How to assess the profitability of implementing an expensive system and justify the budget to management
- We should buy a cow ...
- We should, but where can we get the money?
“Three from Prostokvashino”

In order for your conversation with the management about the necessity of the implementation project not to come down to this short dialogue from the cartoon, you need to prepare an argument in advance. For many years we have been engaged in the implementation of access control systems (IdM), and during this time, communicating with customers, we heard about a variety of methods to justify budgets. Today we put these life hacks in one article. Under the cat - a step-by-step guide and examples of formulas for calculating the payback period, improving operational efficiency and total system ownership costs. All this is considered on the example of IdM implementation, but the general principles are applicable to almost any IT system.
Any justification should include the expected benefits of the implementation, presented in the form of specific figures. In the case of IdM, it can rely on one or more criteria from the following list:
If the process of justifying budgets in a company is not very rigidly formalized, general considerations may be sufficient for coordination. But usually, management still requires translating everything into a cash equivalent and marking the time it takes to pay back.
Let's take a closer look at what benefits you can rely on to justify the IdM implementation project and when / how to use them.
Improving performance indicators
IdM implementation can indeed improve many performance indicators. For example, reduce the flow of applications for manual provision of access to employees and speed up their execution. Reduce the time and effort required to prepare data for auditors or information security services. Minimize the number of requests for technical support regarding the status of access requests.
To assess the increase in operating efficiency, indicators such as are commonly used:
When justifying through the improvement of performance indicators, it is important that these indicators are meaningful, so that they have a clear impact on business processes. For example, with a large staff turnover, it will be critical to shorten the term for issuing credentials and shorten the downtime of a new employee.
The easiest thing in financial metrics is to translate the improvement in performance indicators after the implementation of the system. Accordingly, it is necessary to calculate how much “it costs” to provide access before the introduction of IdM and how much - after.
Calculating the cost of access control before implementing IdM
We will consider the principles of calculation on a theoretical example, but, of course, when justifying the budget, you should use indicators that describe the realities of a particular organization. Suppose a company has 10,000 employees. To estimate the cost of access control, we use two indicators:
Here you can also take into account the “cost” of auditing and revising employees ’access rights to information systems, but these are more specific needs that not every organization has, so for simplicity we’ll leave them behind the scenes.
Employee downtime
losses To estimate employee downtime losses, we use a staff turnover indicator that reflects the average percentage of employees who leave the company during the year and who will need to be replaced by new staff. This will give us the average number of new employees per year who will need to provide access to information resources so that they can fully carry out their work.
Depending on the industry of the company and the type of activity of specific specialists, the level of turnover can vary significantly.
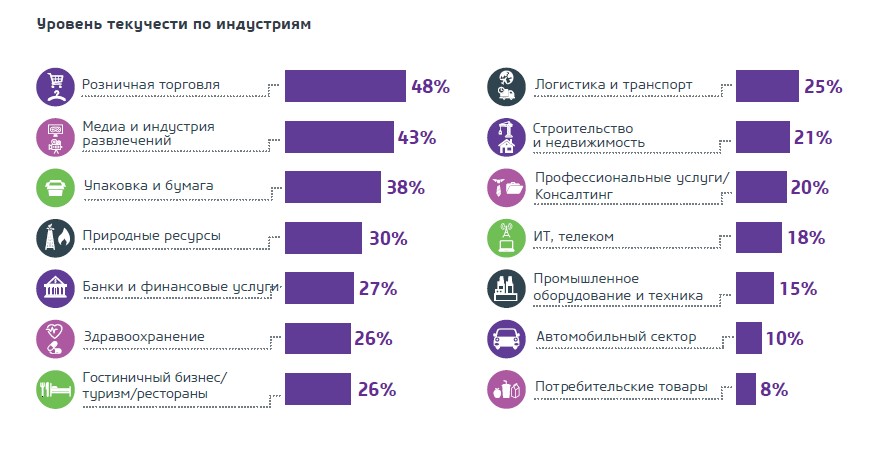
Statistics recruitment company Antal Russia
Suppose our company works in the field of logistics, and staff turnover is 25%. Therefore, we have to grant access rights to 2500 new employees a year.
In the next step, we will need to calculate the average time during which new employees are granted access to the IS. Depending on the size of the organization and the availability of a regional network, this figure can vary from 1 day to 2 weeks. In our experience, the average for the market is 3 working days, so we will use it.
Next, we need to estimate the amount of company losses from the downtime of one employee. Here, as they say, everything is very individual. The volume of losses can be highly dependent on the scope of the company, and on the region of presence, and on the size of the enterprise, and even on the position of the employee. For example, for a technical support employee, the lack of access to information systems is fraught with one hundred percent downtime. And the effectiveness of the work of the ACS manager, who can ensure the vital activity of the enterprise in many respects without the use of IP, the lack of access, of course, will not affect so dramatically. So that we are not accused of excesses on the ground, we take for our calculations an average of 50%.
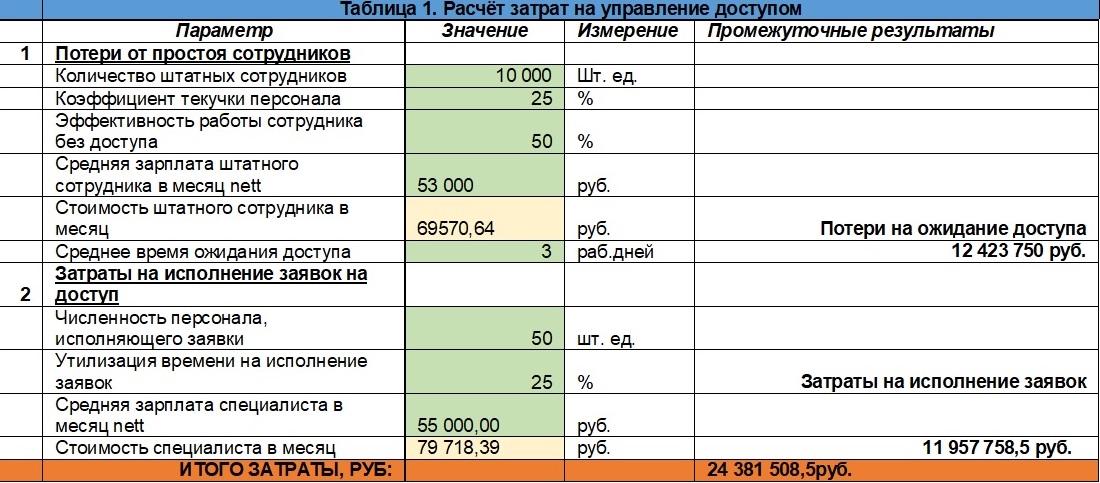
To calculate losses from idle employees in the process of waiting for the necessary rights, it will also be necessary to determine the average “employee cost” for the organization without taking into account bonuses and overhead costs. In our example, this is 69570.64 rubles. In a month, an average of 20-21 working days, that is, the cost of employee remuneration is on average about 3,313 rubles per day.
So we count. Above, we have indicated that the granting of access rights takes 3 working days, during which the employee works with 50% efficiency. That is, 3,747 * 3 * 0.5 = 4969.5 rubles. the company is losing due to the downtime of one new employee. There are 2500 of them in a year, that is 12423 750 rubles in total.
Costs for the execution of applications for access
To estimate the costs for the execution of applications for access, we use the following indicators:
Based on the national average salary of the gross of such a specialist (79,718.39 rubles), we find that the company spends 79,718.39 * 12 * 50 * 0.25 = 11,957,758.5 rubles per year to execute applications.
Alternatively, the average number of requests (often this information can be obtained from the Service Desk system), the average execution time of an application and estimate the actual time spent on their execution can be taken as the basis for calculations. In this case, the calculations should be made separately for each type of system, since they can vary greatly. For example, providing access to Active Directory takes 5-10 minutes, but this type of access is required for all company employees. It may take 20-30 minutes to provide access to the SAP landscape, but not everyone needs such access.
As a result, we get some estimate of these costs. In our calculation, it amounted to a little more than 26 million rubles (see table 1).
Calculating the cost of access control after the implementation of IdM
Next, to estimate the payback period of the project, it will be necessary to compare the amount received with the assessment of similar costs after the implementation of IdM, plus the cost of directly implementing and maintaining the system.
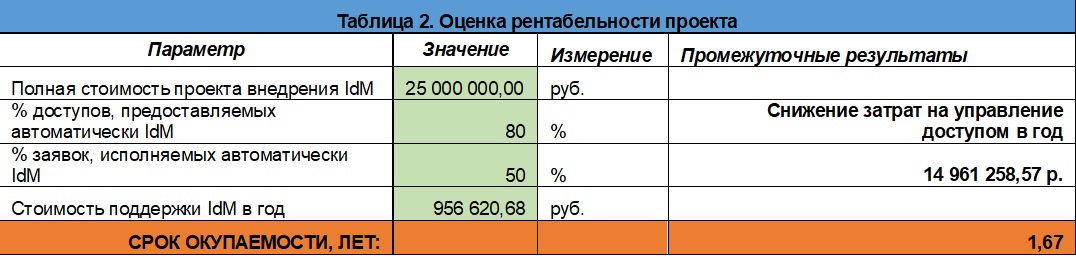
The cost of implementing IdM for a particular company will be considered by you as a vendor or integrator. According to our estimates, the introduction of IdM-system in an enterprise with a staff of 10,000 employees on average will cost the company 25 million rubles. excluding annual technical support.
And now let's estimate how our costs will change after the introduction of IdM.
First, we calculate the percentage of access rights that the IdM system will provide to employees. As a rule, if an organization has some basic set of authority that is assigned to employees when they are hired, IdM automatically provides them. But let's even assume that IdM does not provide the entire basic set, but only 80%. If a year the company lost 12,423,750 rubles. due to downtime of employees waiting for access rights, now this amount is reduced by 80% and amounts to 2,484,750 rubles.
Now let's estimate what percentage of applications the IdM system can execute automatically, without human intervention. By experience, you can automate all 100% of applications for access to the system, if it is connected to the IdM through a connector. However, this requires a lot of work to create a catalog of functional powers of each full-time role, so in reality, the average percentage of automatically executed applications is lower - also at about 80%. Let us make an amendment that not all information systems will be connected to IdM via connectors, and we will lower this figure to 50%. Accordingly, the cost of providing access will decrease from 11,957,758.5 rubles. up to 5,978,879.25 rubles.
So, after the introduction of IdM, the same processes related to access control will cost the company 15,917,879.25 rubles cheaper per year. and amount to 8,463,629.25 rubles. But at the same time they will add the cost of technical support. Suppose a company allocates an individual employee for this task. The cost of the specialist’s work is taken from table 1 (calculation of the cost of access control) 79 718,39 rub. It turns out that a year it will take about 956,620.68 rubles to support IdM. and the total costs will be 9 420 249.93 rubles.
As a result, when the cost of implementing the system is 25 million rubles, the allocation of one specialist to support the system, 80% automated issuance of rights for recruitment and 50% of applications for access for the company as a whole, the payback period from the moment the system is commissioned will be a little over one and a half years (see table 2).
Sometimes analytical reports are used for this kind of substantiation, mainly coming from the pen of foreign analysts. They provide some figures on the effectiveness of system implementation. For example, reports promise that IT staff’s time savings using IdM will be 14%, the number of support calls related to access will decrease by 52%, and the number of unnecessary accounts will decrease by 10%. Unfortunately, these figures do not always reflect Russian realities.
Reducing the risk of incidents
The introduction of IdM allows you to reduce a number of information security risks or to ensure the timely detection of relevant incidents:
Often, when justifying the implementation of a system through information security risks, it is crucial for management to determine whether similar incidents occurred earlier. (And if not, then why defend against these risks?) Well, as one distinguished head of information security likes to say, such people can be advised not to put the lock on the door - since they have not been robbed before!
However, as practice shows, such incidents happen from time to time, and the effect of them can be quite tangible. In our practice, there was a case when a bank branch was idle for several days due to the fact that an employee “caught” a virus that encrypted critical data on behalf of his account, to which an employee should not have access at all. In this case, the damage is relatively simply translated into rubles, but this is not the case with all information security incidents related to access rights violations.
What are the risks of information security can reduce IdM-system? Examples include:
In general, in the matter of substantiation through IS, the attitude of business to information security is of fundamental importance. Somewhere it is treated as a formal function, somewhere - as a business critical. If information security is not essential for business, then it is better to justify the introduction through other articles.
Meeting the requirements of regulators / standards
This block of justifications is relevant for organizations that fall under the requirements of external regulators - for example, the Central Bank of the Russian Federation, or internal - for example, the parent organization that sets the standards of activity. The first, including organizations that are traded on the stock exchange.
The implementation of IdM allows you to meet the requirements for access control in accordance with standards such as STO BR, PCI DSS, SoX, ISO 27001 and others. Often, these requirements are closed by organizational measures, but often large organizations that undergo external audits are advised on the use of IdM class systems to restore order and reduce access control risks.
If there is a recommendation from external auditors, then the justification for the implementation of IdM through the standards runs quite smoothly.
Support current organization strategy
This approach to justifying the decision is partly a compilation of the previous ones, but in fact focuses on the other, using the above options as a set of arguments. The idea of this approach is to support the current mission, strategy or programs of the organization being implemented through the implementation of the system. For example, if a company has taken a course to increase the efficiency of processes, then IdM fits perfectly into the implementation of this program, helping to reduce costs for access control processes associated with downtime and manual labor. If an enterprise plans to enter an IPO, then IdM can be a means of increasing the company's capitalization. Such cases in our practice were more than once.
If the project fits into the framework of changes made by management, then its usefulness is much easier to communicate using the appropriate language. Previous approaches in this case can be used as a more substantive argument to reinforce the expected effect.
Summary
Above is a series of general approaches to justifying IdM implementation projects with which we personally met in practice. Our goal was to show how to approach this issue, and to give guidelines, in which situations it is better to use one or another method of justification. Nevertheless, in each company this process is very creative: it has its own specifics, procedures, format of presentation and even its own “language”, and always has an individual character. It remains to wish you creative success in this difficult task, and we hope our advice will help you justify before the leadership the justification for implementing any solution that you consider necessary.
Author: Dmitry Bondar, Head of Solar inRights Development and Promotion Department
- We should, but where can we get the money?
“Three from Prostokvashino”

In order for your conversation with the management about the necessity of the implementation project not to come down to this short dialogue from the cartoon, you need to prepare an argument in advance. For many years we have been engaged in the implementation of access control systems (IdM), and during this time, communicating with customers, we heard about a variety of methods to justify budgets. Today we put these life hacks in one article. Under the cat - a step-by-step guide and examples of formulas for calculating the payback period, improving operational efficiency and total system ownership costs. All this is considered on the example of IdM implementation, but the general principles are applicable to almost any IT system.
Any justification should include the expected benefits of the implementation, presented in the form of specific figures. In the case of IdM, it can rely on one or more criteria from the following list:
- improved performance;
- reducing the risk of information security incidents;
- compliance with regulatory / industry standards;
- support current organization strategy.
If the process of justifying budgets in a company is not very rigidly formalized, general considerations may be sufficient for coordination. But usually, management still requires translating everything into a cash equivalent and marking the time it takes to pay back.
Let's take a closer look at what benefits you can rely on to justify the IdM implementation project and when / how to use them.
Improving performance indicators
IdM implementation can indeed improve many performance indicators. For example, reduce the flow of applications for manual provision of access to employees and speed up their execution. Reduce the time and effort required to prepare data for auditors or information security services. Minimize the number of requests for technical support regarding the status of access requests.
To assess the increase in operating efficiency, indicators such as are commonly used:
- Employee downtime for hiring pending access to information systems.
- The number of operations for the management of user accounts associated with hiring, dismissal, transfer of positions, other requests of employees.
- The number of support calls related to the status of requests for access or change of passwords in information systems.
- The time required to collect data on employee access rights — for example, during an audit or upon request from a security service. Sometimes a simple collection of information about where an employee has access may take several days.
- The time it takes for IT and information security personnel to review their employees' access rights. This measure is provided by a number of standards in order to reduce redundancy of access rights, but in reality it is almost not carried out due to the very high labor intensity. For example, in an organization with a staff of 10,000, it takes about 1 day per employee.
When justifying through the improvement of performance indicators, it is important that these indicators are meaningful, so that they have a clear impact on business processes. For example, with a large staff turnover, it will be critical to shorten the term for issuing credentials and shorten the downtime of a new employee.
The easiest thing in financial metrics is to translate the improvement in performance indicators after the implementation of the system. Accordingly, it is necessary to calculate how much “it costs” to provide access before the introduction of IdM and how much - after.
Calculating the cost of access control before implementing IdM
We will consider the principles of calculation on a theoretical example, but, of course, when justifying the budget, you should use indicators that describe the realities of a particular organization. Suppose a company has 10,000 employees. To estimate the cost of access control, we use two indicators:
- losses from downtime of employees who were not given access rights in a timely manner;
- the cost of the execution of applications for access.
Here you can also take into account the “cost” of auditing and revising employees ’access rights to information systems, but these are more specific needs that not every organization has, so for simplicity we’ll leave them behind the scenes.
Employee downtime
losses To estimate employee downtime losses, we use a staff turnover indicator that reflects the average percentage of employees who leave the company during the year and who will need to be replaced by new staff. This will give us the average number of new employees per year who will need to provide access to information resources so that they can fully carry out their work.
Depending on the industry of the company and the type of activity of specific specialists, the level of turnover can vary significantly.

Statistics recruitment company Antal Russia
Suppose our company works in the field of logistics, and staff turnover is 25%. Therefore, we have to grant access rights to 2500 new employees a year.
In the next step, we will need to calculate the average time during which new employees are granted access to the IS. Depending on the size of the organization and the availability of a regional network, this figure can vary from 1 day to 2 weeks. In our experience, the average for the market is 3 working days, so we will use it.
Next, we need to estimate the amount of company losses from the downtime of one employee. Here, as they say, everything is very individual. The volume of losses can be highly dependent on the scope of the company, and on the region of presence, and on the size of the enterprise, and even on the position of the employee. For example, for a technical support employee, the lack of access to information systems is fraught with one hundred percent downtime. And the effectiveness of the work of the ACS manager, who can ensure the vital activity of the enterprise in many respects without the use of IP, the lack of access, of course, will not affect so dramatically. So that we are not accused of excesses on the ground, we take for our calculations an average of 50%.
To calculate losses from idle employees in the process of waiting for the necessary rights, it will also be necessary to determine the average “employee cost” for the organization without taking into account bonuses and overhead costs. In our example, this is 69570.64 rubles. In a month, an average of 20-21 working days, that is, the cost of employee remuneration is on average about 3,313 rubles per day.
So we count. Above, we have indicated that the granting of access rights takes 3 working days, during which the employee works with 50% efficiency. That is, 3,747 * 3 * 0.5 = 4969.5 rubles. the company is losing due to the downtime of one new employee. There are 2500 of them in a year, that is 12423 750 rubles in total.
Costs for the execution of applications for access
To estimate the costs for the execution of applications for access, we use the following indicators:
- The number of professionals who execute applications for access. In our example, it is 50 people.
- The percentage of working time they devote to this task is, say, 25%.
Based on the national average salary of the gross of such a specialist (79,718.39 rubles), we find that the company spends 79,718.39 * 12 * 50 * 0.25 = 11,957,758.5 rubles per year to execute applications.
Alternatively, the average number of requests (often this information can be obtained from the Service Desk system), the average execution time of an application and estimate the actual time spent on their execution can be taken as the basis for calculations. In this case, the calculations should be made separately for each type of system, since they can vary greatly. For example, providing access to Active Directory takes 5-10 minutes, but this type of access is required for all company employees. It may take 20-30 minutes to provide access to the SAP landscape, but not everyone needs such access.
As a result, we get some estimate of these costs. In our calculation, it amounted to a little more than 26 million rubles (see table 1).

Calculating the cost of access control after the implementation of IdM
Next, to estimate the payback period of the project, it will be necessary to compare the amount received with the assessment of similar costs after the implementation of IdM, plus the cost of directly implementing and maintaining the system.
The cost of implementing IdM for a particular company will be considered by you as a vendor or integrator. According to our estimates, the introduction of IdM-system in an enterprise with a staff of 10,000 employees on average will cost the company 25 million rubles. excluding annual technical support.
And now let's estimate how our costs will change after the introduction of IdM.
First, we calculate the percentage of access rights that the IdM system will provide to employees. As a rule, if an organization has some basic set of authority that is assigned to employees when they are hired, IdM automatically provides them. But let's even assume that IdM does not provide the entire basic set, but only 80%. If a year the company lost 12,423,750 rubles. due to downtime of employees waiting for access rights, now this amount is reduced by 80% and amounts to 2,484,750 rubles.
Now let's estimate what percentage of applications the IdM system can execute automatically, without human intervention. By experience, you can automate all 100% of applications for access to the system, if it is connected to the IdM through a connector. However, this requires a lot of work to create a catalog of functional powers of each full-time role, so in reality, the average percentage of automatically executed applications is lower - also at about 80%. Let us make an amendment that not all information systems will be connected to IdM via connectors, and we will lower this figure to 50%. Accordingly, the cost of providing access will decrease from 11,957,758.5 rubles. up to 5,978,879.25 rubles.
So, after the introduction of IdM, the same processes related to access control will cost the company 15,917,879.25 rubles cheaper per year. and amount to 8,463,629.25 rubles. But at the same time they will add the cost of technical support. Suppose a company allocates an individual employee for this task. The cost of the specialist’s work is taken from table 1 (calculation of the cost of access control) 79 718,39 rub. It turns out that a year it will take about 956,620.68 rubles to support IdM. and the total costs will be 9 420 249.93 rubles.
As a result, when the cost of implementing the system is 25 million rubles, the allocation of one specialist to support the system, 80% automated issuance of rights for recruitment and 50% of applications for access for the company as a whole, the payback period from the moment the system is commissioned will be a little over one and a half years (see table 2).

Sometimes analytical reports are used for this kind of substantiation, mainly coming from the pen of foreign analysts. They provide some figures on the effectiveness of system implementation. For example, reports promise that IT staff’s time savings using IdM will be 14%, the number of support calls related to access will decrease by 52%, and the number of unnecessary accounts will decrease by 10%. Unfortunately, these figures do not always reflect Russian realities.
Reducing the risk of incidents
The introduction of IdM allows you to reduce a number of information security risks or to ensure the timely detection of relevant incidents:
- risks of inconsistent access to information systems,
- risks of access of laid-off employees due to the fact that their accounts were not blocked,
- risks of unauthorized access to contractors whose rights were not revoked on time,
- risks of excessive powers of employees.
Often, when justifying the implementation of a system through information security risks, it is crucial for management to determine whether similar incidents occurred earlier. (And if not, then why defend against these risks?) Well, as one distinguished head of information security likes to say, such people can be advised not to put the lock on the door - since they have not been robbed before!
However, as practice shows, such incidents happen from time to time, and the effect of them can be quite tangible. In our practice, there was a case when a bank branch was idle for several days due to the fact that an employee “caught” a virus that encrypted critical data on behalf of his account, to which an employee should not have access at all. In this case, the damage is relatively simply translated into rubles, but this is not the case with all information security incidents related to access rights violations.
What are the risks of information security can reduce IdM-system? Examples include:
- Active accounts of dismissed employees.
- Inconsistent access rights or access that should not have been.
- Excessive access rights (may “multiply” due to transfers of employees within the organization without revoking extra powers, by granting rights to an employee according to the principle “like another employee in a similar position”).
- Access that was agreed and granted for a time, but not revoked on time.
- Accounts created at the time for technological needs, but not deleted later.
- Use of impersonal (group) accounts.
In general, in the matter of substantiation through IS, the attitude of business to information security is of fundamental importance. Somewhere it is treated as a formal function, somewhere - as a business critical. If information security is not essential for business, then it is better to justify the introduction through other articles.
Meeting the requirements of regulators / standards
This block of justifications is relevant for organizations that fall under the requirements of external regulators - for example, the Central Bank of the Russian Federation, or internal - for example, the parent organization that sets the standards of activity. The first, including organizations that are traded on the stock exchange.
The implementation of IdM allows you to meet the requirements for access control in accordance with standards such as STO BR, PCI DSS, SoX, ISO 27001 and others. Often, these requirements are closed by organizational measures, but often large organizations that undergo external audits are advised on the use of IdM class systems to restore order and reduce access control risks.
If there is a recommendation from external auditors, then the justification for the implementation of IdM through the standards runs quite smoothly.
Support current organization strategy
This approach to justifying the decision is partly a compilation of the previous ones, but in fact focuses on the other, using the above options as a set of arguments. The idea of this approach is to support the current mission, strategy or programs of the organization being implemented through the implementation of the system. For example, if a company has taken a course to increase the efficiency of processes, then IdM fits perfectly into the implementation of this program, helping to reduce costs for access control processes associated with downtime and manual labor. If an enterprise plans to enter an IPO, then IdM can be a means of increasing the company's capitalization. Such cases in our practice were more than once.
If the project fits into the framework of changes made by management, then its usefulness is much easier to communicate using the appropriate language. Previous approaches in this case can be used as a more substantive argument to reinforce the expected effect.
Summary
Above is a series of general approaches to justifying IdM implementation projects with which we personally met in practice. Our goal was to show how to approach this issue, and to give guidelines, in which situations it is better to use one or another method of justification. Nevertheless, in each company this process is very creative: it has its own specifics, procedures, format of presentation and even its own “language”, and always has an individual character. It remains to wish you creative success in this difficult task, and we hope our advice will help you justify before the leadership the justification for implementing any solution that you consider necessary.
Author: Dmitry Bondar, Head of Solar inRights Development and Promotion Department
