Security Week 23: Notepad vulnerability, a million systems with unpatched RDP
Notepad on Windows is an island of stability in the midst of a bacchanal of progress. An application that never fails. The functionality of Notepad has not changed much over 34 years of its existence (except that the limits on the size of opened documents have been raised), and the design of the current version is not much different from the version for Windows 3.0. The expansion of the functionality of Microsoft's large office suite has led to a host of vulnerabilities, and against this background, the minimalistic Notepad seems to be the embodiment of security.
Not anymore. Researcher Tavis Ormandy of the Google Project Zero team found a vulnerability in Notepad that could lead to arbitrary code execution. The real danger of the problem is still difficult to assess: the details are not disclosed until the release of the patch. Ormandy himself believes that the bug is serious, other experts doubt the existence of a real threat. True, their assessment is based on the only screenshot provided by Thevis, so you should still wait for the full description. But the fact itself!

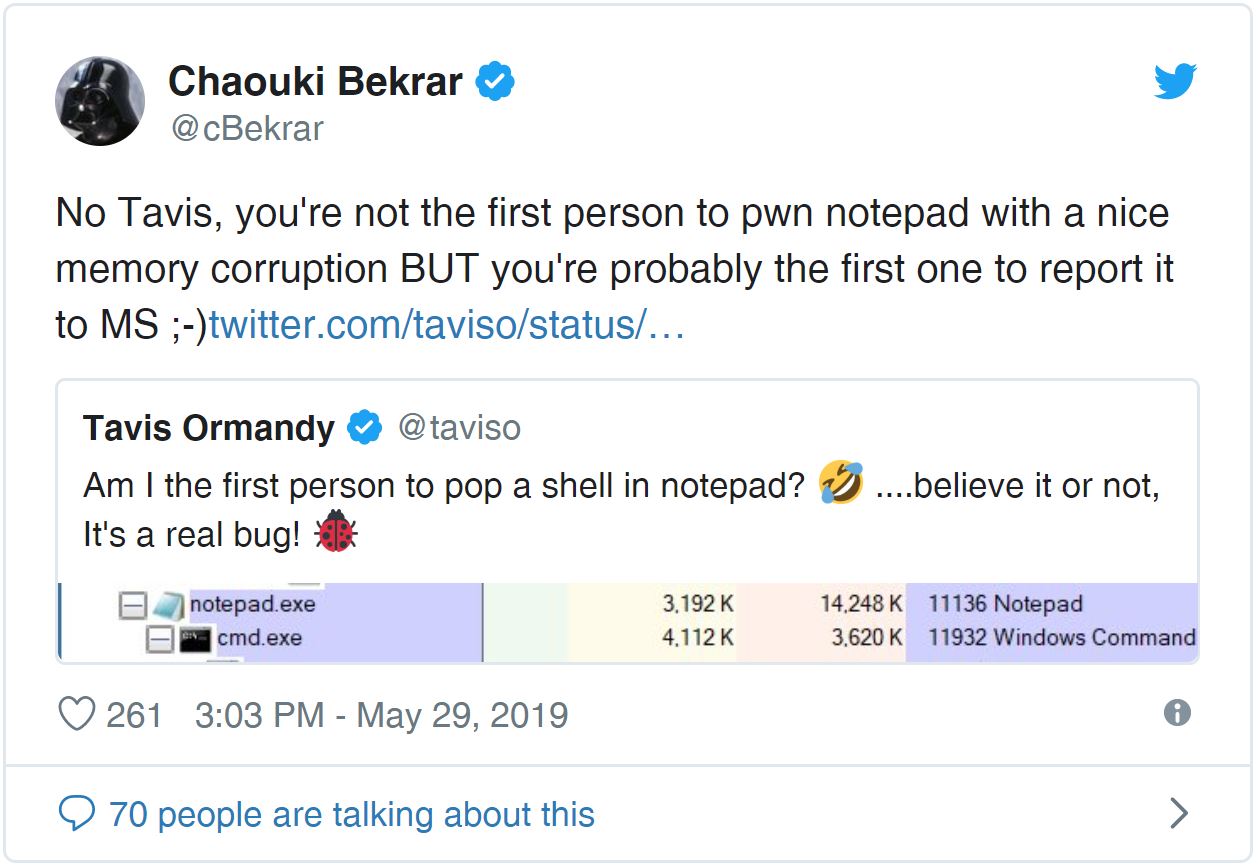
The researcher was able to implement in Notepad a scenario of memory corruption, leading to the execution of arbitrary code. It can be assumed that a real attack involves sending a prepared text file that needs to be opened using the program. What rights this code will be executed with and how the attack may develop later is not yet clear. Tavis suggested that he was the first to successfully open a console from Notepad. Chaouki Bekrar, founder of Zerodium, an exploit reselling company, claims that exploits for Notepad already exist, but no information has been published about them.
There is a chance that the bug will be fixed on June 11, when Microsoft will release the next monthly set of patches. By the way, previous patches covered a much more serious vulnerability in Remote Desktop Services, known as BlueKeep . We wrote more about it in this digest and in this news. The vulnerability allows full access to a device with Windows if three conditions are met: the ability to establish an RDP connection, the absence of a patch and the disabled Network Level Authentication .
Errata Security's Rob Gram was able to estimate the number of vulnerable systems accessible from the Internet: more than a million came out ( news , articleRob). For scanning, a samopisny utility was used, which found network nodes with an open RDP port (3389) and evaluated their properties.
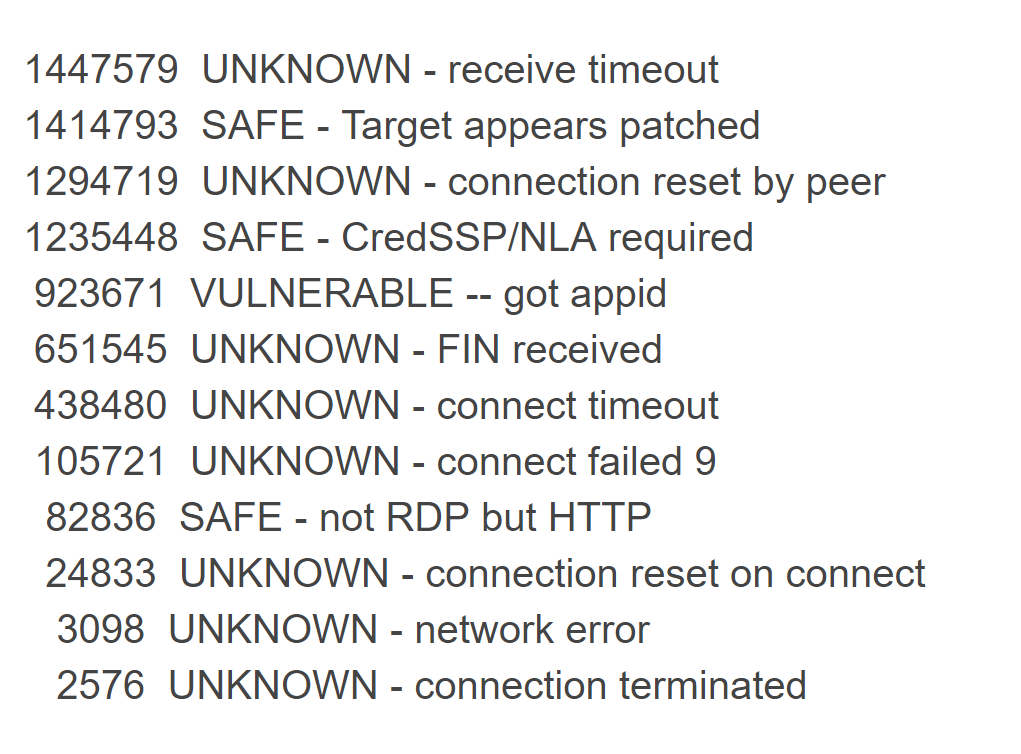
A total of 7.6 million open port systems were found. Of these, the majority (53%) either did not respond to requests, either responded using the HTTP protocol, or dropped the connection. 34% of systems are either patched or use network authentication. 16% of computers, or 1.2 million, are most likely vulnerable. Access to them can be obtained without the knowledge of the administrator, operating Bluekeep. Unfortunately, cybercriminals will certainly take advantage (if they have not already taken advantage) of such a large database of vulnerable devices. If your computer is accessible from outside for some reason, it’s definitely worthwhile either to enable NLA or update the system (patches are released for all OS up to Windows XP). It is advisable to do both, and another and once again evaluate: is it really necessary to access computers outside the secure perimeter.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.

Not anymore. Researcher Tavis Ormandy of the Google Project Zero team found a vulnerability in Notepad that could lead to arbitrary code execution. The real danger of the problem is still difficult to assess: the details are not disclosed until the release of the patch. Ormandy himself believes that the bug is serious, other experts doubt the existence of a real threat. True, their assessment is based on the only screenshot provided by Thevis, so you should still wait for the full description. But the fact itself!

The researcher was able to implement in Notepad a scenario of memory corruption, leading to the execution of arbitrary code. It can be assumed that a real attack involves sending a prepared text file that needs to be opened using the program. What rights this code will be executed with and how the attack may develop later is not yet clear. Tavis suggested that he was the first to successfully open a console from Notepad. Chaouki Bekrar, founder of Zerodium, an exploit reselling company, claims that exploits for Notepad already exist, but no information has been published about them.

There is a chance that the bug will be fixed on June 11, when Microsoft will release the next monthly set of patches. By the way, previous patches covered a much more serious vulnerability in Remote Desktop Services, known as BlueKeep . We wrote more about it in this digest and in this news. The vulnerability allows full access to a device with Windows if three conditions are met: the ability to establish an RDP connection, the absence of a patch and the disabled Network Level Authentication .
Errata Security's Rob Gram was able to estimate the number of vulnerable systems accessible from the Internet: more than a million came out ( news , articleRob). For scanning, a samopisny utility was used, which found network nodes with an open RDP port (3389) and evaluated their properties.

A total of 7.6 million open port systems were found. Of these, the majority (53%) either did not respond to requests, either responded using the HTTP protocol, or dropped the connection. 34% of systems are either patched or use network authentication. 16% of computers, or 1.2 million, are most likely vulnerable. Access to them can be obtained without the knowledge of the administrator, operating Bluekeep. Unfortunately, cybercriminals will certainly take advantage (if they have not already taken advantage) of such a large database of vulnerable devices. If your computer is accessible from outside for some reason, it’s definitely worthwhile either to enable NLA or update the system (patches are released for all OS up to Windows XP). It is advisable to do both, and another and once again evaluate: is it really necessary to access computers outside the secure perimeter.
Disclaimer: The opinions expressed in this digest may not coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
