Security Week 18: ShadowHammer attack in detail
In late March, Motherboard published an article on a potential hack into Asus' infrastructure. Having gained partial access to the company's resources, the attackers were able to distribute among the customers who installed the Asus Live Update utility for the timely download of new drivers a version of the program signed with an official certificate with malicious functionality. About this attack, discovered by Kaspersky Lab experts, we wrote in early April .
Kaspersky Lab published an extended reportAbout ShadowHammer April 23rd. This very fascinating, although completely technical document is recommended for reading in its entirety, and in this post there will be only a brief description of some of the finds. The most interesting thing is the potential connection of ShadowHammer with infected copies of not the best computer game about zombies and a coordinated attack on software developers.
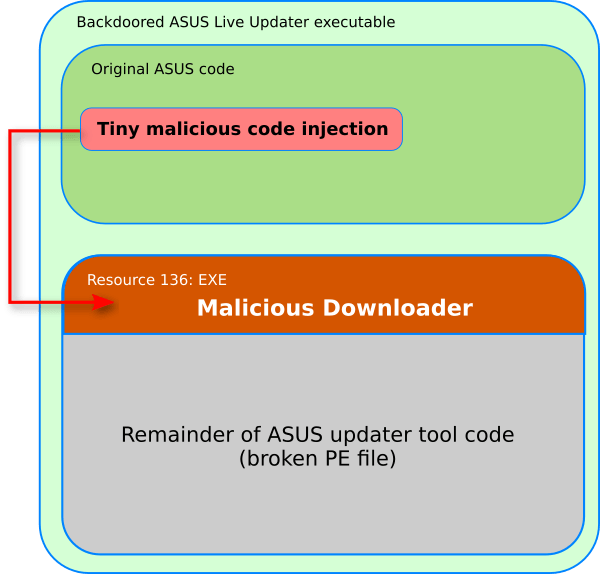
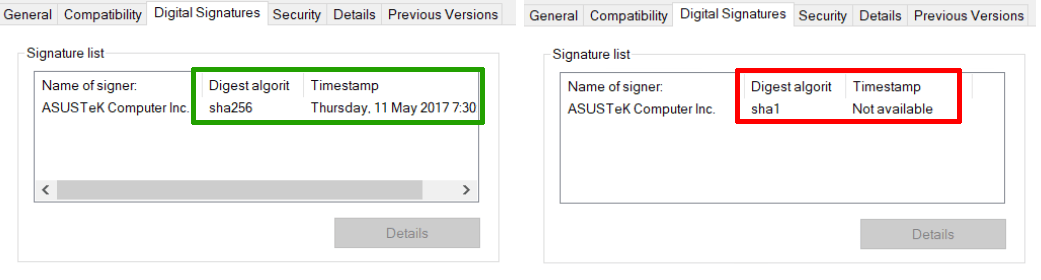
In total, Kaspersky Lab experts found 230 samples of an infected utility for updating drivers on Asus devices. In all cases, its original version is dated 2015, but later during the attack, the method of injecting its own executable code was changed - most likely to more effectively avoid detection:
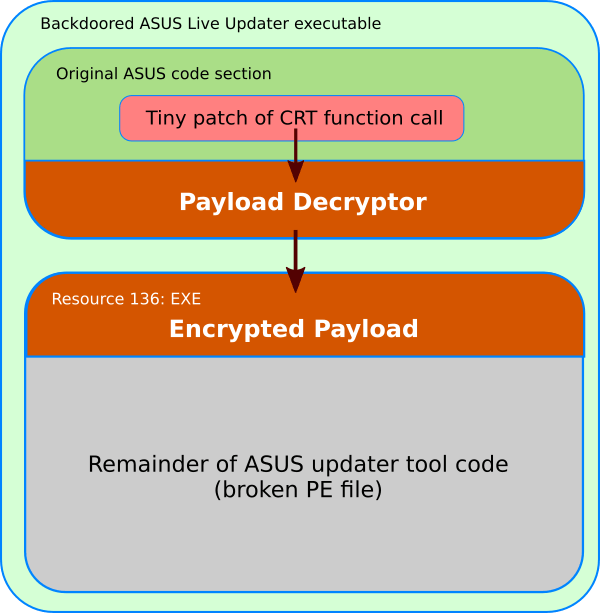
The method of introducing malicious code was changed between July and December 2018. The start date of the attack is not reliably known, but was discovered in January 2019. The most effective way to infect users' computers and go unnoticed was to use Asus legitimate certificates, which were also used to sign “official” harmless utilities issued by this company.
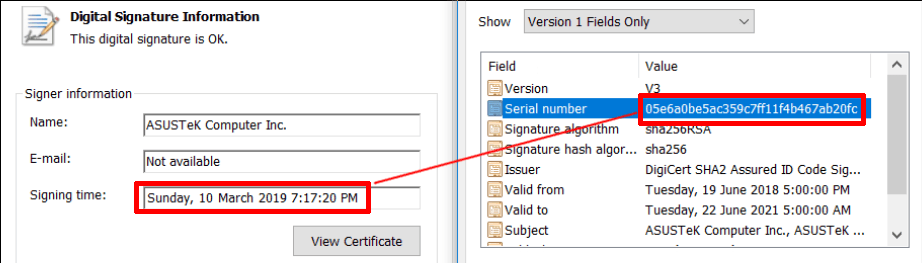
The screenshot above shows an example of a legitimate Asus utility signed with the same certificate as the malicious version of Asus Live Update. The signature date is March 2019, after the vendor received information about the attack and the certificates used. The campaign operators had to change the digital signature for the modified executable files in the process, as the first stolen certificate expired in August 2018.
Judging by the use of the old version of the legitimate program and the differences in the digital signature of the official and modified software, the organizers of the attack had limited access to the internal resources of the vendor. For example, it was possible to hack into the computer of one of the developers, steal certificates, but not the actual source code of the utility. In addition, attackers gained access to the infrastructure for the delivery of updated versions of the utility in order to spread the malicious modification.
A key feature of a ShadowHammer attack is the limited number of attack targets. There were a lot of potential victims: a malicious version of Asus Live Update was detected only by Kaspersky Lab tools in 57 thousand users. The actual number of victims could be even higher, but on most computers the malware did not do anything clearly illegal.
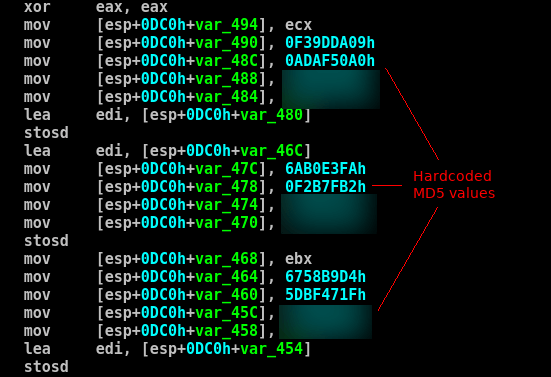
In all cases, the modified utility collected data about the MAC addresses of all available network adapters and compared their MD5 hashes with its own list. Only if one of the MAC addresses from the list was found, did the command contact the server from which another executable file was downloaded. The number of addresses differs from sample to sample: the shortest list consists of eight MAC addresses, the longest of them 307. In total, we managed to identify more than 600 identifiers of network devices by which the attackers found systems of interest. Check your own MAC addresses for presence in this list here .
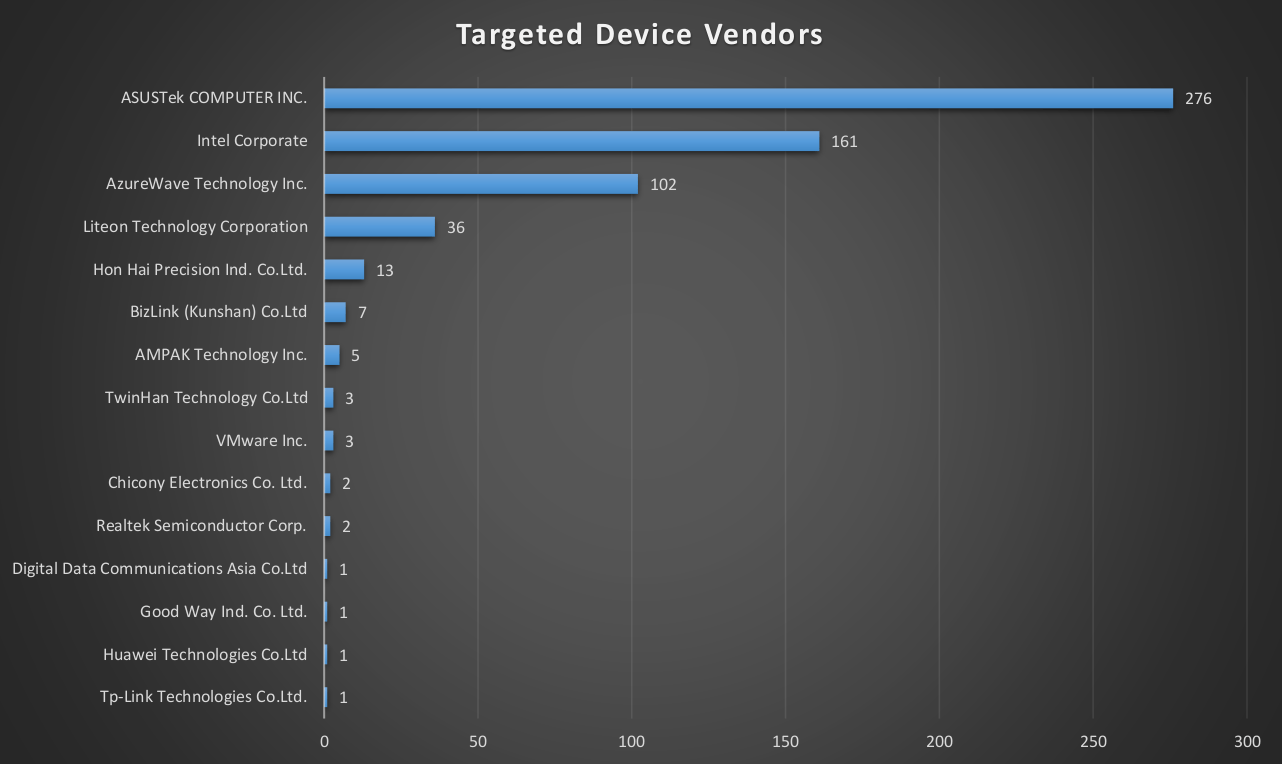
It is logical that most of the MAC addresses in the list relate to devices manufactured by Asus itself. But there are addresses covering a large number of users, for example 00-50-56-C0-00-08 - the identifier of the virtual network adapter VMWare. However, this coincidence did not always lead to the development of an attack: it started only if the MAC address of the physical network adapter also matched the required one.
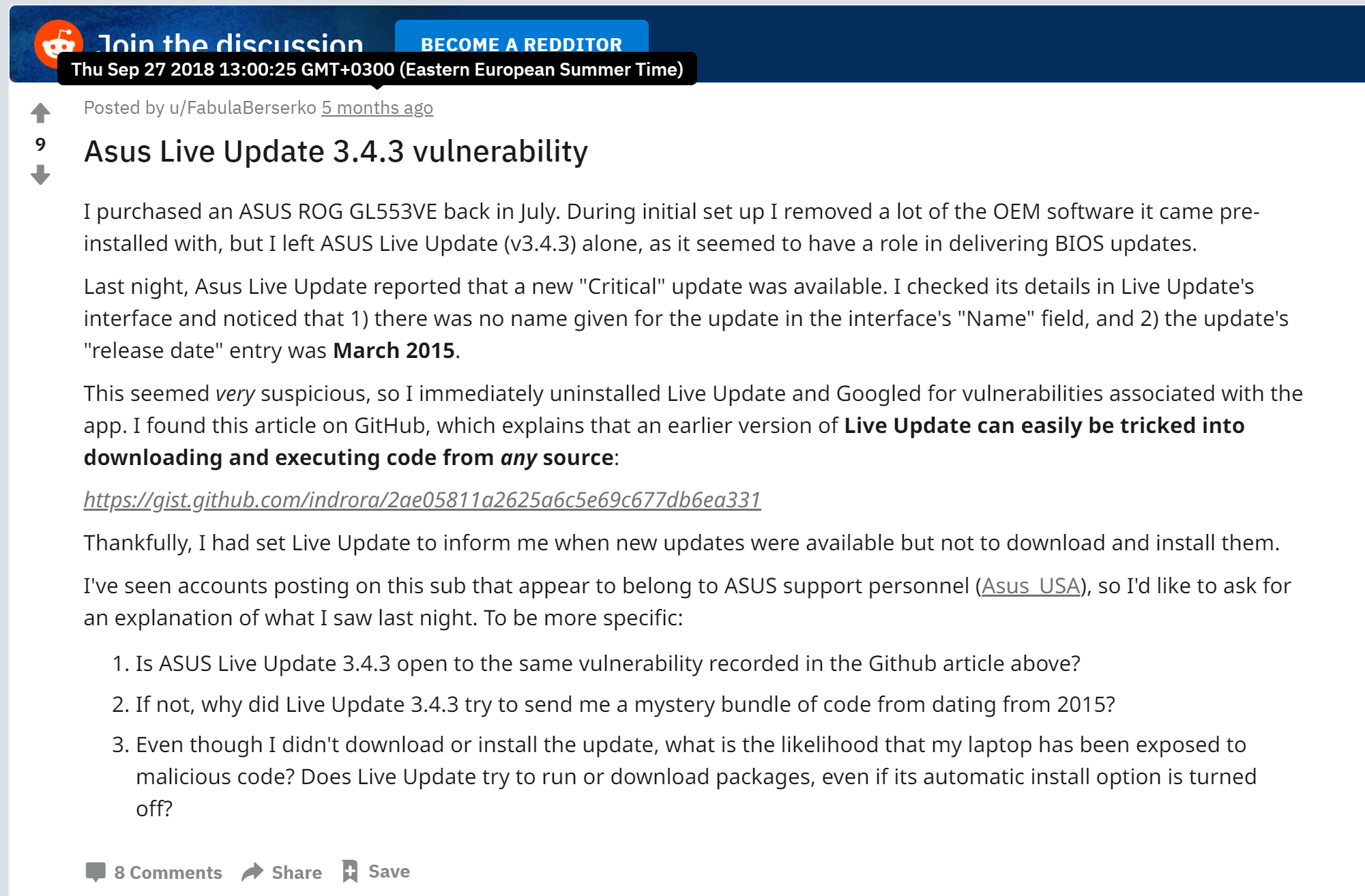
How it looked in practice, shows a screenshot of the discussion on Reddit. A user with the installed Asus Live Update utility receives a notification about a “critical update”, and it is suggested to download the program three years ago. It is not a fact that this discussion is about this particular attack (since there is no file identifier), but judging by the build date of the binary, it was she. Considering that the search for mentions gave only two reports of potential problems (the second was not connected with ShadowHammer for sure), we can say that the attack went unnoticed, despite the rather large number of potential victims.
What happened to those whose MAC address was on the list is unknown. At the time the attack was detected in January 2019, the command server was turned off, and so far the researchers have not been able to obtain executable files downloaded to the computers of real victims.
Connection with other attacks
And here zombies burst into the post !

In March 2019, ESET experts examined infected versions of the game Infestation: Survivor Stories. Given the theme of the game, this in itself sounds like a joke, but the situation for the developer (probably using the sources of the earlier The War Z game) is not the most fun. Most likely, the malicious code appeared in the official builds after the computers of the developers were compromised. In this, and in a couple of other incidents related to attacks on game studios, a method similar to ShadowHammer was used to inject malicious code:
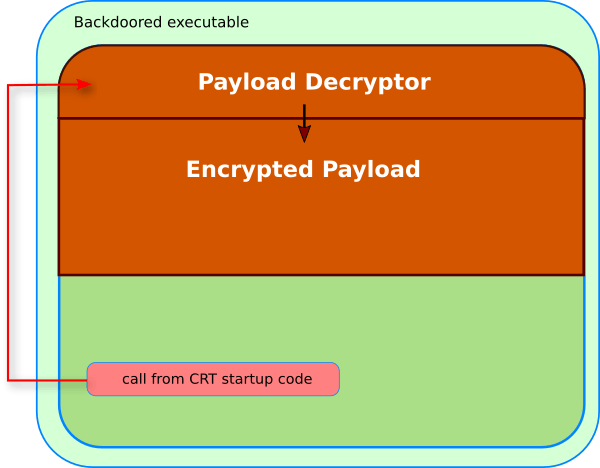
Okay, this is not reliable evidence of the connection between the two incidents. But there is a coincidence in the hash algorithms used for the data collected on victim computers, and a couple of other common technical features of the attacks. Judging by the lines in the malicious code, it can be assumed that the sources of the earlier War Z game could be distributed as a kind of Trojan horse for game developers who want to use them. Kaspersky Lab experts also found signs of reusing algorithms from ShadowHammer in the PlugX backdoor , most likely developed in China.
This potential connection between different attacks gives the ShadowHammer story a new dimension and is a warning to developers. Programmers can become unwitting distributors of malicious code thanks to the coordinated and consistent actions of attackers. Moreover, different “implementation” tools can be used: theft of certificates, the inclusion of malicious code in the sources, injection into executable files (for example, before sending to the customer). Judging by the number of blank spots in this and other investigations, the attackers managed to infiltrate the infrastructure of the software developers, spread the malicious code to a large number of victims, while carefully selecting targets so that they go unnoticed for at least several months (as is the case with ShadowHammer) .
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.

Kaspersky Lab published an extended reportAbout ShadowHammer April 23rd. This very fascinating, although completely technical document is recommended for reading in its entirety, and in this post there will be only a brief description of some of the finds. The most interesting thing is the potential connection of ShadowHammer with infected copies of not the best computer game about zombies and a coordinated attack on software developers.

In total, Kaspersky Lab experts found 230 samples of an infected utility for updating drivers on Asus devices. In all cases, its original version is dated 2015, but later during the attack, the method of injecting its own executable code was changed - most likely to more effectively avoid detection:

The method of introducing malicious code was changed between July and December 2018. The start date of the attack is not reliably known, but was discovered in January 2019. The most effective way to infect users' computers and go unnoticed was to use Asus legitimate certificates, which were also used to sign “official” harmless utilities issued by this company.

The screenshot above shows an example of a legitimate Asus utility signed with the same certificate as the malicious version of Asus Live Update. The signature date is March 2019, after the vendor received information about the attack and the certificates used. The campaign operators had to change the digital signature for the modified executable files in the process, as the first stolen certificate expired in August 2018.
Judging by the use of the old version of the legitimate program and the differences in the digital signature of the official and modified software, the organizers of the attack had limited access to the internal resources of the vendor. For example, it was possible to hack into the computer of one of the developers, steal certificates, but not the actual source code of the utility. In addition, attackers gained access to the infrastructure for the delivery of updated versions of the utility in order to spread the malicious modification.
A key feature of a ShadowHammer attack is the limited number of attack targets. There were a lot of potential victims: a malicious version of Asus Live Update was detected only by Kaspersky Lab tools in 57 thousand users. The actual number of victims could be even higher, but on most computers the malware did not do anything clearly illegal.

In all cases, the modified utility collected data about the MAC addresses of all available network adapters and compared their MD5 hashes with its own list. Only if one of the MAC addresses from the list was found, did the command contact the server from which another executable file was downloaded. The number of addresses differs from sample to sample: the shortest list consists of eight MAC addresses, the longest of them 307. In total, we managed to identify more than 600 identifiers of network devices by which the attackers found systems of interest. Check your own MAC addresses for presence in this list here .

It is logical that most of the MAC addresses in the list relate to devices manufactured by Asus itself. But there are addresses covering a large number of users, for example 00-50-56-C0-00-08 - the identifier of the virtual network adapter VMWare. However, this coincidence did not always lead to the development of an attack: it started only if the MAC address of the physical network adapter also matched the required one.

How it looked in practice, shows a screenshot of the discussion on Reddit. A user with the installed Asus Live Update utility receives a notification about a “critical update”, and it is suggested to download the program three years ago. It is not a fact that this discussion is about this particular attack (since there is no file identifier), but judging by the build date of the binary, it was she. Considering that the search for mentions gave only two reports of potential problems (the second was not connected with ShadowHammer for sure), we can say that the attack went unnoticed, despite the rather large number of potential victims.
What happened to those whose MAC address was on the list is unknown. At the time the attack was detected in January 2019, the command server was turned off, and so far the researchers have not been able to obtain executable files downloaded to the computers of real victims.
Connection with other attacks
And here zombies burst into the post !

In March 2019, ESET experts examined infected versions of the game Infestation: Survivor Stories. Given the theme of the game, this in itself sounds like a joke, but the situation for the developer (probably using the sources of the earlier The War Z game) is not the most fun. Most likely, the malicious code appeared in the official builds after the computers of the developers were compromised. In this, and in a couple of other incidents related to attacks on game studios, a method similar to ShadowHammer was used to inject malicious code:

Okay, this is not reliable evidence of the connection between the two incidents. But there is a coincidence in the hash algorithms used for the data collected on victim computers, and a couple of other common technical features of the attacks. Judging by the lines in the malicious code, it can be assumed that the sources of the earlier War Z game could be distributed as a kind of Trojan horse for game developers who want to use them. Kaspersky Lab experts also found signs of reusing algorithms from ShadowHammer in the PlugX backdoor , most likely developed in China.
This potential connection between different attacks gives the ShadowHammer story a new dimension and is a warning to developers. Programmers can become unwitting distributors of malicious code thanks to the coordinated and consistent actions of attackers. Moreover, different “implementation” tools can be used: theft of certificates, the inclusion of malicious code in the sources, injection into executable files (for example, before sending to the customer). Judging by the number of blank spots in this and other investigations, the attackers managed to infiltrate the infrastructure of the software developers, spread the malicious code to a large number of victims, while carefully selecting targets so that they go unnoticed for at least several months (as is the case with ShadowHammer) .
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
