SafeERP software package update: Authority hierarchy
In March 2019, Gazinformservice introduced an updated version of the SafeERP 4.6 software package. A detailed description of the SafeERP product is provided on the company's website .
The new version of the SafeERP 4.6 software package includes a procedure for constructing a hierarchy of privileges for selected permission objects for analysis.
Recall the structure and general concepts of the SAP authorization concept: “Authorization Object” -> “Authority” -> “Profile” -> “Role” -> “User Account”. The concept of authority is classic, but the actual implementation is more complex:
The hierarchy of the possible authority structure is shown in Figure 1.
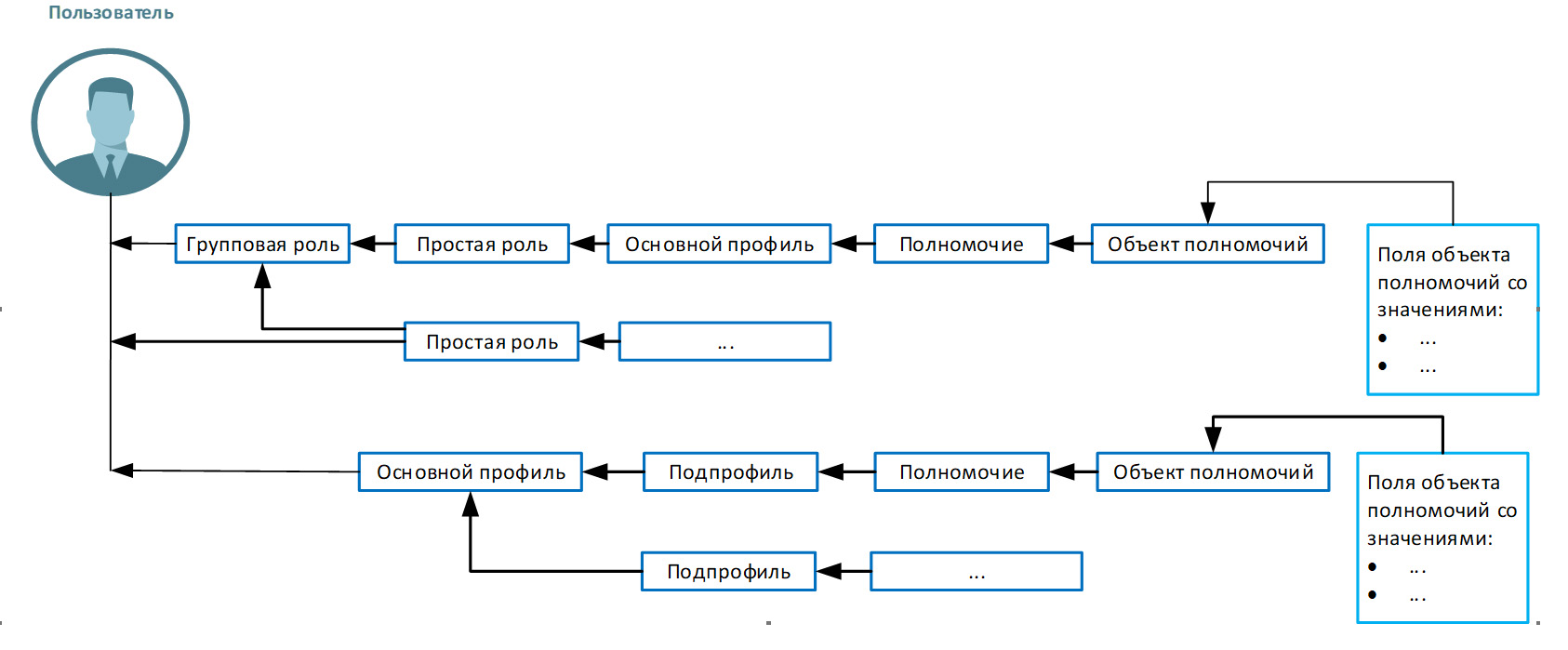
Figure 1 - General structure of the SAP authority concept
To control user access rights to authority fields and analyze configuration checks for SAP systems, a new authorization hierarchy analysis functionality has been developed.
To control user access rights, the procedure for constructing a hierarchy of privileges is included in the SafeERP Platform Security software module (for all authorization checks).
As part of the SafeERP Platform Security product, for all authorization checks, you can control user access rights to authorization fields. An example of the report execution is given for checking 0002 “Server startup ” (Fig. 2):

Figure 2 - Data output interface in the SafeERP Platform Security software module
An example of an authorization hierarchy list is shown in Figure 3.
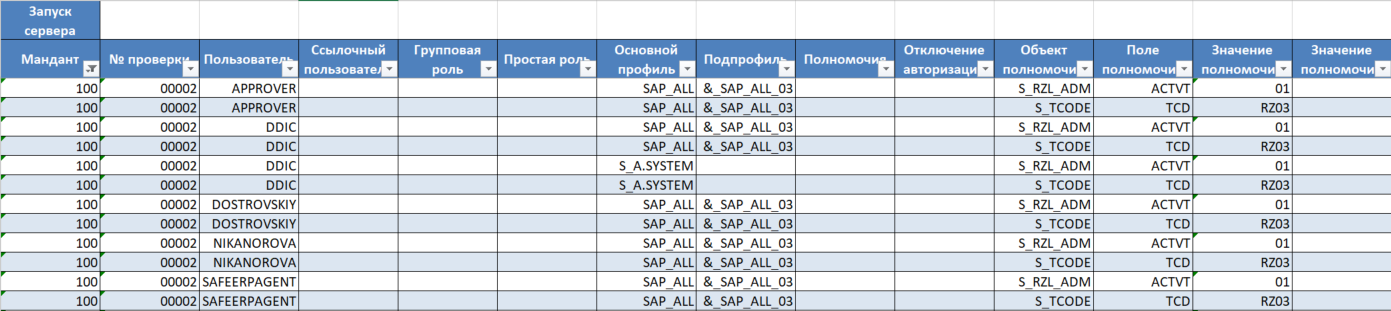
Figure 3 - Format of an authorization hierarchy list in XLS format
As part of the SafeERP Code Security product, verification of authorization objects for specified transactions is implemented. The result of the work is a list of authorization objects for the selected transactions. An example of finding authorization objects for an SUIM transaction (Fig. 4):
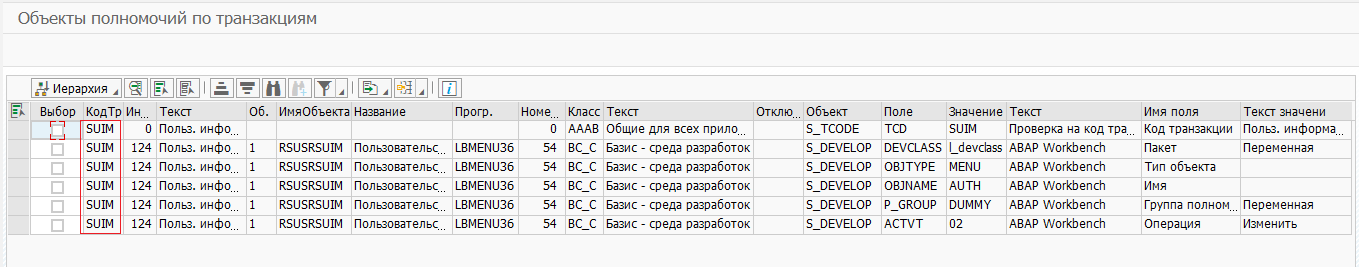
Figure 4 - Authorization objects for transactions
To obtain data about permissions, profiles, and roles that contain the checked authorization objects, as well as about user accounts, the hierarchy construction procedure is activated. A report with a hierarchy of permissions is generated in the ALV format or downloaded to an Excel file and contains all the relationships between users and the analyzed authorization objects. The format of the list of authority hierarchies in the ALV form is presented in Figure 5.
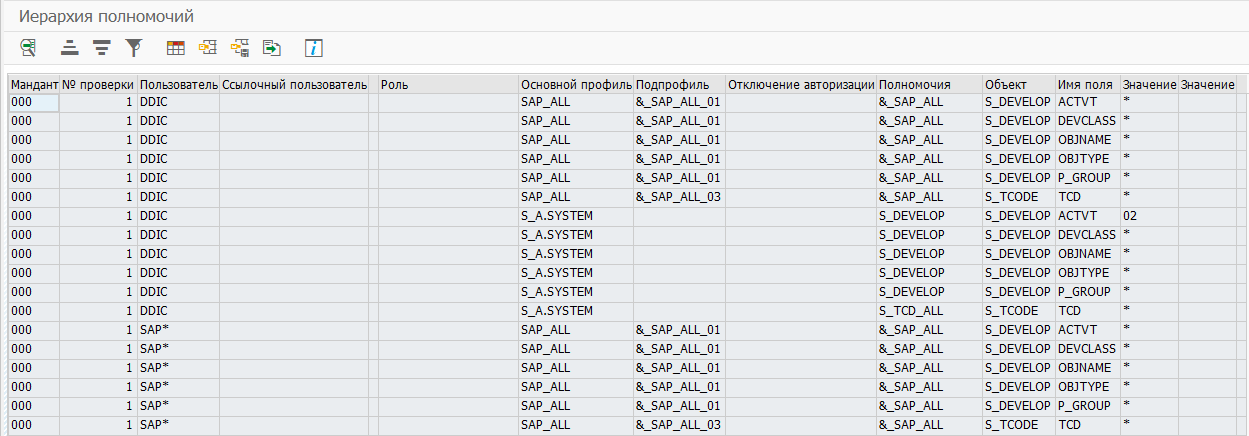
Figure 5 - The format of the list of authority hierarchies in the ALV form The
construction of a system of separation of powers (SoD matrix, Segregation of Duties) is an important condition for the security of ERP systems. The control of the correctness of the implemented system of differentiation of powers is a complex procedure, the report “Hierarchy of powers” will help automate this process.
The new version of the SafeERP 4.6 software package includes a procedure for constructing a hierarchy of privileges for selected permission objects for analysis.
Recall the structure and general concepts of the SAP authorization concept: “Authorization Object” -> “Authority” -> “Profile” -> “Role” -> “User Account”. The concept of authority is classic, but the actual implementation is more complex:
- multiple roles can be assigned to the user;
- a composite role (Composite Role) may include several roles;
- a composite authorization profile may consist of several profiles (Composite Profile);
- another composite profile may be included in the composite profile;
- the user can inherit the authority of the reference user.
The hierarchy of the possible authority structure is shown in Figure 1.

Figure 1 - General structure of the SAP authority concept
To control user access rights to authority fields and analyze configuration checks for SAP systems, a new authorization hierarchy analysis functionality has been developed.
To control user access rights, the procedure for constructing a hierarchy of privileges is included in the SafeERP Platform Security software module (for all authorization checks).
As part of the SafeERP Platform Security product, for all authorization checks, you can control user access rights to authorization fields. An example of the report execution is given for checking 0002 “Server startup ” (Fig. 2):

Figure 2 - Data output interface in the SafeERP Platform Security software module
An example of an authorization hierarchy list is shown in Figure 3.

Figure 3 - Format of an authorization hierarchy list in XLS format
As part of the SafeERP Code Security product, verification of authorization objects for specified transactions is implemented. The result of the work is a list of authorization objects for the selected transactions. An example of finding authorization objects for an SUIM transaction (Fig. 4):

Figure 4 - Authorization objects for transactions
To obtain data about permissions, profiles, and roles that contain the checked authorization objects, as well as about user accounts, the hierarchy construction procedure is activated. A report with a hierarchy of permissions is generated in the ALV format or downloaded to an Excel file and contains all the relationships between users and the analyzed authorization objects. The format of the list of authority hierarchies in the ALV form is presented in Figure 5.

Figure 5 - The format of the list of authority hierarchies in the ALV form The
construction of a system of separation of powers (SoD matrix, Segregation of Duties) is an important condition for the security of ERP systems. The control of the correctness of the implemented system of differentiation of powers is a complex procedure, the report “Hierarchy of powers” will help automate this process.
