SIEM Depths: Expertise. Whose correlation rules are better
Many of those who have come across SIEM are familiar with the development of correlation rules. Manufacturers of SIEM solutions, commercial SOC, integrators - all propose their own rules and claim that they are better than others. Is it really? How to choose a provider of rules? What is SIEM expertise? Let's think about these topics under the cut.

As always, the conclusion contains all the key points of the article.
Any specialist in information security sooner or later begins to use SIEM systems or some individual elements of systems of this class.
An important part of SIEM is the correlation rules - knowledge that allows you to solve the problem of identifying information security incidents. They can be developed by themselves, delegated to the integrator, or, if connected to a commercial SOC, use the knowledge of their specialists. As you can see, there are many sources of correlation rules in SIEM, so the question naturally arises of choice. This task is especially relevant if your company does not have dedicated specialists for SIEM tasks. In this case, you or your colleagues have to administer several security tools at once and additionally SIEM.
About a month after the implementation of SIEM, it comes to understanding that this class of solutions requires significant labor costs. The art of attacks on information systems is constantly evolving. It takes time to track modern trends, analyze them, assess the applicability to their infrastructure, and also write correlation rules to identify attacks. As a rule, specialists do not have enough time for this.
Faced with similar problems, companies decide either to build their SOC and attract dedicated specialists, or to find external suppliers of correlation rules. Next, we will discuss how to choose a supplier and whether the end customer only needs correlation rules.
By expertise we mean a set of correlation rules, expert knowledge and data that are minimally necessary for identifying and responding to incidents. Expertise is provided by the supplier (the manufacturer of the SIEM solution or SOC), and the customer is its consumer.
Correlation rules can be provided by SIEM developers, MSSP providers / SOCs, integrators and the community. Everyone postulates that their correlation rules are qualitative. True, often the concept of quality is simply replaced by the number of available rules. Is quantity an indicator of quality? In the general case, this is a controversial statement. Qualitative examination has the following properties:
Some of these properties impose requirements on the developer of the examination, and some on the result of his work - the rules of correlation and related materials.
Based on what criteria to choose a supplier? We have formulated six basic properties that characterize quality expertise. To ensure them, the rule provider must:
The set of requirements is quite wide. Unfortunately, if we devote one specialist who will spend 2 hours a day on this activity to develop correlation rules, this will not allow to achieve the same high-quality examination.
Now let's look at the correlation rules themselves through the eyes of the customer. He wants to receive quality rules from the supplier and to activate them without problems in his SIEM. In fact, not everything is so simple.
For the rules to work, you need to connect the required sources to SIEM. They must be configured to generate the necessary events for the rules. Looking at the rule itself, it is important that the logic of its work is understood from it. In addition, the customer needs to understand how to react if the rule works.
Correlation rules alone are not enough to be called expertise. Examination is the correlation rules, together with an additional environment, all of whose elements are interconnected and can be arranged in a closed circuit - the so-called closed-loop examination.
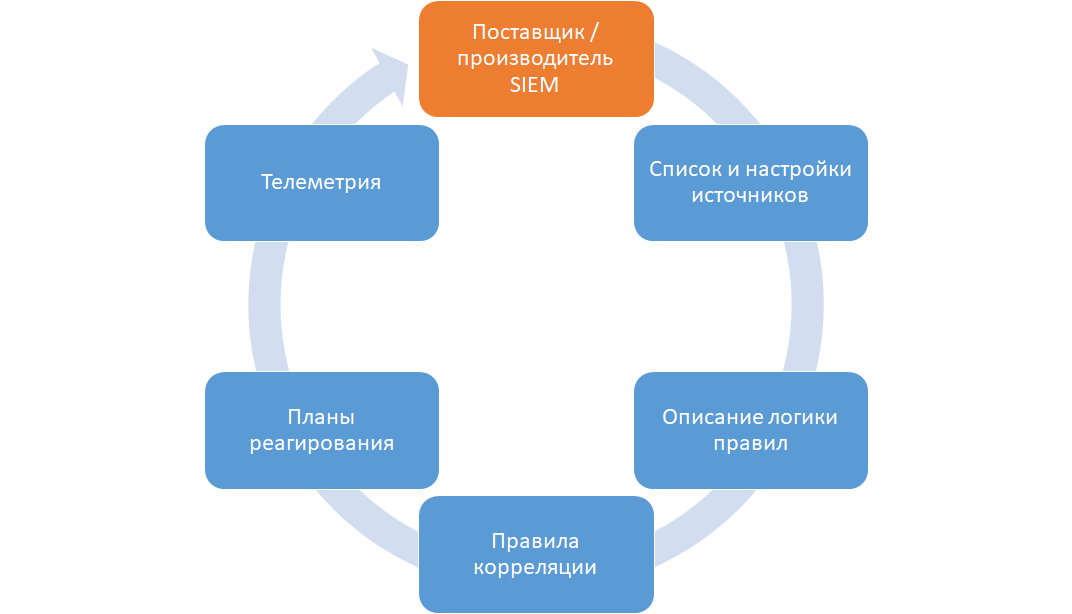
Closed loop expertise
Consider each link in this chain:
The set of requirements for the supplier, as well as all the above chain links, are collectively called expertise. As you can see, the chain is closed, therefore this approach is designated as “closed-loop expertise”.
At present, this approach is used by the main foreign leaders of the SIEM market: IBM QRadar, Micro focus ArcSight. In Russia, it is used in our company Positive Technologies in the MaxPatrol SIEM product. An interesting vendor-independent project is developing within the community - Atomic Threat Coverage , promoting a similar ideology. Next, I’ll give a description of it, taken from the project page.
Separately, I note a moment that often falls outside the field of view of customers and suppliers. Sometimes complex incidents happen that cannot be unraveled by the customer’s specialists. The supplier should not leave the customer face to face with his problem: “We deliver you the rules, they work, the rest is not our problems.” In my opinion, serious suppliers of expertise should have incident investigation services in their portfolio, which the customer can use at any time 24/7 in case of a critical situation.
To summarize:

As always, the conclusion contains all the key points of the article.
Any specialist in information security sooner or later begins to use SIEM systems or some individual elements of systems of this class.
An important part of SIEM is the correlation rules - knowledge that allows you to solve the problem of identifying information security incidents. They can be developed by themselves, delegated to the integrator, or, if connected to a commercial SOC, use the knowledge of their specialists. As you can see, there are many sources of correlation rules in SIEM, so the question naturally arises of choice. This task is especially relevant if your company does not have dedicated specialists for SIEM tasks. In this case, you or your colleagues have to administer several security tools at once and additionally SIEM.
About a month after the implementation of SIEM, it comes to understanding that this class of solutions requires significant labor costs. The art of attacks on information systems is constantly evolving. It takes time to track modern trends, analyze them, assess the applicability to their infrastructure, and also write correlation rules to identify attacks. As a rule, specialists do not have enough time for this.
Faced with similar problems, companies decide either to build their SOC and attract dedicated specialists, or to find external suppliers of correlation rules. Next, we will discuss how to choose a supplier and whether the end customer only needs correlation rules.
Examination and its properties
By expertise we mean a set of correlation rules, expert knowledge and data that are minimally necessary for identifying and responding to incidents. Expertise is provided by the supplier (the manufacturer of the SIEM solution or SOC), and the customer is its consumer.
Correlation rules can be provided by SIEM developers, MSSP providers / SOCs, integrators and the community. Everyone postulates that their correlation rules are qualitative. True, often the concept of quality is simply replaced by the number of available rules. Is quantity an indicator of quality? In the general case, this is a controversial statement. Qualitative examination has the following properties:
- Accurately identifies violations in a specific customer infrastructure.
- Identifies current world-class threats. Identifies threats specific to a specific country and industry customer.
- It has both a reactive and a proactive component.
- Explains to the customer the results of its logical conclusion.
- Provides clarification on the next steps in responding to an identified incident.
Some of these properties impose requirements on the developer of the examination, and some on the result of his work - the rules of correlation and related materials.
Developer of expertise and its competencies
Based on what criteria to choose a supplier? We have formulated six basic properties that characterize quality expertise. To ensure them, the rule provider must:
- Identify current world-class threats . These may be suppliers who have their own analytical centers specializing in detecting and analyzing attacks. They should regularly monitor the latest types of attacks and approaches to violating the information security of systems.
- Identify threats specific to a specific country and industry of the customer . In each country, the threat landscape and the list of attack types may have their own specifics. Therefore, when choosing a supplier, it is important that its analytical center has a clear focus on tracking threats inherent in exactly the country in which your company’s infrastructure is located. The center’s specialists must not only understand the specifics of threats in a particular country, but also be able to quickly respond to them. It should not be that the supplier responds to a new regional threat a week after its occurrence, only because your region is not a priority for it in terms of doing business.
- Have both a reactive and a proactive component . It is not enough to recruit Pentester analysts at the center. It is important that these experts not only understand and know how to crack systems, but also know how to detect hacking attempts and prevent them, or stop them in the early stages. Practice shows that little attention is paid to this aspect: often analytical centers are built from experts, either only in the field of attack, or only in the field of defense, which will certainly affect the level of their expertise.
- Accurately identify violations in a specific customer infrastructure . The supplier must have a methodology for developing correlation rules that can adapt to a specific customer infrastructure. This is necessary in order to minimize the number of false positives for rules. A large series of articles entitled “Correlation rules that work out of the box” was devoted to this issue . It is important to remember that the process of precisely “industrial development” of correlation rules should be built at the supplier. It follows that:
- rules should be tested on live systems, not synthetic ones;
- during the testing process, those types of attacks should be reproduced live, to the detection of which the tested correlation rule is directed;
- stress and regression tests should be performed to confirm compatibility of the rules with SIEM;
- the supplier must issue updates for previously issued rules if it turns out that the rules have a large number of false positives;
- SIEM and the supplier themselves must have channels for the prompt delivery of updates and new correlation rules to end customers.
The set of requirements is quite wide. Unfortunately, if we devote one specialist who will spend 2 hours a day on this activity to develop correlation rules, this will not allow to achieve the same high-quality examination.
Correlation rules and their environment
Now let's look at the correlation rules themselves through the eyes of the customer. He wants to receive quality rules from the supplier and to activate them without problems in his SIEM. In fact, not everything is so simple.
For the rules to work, you need to connect the required sources to SIEM. They must be configured to generate the necessary events for the rules. Looking at the rule itself, it is important that the logic of its work is understood from it. In addition, the customer needs to understand how to react if the rule works.
Correlation rules alone are not enough to be called expertise. Examination is the correlation rules, together with an additional environment, all of whose elements are interconnected and can be arranged in a closed circuit - the so-called closed-loop examination.

Closed loop expertise
Consider each link in this chain:
- Supplier / Manufacturer SIEM . The examination begins with the fact that a supplier with the relevant competencies develops correlation rules according to the technological process.
- List and source settings . The developed correlation rules are supplied with a description of those sources on the basis of which the correlation rule works. The provider also describes in detail how the source should be configured so that it provides the generation of the required event types. It will be good form if the supplier submits an instance of the events themselves.
- Description of the rule logic . In order for the customer to understand what triggering principles are laid down in the correlation rules, the supplier describes the logic of each rule in the form of flow diagrams or text descriptions.
- Correlation rules . The correlation rules themselves and the method of prioritizing the incidents generated by them are directly.
- Response plans . A correlation rule triggering can be an information security incident. It is important for the customer to understand how to respond to this incident in order to minimize its impact on the infrastructure. Also, explanations should be included in the plan which data should be additionally collected in case of an incident. Undoubtedly, the customer must adapt the response rules to the specifics of his company. However, as part of the response plans, the supplier should reflect general recommendations on the user's actions in the event of an incident caused by a specific rule. So the customer will have something to push from, adapting the overall response process for himself.
- Telemetry . Correlation rules do not work in a spherical vacuum, but in the specific conditions of the customer’s company. The supplier is responsible for the quality of the rules provided and must understand how they work. Therefore, statistics on the operation of rules should be collected in SIEM.
- Supplier / Manufacturer SIEM . The collected telemetry in anonymized form should be sent back to the supplier. Statistics helps him quickly make changes to the rules, in case of false positives. It also allows you to identify new techniques and tactics of attacks and promptly release new correlation rules for their detection.
The set of requirements for the supplier, as well as all the above chain links, are collectively called expertise. As you can see, the chain is closed, therefore this approach is designated as “closed-loop expertise”.
At present, this approach is used by the main foreign leaders of the SIEM market: IBM QRadar, Micro focus ArcSight. In Russia, it is used in our company Positive Technologies in the MaxPatrol SIEM product. An interesting vendor-independent project is developing within the community - Atomic Threat Coverage , promoting a similar ideology. Next, I’ll give a description of it, taken from the project page.
Atomic Threat Coverage allows you to automatically generate a database of analytical data designed to counter the threats described in MITER ATT & CK from the perspective of Detection, Response, Prevention and Simulation of threats. It includes:
- Detection Rules - Sigma - based Detection Rules (correlation), a general format for describing correlation rules for SIEM systems.
- Data Needed - data that must be collected to detect a specific threat.
- Logging Policies - logging settings that must be made on the device to collect the data necessary to detect a specific threat.
- Enrichments - Data Needed settings needed to implement some of the Detection Rules.
- Triggers - attack simulation scripts based on the Atomic Red Team - atomic tests / threat implementation scenarios from MITER ATT & CK.
- Response Actions - atomic incident response steps.
- Response Playbooks - incident response scenarios generated during the detection of a specific threat, based on Response Actions.
- Hardening Policies - system settings that allow you to level a specific threat.
- Mitigation Systems - systems and technologies that allow you to level a specific threat.
Separately, I note a moment that often falls outside the field of view of customers and suppliers. Sometimes complex incidents happen that cannot be unraveled by the customer’s specialists. The supplier should not leave the customer face to face with his problem: “We deliver you the rules, they work, the rest is not our problems.” In my opinion, serious suppliers of expertise should have incident investigation services in their portfolio, which the customer can use at any time 24/7 in case of a critical situation.
conclusions
To summarize:
- The customer who bought SIEM often does not have the opportunity to allocate individual specialists to work with a solution of 100% of the working time. In this case, SIEM ceases to be used after some time.
- Correlation rules alone are not enough to ensure that actual security threats are identified. In this regard, the rules of correlation alone cannot be called expertise. Examination - a set of correlation rules, expert knowledge and data that are minimally necessary for identifying and responding to incidents.
- Examination should have the following properties :
- accurately identifies violations in the specific infrastructure of the customer;
- identifies current world-class threats, as well as specific to a particular country and industry customer;
- has both a reactive and a proactive component;
- explains to the customer the results of its logical conclusion;
- Provides explanations on further steps to respond to an identified incident.
- It is not enough to supply ready-made Sigma rules to be considered an expert supplier. The supplier of expertise must satisfy a number of requirements .
- The delivered expertise consists of the following interconnected elements:
- list and settings of sources;
- rule logic descriptions;
- correlation rules;
- response plans;
- telemetry for triggering rules.
- Examination providers should have in their portfolio investigation services that the customer can use if he does not have his own competencies to analyze a complex incident.
