Hacking cameras: attack vectors, vulnerability search tools and anti-tracking

Surveillance cameras have become part of the Internet of things and, like other devices with unhindered access to the network, have fallen into the focus of interest of hackers. Millions of IP cameras from different manufacturers are open to attackers.
Camera manufacturers can save on the work of programmers and hardware - customers get cheap devices with limited computing resources and huge holes in security mechanisms.
Firmware for mass-consumer noname devices do not stand up to criticism. Often they are not updated by anyone and do not become more secure after changing the default password. Moreover, the manufacturer itself can lay a backdoor.
Next, we consider the main areas of attack on video surveillance systems.
Free cheese

“5MP pinhole lens camera module for video surveillance camera pinhole module from the factory”
From the point of view of the consumer, the market is complicated illogical. With the “penny” cost of the IP camera modules themselves, at the output we get the cost of the simplest devices close to $ 100.
The main value is formed at a level above iron. The main thing is computing resources, firmware and the ability to support all the "chips" of the firmware for an arbitrarily long time. The camera should work for years at an equally high level of protection.
The point is that the manufacturer of embedded equipment, which seeks to save on everything, is highly likely to leave such vulnerabilities in firmware and hardware that even access via the bare-line ONVIF protocol with a complex password does not protect against an attacker.
The lack of automatic updates is a sentence to the entire security system. A regular user does not follow the news in the IT field and will not go to manually download the new firmware for his camera, bought on Aliexpress for sale.
One of the most impressive examples of exploiting the features of cheap cameras is related to the Heartbleed OpenSSL exploit - an unpleasant combination of the Heartbleed vulnerability with the specifics of embedded devices that may never be updated at all.
As a result, cameras are used for espionage and, which happens much more often, become part of botnets. So hacking Xiongmai cameras led to a powerful DDOS attack not on Netflix, Google, Spotify, and Twitter.
Passwords
The woman in the video purchased a camera in a discount store. She wanted to use the device to keep track of her puppy. After some time, the camera began to talk with the hostess and independently rotate. And what happened often happens with cheap Chinese cameras, in which direct open access to the video stream is provided even on the manufacturer’s website.
At first glance, camera passwords may seem too obvious a security measure for discussion, however, tens of thousands of cameras and DVRs are regularly compromised due to the use of default passwords.
Hacker group Lizard Squad hackedThousands of CCTV cameras, using a simple factory account, the same for all cameras. The devices were hacked with a banal brute force (although, perhaps, they looked at the username and password from the manufacturer itself).
Ideally, manufacturers should assign a unique, long, and non-obvious password for each camera. Such a meticulous process takes time to set up and is difficult to administer. Therefore, many integrators use the same password for all cameras.
Staff turnover or changing user roles helps create unexpected security holes in enterprises. If the system lacks a well-thought-out mechanism for delimiting access rights for various employees, groups of cameras and objects, we get a potential vulnerability like the “Chekhov rifle” - it will definitely fire.
Port forwarding
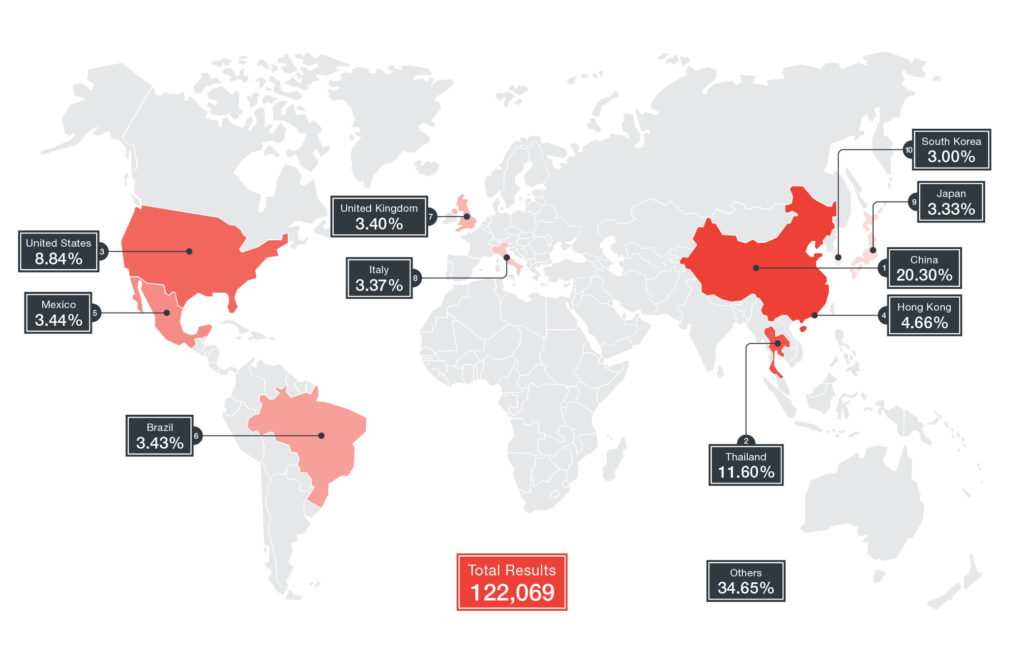
Number of cameras infected via 81 TCP ports (Shodan data)
The term “port forwarding” is sometimes replaced with the same ones: “port forwarding”, “port forwarding” or “port forwarding”. Open the port on the router, for example, to connect from the Internet to your home camera.
Most traditional surveillance systems, including DVR, NVR and VMS, are now connected to the Internet for remote access or operate on a LAN, which, in turn, is connected to the global network.
Port forwarding allows you to get customizable access to the camera on your local network, but also opens a window for hacking opportunities. If you apply a specific type of query , the Shodan search engine will show about 50,000 vulnerable devices that hang around the network freely.
An Internet-open system requires at least IDS / IPS for additional protection. Ideally, put the video surveillance system on a physically separate network or use a VLAN.
Encryption
Argentine security researcher Esekiel Fernandez has published a vulnerability that makes it easy to extract unencrypted video from the local drives of various DVRs.
Fernandez discovered that you can access the control panel of certain DVRs using a short exploit:
$> curl "http: // {DVR_HOST_IP}: {PORT} /device.rsp?opt=user&cmd=list" -H "Cookie: uid = admin"We met surprisingly many cameras, DVR, NVR, VMS, which did not even encrypt the channel over SSL. The use of such devices poses worse problems than the complete abandonment of https. At Ivideon, we use TLS encryption not only for video in the cloud, but also for streams from cameras.
In addition to unsafe connections, the same privacy risks come with storing unencrypted video on disk or in the cloud. For a truly secure system, the video must be encrypted both when stored on disk, and when transferred to the cloud or local storage.
Hacking procedure
Busting for the smallest
Video stream management software often interacts with various potentially vulnerable components of the operating system. For example, many VMS use Microsoft Access. Thus, unencrypted video can be accessed through “holes” in the OS.
Since the cameras are vulnerable from all sides, the choice of targets for attack is unusually wide, most of the illegal actions do not require special knowledge or special skills.
Almost anyone who wants to illegally watch a broadcast from a camera can easily do this. Therefore, it is not surprising that unskilled hackers are often involved in connecting to unprotected cameras just for fun.
For brute force, you can use the BIG HIT SPAYASICAM and SquardCam programs, along with the masscan and RouterScan penetration testing tools. Sometimes you don’t even need to use security scanners - Insecam and IP-Scan sites make it easy to find cameras on the Internet.
Significantly simplifies hacking access to the RTSP-link of the camera. And the desired links can be obtained here or here . For remote viewing and control of DVRs and cameras, official applications from equipment manufacturers - SmartPSS and IVMS-4200 are widely used.
Unobvious consequences
Information about open cameras or cameras with known passwords is widely distributed on imageboards and social networks. Clips from hacked cameras on YouTube gain hundreds of thousands of views.
Compromised cameras have several non-obvious uses. Among them is cryptocurrency mining. Employees of the IBM X-Force division discovered a variant of the ELF Linux / Mirai trojan , which is equipped with a module for mining bitcoins. The malware scans and infects vulnerable Linux devices, including DVRs and video surveillance cameras.
More serious consequences may arise due to the use of vulnerable devices as intermediate points for attacks on third-party infrastructures, which can be launched to conceal forensic evidence, falsify data or perform a denial of service.
And the last thing you need to know when using cameras - the manufacturer himself can leave a backdoor for himself with an unknown purpose. So, security specialists from Risk Based Security discovered a vulnerability in surveillance cameras of the Chinese manufacturer Zhuhai RaySharp Technology.
Firmware for RaySharp products is a Linux system with CGI scripts that form the web interface. It turned out that the password 519070 provides access to image viewing and system settings of all cameras. However, such firmware with an insecure connection to the backend are common .
Hacking cameras

Inside one of the Google data centers,
Cloud-based video surveillance services are not affected by the vulnerabilities of previous-generation systems. For a cloud solution without port forwarding, configuring a firewall is usually not required. Any Internet connection is suitable for connecting to Ivideon Cloud and does not require a static IP address.
For all devices with the Ivideon service, a password is randomly generated when connecting cameras in your account. For some camera models, for example, Nobelic , you can create your own password in your Ivideon user account.
We do not store user passwords, so you cannot access them. We do not store video archives centrally. They are distributed between many machines in different data centers.
Access to the mobile application is protected by a PIN code, and biometric protection will appear in the future.
Also, the cloud service automatically sends patches and security updates via the Internet to any local user device. The end user is not required to take any additional steps to monitor security.
In Ivideon, many functions (except for the cloud archive and video analytics modules) and all security updates for all clients are provided for free.
We hope that these simple rules will be used in all cloud surveillance services.
