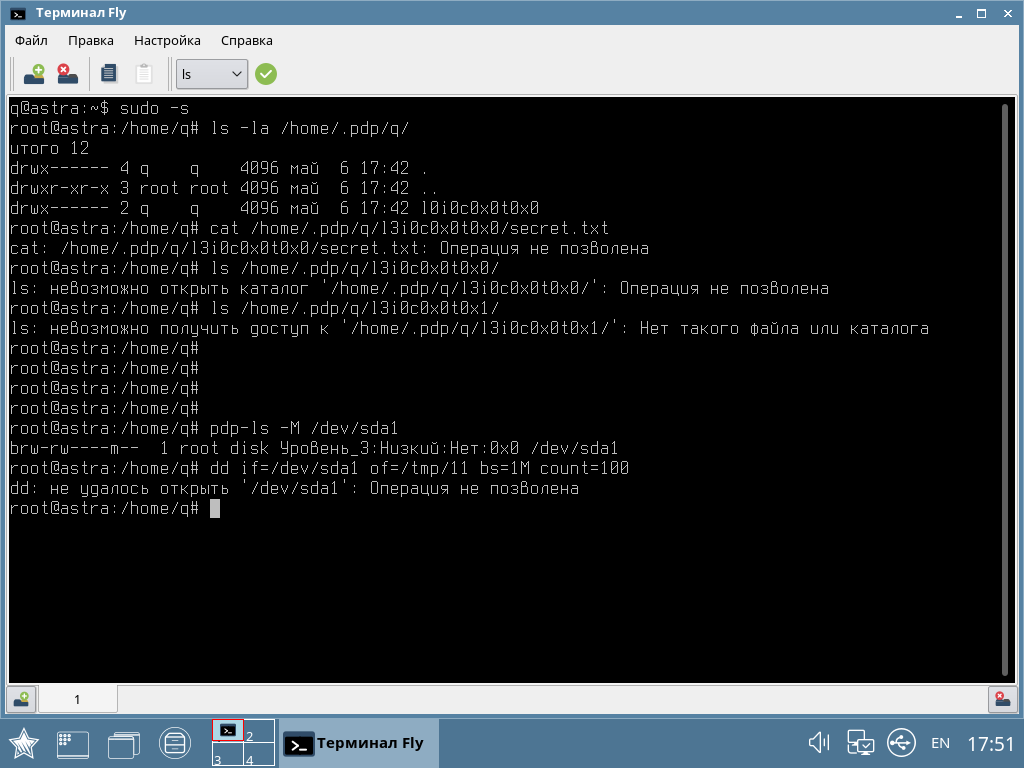
In the screenshot, an example of how a low-integrity user received superuser rights, but cannot copy data at the same time.
To justify the security of such access provision, a mathematical model was built, which was tested for logical integrity, isolation and correctness.
Further, the source code of the security system was checked for compliance with the declared mathematical model. And this is a rather complicated and laborious procedure, which was carried out jointly with the staff of the Institute for System Programming of the Russian Academy of Sciences.
It is worth noting that now in Russia we can solve similar problems of checking the code for compliance with the mathematical model for components with a total complexity of up to 10 thousand lines. And the Astra Linux security system is well within these limits. But the Linux kernel is tens of millions of lines of code, and there are currently no tools for rigorous mathematical verification of a project of this size not only in the company, but in the country as a whole. So other control mechanisms are used for them - with the help of static and dynamic code analysis tools from the same Institute for System Programming of the Russian Academy of Sciences or own development. The objective of this step is to check the code for errors, bookmarks or backdoors. Passing this check provides a high level of trust in the code and, accordingly,
Certification determines not only how Astra Linux code looks, but also how the product (or rather its special version) is delivered to the user - it is distributed only on disks. This is due both to the limitations of regulatory documents: to confirm that the program code has not been changed, as well as to the real tasks of long-term storage of the original medium. Technically, it can be a flash drive, but they tend to break, while storage on an optical disk is more predictable (and there is a guarantee against rewriting).
At the moment, no one can boast of certification for such a high class of protection.
But even assuming that tomorrow there will be a competitor with a version of the OS that hypothetically could meet the conditions of certification, in the near future it will not be able to squeeze Astra Linux. The barrier will be the very certification procedure, or rather its part relating to verification of program code. According to our estimates, only the Institute for System Programming of the Russian Academy of Sciences and Astra Linux have the resources and scientific knowledge for this procedure in Russia.
If we evaluate the scientific and technical potential of companies, then theoretically certification in Russia could pass Microsoft products. The company has the necessary resources and competencies, they even talk about the importance of the task of code verification on YouTube. However, they are unlikely to decide to open the source. And even more so, they will not finalize their security model for Russian requirements (I recall that in the USA there is a different list of requirements for state certification).
Perhaps Google and Kaspersky Lab could have taken the same path with their protected Kaspersky OS project. However, we have no information on their account. “Basalt” company tried to get certification in the second class. But it is not yet clear to us whether they have technical and scientific potential.
In fact, Astra Linux has many clients, because the system was introduced before certification. And the potential market is quite large - these are the bodies of military and state administration working with any information of limited access. In the absence of a certified operating system, these organizations created their own information systems - compiled existing solutions, finalized them as part of individual projects in order to pass certification for working with data requiring protection. However, such solutions are expensive and far from always optimal. Suppose there is no system that allows one to differentiate access to three levels of secret data within a single workplace, which means that you can use three different computers and issue keys for them in a journal (i.e., you can solve the problem by administrative means, though not the easiest and most convenient). This does not correspond to the current level of IT development. And the development of such systems requires considerable time, because here we need an individual threat model (relevant for this particular system), additional protection components, and the certification procedure itself.
The serial product - in this case, the Astra Linux Special Edition - is cheaper, more logical, more modern, although it requires administrators to go through the training phase. Otherwise, it will be difficult to configure a security system that has no analogues in the software for a wide range of users.
Astra Linux is suitable for implementation even at the highest levels of management. For example, the Presidential Administration plans to switch to this product. The plans for switching to Astra Linux were included for a long time, but at that time the system could not be implemented, because did not have integration with the necessary components. The OS does not exist by itself, but is embedded in a certain ecosystem of software products - antiviruses, communication channel protection systems, etc. Since then, a new version of Astra Linux has been released, under which certification of the necessary solutions, for example, Kaspersky Anti-Virus 10th version, has already begun. And work with manufacturers of other software products and security systems continues.

What is Astra Linux?

Astra is a domestic Linux distribution that combines components from the community distributed under open licenses such as GPL, MPL, Xiph License, etc., and proprietary software of the same group of companies. The user functionality is mostly closed by components from open source software - standard Linux mechanisms are used to perform basic tasks, such as launching applications, virtualization, hardware support, or Steam. Components of our own development basically solve two key tasks: ensuring security, as well as the interaction of the graphical interface of the operating system and humans.
From the point of view of licensing, the distribution is a complex object (concept from part 4 of the Civil Code of the Russian Federation), i.e. composite work, so its distribution as a whole has some limitations. Although all the components of open source software included in the product retain their free status. Versions of Astra Linux exist for a wide variety of platforms. Moreover, the name of the platform is “hidden” in the first digit of the version number:





- 1 and 2 - Intel (versions Smolensk and Oryol);
- 3 - IBM System Z (Murmansk);
- 4 - ARM (Novorossiysk)
- 6 - MIPS processors (Sevastopol);
- 8 - Elbrus (Leningrad).
It would seem that an unusual solution is to take the platform type to the first position, having received a strange sequence of versions - 1.6, 2.12.13, 8.1, etc. But this was done deliberately in order to simplify the life of technical support, since visually the graphical interface of the operating system looks the same on any hardware platform, regardless of the target area of application of the computer: from the server to the smartphone. So in a conversation with the user, you can quickly understand what kind of platform in question.
By the way, the version for each platform has its own code name in honor of one of the hero cities of Russia. There are no guidelines here, we rely on a sense of beauty.
Among the developed versions of Astra there are as usualdistributions, as well as protected ones (Special Edition), oriented to work with confidential data, certified according to the information security requirements of all certification systems in Russia. From the point of view of the user set of functions, the versions are almost the same. However, the protection system in them is built in different ways. Some components of the special version required to work with confidential data, although they are not necessarily redundant for ordinary users and businesses, are not included in the regular version, because The regulatory and legal framework of the Russian Federation requires their mandatory certification.
Basic version - what and for whom
The regular version of Astra Linux is aimed at corporate customers. For home users, when used for non-commercial purposes, the license is free - but in development we strive to satisfy the needs of the corporate segment. In the end, we are also a commercial company, and the segment of home users is very difficult. There are various Linux distributions for them, including free ones.
The regular version of Astra Linux uses a discretionary access control model - users decide for themselves whom they can grant access rights to their files. Third-party programs (browsers, office suites, etc.) run in exactly the same way as in other Linux distributions.

Like any other software, the regular version of Astra Linux can be downloaded or purchased (for organizations) electronically without any physical media. By the way, this version is also posted on the resource of the international Linux community, where there is a good external channel.
Following global trends, the version is actively developing in the direction of supporting new equipment and technologies.
Special version
In addition to regular versions, Astra Linux has so-called special versions - Special Edition, which are developed with the expectation of certification by the FSTEC of Russia and other certification systems. From the point of view of user functionality, the special version is practically no different from the usual one. However, it implements additional components to increase security (just self-written), in particular:
- Mandatory model of access control (MAC) and integrity control (MIC), when all components of the system are hierarchically divided by the degree of importance for its security from the most untrusted, user (integrity level 0), to system, administrative (integrity level by default 63);
- automatic verification of the electronic digital signature of any file in the system to protect against unauthorized changes. In fact, the EDS mechanism can block not only individual files, but even scripts written in any text editor in languages like Python or Perl. When trying to start or open a file, a module that is hanging in memory on the fly checks the EDS for correctness and makes a decision about the possibility of starting. In the case of scripts, the digital signature is not placed in the script itself, but in the extended attributes of the file system. Separately, I would like to note the use of the term "digital signature" in relation to the implemented security function. Such a name is intentionally taken from the national standard GOST R 34.

- kiosk mode, at the kernel level, allowing the launch of a strictly defined set of applications;
- restriction of work with interpreted programming languages;
- restrict user access to the console;
- the ability to overwrite files on a disk with sequences of zeros and ones in several passes;
- blocking the connection of "unfamiliar" external devices, which prevents malware from entering the system through various tricks with flash drives. It's no secret that enterprise systems can be compromised by simply scattering cute flash drives with malware around the building in the hope that someone from the staff will pick it up. In our case, such a trick will not work.
Of course, this is not a complete list. There are tons of other modules and components. All these tools work independently of each other, providing a sort of separation of the security system. All of the listed security functions are implemented on the basis of original domestic developments in the field of computer security without the use of SELinux developed by the NSA.

At the same time, they are turned on and off independently of each other (by the system administrator). For some components, there are different operating modes. For example, for the EDS verification tool, you can enable the training mode when files with the wrong EDS (or which do not have it) are still launched, but a warning is issued at the system level. All these mechanisms are configured by the administrator according to the security policy defined by the management. At the same time, almost all the configuration is already carried out as in graphic mode. Of course, administrators have access to the entire console-based toolset to automate the tasks of setting up and configuring security subsystems. The current version of Astra Linux Special Edition is Smolensk 1.6.


A special version is developing, like the regular one, but innovations get into it only after testing and running in a regular release.
How we prepared a special version for certification
Each security officer and system administrator in their own way prioritize information security issues. Ask them to create a project for protecting a certain IT infrastructure, and each one will offer his own solution, because he will see some of his threats and accents. When it comes to commercial companies, the decision about whose opinion to listen to is made by the business at your own risk.
At the state level, any risk must be minimized, therefore, we need general mechanisms for assessing the effectiveness of protection, or rather, confirming that information systems can resist a certain set of threats. To do this, certain security functions must be implemented in systems (for example, password verification, access control functions, etc.), and on the other hand, the development process and the code of this system itself must meet certain trust requirements. The task of the certification system and the certification body is to check a specific product for compliance with all functional conditions and trust requirements.
Depending on the functionality of information systems, various departments are involved in issues of their certification for the possibility of using them in work with important data. For example, FSTEC of Russia is engaged in certification of information security tools. However, the FSB and the Ministry of Defense also have their own certification systems for protective equipment. By the way, Astra Linux Special Edition is the only OS that has all the certificates in our country.



Degree of secrecy
With regard to restricted access data processing systems, the nature of this data plays an important role - this is information for free distribution, personal data, valuable medical information, state secret, including information of special importance. It is logical that for each degree of secrecy there is a list of functional requirements and criteria for assessing the "power of attorney" of the code of information systems - its own protection class, which includes the level of trust. The list of requirements for each subsequent level includes a list for the previous level, as well as some additional conditions. A similar practice exists in many countries. At the same time, each insists on some of its own criteria and even in its own way shares the data by levels. Six classes are accepted in Russia, with the sixth being the lowest, and the first the highest.
The lower grades - from the sixth to the fourth - are requirements for the protection of personal data, as well as commercial and official secrets. In the Russian market, products corresponding to these classes are no longer rare. We’ll talk about certification for the upper classes - from third to first - with the stamps "secret", "top secret" and "of special importance" (living examples - drawings of the new Sukhoi fighter or general data on the state of critical infrastructure in the country, not so long ago equated to state secret). And here the most difficult part is not even functional requirements (in the end, to develop something is not a problem), but to confirm trust in the OS. This requires a correct mathematical model of data access control and justification of the correspondence of a real software product to this mathematical model. Those. system development procedure
Here is an example of the system’s reaction to the inclusion of the MLS (multi level security) policy in SELinux in the Fedora distribution:

As we can see, neither the graphical shell nor console applications can correctly handle the situation when the policy for working with several security levels is enabled in the system. Accordingly, all this is necessary either to recycle or to do your own, which is done in Astra Linux.
By the way, certification does not limit the freedom of system administrators in terms of enhanced protection. Passing certification reflects the satisfaction of minimum requirements, however, each company, government agency and even each individual security guard can improve the system as they see fit. Certification only confirms the “necessary minimum” of the availability of information security functionality and the correctness of its work, as well as the vendor’s commitment to maintain this functionality throughout the entire life cycle, for example:
- identification and authentication;
- access control;
- Security event logging
- software environment restriction;
- process isolation;
- memory protection;
- integrity control;
- ensuring reliable operation;
- network stream filtering

Certification Preparation
The certification procedure in practice is quite lengthy. However, the mentioned release was certified for only six months, which is fast enough, since this is the sixth version that has been tested. The previous five releases (and this is about ten years of development) Astra Linux went to get certificates up to the second class, and without these developments it would not be possible to debug all protection mechanisms, adapt the code for verification, pass the necessary checks and “swipe” at first grade.
It should be noted that at present, certification is not a product freeze, but the mandatory prompt elimination of identified vulnerabilities in a certified solution.
The most important thing that has happened over the past six months is that the Astra Linux Special Edition has gone through a multi-level procedure for checking and analyzing program code. However, different parts of the product were tested differently.
The most serious security system was tested. In addition to the standard discretionary one, it uses a mandated role-based model of access control and integrity control, which supports the degree of information security existing in Russia - “secret”, “top secret”, etc. According to this model, each user account, process, file or directory is assigned a privacy label by which access rights are determined. For example, files created by a top secret tank production department are not available to other departments with a secret level or lower. In addition, an integrity label is assigned to all user accounts, processes, files or directories, as a result, for example, user low-integrity processes cannot modify system high-integrity files.

In the screenshot, an example of how a low-integrity user received superuser rights, but cannot copy data at the same time.
To justify the security of such access provision, a mathematical model was built, which was tested for logical integrity, isolation and correctness.
Further, the source code of the security system was checked for compliance with the declared mathematical model. And this is a rather complicated and laborious procedure, which was carried out jointly with the staff of the Institute for System Programming of the Russian Academy of Sciences.
It is worth noting that now in Russia we can solve similar problems of checking the code for compliance with the mathematical model for components with a total complexity of up to 10 thousand lines. And the Astra Linux security system is well within these limits. But the Linux kernel is tens of millions of lines of code, and there are currently no tools for rigorous mathematical verification of a project of this size not only in the company, but in the country as a whole. So other control mechanisms are used for them - with the help of static and dynamic code analysis tools from the same Institute for System Programming of the Russian Academy of Sciences or own development. The objective of this step is to check the code for errors, bookmarks or backdoors. Passing this check provides a high level of trust in the code and, accordingly,

Certification determines not only how Astra Linux code looks, but also how the product (or rather its special version) is delivered to the user - it is distributed only on disks. This is due both to the limitations of regulatory documents: to confirm that the program code has not been changed, as well as to the real tasks of long-term storage of the original medium. Technically, it can be a flash drive, but they tend to break, while storage on an optical disk is more predictable (and there is a guarantee against rewriting).
What about competitors?
At the moment, no one can boast of certification for such a high class of protection.
But even assuming that tomorrow there will be a competitor with a version of the OS that hypothetically could meet the conditions of certification, in the near future it will not be able to squeeze Astra Linux. The barrier will be the very certification procedure, or rather its part relating to verification of program code. According to our estimates, only the Institute for System Programming of the Russian Academy of Sciences and Astra Linux have the resources and scientific knowledge for this procedure in Russia.
If we evaluate the scientific and technical potential of companies, then theoretically certification in Russia could pass Microsoft products. The company has the necessary resources and competencies, they even talk about the importance of the task of code verification on YouTube. However, they are unlikely to decide to open the source. And even more so, they will not finalize their security model for Russian requirements (I recall that in the USA there is a different list of requirements for state certification).
Perhaps Google and Kaspersky Lab could have taken the same path with their protected Kaspersky OS project. However, we have no information on their account. “Basalt” company tried to get certification in the second class. But it is not yet clear to us whether they have technical and scientific potential.
Who is using Astra?
In fact, Astra Linux has many clients, because the system was introduced before certification. And the potential market is quite large - these are the bodies of military and state administration working with any information of limited access. In the absence of a certified operating system, these organizations created their own information systems - compiled existing solutions, finalized them as part of individual projects in order to pass certification for working with data requiring protection. However, such solutions are expensive and far from always optimal. Suppose there is no system that allows one to differentiate access to three levels of secret data within a single workplace, which means that you can use three different computers and issue keys for them in a journal (i.e., you can solve the problem by administrative means, though not the easiest and most convenient). This does not correspond to the current level of IT development. And the development of such systems requires considerable time, because here we need an individual threat model (relevant for this particular system), additional protection components, and the certification procedure itself.
The serial product - in this case, the Astra Linux Special Edition - is cheaper, more logical, more modern, although it requires administrators to go through the training phase. Otherwise, it will be difficult to configure a security system that has no analogues in the software for a wide range of users.
Astra Linux is suitable for implementation even at the highest levels of management. For example, the Presidential Administration plans to switch to this product. The plans for switching to Astra Linux were included for a long time, but at that time the system could not be implemented, because did not have integration with the necessary components. The OS does not exist by itself, but is embedded in a certain ecosystem of software products - antiviruses, communication channel protection systems, etc. Since then, a new version of Astra Linux has been released, under which certification of the necessary solutions, for example, Kaspersky Anti-Virus 10th version, has already begun. And work with manufacturers of other software products and security systems continues.
