Access control and what it is eaten with
Increasingly, issues regarding information security are brewing in the IT world. Indeed, the World Wide Web has become a global platform for the exchange and storage of information, and the word Internet is familiar to everyone. In the modern world, it is difficult to find a company that would not use Internet technologies: all kinds of applications, gadgets, IOT devices - all this is at risk. Therefore, we will talk about the basics of information security, namely, access control.

I would like to discuss some seemingly obvious aspects of information security. Ironically, many underestimate the importance of security or consider their measures sufficient. It is worth recalling the Dunning-Krueger effectthe essence of which is that people with low qualifications in a certain field make erroneous conclusions. Hence the unsuccessful decisions in business that they are not able to realize. Information security - this is an area in which it is not permissible to assume anything and act on the principle of "if only to do for the species." Information security should be the ultimate goal, a lever in the business that minimizes losses and expenses, and protects your data. The greatest danger to the company is the human factor. Indeed, thanks to the clever manipulation of an employee, an attacker is able to compromise your system. Unfortunately, there is a misconception that if you have strong technical protection (all kinds of IDS, antifraud systems, antiviruses, DLP, firewalls), then your business is safe, but this is not so. Our psychology is predictable, and in most cases, our impulses are triggered by fear and rash actions. Take, for example, banal attacks through the mail: the employee received a letter stating that some system where he is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control. that a certain system where it is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control. that a certain system where it is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control.
Any task is best viewed from a different angle, this also applies to access control: installing antiviruses and other means of protection is not enough. From logical reasoning, as an option, the following formula emerges: A good access control system = administrative measures + technical measures + physical protection.
What is included in administrative measures? Yes, everything is very simple! This is the correct organization of documentation in the information security management system. A good security policy, risk assessment methodologies, internal audits, procedures, staff training - all this contributes to the proper organization of security in business.
In the Security Policy, it is most important to reflect the goals of the company and the scope (which units this policy covers), and also take into account the requirements of the business, partners and customers. The company should identify information assets, and those assets that require more careful handling should be classified by significance and value. To determine who has access to assets and is responsible for the implementation of information security measures, you can use the role table (the table indicates the roles and who is responsible for what is allocated). Another important stage is training: invite specialists or hire those who will tell your employees about network security rules (for example: what phishing is, how to recognize it, how to crack a social engineer and which site is safe). These are very important aspects, because it is the human factor that is the most vulnerable link. Internal audits will help you identify the shortcomings of your information security management system, determine which departments are vulnerable and which departments need advanced training, and understand whether the requirements specified in the Policy are being followed. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks. to determine which departments are vulnerable and which units need advanced training, to understand whether the requirements prescribed in the Policy are complied with. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks. to determine which departments are vulnerable and which units need advanced training, to understand whether the requirements prescribed in the Policy are complied with. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks.
By hardware, we attribute various software and hardware, information security services. It can be password systems, firewalls, security scanners, secure protocols, operating systems, and so on. Extremely carefully you need to be with password systems. Since they are always under the scrutiny of attackers, they are most at risk. Communicating with a huge number of people, I noticed how easy and negligent they are to password protection (they come up with simple passwords, store them in accessible places), not realizing that an attacker can easily crack them. For example, take a type of attack such as brute force (which means brute force passwords). Suppose you didn’t really fantasize about your password and took a common hacker, meanwhile, knowing your mail, using various dictionaries will find a match and compromise your system. Everything is simple! It is also worth remembering and reminding employees about phishing emails: do not open links and enter a password, take a breath and figure it out.

Well, the third is physical protection: locks, special protection, video cameras, access systems, and so on.
I also want to focus on three access control methods. If your work is connected with sensitive data and sensitive information, state secrets, then you should pay attention to the mandatory access control method. The peculiarity of this method lies in its hierarchy, since employees and objects (files, documents, etc.) are assigned a certain hierarchical level of security. The security level of an object characterizes its value and, in accordance with the level, a security label is assigned to it.
The level of security characterizes the degree of trust in the employee, as well as his responsibility for this information. The operating system assigns certain attributes to the employee, thanks to which the employee is granted access within the framework of his official powers. Consider the following example, let's say we have several access levels:
We also have users who have different levels of access to the above information:
Let us imagine the structure of our system in the form of the following diagram, where RW - read and write rights, R - read rights, W - write rights:
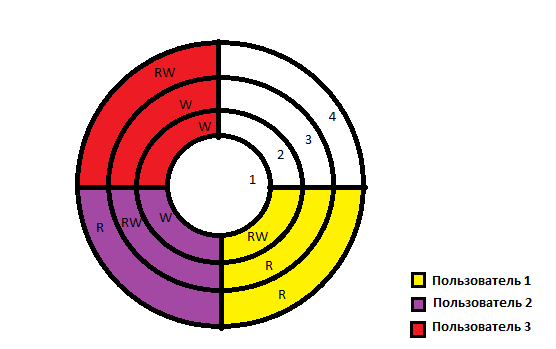
From the diagram it follows that:
User 1 has the right to read and write objects intended for working with classified information, as well as the right to read objects with limited and free information.
User 2 has the right to read and write objects belonging to the restricted access information, and also has the right to read objects with free access information and the right to write objects with secret information.
User 3: has the rights to read and write objects with free access information, as well as the right to write objects with limited access and secret information.
But all users are denied access to objects with top secret information.
The simplest method is considered discretionary, which is considered quite common. The essence of access is simple: the owner of the object decides to whom to grant access and in what form (reading, writing, etc.). The method can be implemented using access lists or an access matrix, but you need to consider that an employee with certain rights can transfer your object to another for use without notifying you. Therefore, if you are working with important information, you should be wary of this method.
Next, let's talk about the role-based access control method. The essence of this method is simple: between users of the system and their privileges intermediate entities appear, which are called roles. The method assumes that for each user several roles can be assigned, providing access to the necessary information. This method eliminates the abuse of rights, because it implements the principle of least privilege.
It provides only that level of access to an employee that falls within his area of responsibility. Also, this method implements the principle of separation of duties, which simplifies the management of information assets. The disadvantage of this method is that it is difficult to implement when there are a huge number of users and roles, since it is costly.
There are other methods, but talked about the most key. All of the above methods of organizing access are an important step in the security of your company and therefore it is worth paying close attention to them.

I would like to discuss some seemingly obvious aspects of information security. Ironically, many underestimate the importance of security or consider their measures sufficient. It is worth recalling the Dunning-Krueger effectthe essence of which is that people with low qualifications in a certain field make erroneous conclusions. Hence the unsuccessful decisions in business that they are not able to realize. Information security - this is an area in which it is not permissible to assume anything and act on the principle of "if only to do for the species." Information security should be the ultimate goal, a lever in the business that minimizes losses and expenses, and protects your data. The greatest danger to the company is the human factor. Indeed, thanks to the clever manipulation of an employee, an attacker is able to compromise your system. Unfortunately, there is a misconception that if you have strong technical protection (all kinds of IDS, antifraud systems, antiviruses, DLP, firewalls), then your business is safe, but this is not so. Our psychology is predictable, and in most cases, our impulses are triggered by fear and rash actions. Take, for example, banal attacks through the mail: the employee received a letter stating that some system where he is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control. that a certain system where it is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control. that a certain system where it is registered is compromised. This news will certainly scare him, and with a greater likelihood he will follow the link, giving his data to attackers. Therefore, it is important to configure access correctly and improve the skills of employees in information security. A whole “science” is devoted to this topic - social engineering, but about this sometime next time, and today we’ll talk about organizing access control.
Any task is best viewed from a different angle, this also applies to access control: installing antiviruses and other means of protection is not enough. From logical reasoning, as an option, the following formula emerges: A good access control system = administrative measures + technical measures + physical protection.
What is included in administrative measures? Yes, everything is very simple! This is the correct organization of documentation in the information security management system. A good security policy, risk assessment methodologies, internal audits, procedures, staff training - all this contributes to the proper organization of security in business.
In the Security Policy, it is most important to reflect the goals of the company and the scope (which units this policy covers), and also take into account the requirements of the business, partners and customers. The company should identify information assets, and those assets that require more careful handling should be classified by significance and value. To determine who has access to assets and is responsible for the implementation of information security measures, you can use the role table (the table indicates the roles and who is responsible for what is allocated). Another important stage is training: invite specialists or hire those who will tell your employees about network security rules (for example: what phishing is, how to recognize it, how to crack a social engineer and which site is safe). These are very important aspects, because it is the human factor that is the most vulnerable link. Internal audits will help you identify the shortcomings of your information security management system, determine which departments are vulnerable and which departments need advanced training, and understand whether the requirements specified in the Policy are being followed. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks. to determine which departments are vulnerable and which units need advanced training, to understand whether the requirements prescribed in the Policy are complied with. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks. to determine which departments are vulnerable and which units need advanced training, to understand whether the requirements prescribed in the Policy are complied with. It is important to choose a competent auditor who will carefully check the condition of your system for compliance with the rules. Thanks to the risk assessment methodology, you can calculate the probability of certain threats, as well as detect existing ones and choose further actions with regard to risks.
By hardware, we attribute various software and hardware, information security services. It can be password systems, firewalls, security scanners, secure protocols, operating systems, and so on. Extremely carefully you need to be with password systems. Since they are always under the scrutiny of attackers, they are most at risk. Communicating with a huge number of people, I noticed how easy and negligent they are to password protection (they come up with simple passwords, store them in accessible places), not realizing that an attacker can easily crack them. For example, take a type of attack such as brute force (which means brute force passwords). Suppose you didn’t really fantasize about your password and took a common hacker, meanwhile, knowing your mail, using various dictionaries will find a match and compromise your system. Everything is simple! It is also worth remembering and reminding employees about phishing emails: do not open links and enter a password, take a breath and figure it out.

Well, the third is physical protection: locks, special protection, video cameras, access systems, and so on.
I also want to focus on three access control methods. If your work is connected with sensitive data and sensitive information, state secrets, then you should pay attention to the mandatory access control method. The peculiarity of this method lies in its hierarchy, since employees and objects (files, documents, etc.) are assigned a certain hierarchical level of security. The security level of an object characterizes its value and, in accordance with the level, a security label is assigned to it.
The level of security characterizes the degree of trust in the employee, as well as his responsibility for this information. The operating system assigns certain attributes to the employee, thanks to which the employee is granted access within the framework of his official powers. Consider the following example, let's say we have several access levels:
- Top secret information (access denied);
- Secret information;
- Restricted access information;
- Free access information.
We also have users who have different levels of access to the above information:
- User 1 - works with classified information;
- User 2 - works with information of limited access;
- User 3 - works with free access information.
Let us imagine the structure of our system in the form of the following diagram, where RW - read and write rights, R - read rights, W - write rights:

From the diagram it follows that:
User 1 has the right to read and write objects intended for working with classified information, as well as the right to read objects with limited and free information.
User 2 has the right to read and write objects belonging to the restricted access information, and also has the right to read objects with free access information and the right to write objects with secret information.
User 3: has the rights to read and write objects with free access information, as well as the right to write objects with limited access and secret information.
But all users are denied access to objects with top secret information.
The simplest method is considered discretionary, which is considered quite common. The essence of access is simple: the owner of the object decides to whom to grant access and in what form (reading, writing, etc.). The method can be implemented using access lists or an access matrix, but you need to consider that an employee with certain rights can transfer your object to another for use without notifying you. Therefore, if you are working with important information, you should be wary of this method.
Next, let's talk about the role-based access control method. The essence of this method is simple: between users of the system and their privileges intermediate entities appear, which are called roles. The method assumes that for each user several roles can be assigned, providing access to the necessary information. This method eliminates the abuse of rights, because it implements the principle of least privilege.
It provides only that level of access to an employee that falls within his area of responsibility. Also, this method implements the principle of separation of duties, which simplifies the management of information assets. The disadvantage of this method is that it is difficult to implement when there are a huge number of users and roles, since it is costly.
There are other methods, but talked about the most key. All of the above methods of organizing access are an important step in the security of your company and therefore it is worth paying close attention to them.
