If you already knock on the door: how to protect information on devices
Several previous articles on our blog were devoted to the issue of the security of personal information, which is sent using instant messengers and social networks. Now it's time to talk about precautions regarding physical access to devices.
Often, the easiest way to destroy information is if it is nearby. We are talking about the destruction of data from storage devices - USB-flash drives, SSD, HDD. You can destroy the drive in a special shredder or just something heavy, but we will talk about more elegant solutions.
Various companies produce storage media that receive the self-destruct function directly from the box. A huge number of solutions.
One of the simplest and most obvious examples is the Data Killer USB stick and the like. Such a device looks no different from other flash drives, but there is a battery inside. When the button is pressed, the battery destroys the data on the chip by strong heating. After that, the flash drive is not recognized when connected, so the chip itself is also destroyed. Unfortunately, detailed studies on whether it can be restored have not been conducted.

Image source: hacker.ru
There are flash drives that do not store any information, but can destroy a computer or laptop. If you put such a "flash drive" next to your laptop, and someonemajor wants to quickly check what is written on it, then it will destroy itself and the laptop. Here is one example of such a killer .
There are interesting systems for reliable destruction of information stored on a hard disk inside a PC.
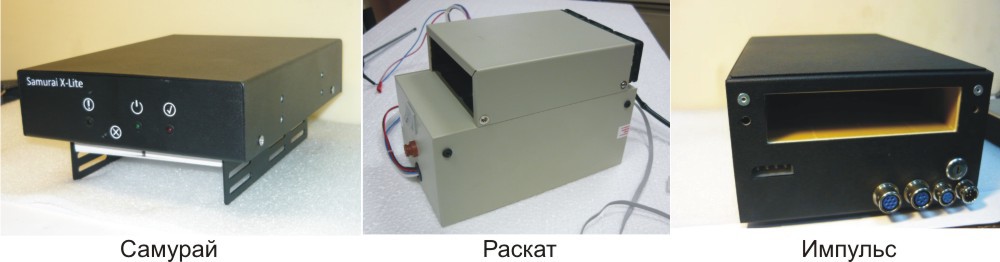
Earlier they were described on Habré, but it’s impossible not to mention them. Such systems are equipped with autonomous power (that is, turning off the electricity in the building will not help stop data destruction). There is also a timer for power outages, which will help if the computer is seized in the absence of the user. Even radio and GSM channels are available, so data destruction can be started remotely. It is destroyed by the device generating a magnetic field of 450 kA / m.
With SSD, this does not work out, and they were once offered the option of thermal destruction .

Above is a makeshift method that is unreliable and dangerous. Other types of devices are used for SSDs, for example, Impulse-SSD, which destroys a drive with a voltage of 20,000 V.
Information is erased, chips crack, the drive comes into complete disrepair. There are options with remote destruction (via GSM).
Sold and mechanical shredders HDD. In particular, LG launches such a device - it's CrushBox.

There are many options for gadgets to destroy HDD and SSD: they are produced both in the Russian Federation and abroad. We suggest discussing such devices in the comments - probably many readers can give their own example.
As with HDDs and SSDs, there are many varieties of laptop protection systems. One of the most reliable is encryption of everything and everything, and in such a way that, after several attempts to get to the information, the data is destroyed.
One of the most famous systems for protecting PCs and laptops was developed by Intel. The technology is called Anti-Theft. True, her support was discontinued several years ago, so this decision cannot be called new, but it is suitable as an example of protection. Anti-Theft made it possible to detect a stolen or lost laptop and block it. The Intel website said that the system protects confidential information, blocks access to encrypted data and prevents the OS from loading in the event of an unauthorized attempt to turn on the device.
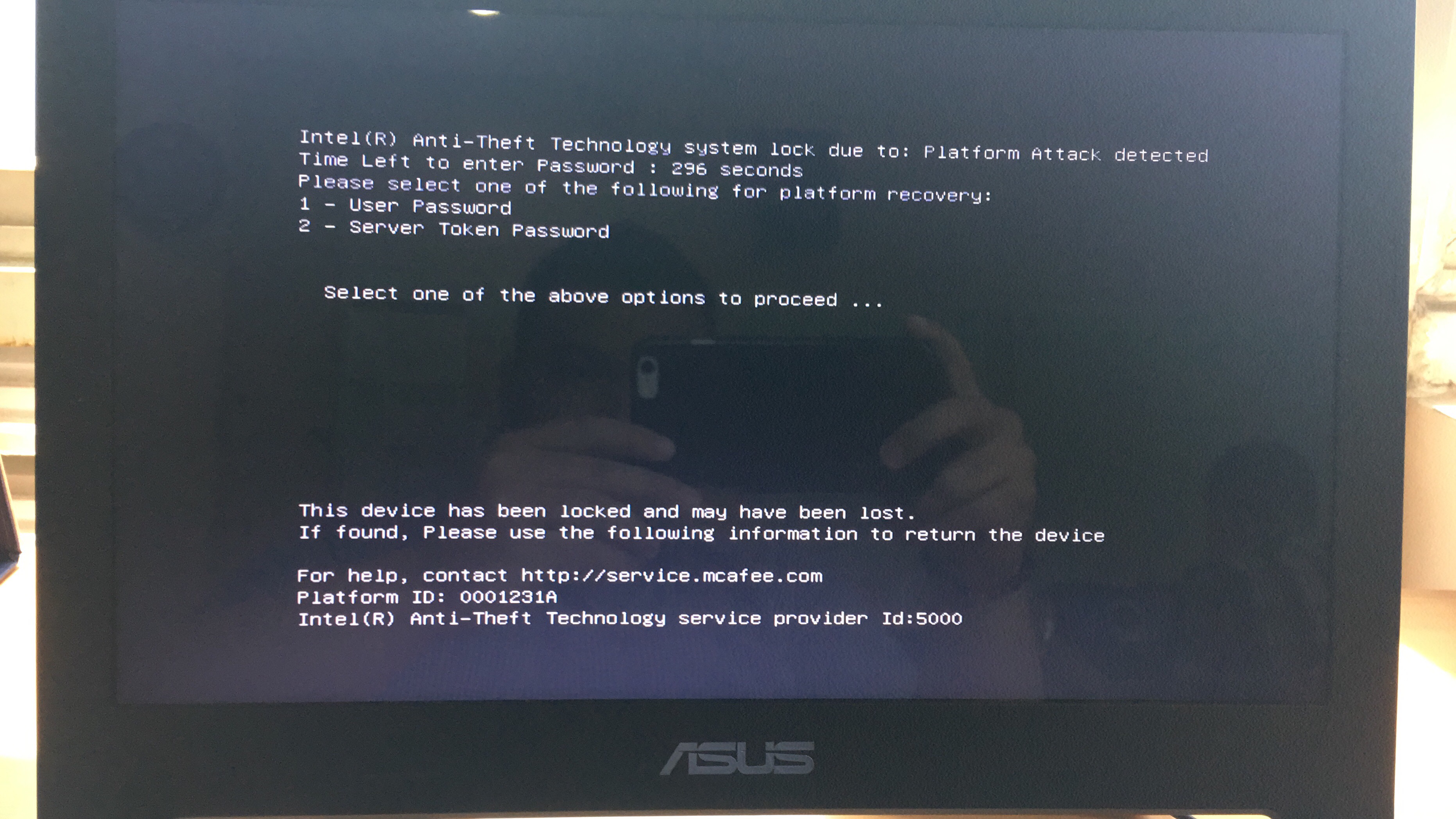
This and similar systems check the laptop for signs of third-party interference, such as too many attempts to log into the system, a crash when trying to log into a previously set server, and blocking the laptop via the Internet.
Anti-Theft blocks access to the Intel chipset chipset, as a result of which it will be impossible to enter the laptop services, launch software or OS even if the HDD or SDD is replaced or reformatted. The main cryptographic files that are needed to access the data are also deleted.
If the laptop returns to the owner, he can quickly restore its performance.
There is an option using smart cards or hardware tokens - in this case, you cannot enter the system without such devices. But in our case (if the door is already knocking), we also need to set a PIN so that when connecting a key, the PC will request an additional password. As long as this type of blocker is not connected to the system, it is almost impossible to start it.
A working option now is the USBKill script written in Python. It allows you to bring a laptop or PC unusable if suddenly some startup parameters change. It was created by the Hephaest0s developer by publishing a script on GitHub.
The only condition for USBKill to work is the need to encrypt the system drive of a laptop or PC, including tools such as Windows BitLocker, Apple FileVault, or Linux LUKS. There are several ways to activate USBKill, including connecting or disconnecting a USB flash drive.
Another option is laptops with an integrated self-destruction system. One such in 2017 received the military of the Russian Federation. To destroy data with the media, you just need to click on the button. In principle, a similar artisanal system can be done by yourself or purchased online - there are many of them.
One example is the Orwl mini-PC , which can run various OSs and self-destruct when an attack is detected. True, the price tag is inhumane - $ 1699.
On smartphones running iOS, it is possible to erase data in the event of multiple failed authorization attempts. This function is standard and is enabled in the settings.
One of our employees discovered an interesting feature of iOS devices: if you need to quickly lock the same iPhone, just press the power button five times in a row. In this case, the emergency call mode starts, and the user will not be able to access the device via Touch or FaceID - only by password code.
Android also has various standard functions for protecting personal data (encryption, multi-factor authentication for different services, graphic passwords, FRP, and so on).
Of the simple life hacks regarding blocking the phone, you can suggest using a fingerprint, for example, a ring finger or little finger. In the event that someone begins to force the user to apply a thumb to the sensor, after several attempts the phone will be locked.
True, for iPhone and Android there are software and hardware systems that allow you to bypass almost any protection. Apple has provided the ability to disable the Lightning-connector when the user is inactive for a certain time, but whether this helps from hacking the phone using these complexes is unclear.
Some manufacturers produce phones that are protected from wiretapping and hacking, but they cannot be called 100% reliable. Android creator Andy Rubin released two years agoEssential Phone , which was called by the developers "the most secure." But he never became popular. Plus, it was practically impossible to repair: if the phone broke, then you could put an end to it.
Safe phones have also been released by Sirin Labs and Silent Cirlce. The gadgets were called Solarin and Blackphone. Boeing has created Boeing Black, a device that is recommended to defense officials. This gadget has a self-destruct mode, which is activated in case of hacking.
Be that as it may, with smartphones in terms of protection against third-party interference, everything is somewhat worse than with storage media or laptops. The only thing that can be recommended is not to use a smartphone to exchange and store sensitive information.
Until now, we talked about how to quickly destroy information if someone knocks on the door and you did not wait for guests. But there are also public places - cafes, fast food restaurants, street. If someone comes up from behind and picks up a laptop, then data destruction systems will not help. And no matter how many secret buttons there are, with their hands tied they cannot be pressed.
The simplest thing is not to take gadgets with critical information to the street at all. If you take it, then do not remove the lock from the device in a crowded place unless absolutely necessary. Just at that moment, being in the crowd, the gadget can be easily intercepted.
The more devices, the easier it is to intercept at least something. Therefore, instead of the “smartphone + laptop + tablet” bundle, you should use only a netbook, for example, with Linux on board. You can call using it, and information on one gadget is easier to protect than data on three devices at once.
In a public place like a cafe, you should choose a place with a wide viewing angle, and it is better to sit with your back to the wall. In this case, it will be possible to see everyone who is approaching. In a suspicious situation, we block a laptop or phone and look forward to the development of events.
The lock can be configured for different operating systems, and the easiest way to do this is by pressing a certain key combination (for Windows, this is the system button + L, you can press in a split second). On MacOS, this is Command + Control + Q. It is also pressed quickly, especially if you work out.
Of course, in unforeseen situations, you can also miss, so there is another option - locking the device when you press any of the keys at the same time (punching the keyboard as an option). If you know the application that can do this for MacOS, Windows or Linux - share the link.
The MacBook also has a gyroscope. You can envisage a scenario when the laptop is blocked when the device is lifted or a sudden, rapid change in its position according to the built-in gyro sensor.
We did not find the appropriate utility, but if someone knows about such applications, tell us about them in the comments. If they are not, then we suggest writing a utility for which we will give the author a multi-year subscriptionto our VPN (depending on its complexity, functionality) and we will facilitate the distribution of the utility.

Another option is to close your screen (laptop, phone, tablet) from prying eyes. For this, the so-called “privacy filters” are ideal — special films that darken the display when the viewing angle changes. You can see what the user is doing only from the back.
By the way, a simple life hack on the topic of the day: if you are still at home, but they knock on the door or ring (the courier brought pizza, for example), then it’s better to block gadgets. Just in case.
It is possible, but difficult, to protect oneself from the "comrade major", that is, from a sudden attempt by the outside to gain access to personal data. If you have your own cases that you can share, we are waiting for examples in the comments.
How to quickly destroy information on a flash drive, HDD or SSD
Often, the easiest way to destroy information is if it is nearby. We are talking about the destruction of data from storage devices - USB-flash drives, SSD, HDD. You can destroy the drive in a special shredder or just something heavy, but we will talk about more elegant solutions.
Various companies produce storage media that receive the self-destruct function directly from the box. A huge number of solutions.
One of the simplest and most obvious examples is the Data Killer USB stick and the like. Such a device looks no different from other flash drives, but there is a battery inside. When the button is pressed, the battery destroys the data on the chip by strong heating. After that, the flash drive is not recognized when connected, so the chip itself is also destroyed. Unfortunately, detailed studies on whether it can be restored have not been conducted.

Image source: hacker.ru
There are flash drives that do not store any information, but can destroy a computer or laptop. If you put such a "flash drive" next to your laptop, and someone
There are interesting systems for reliable destruction of information stored on a hard disk inside a PC.

Earlier they were described on Habré, but it’s impossible not to mention them. Such systems are equipped with autonomous power (that is, turning off the electricity in the building will not help stop data destruction). There is also a timer for power outages, which will help if the computer is seized in the absence of the user. Even radio and GSM channels are available, so data destruction can be started remotely. It is destroyed by the device generating a magnetic field of 450 kA / m.
With SSD, this does not work out, and they were once offered the option of thermal destruction .

Above is a makeshift method that is unreliable and dangerous. Other types of devices are used for SSDs, for example, Impulse-SSD, which destroys a drive with a voltage of 20,000 V.
Information is erased, chips crack, the drive comes into complete disrepair. There are options with remote destruction (via GSM).
Sold and mechanical shredders HDD. In particular, LG launches such a device - it's CrushBox.

There are many options for gadgets to destroy HDD and SSD: they are produced both in the Russian Federation and abroad. We suggest discussing such devices in the comments - probably many readers can give their own example.
How to protect your PC or laptop
As with HDDs and SSDs, there are many varieties of laptop protection systems. One of the most reliable is encryption of everything and everything, and in such a way that, after several attempts to get to the information, the data is destroyed.
One of the most famous systems for protecting PCs and laptops was developed by Intel. The technology is called Anti-Theft. True, her support was discontinued several years ago, so this decision cannot be called new, but it is suitable as an example of protection. Anti-Theft made it possible to detect a stolen or lost laptop and block it. The Intel website said that the system protects confidential information, blocks access to encrypted data and prevents the OS from loading in the event of an unauthorized attempt to turn on the device.

This and similar systems check the laptop for signs of third-party interference, such as too many attempts to log into the system, a crash when trying to log into a previously set server, and blocking the laptop via the Internet.
Anti-Theft blocks access to the Intel chipset chipset, as a result of which it will be impossible to enter the laptop services, launch software or OS even if the HDD or SDD is replaced or reformatted. The main cryptographic files that are needed to access the data are also deleted.
If the laptop returns to the owner, he can quickly restore its performance.
There is an option using smart cards or hardware tokens - in this case, you cannot enter the system without such devices. But in our case (if the door is already knocking), we also need to set a PIN so that when connecting a key, the PC will request an additional password. As long as this type of blocker is not connected to the system, it is almost impossible to start it.
A working option now is the USBKill script written in Python. It allows you to bring a laptop or PC unusable if suddenly some startup parameters change. It was created by the Hephaest0s developer by publishing a script on GitHub.
The only condition for USBKill to work is the need to encrypt the system drive of a laptop or PC, including tools such as Windows BitLocker, Apple FileVault, or Linux LUKS. There are several ways to activate USBKill, including connecting or disconnecting a USB flash drive.
Another option is laptops with an integrated self-destruction system. One such in 2017 received the military of the Russian Federation. To destroy data with the media, you just need to click on the button. In principle, a similar artisanal system can be done by yourself or purchased online - there are many of them.

One example is the Orwl mini-PC , which can run various OSs and self-destruct when an attack is detected. True, the price tag is inhumane - $ 1699.
We block and encrypt data on smartphones
On smartphones running iOS, it is possible to erase data in the event of multiple failed authorization attempts. This function is standard and is enabled in the settings.
One of our employees discovered an interesting feature of iOS devices: if you need to quickly lock the same iPhone, just press the power button five times in a row. In this case, the emergency call mode starts, and the user will not be able to access the device via Touch or FaceID - only by password code.
Android also has various standard functions for protecting personal data (encryption, multi-factor authentication for different services, graphic passwords, FRP, and so on).
Of the simple life hacks regarding blocking the phone, you can suggest using a fingerprint, for example, a ring finger or little finger. In the event that someone begins to force the user to apply a thumb to the sensor, after several attempts the phone will be locked.
True, for iPhone and Android there are software and hardware systems that allow you to bypass almost any protection. Apple has provided the ability to disable the Lightning-connector when the user is inactive for a certain time, but whether this helps from hacking the phone using these complexes is unclear.
Some manufacturers produce phones that are protected from wiretapping and hacking, but they cannot be called 100% reliable. Android creator Andy Rubin released two years agoEssential Phone , which was called by the developers "the most secure." But he never became popular. Plus, it was practically impossible to repair: if the phone broke, then you could put an end to it.
Safe phones have also been released by Sirin Labs and Silent Cirlce. The gadgets were called Solarin and Blackphone. Boeing has created Boeing Black, a device that is recommended to defense officials. This gadget has a self-destruct mode, which is activated in case of hacking.
Be that as it may, with smartphones in terms of protection against third-party interference, everything is somewhat worse than with storage media or laptops. The only thing that can be recommended is not to use a smartphone to exchange and store sensitive information.
And what to do in a public place?
Until now, we talked about how to quickly destroy information if someone knocks on the door and you did not wait for guests. But there are also public places - cafes, fast food restaurants, street. If someone comes up from behind and picks up a laptop, then data destruction systems will not help. And no matter how many secret buttons there are, with their hands tied they cannot be pressed.
The simplest thing is not to take gadgets with critical information to the street at all. If you take it, then do not remove the lock from the device in a crowded place unless absolutely necessary. Just at that moment, being in the crowd, the gadget can be easily intercepted.
The more devices, the easier it is to intercept at least something. Therefore, instead of the “smartphone + laptop + tablet” bundle, you should use only a netbook, for example, with Linux on board. You can call using it, and information on one gadget is easier to protect than data on three devices at once.
In a public place like a cafe, you should choose a place with a wide viewing angle, and it is better to sit with your back to the wall. In this case, it will be possible to see everyone who is approaching. In a suspicious situation, we block a laptop or phone and look forward to the development of events.
The lock can be configured for different operating systems, and the easiest way to do this is by pressing a certain key combination (for Windows, this is the system button + L, you can press in a split second). On MacOS, this is Command + Control + Q. It is also pressed quickly, especially if you work out.
Of course, in unforeseen situations, you can also miss, so there is another option - locking the device when you press any of the keys at the same time (punching the keyboard as an option). If you know the application that can do this for MacOS, Windows or Linux - share the link.
The MacBook also has a gyroscope. You can envisage a scenario when the laptop is blocked when the device is lifted or a sudden, rapid change in its position according to the built-in gyro sensor.
We did not find the appropriate utility, but if someone knows about such applications, tell us about them in the comments. If they are not, then we suggest writing a utility for which we will give the author a multi-year subscriptionto our VPN (depending on its complexity, functionality) and we will facilitate the distribution of the utility.

Another option is to close your screen (laptop, phone, tablet) from prying eyes. For this, the so-called “privacy filters” are ideal — special films that darken the display when the viewing angle changes. You can see what the user is doing only from the back.
By the way, a simple life hack on the topic of the day: if you are still at home, but they knock on the door or ring (the courier brought pizza, for example), then it’s better to block gadgets. Just in case.
It is possible, but difficult, to protect oneself from the "comrade major", that is, from a sudden attempt by the outside to gain access to personal data. If you have your own cases that you can share, we are waiting for examples in the comments.
