How to hack a factory: radio control systems as a weak link in modern production

Trend Micro released a study that examined the vulnerabilities of the remote control system of industrial equipment and how easy it was for attackers to use them to attack industrial facilities.
Recently we (Trend Micro specialists) published the results of another research that this time concerns remote radio control systems. used to work with industrial equipment. During the study, we tested equipment from seven major vendors to find vulnerabilities in its protection systems, and ways that criminals can take advantage of, wanting to take control of this equipment. And found, which is typical, and vulnerabilities, and ways. They can potentially be used to sabotage production, theft, and even blackmail.
Protection VS Attack: Vulnerability Analysis
For our research, we used equipment samples from seven of the most popular global manufacturers of radio control systems, including Saga, Circuit Design, Juuko, Autec, Hetronic, Elca and Telecrane. Saga and Juuko equipment was researched in the laboratory to better study the protocols used, and the hacking of the control systems of the other five vendors was carried out directly in the field. The search for vulnerabilities was conducted in five main areas: recording / playing commands of the remote control, substitution of commands from the remote control, initiation of emergency shutdown of equipment, replacement of the remote control connected to the system and reprogramming of equipment.
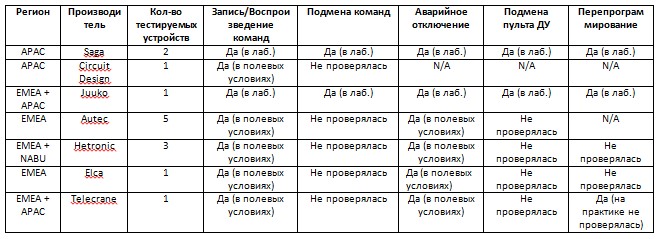
Results of research. The status N / A means that the device in principle does not support the tested functions (for example, the function of emergency shutdown).
The studies also revealed the main weaknesses in the data transmission protocols and software used, including the absence of a changing code (ie, any once intercepted data packet can be used in the future), the complete absence or weak cryptographic data protection (transmitted between the receiver and transmitter the command sequence can be easily deciphered), and the lack of software protection methods (software for flashing transmitters and receivers is in no way protected from being used by attackers in their x goals).
At the same time, it is worth noting that developing “patches” for all three problems is extremely simple, but they can be implemented quickly and efficiently only for software that supports the addition of an access control system. In other cases, the obstacle will be a huge amount of used equipment, the lack of convenient access to the necessary components and the fact that part of it is so outdated that it does not support the necessary functions at the hardware level, for example, encryption.

Examples of equipment used in the research
Record / play commands
To test the system for this vulnerability, we recorded the "traces" of the "Start" command, clicking on various buttons on the remote and the device's emergency shutdown commands. Reproducing them then, they immediately confirmed three important facts:
- there are no defensive mechanisms in the system, such as a changing code, since the signals recorded earlier were perceived by the receivers as original;
- an attacker may well enable a disabled device using these signals;
- the command to initiate an emergency shutdown is encoded in such a way that it can easily be used as a separate type of attack.
During the attacks, various SDR devices were used, including Ettus USRP N210, BladeRF x115 and HackRF. As a result, we came to the conclusion that practically any device of this type of sufficient power, equipped with a transmitting antenna, is suitable for such attacks. Ettus USRP N210 was used in conjunction with GNU Radio, and special scripts were written for the BladeRF x115.
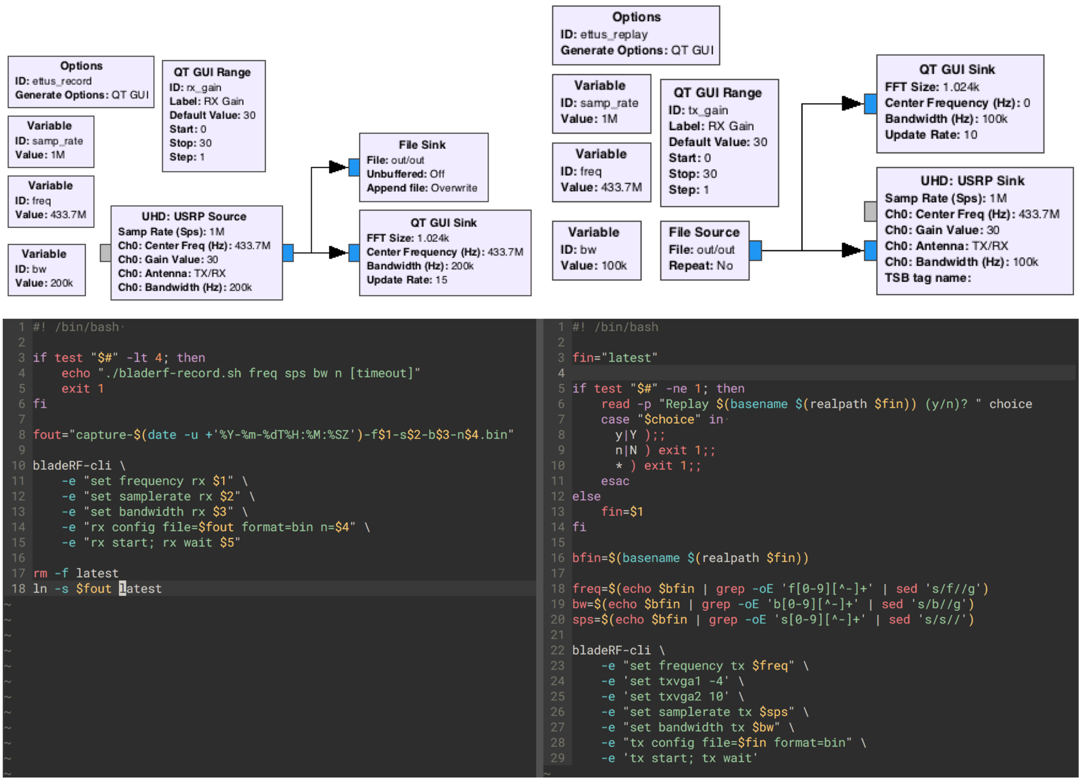
GNU Radio scripts and scheme written to record and play commands
In all tests that were conducted both in the laboratory and in the field, the command record / play scheme worked without additional settings or modifications, which confirms the simplicity of such attacks and almost complete exposure. from them used equipment.
Command substitution
To use this type of attack, it is necessary to decipher the protocols used by remote control systems, both at the software level and at the transmitter hardware level. As for the attack using recording / replaying, they wrote down the basic commands that are used to control devices, but this time the goal was to record all possible combinations of button presses, including short and long presses.
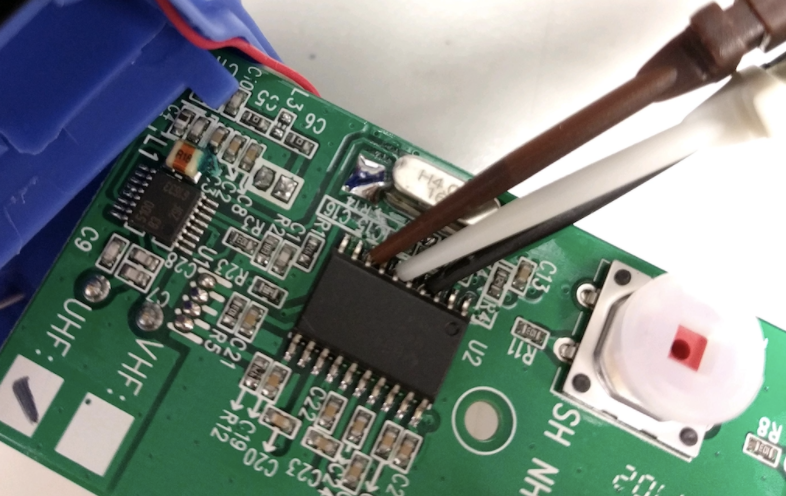
Diagnostic analyzer connected to a radio transmitter to decrypt data
This was necessary in order to begin to understand the demodulation schemes used in various remote controls. For the same purpose, we studied all the available documentation and used the Universal Radio Hacker application to study the form of radio signals. After that, we developed scripts to conduct an attack, and working with Juuko devices even led to the creation of a special hardware module for hacking, which we called RFQuack.
Trigger Disable
In fact, initiation of an emergency shutdown is a logical continuation of the first two types of attacks. For its implementation, the remote control used by hackers constantly sends packets to the equipment that are responsible for the restart or emergency shutdown commands. Moreover, even with the original remote control, which other teams gave to the equipment at that moment, these packages were still processed during the tests and led to the device shutting down / rebooting. This method can be easily used for sabotage or extortion, completely paralyzing the work of individual pieces of equipment or its mass shutdown.
Substitution remote control
In both tested devices (Saga and Juuko), to test this vector of attack, we first had to activate the pairing function, which is disabled by default. After that, it was necessary to turn on the receiver and press on certain buttons on the remote control. We intercepted the signals transmitted by the pairing process using BladeRF and replayed them, after which the receiver stopped receiving commands from the original remote control, taking the new signal source as the main one.
At the same time, the protocol itself used in the pairing process is in no way protected from hacking and is not much different from the usual commands transmitted from the remote control to the receiver. Moreover, due to the vulnerability of the data transfer protocol for pairing, a similar method worked even with Juuko devices, although in them you need to press a special button on the equipment to complete the pairing. Subsequently, with the help of this method, attackers will be able to initiate mass DoS attacks on equipment and sabotage its operation within the whole plant or automated dock / warehouse.
Reprogramming
To check this attack vector, a copy of the firmware was used and, if necessary, a special dongle was used. Samples Juuko and Saga thus managed to reprogram in the laboratory, and for the equipment Telecrane the possibility of reprogramming was confirmed at the theoretical level, based on the technical documentation of the device.
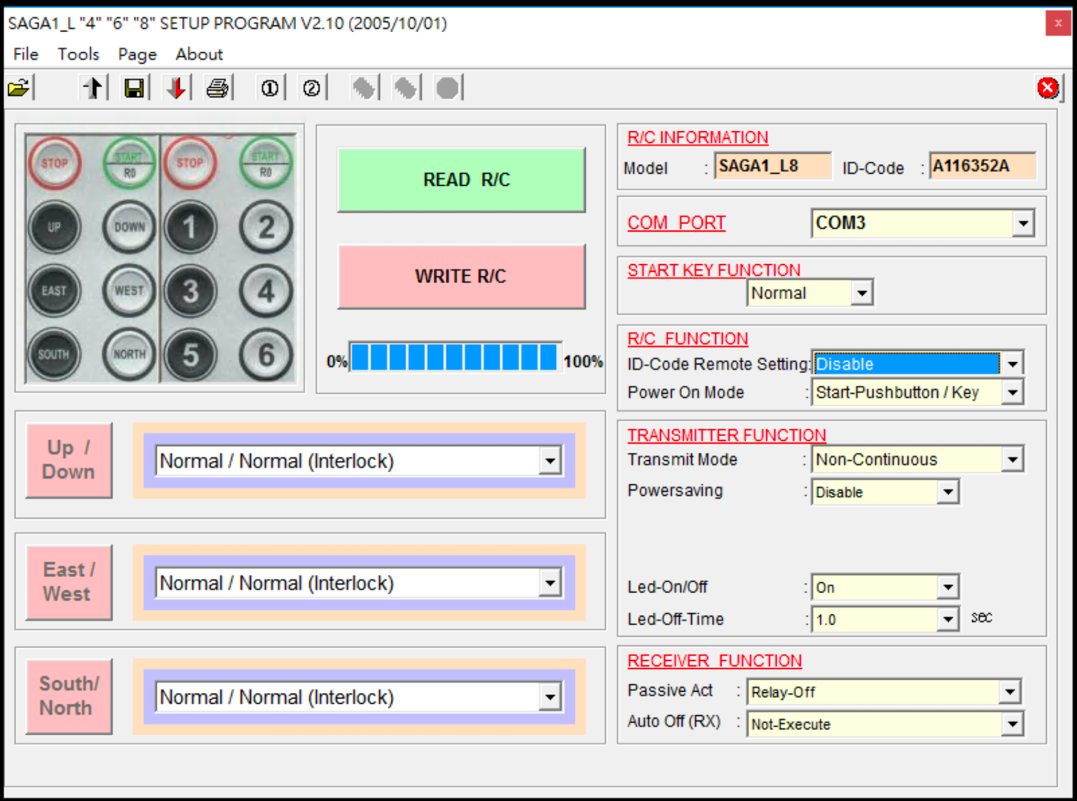
Software interface for flashing Saga devices
In all three cases, it was found that the software for working with firmware devices lacks user authentication and protection mechanisms against third-party interference. In addition, the software is only designed to work with Windows (and, in some cases, with outdated Windows XP), which remains the most popular OS for distributing malware.
In the case of Saga equipment, attackers can also quite easily get access to BSL passwords and parameters that are recorded in the device’s flash memory and, accordingly, modify the firmware, extract its files for further study, implement their own malicious code for delayed activation and even initiate a complete erasure of information from memory to hide the traces of their activities. The only condition for the successful use of this vector of attack is access to a computer, which is used for flashing systems of remote control equipment.
findings
The main conclusion that can be drawn from the report ( A Security Analysis of Radio Remote Controllers for Industrial Applications ) is that the so-called protection systems of this equipment against malicious attacks do not withstand any criticism, and in some devices are not provided at all. We believe that the main reasons for the current situation are the long service life of this equipment (the life cycle of some of the studied samples ended many years ago), the high cost of replacing it, the complexity of updating the software and the introduction of any new security systems.
Industrial systems of remote control of equipment in terms of their level of protection from external influence are far behind such systems in the consumer segment and without major modernization and revision of the manufacturers' approach to this issue, they remain a weak link in the safety of industrial facilities. As the results of the study showed, taking advantage of existing vulnerabilities is quite simple, so you need to develop a systematic approach to fixing them, including regular release of software updates and firmware, transition of industrial equipment to generally accepted radio standards (Bluetooth Low Energy and 5G), using hardware encryption, and developing unique mechanisms for protection against unauthorized access to the hardware of receivers and transmitters, in order to complicate the task for intruders,
