How to recover a lost archive password using a video card

Good afternoon, Habrasociety!
It so happened that I needed to pick up the lost password for the 7zip archive, which contained a backup copy of several files from the old disk. I lost my password a long time ago, and the process of recovering it took some effort and turned out to be a rather interesting affair. I’ll tell you more about this in the article.
What is a password?
Since the developers realized that it is unsafe to store a password in text, we only see a hash - a set of values that are generated based on the password. Such a conversion is performed by a hash function according to a given algorithm and is one-way.
There are different hashing algorithms: MD5, SHA-1, SHA-2 and others. To recover the password from the hash, you can use the brute force method. It is enough for us to create a hash for each possible password and compare it with that hash which needs to be decrypted. In fact, we need to take the file, extract the hash from it and decrypt it with the cracker program. The method of hash extraction for each algorithm is different, and the complexity of iterating over each of them varies.
How to calculate search complexity? Without going deep into the intricate matan, we can say that it depends both on the length of the password and on the set of characters used in it:
for example, the numeric password 0-9 contains 10 characters. The five-digit password contains m = 5 characters. The number of combinations will be P = m ^ n or 5 to the power of 10 - 9765625.
If we take into account the Latin characters - large and small, then this is 26 * 2 + 10 = 62 and our P is already 5 to the power of 62!
I saw how over the course of a week using two 22-core Xeon they restore the password to zip. Neither such resources nor so much time for password selection I had and thought about using a graphic chip for my own purposes. The computing power of these devices is now widely known. Graphics accelerator manufacturers are AMD and Nvidia. Nvidia has CUDA - its own closed API for computing on the GPU, which, according to synthetic tests, is 20% faster than the open analog of OpenCL, but not every program has an SDK for it . In addition, Nvidia cards are inferior to AMD cards in calculations implemented on OpenCL. This problem is partially treated by fresh drivers, but the gap still remains. In the end, we also run into the number of computing units of the video card.
Below I will consider a Hashchat solution that runs on OpenCL and allows you to connect up to 128 video cards at the same time. Although there is no such possibility for this test, it presumably makes sense to give preference to the middle price segment, since you can put more cards and the difference in performance is disproportionate to the price.
Password Recovery Tools
Hashcat is the successor to previously used oclHashcat / cudaHashcat utilities. It is declared as the fastest tool for selecting a lost password. Starting with version 3.0, it supports the use of both CPU and GPU, but not for all algorithms. For example, using the GPU, you can’t find the password for Bcrypt. But for MD5 and SHA-1 passwords are selected quite quickly. Works with over 200 hashes. In fact, it is a universal cross-platform solution.
To get some of them, you will need the utility below:
John The Ripper- Administrator tool for recovering lost passwords - the legendary hack software utility. Popular due to the support of a large number of hashes and their auto-recognition. It supports many modules, including third-party ones. John The Ripper is even included in Kali Linux, but in a truncated form. Only with this program I found absolutely necessary extensions for extracting hashes from other formats: zip2john, rar2john, pdf2john.py, pfx2john.exe and much more.
Cain & Abel - also needs no introduction. The program even has its own sniffer.
There are other tools, however, they are either poorly documented and do not have a GUI, or they are inferior in speed. Support for different types of hashes is also important. Thus, we stop at Hashcat.
As an example, we use a custom 7zip archive. We generate the archive ourselves. 7zip uses the AES256 algorithm.
To restore the hash, we use the 7z2hashcat utility. This is actually a Perl script. Download it from the link and unpack it.
7z2hashcat64-1.2 7z.7z > hash.txtAs a result, we will see the desired hash in the text file. Next, configure our Hashcat:
- We put the product itself
- We put GUI at will and for acquaintance with the program.
- We go to the hashkiller - and take away the HashcatGUI from there.
- We go into the folder with HashcatGUI, run App.HashcatGUI.exe.
- When starting, specify the executable file of the hashcat64.exe or hashcat32.exe program , depending on the bit depth of the system
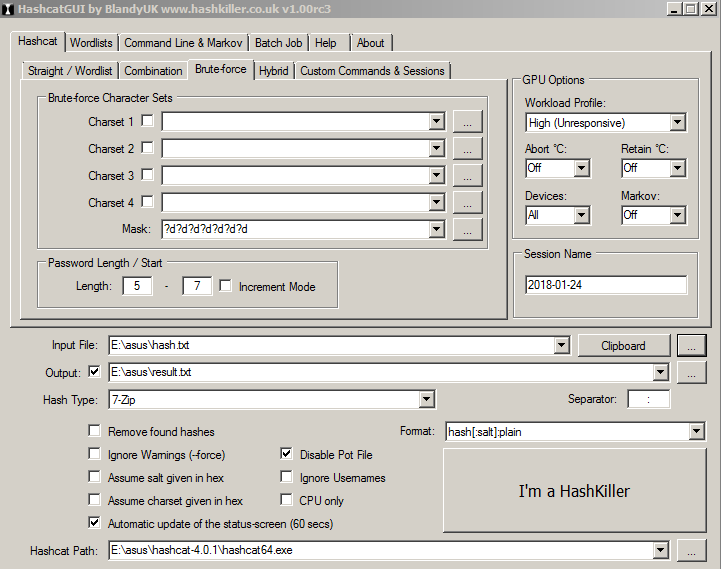
The GUI sometimes throws errors and crashes when the search is completed. Nevertheless, the checkpoint is provided, we can return to the last running session and continue the search in the Custom commands & Services tab.
Hashcat will detect all the GPU / CPU devices in the computer and begin decryption.
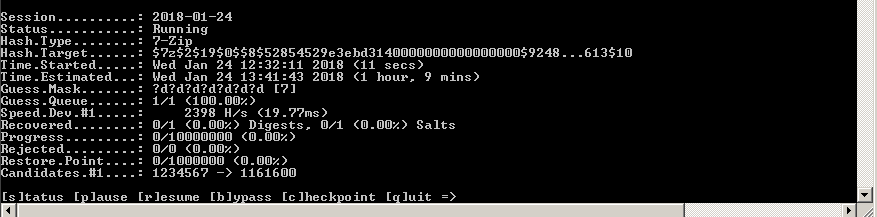
Testing the features of the program
Launch Hashchat. Specify the hash type as m 11600 (7zip), update the search status every 60 seconds, the output file and mask for the search.
Search by mask is positioned as an improved version of brute force. Knowing something about the password pattern, we can significantly speed up the search. Suppose this is a date, name or year, or any intended characters, for example,? R? R? R - any three characters of the Russian alphabet.
In this case, it is any seven digits. It should be borne in mind that if the password is six digits long, then we will not find it and you need to try again. To automate the process, a tick "increment" is provided.
hashcat64.exe -a 3 --session=2018-01-24 -m 11600 -w 3 --status --status-timer=60 --potfile-disable -p : --gpu-temp-disable -o "E:\asus\result.txt" --outfile-format=3"E:\asus\hash.txt" ?d?d?d?d?d?d?dBottom line: in the file E: \ asus \ result.txt . Password 3332221 is picked up in about 10 seconds.
We are trying to increase the password length. The search speed has fallen noticeably - to 635 passwords per second.
Result: password 3334566611 - 10 characters. It took about three minutes to recover.
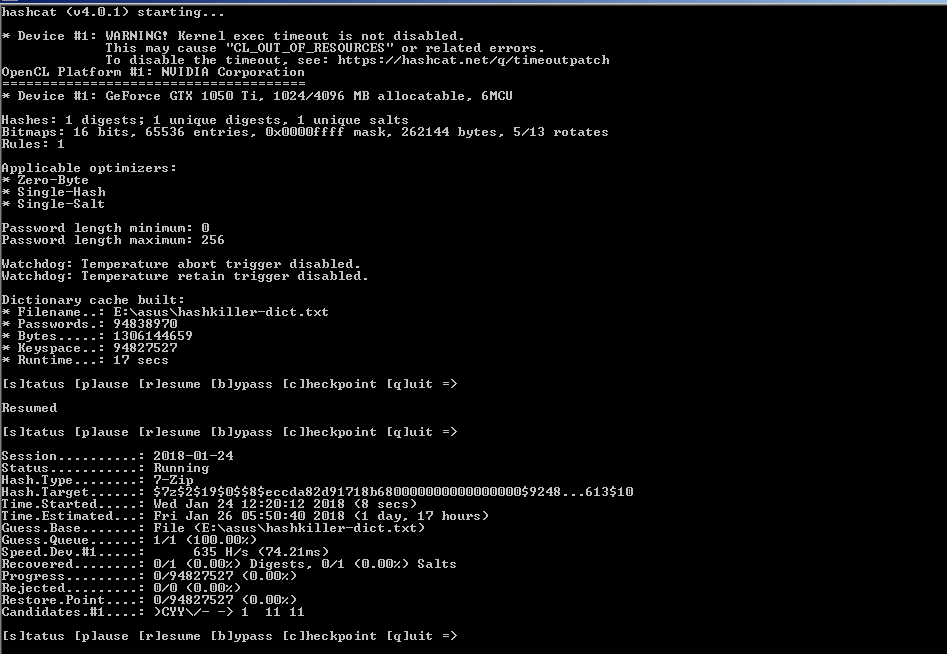
Let's complicate the task. Password now consists of latin letters and numbers. The password has grown to 11 characters. The program has a number of options that even accelerate the selection. The obvious option is to use the base of standard passwords using the database.
We put the dictionary HashKiller Passwords. There is already an example in the program folder - there are 1000 words that way. We add our dictionary in the “Wordlists & Markov” tab. Download the HashKiller Passwords dictionary, and then extract it, for example, into the Dict folder.
Launch Example:
hashcat64.exe -a 0 --session=2018-01-24 -m 11600 -w 3 --status --status-timer=60 --potfile-disable -p : --gpu-temp-disable -o "E:\asus\result.txt" --outfile-format=3"E:\asus\hash.txt""E:\asus\hashkiller-dict.txt"
Markov is another combination option and has a separate executable. https://ru.wikipedia.org/wiki/Markova_Chain
The option is poorly documented. In the GUI help, the value 40 is recommended for typing? D? L? U (Latin letters and numbers).
We also use a hybrid attack. This is a search for a word from a dictionary with the addition of a mask ending, for example, Password113 , Qwe1235 .
Also in the program there are ready-made masks in the .hcmask format, which allow you to iterate over well-known patterns line by line. Extra lines can be commented on by opening this file with Notepad. They can also be used with the “increment” option, or combined with a list of words.
In addition to hybrid attacks, the program supports the selection rules for certain algorithms identified empirically, which give good results.
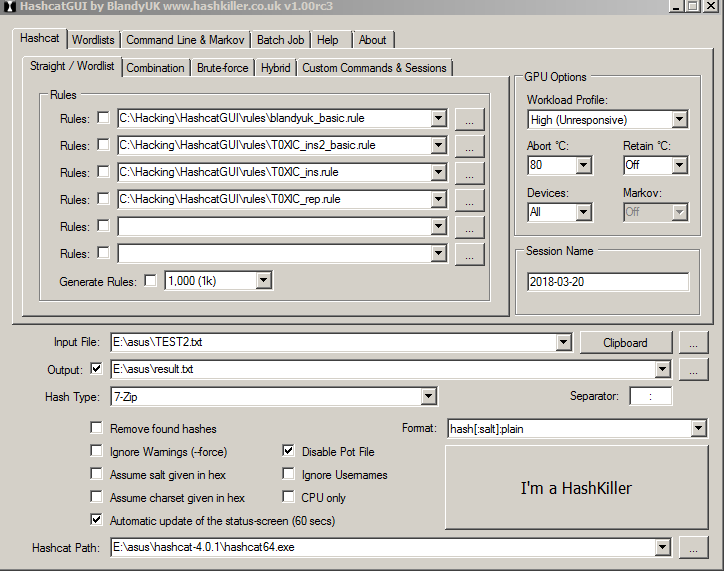
The so-called rule-searching is the most technically complex attack and is a programming language. According to the developers, this approach is faster than regular expressions. Ready-made rules can already be used by loading them into the GUI from the rules directory in Hashchat. Given these options, the program produced a result in 2.5 hours.
Password Property123
Rainbow tables
In the example, we have a rather complicated encryption algorithm. If you pick, for example, a hash to MD5 in a reasonable amount of time, and your password has not been picked up, it makes sense to pay attention to the last argument - rainbow tables. These are estimated hash values for all common passwords that have been counted and stored in a conditional table. Knowing the hashing algorithm, you can load the table into memory and search for the desired hash. Usually they are used to select a large number of passwords in the shortest possible time, for example, all leaked passwords for a web application, but this is another story.
Today, there are two projects supporting various types of hashes:
- Rainbowcrack - supports four hash algorithms: LN / NTLM, MD5 and SHA-1
- rcracki_mt or rcracki for Linux - MD4, MD5, DoubleMD5, SHA1, RIPEMD160, MSCACHE, MySQL323, MySQLSHA1, PIX, LMCHALL, HALFLMCHALL, NTLMCHALL, ORACLE
Conclusion
Without great computing resources, today you can still decrypt even very persistent types of hashes. Given their wide distribution as a standard, at the moment, many applications are a priori vulnerable. Perhaps in the near future we are expected to switch to such standards as SHA-2 or GOST_R_34.11-2012. In the meantime, it remains only to use the general recommendations for generating passwords:
- Do not use common words from daily use. There are only a few thousand of them.
- Do not use words followed by numbers or letter rows on the keyboard. Adding 1231231 to Qwerty will not make your password more secure. The entire dictionary and masks can be sorted out in half a day.
- Standard combinations of doubling words, etc. easily understood by the selection rules that are focused on such techniques.
- Do not use personal information. There is too much public information in our world.
