Security Week 14: RSA Conference, Leaky Ad Networks, Alliances, and Confrontations
 Last week, the twenty-seventh RSA Conference was held in San Francisco. Until the early 2000s, this event could be described as a highly specialized cryptography party, but gradually the business content almost completely replaced the technical one. Not everyone liked this format of an information security event. Throughout the week on Twitter, caustic comments by technical experts slipped through, such as “RSA is as productive as possible if you lock yourself in a hotel room and work.”
Last week, the twenty-seventh RSA Conference was held in San Francisco. Until the early 2000s, this event could be described as a highly specialized cryptography party, but gradually the business content almost completely replaced the technical one. Not everyone liked this format of an information security event. Throughout the week on Twitter, caustic comments by technical experts slipped through, such as “RSA is as productive as possible if you lock yourself in a hotel room and work.”RSA is really a hangout of managers, and it doesn’t matter on whose part - a provider of security solutions or a client company. They say about cyber defense "at a high level," in general terms, sometimes foggy and vague. On the whole, one can understand why techies are so bombed by formulations such as “inclusive diversification in building a new information security paradigm”. But there is nothing good in trying to divide the near-IB community into “ours” and “yours”. Firstly, there are too many dividers in our life. Secondly, the information technology industry (if you recall the same scandal around Facebook) is faced with problems that, unfortunately, have no technical solution. Let's try to show with examples.
A typical, spherical in a vacuum RSA conference follows the following pattern: some fresh technical trend is selected by the main topic of the event, keynote addresses by the most important guests (read, platinum sponsors) are built around it. This year the template broke: the number and complexity of attacks are growing, but to talk about it without immediately offering at least some kind of product for protection, and preferably from all attacks at once, does not comply with generally accepted business practices. And there is no solution to all the problems on a global scale at once. On the very first day of the conference, obvious but unconventional words for business sounded: that there are no silver bullets (= universal pills for cybercrime), that there is a huge gap between the market's demand for information security specialists and their presence.
Come on? No, the approach “in order for something to work, you have to work hard and hard” is generally correct, but it was somehow unexpected to hear it at the RSA Conference. Even two years ago,almost the same people buzzed cheerfully about the incredible advantages of IoT and bottomless security failures, to which either machines were already screwed, or blockchain, or nekstgen, and that very soon everything would be fine. And here it is. I suppose that the source of such a wind of change is in the mood of corporate clients who are tired of hearing about another terrible APT in the absence of any sane counteraction plan. It’s time to already talk about solutions, and this wish also applies to techies who usually seek only problems. At least in the conference infrastructure itself: on the fourth day of the RSA Conference, someone discovered the base of a proprietary mobile application on the contractor’s servers in the public domain.

To be precise, not all user data has leaked. And not necessarily users. But something was not as well protected as we would like.
Nevertheless, technical trends, although modestly, were outlined. This is data encryption wherever possible, including those that are idle and seem to have not given up to anyone. The reason for this is the big data processing methods and the correlation efficiency when a truck of non-essential inputs is processed into information that is really dangerous in case of a leak. Machine learning in this context is no longer regarded as a healing powder that will save everyone, but also as an attack tool. This is also the further automation of event monitoring systems in the corporate network - not for the sake of beautiful schedules (although for them too), but just to free up the time of living specialists for something more useful.
Almost all
Microsoft’s second major announcement was the creation of the Cybersecurity Tech Accord alliance of 34 companies, including Cisco, Facebook, HP Enterprise and Trend Micro ( news) The alliance was created to reduce the damage from cyber warfare to “civilians and companies” - its members committed themselves not to help states develop cyber weapons and protect clients around the world from complex cyber attacks. In a sense, this is an initiative in the style of “Bees against smoking in public places”: a worthy goal, no doubt, but what does the bee have to do with it? But here we return to the beginning of the opus: any attempt to unite with a good goal is good news. The efficiency of such associations may be small, but in relations between people and in politics it is always so, in contrast to technology.

Millions of mobile applications send personal data in clear text
News . Research .
One of Kaspersky Lab's presentations on RSA was devoted to the security of personal data in mobile applications, or rather, not even in the app itself, but in the ad networks to which these applications access. Lab’s expert Roman Unuchek found that many applications send in clear text, without encryption, sensitive enough data, such as geolocation:

At the same time, they communicate with their servers via HTTPS. The problem is that the integration of advertising modules (for displaying banners and other things) is often done using the copy-paste method, and in some cases this “additional” functionality takes from 75% to 90% of the application code. Since 2014, the Lab has run a giant sandbox for mobile applications, which analyzes the network activity of 13 million app. Of these, as it turned out, about 4 million communicate with someone over the insecure HTTP protocol. Further analysis of the most common advertising modules revealed an interesting picture: some advertising networks provide the ability to exchange information via HTTPS, but not all developers spend time finding the right code. In other networks, there is no way to forward data using encryption.
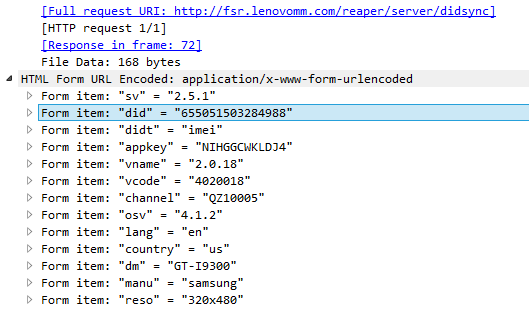
The problem, however, is not only in ad networks. A number of applications send HTTP information to their own backend, including passwords:
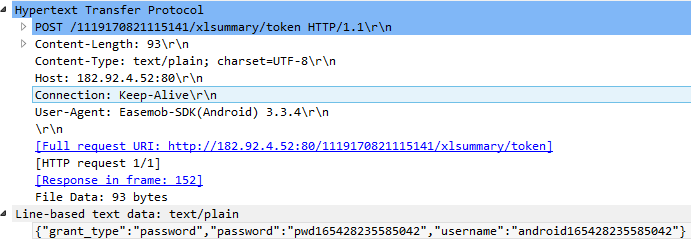
This study is a good example of how you can increase the security of a large number of users with a little effort. Users also have nothing to recommend, except for the widespread use of VPN. Do not carry a separate phone without a SIM and GPS, and only for app?
Finish with a small offtopic. Arstechnica published yesterdayinteresting material about the ongoing problems with the production of the Tesla 3 mass electric car. It states that Elon Musk overestimated the possibilities of automating production and thus repeated the mistake made by classical automakers in the 80s of the last century. Then, too, an attempt was made to automate everything in general, and also failed. Robots are important, but you can't do without people. Perhaps the same thing can be said about the information security industry: you can automate the routine, but some new ideas require human talent. At least for today it is. And even if at an RSA conference, which tends to exaggerate the possibilities of technical innovations, this is recognized at the highest level, then this is good news.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
